Ticket#19 – DHCP Clients Getting APIPA Address: Troubleshooting DHCP Snooping and Relay Agent Issues [CCNP ENTERPRISE]
Table of Contents
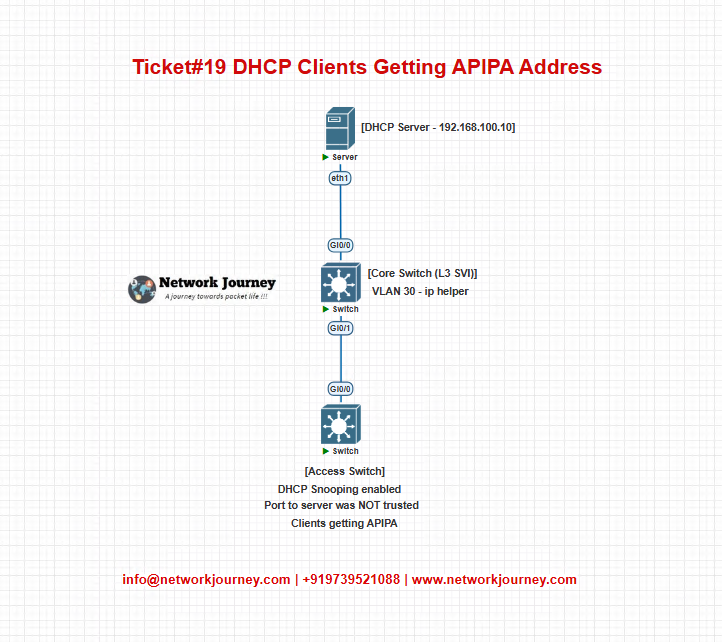
Problem Summary
A new VLAN was added for a temporary training lab. Clients connected successfully but were not receiving IP addresses from the DHCP server. Instead, they self-assigned APIPA addresses (169.254.x.x), making them unable to reach the internet or internal resources.
Initial pings to the DHCP server worked from the switch. Server was online and responsive. But DHCP clients still failed to get valid IPs.
Symptoms Observed
- Clients in VLAN 30 got 169.254.x.x addresses
ipconfig /renewfailed with “No DHCP server found”- DHCP server reachable via ping from access switch
- Wireshark on client showed DHCP DISCOVER sent, but no OFFER received
- Logs showed DHCP packets being dropped by switch
- Relay (ip helper-address) configured, but no bindings created on the server
Root Cause Analysis
This issue was caused by a combination of two misconfigurations:
- DHCP Snooping enabled, but uplink to DHCP server not marked as trusted
- This caused DHCP OFFER/ACK packets (server to client) to be dropped by the switch
- Relay Agent (ip helper-address) was missing on the Layer 3 interface of the new VLAN
- So DHCP DISCOVER from clients never reached the centralized DHCP server
Together, these caused DHCP to silently fail, leading to APIPA addresses.
The Fix
- Mark DHCP server-facing interface as trusted:
interface GigabitEthernet0/1 ip dhcp snooping trust - Ensure DHCP snooping is enabled globally and per VLAN:
ip dhcp snooping ip dhcp snooping vlan 30 - Add relay configuration to SVI of new VLAN:
interface Vlan30 ip helper-address 192.168.100.10 - Clear DHCP bindings (optional for revalidation):
clear ip dhcp binding * - Restart client interfaces or manually release/renew:
ipconfig /release ipconfig /renew
EVE-NG Lab Topology
Verification
| Command | Purpose |
|---|---|
show ip dhcp snooping | Confirm snooping enabled globally |
show ip dhcp snooping vlan 30 | Check VLAN-specific configuration |
show ip dhcp snooping binding | Review learned bindings |
debug ip dhcp server packet | On server to trace DISCOVER/OFFER |
show run interface Gi0/1 | Confirm trust status |
ipconfig /all (client) | Check assigned IP/lease info |
| Wireshark capture | Confirm OFFER/ACK dropped at switch |
Key Takeaways
- DHCP Snooping protects against rogue servers—but must be properly trusted at server-facing ports
- Relay (ip helper-address) is essential when DHCP server is not in the same VLAN
- APIPA addresses (169.254.x.x) = client fallback when no DHCP reply is received
- Always verify trust boundaries and Layer 3 relay config
- DHCP issues often don’t show up in logs—packet captures are your best friend!
Best Practices / Design Tips
- Always enable
ip dhcp snoopingwith correct trusted port config - On Layer 3 interfaces, add
ip helper-addressfor every DHCP-enabled VLAN - Use static ARP entries or DHCP reservations for critical clients
- Monitor snooping bindings regularly for anomalies
- Test new VLANs with real clients or DHCP simulators
- Keep DHCP logs and binding database backups
- Use loopback filters or ACLs to limit rogue DHCP servers on the network
FAQs
1. What is an APIPA address and when does it occur?
Answer: APIPA (Automatic Private IP Addressing) is an address in the 169.254.0.0/16 range assigned automatically by a Windows client when a DHCP server response is not received. It typically indicates DHCP failure or lack of network communication with the DHCP server.
2. How do I know if DHCP Snooping is enabled on a Cisco switch?
Answer: Use the command:
show ip dhcp snooping
It displays the status, VLANs under protection, and trusted interfaces.
3. What causes DHCP Snooping to block DHCP responses?
Answer: If the DHCP server or relay agent is connected to an interface not marked as trusted, DHCP Snooping drops incoming DHCP OFFER or ACK packets from that interface, preventing clients from getting IPs.
4. How can I fix DHCP Snooping-related issues?
Answer: Ensure that the switchport connected to the DHCP server or upstream relay is configured as trusted:
interface GigabitEthernet1/0/24 ip dhcp snooping trust
5. What is a DHCP Relay Agent and when is it needed?
Answer: A DHCP Relay Agent (configured using ip helper-address) is required when the DHCP server is not on the same subnet as the client. It forwards DHCP broadcast packets to the server’s IP over unicast.
6. How do I verify that ip helper-address is correctly set?
Answer: Check the client VLAN’s Layer 3 interface:
show run interface vlan 10
Look for the ip helper-address <DHCP_SERVER_IP> line.
7. Can DHCP Snooping and Relay be used together?
Answer: Yes. DHCP Snooping should be configured on Layer 2 switches, while the DHCP Relay is typically set on the Layer 3 gateway (SVI or routed interface) for the client VLAN.
8. What happens if a switch doesn’t support DHCP Snooping properly?
Answer: It may allow rogue DHCP servers to assign IPs, or it may drop legitimate DHCP packets, causing clients to self-assign APIPA addresses.
9. Which packets are filtered by DHCP Snooping?
Answer: DHCP Snooping filters untrusted DHCP responses (OFFER, ACK, NAK) from untrusted interfaces to prevent spoofing or rogue servers.
10. How do I verify DHCP bindings on the switch?
Answer: Use:
show ip dhcp snooping binding
This shows MAC-to-IP mappings dynamically learned through DHCP.
11. Why would a DHCP client intermittently receive an APIPA address?
Answer: Possible reasons include:
- DHCP server unreachable at time of request
- Temporary STP delay
- Relay misconfiguration
- Packet dropped due to untrusted port under DHCP Snooping
12. How many ip helper-address entries can be configured?
Answer: Cisco IOS allows up to eight helper addresses per interface. They forward DHCP and other UDP broadcasts.
13. What other UDP ports does ip helper-address forward?
Answer: Besides DHCP (67/68), by default it also forwards:
- TFTP (69)
- DNS (53)
- TACACS (49)
- NetBIOS (137/138)
- Time (37)
You can control this with:
no ip forward-protocol udp 69
14. Is it necessary to configure DHCP Snooping per VLAN?
Answer: Yes. By default, it is disabled globally and per VLAN. Enable it like this:
ip dhcp snooping ip dhcp snooping vlan 10
15. How do I ensure clients always get valid IP addresses?
Answer:
- Ensure DHCP server/relay reachability
- Configure correct
ip helper-address - Trust the correct switchports
- Enable and monitor DHCP Snooping
- Avoid overlapping scopes and rogue DHCP servers
YouTube Video
Final Note
Understanding how to differentiate and implement DHCP Clients Getting APIPA Address: Troubleshooting DHCP Snooping and Relay Agent Issues is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career
![Ticket#19 – DHCP Clients Getting APIPA Address: Troubleshooting DHCP Snooping and Relay Agent Issues [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/Ticket19_DHCP-Clients-Getting-APIPA-Address-Troubleshooting-DHCP-Snooping-and-Relay-Agent-Issues_networkjourney.png)

![[Day 31] Cisco ISE Mastery Training: Wired Posture Assessment Overview](https://networkjourney.com/wp-content/uploads/2025/08/Day-31-–-Cisco-ISE-Mastery-Training-Wired-Posture-Assessment-Overview-1.png)
