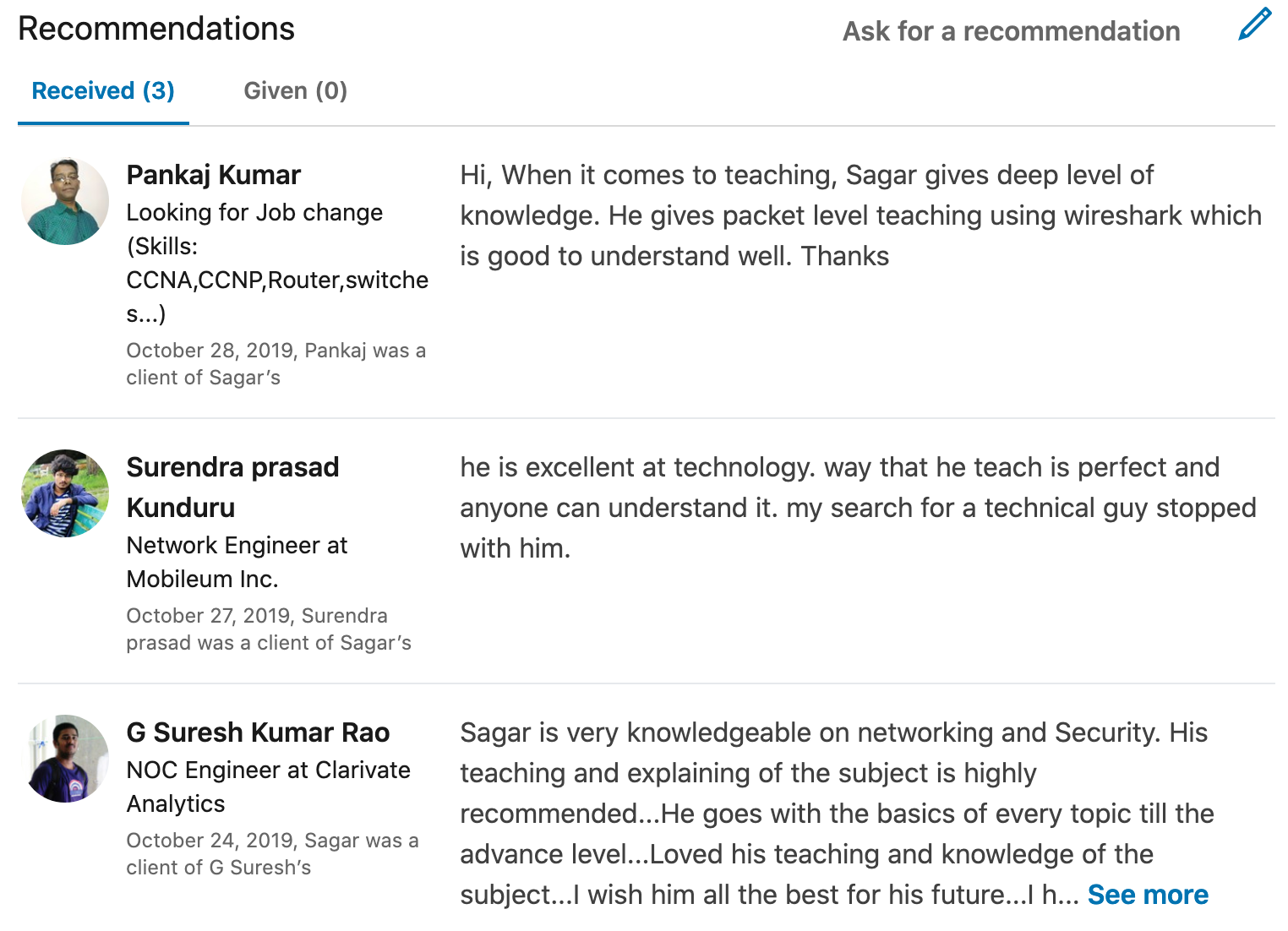
This is enrollment page for only Cisco ASA FTD firewall module.
To enroll to complete Combo Bundle: Firewall mastery 5IN1 – Learn 5 Top Technologies = PALO + CHECKPOINT + FORTIGATE + ASA/FTD + F5 LTM LOADBALANCER, more info !!!
Cisco ASA FTD (Firepower) Firewall
Welcome to CISCO ASA FTD (Firepower) Network Security Platform.
The flagship firewall of Cisco – the Cisco ASA (Adaptive Security Appliance) and FirePOWER technology (the result acquisition of Source Fire company by Cisco in 2013) lied down the foundation of “next generation firewall” line of products in Cisco’s portfolio: ASA FirePOWER Services. This next generation firewall is composed of widely known ASA-OS and software module (SFR) that takes care of main “next generation” functions like Application control, Intrusion Protection, Anti-Malware and URL Filtering.


What You Get:
- 40+ Hours – Live Online Instructor-led Training
- Lifetime Access to Web-portal Recordings
- 1.5 Months – Access to Our Lab Server Rack
- 1.5 Months – Live Dedicated Trainer Support
- You Learn – CISCO ASA / FTD
- Instant Access to Recordings after the Live Class
- 24×7 – Home Lab Setup Provided with 100+ Workbook for self practicing
- 10% OFF – Avail additional discount on our next Instructor-led Online Course
- Material: All training Material will be provided in pdf, CLI commands, study material
Course Content – Detailed
Module 1: NGFW overview & Cisco ASA/FTD Features
- [THEORY] Why do we need Firewall in spite of ACL in Router
- [THEORY] Stateful Inspection
- [THEORY] CheckPoint UTM Features
Module 2: CISCO ASA/FTD Components Overview
- [THEORY] Firewall / Gateway/ Enforcement Module (NG Appliances)
- [THEORY] Management Server (Smart-1 Appliances)
- [THEORY] Log Server
Module 3: CISCO ASA/FTD Installation Scenarios
- [THEORY] Standalone Installation (2 Tier)
- [THEORY] Distributed Installation (3 Tier)
- [THEORY] Standalone vs Distributed
Module 4: CISCO ASA/FTD Standalone (2-Tier) Installation
- [LABS] Installation of CISCO ASA/FTD ISO (FW + Management) in PNET Site-A setup
- [LABS] Installation of Smart Console at Site-A on Windows PC
- [LABS] Enabling Blades on CISCO ASA/FTD Objects
- [LABS] Configure Network Interfaces & Topology (Anti-Spoofing concept)
- [LABS] Configure Routing (static & Default Routes)
- [LABS] Login to the Console and install Default Policy
Module 5: CISCO ASA/FTD Distributed (3-Tier) Installation
- [LABS] Installation of CISCO ASA/FTD ISO (FW) in PNET Site-B setup
- [LABS] Installation of CISCO ASA/FTD ISO (Management) in PNET Site-B setup
- [LABS] Adding a Gateway to the Security Management Server (SIC Integration)
- [LABS] SIC Troubleshooting
- [THEORY] Expert Mode & CLISH
- [LABS] Expert Mode & CLISH
Module 6: Managing Administrators
- [THEORY] Add Permission Profile
- [LABS] Add Permission Profile
- [THEORY] Add Administrator and Add Permission Profile
- [LABS] Add Administrator and Add Permission Profile
- [THEORY] Database Lock concepts
- [LABS] Database Lock concepts
Module 7: Policies
- [LABS] Add a Site-C Firewall to Management Server at Site B
- [LABS] Add a Policy for Site-C Firewall on Management Server B
- [LABS] Add a Policy for Site-B to Site-C connectivity
- [THEORY] Policy Objects ( Nodes, Host, Network, Groups, Address Ranges, Services etc.)
- [LABS] Policy Objects ( Nodes, Host, Network, Groups, Address Ranges, Services etc.)
- [LABS] Add Internet Access Rule
Module 8: Policies (contd.)
- [LABS] Add FW Management Rules
- [LABS] Add DMZ Access Rules
- [THEORY] Policy Layers (Introduction)
- [THEORY] Ordered Layers and Inline Layers
- [LABS] Ordered Layers and Inline Layers
- [THEORY] Policy Optimization for performance
- [THEORY] Implied rules & Global Properties
- [LABS] Implied rules & Global Properties
- [THEORY] Stealth Rule, Clean-up Rule
- [LABS] Stealth Rule, Clean-up Rule
Module 9: Logs Management and Adminsitration
- [THEORY] Log Files & Troubleshootin (Filters, etc)
- [LABS] Log Files & Troubleshootin (Filters, etc)
- [THEORY] Log files Management
- [LABS] Log files Management
Module 10: Network Address Translation
- [THEORY] NAT Theory & Concepts
- [THEORY] Auto NAT (Hide & Static) Lab
- [LABS] Auto NAT (Hide & Static) Lab
- [THEORY] Manual NAT (Hide & Static) Lab
- [LABS] Manual NAT (Hide & Static) Lab
- [THEORY] PAT Concepts
- [THEORY] No-NAT Concept
Module 11: CheckPoint Clustering
- [LABS] Add Cluster object
- [LABS] Add Cluster Members
- [LABS]Configure Clustering
- [LABS] Test Clustering
- [LABS] High-Availabilitiy and Load Sharing scenarios
Module 12: HTTPS Inspection
- [THEORY] SSL Concept & HTTPS Inspection
- [LABS] Configure HTTPS Inspection
- [LABS] Generate HTTPS Cerificate and install the Certificate on Nodes
- [LABS] Enable HTTPS Inspection Blade & Deploy Policy for SSL Decrytion
- [LABS] Test SSL Decryption
Module 13: UTM Features
- [LABS] Application Control
- [LABS] URL filtering
- [LABS] Conetent Awareness
- [LABS] DLP
- [THEORY] Threat Prevention Policy (Concept and Overview)
- [THEORY] IPS (Concept and overview)
Module 14: Identity Awareness
- [THEORY] User based Access rule with authenticated Access
- [LABS] User based Access rule with authenticated Access
- [LABS] Client Authentication
- [LABS] Install AD server at Site-b
- [LABS] Enable Identity Awareness Blade
- [LABS] Configure Identity Awareness rules based on Access objects
Module 15: VPN
- [THEORY] VPN Theory
- [LABS] VPN Site-A to Site-B configuration (Lab)
- [LABS] Remote Access VPN
- [LABS] Mobile Access / SSL VPN
- [LABS] VPN tunnel Utility
Module 16: Backup & Restore (contd.)
- [LABS] Backup, Restore & Snapshot through Web GUI
- [LABS] Backup, Restore & Snapshot through CLI
Module 18: Licensing (overview)
- [THEORY] Central License
- [THEORY] Local License
- [THEORY]Smart update for Licenses& Contracts
Module 17: Command Line Interface (CLI)
- [THEORY] cpconfig
- [LABS] cpconfig
- [THEORY] cpstop and cpstart commands, cprestart
- [LABS] cpstop and cpstart commands, cprestart
- [THEORY] configure interfaces
- [LABS] configure interfaces
- [THEORY] configure routes
- [LABS] configure routes
- [THEORY] Some More commands
- [LABS] Some More commands
More Preview Before You Buy:
Requirements
- PC or Laptop with internet Connection
- Knowledge on basic Networking Components
Who this course is for:
- CCNA certified Network Engineer
- Network L1, L2, L3 Tier
- Senior Network Engineer
- Network Trainers
- Network Consultant
- Mid-level network engineers
- Network administrators
- Network support technicians
- Help desk technicians
- Interns, Freshers, Graduate
Prerequisites
- There are no formal prerequisites, but you should have a good understanding of the exam topics before taking the exam.
- Students expected to have knowledge in basic Network Fundamentals
Certification
- CCNP SECURITY
- CCNP SECURITY FIREPOWER CONCENTRATION PAPER
To obtain certification, you must pass the CCNP mandatory+one of the concentration certification exam. CCNP Security certification is valid for two years from the date of completion.
Student Success Feedback