[Day 4] Cisco ISE Mastery Training: Lab Topology Design for ISE Practice
Table of Contents
Introduction
In today’s enterprise networks, controlling who and what connects is no longer optional — it’s a security necessity.
Cisco Identity Services Engine (ISE) is the gold standard for Network Access Control (NAC), enabling centralized authentication, authorization, and accounting for wired and wireless devices.
This Day 4 session of our Cisco ISE Mastery Training goes beyond theory. You’ll design and build a fully functional ISE lab topology using VMware Workstation or EVE-NG, complete with:
- Catalyst Switch (wired access)
- Wireless LAN Controller (WLC)
- Active Directory (AD) Integration
- Endpoints (wired and wireless)
- Full step-by-step GUI & CLI configuration
We’ll configure 802.1X, MAB, and Guest Access, validate authentication, and troubleshoot with RADIUS Live Logs — exactly as you’d do in production.
Whether you’re preparing for CCNP/CCIE Security, working in a SOC/NOC, or just starting with ISE, this lab will give you real-world NAC deployment skills.
Problem Statement
Without Cisco ISE:
- Unauthorized devices can plug in and access sensitive data.
- Guest Wi-Fi lacks proper isolation.
- Switches and WLCs operate with static VLAN assignments.
- Incident response is slow — no clear visibility of device/user identity.
Result: security gaps, compliance failures, and increased breach risk.
Solution Overview
Cisco ISE addresses this by:
- Centralizing authentication & authorization using RADIUS.
- Enforcing policies based on user identity, device type, and posture.
- Integrating with switches, WLCs, firewalls, and Active Directory.
- Providing guest portals, BYOD onboarding, and profiling.
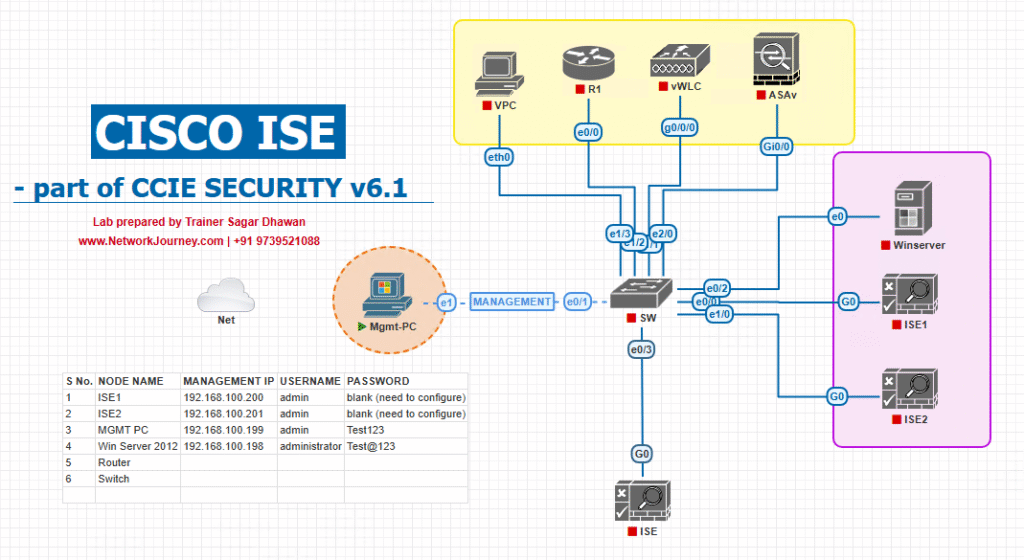
Sample Lab Topology
Lab Components (VMware/EVE-NG):
- Cisco ISE VM (v3.x, 4 vCPU, 16GB RAM, 300GB disk)
- CSR1000v Router (routing + internet simulation)
- Catalyst Switch (IOSv-L2 or physical)
- Cisco WLC (v9800 or legacy 5508 in EVE-NG)
- Windows Server 2019 (AD, DNS, DHCP)
- Windows 10 Client (wired test)
- Wireless Client (laptop or VM)
Topology Layout:
Step-by-Step Lab Guide
Part 1 – ISE Initial Setup
- Deploy ISE VM in VMware/EVE-NG.
- Configure hostname, DNS, NTP.
- Install ISE license.
- Create admin user.
Part 2 – Add Network Devices
- ISE GUI:
Administration → Network Resources → Network Devices→ Add- Name:
Switch-Access1 - IP:
10.10.10.2 - Enable RADIUS Authentication Settings
- Shared Secret:
cisco123
[Screenshot: ISE Add Network Device Screen]
- Name:
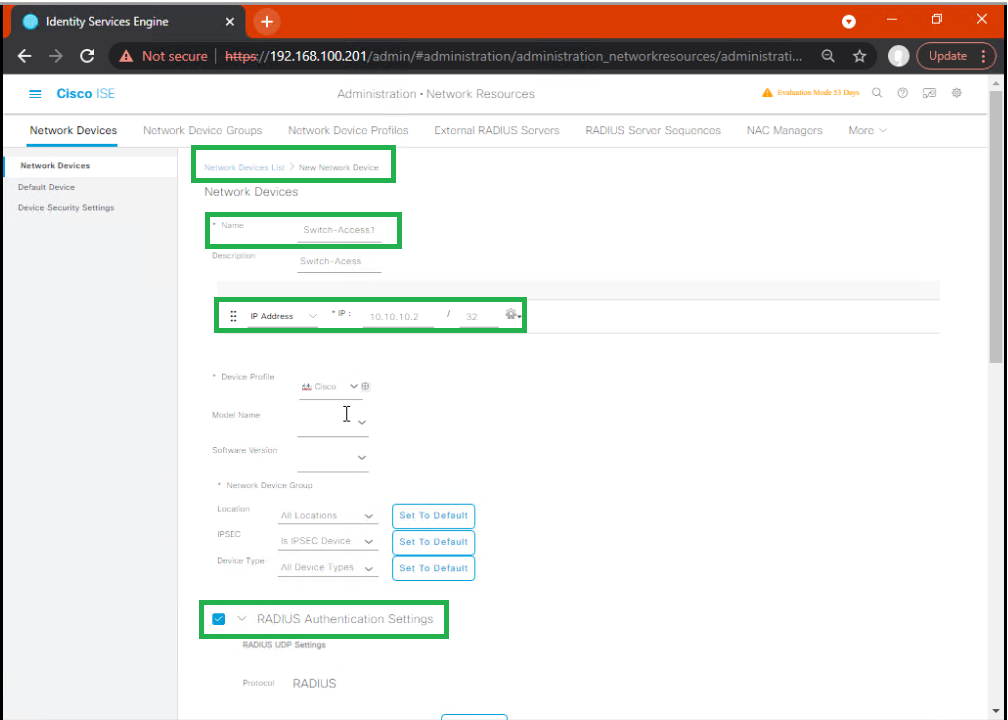
- Repeat for WLC.
Part 3 – Integrate ISE with Active Directory
- ISE GUI:
Administration → Identity Management → External Identity Sources → Active Directory- Click Join → Enter domain & credentials.
[Screenshot: ISE AD Join Screen]
- Click Join → Enter domain & credentials.
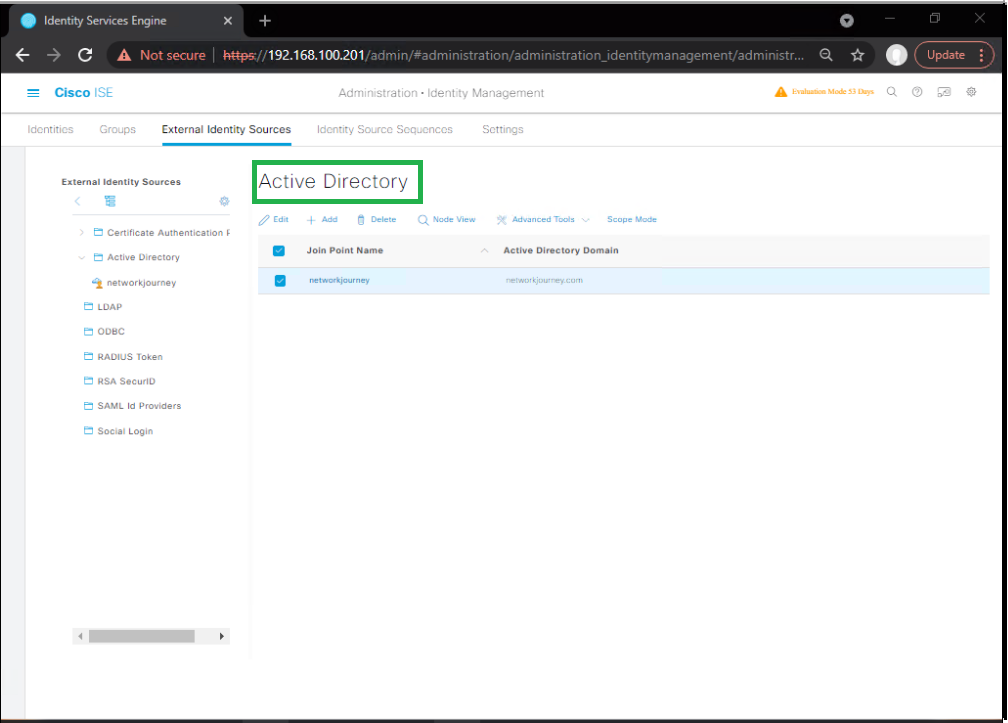
- Verify status.
Part 4 – Configure Policy Sets
- ISE GUI:
Policy → Policy Sets→ Add New:Wired_802.1X
[Screenshot: ISE Policy Set Screen]
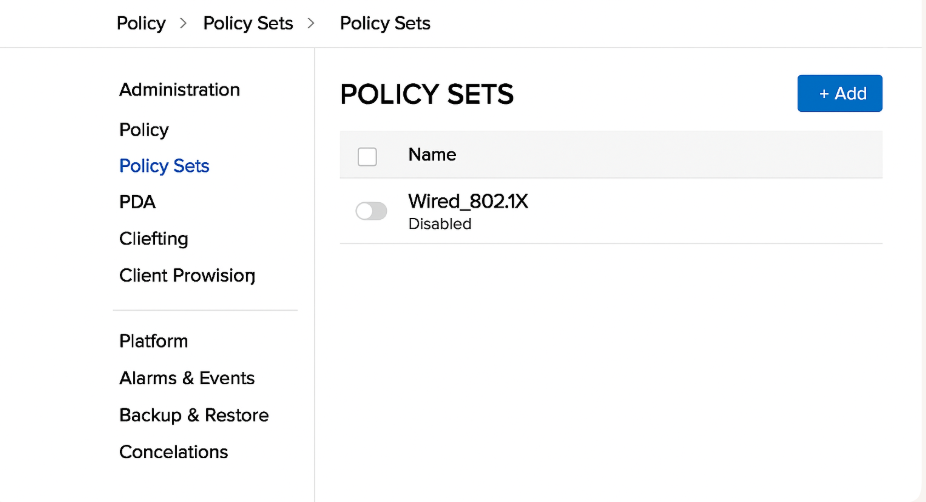
- Authentication Policy:
- If Wired 802.1X → Use AD.
- If MAB → Use Internal Endpoints.
- Authorization Policy:
- AD Group:
IT_Dept→ VLAN 20. - Unknown MAC → Guest VLAN 30.
- AD Group:
Part 5 – Switch Configuration (CLI)
conf t radius server ISE address ipv4 10.10.10.5 auth-port 1812 acct-port 1813 key cisco123 ! aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius ! dot1x system-auth-control ! interface Gig1/0/1 switchport mode access authentication port-control auto mab dot1x pae authenticator spanning-tree portfast
Part 6 – WLC Configuration
- GUI:
Security → AAA → RADIUS Authentication→ Add ISE.
[Screenshot: WLC RADIUS Config Screen]
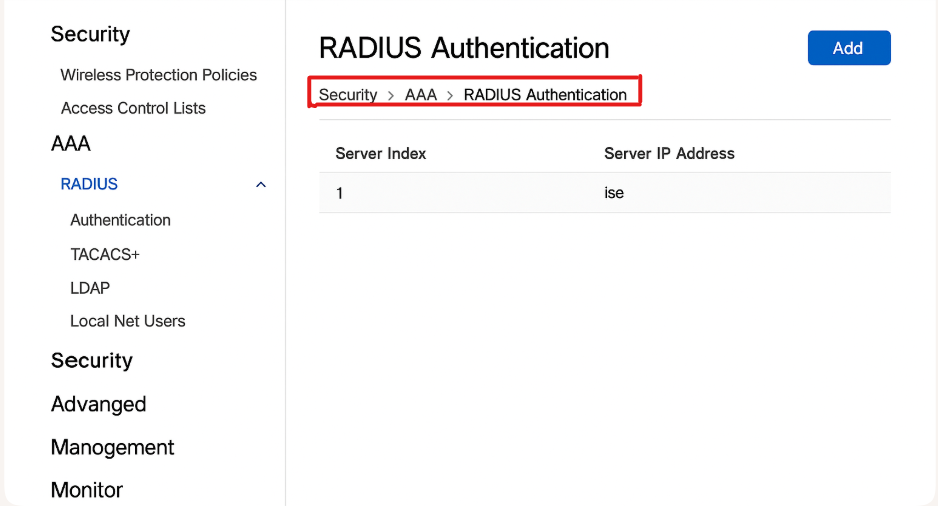
- Enable RADIUS NAC.
- Map WLAN SSID to ISE.
Part 7 – Validation
- ISE GUI:
Operations → RADIUS → Live Logsto verify success.
[Screenshot: ISE Live Logs]
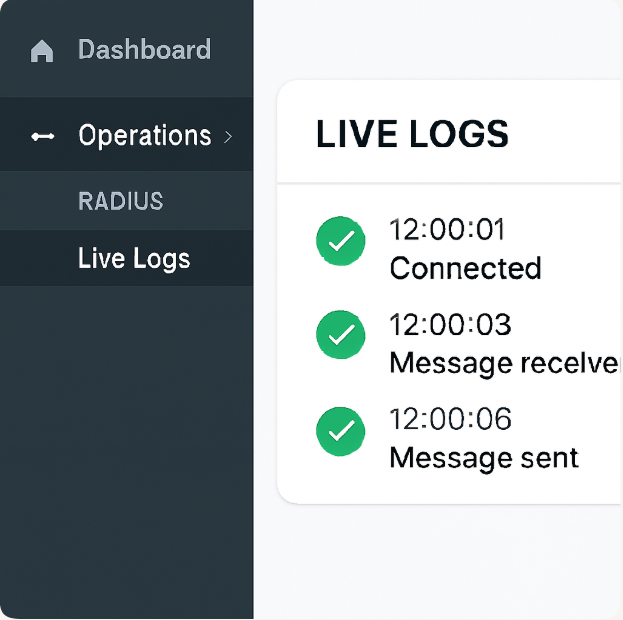
- Switch CLI:
show authentication sessions interface Gi1/0/1 show dot1x all
- WLC CLI:
show client detail <MAC>
FAQ
1. Can I run Cisco ISE in a lab with less than the recommended hardware specs?
- Yes, but expect performance degradation.
- Minimum workable (lab only): 4 vCPU, 12GB RAM, 200GB disk.
- Recommended: 4 vCPU, 16GB RAM, 300GB disk.
- Features like profiling and posture need more resources.
- Tip: Disable unused services in the lab to save CPU/RAM.
2. Why does my ISE fail to join Active Directory?
- Common causes:
- NTP mismatch > 5 minutes between ISE and AD.
- Incorrect DNS resolution of the domain controller.
- Firewall blocking TCP/UDP 88, 389, 636, 3268, 464.
- Fix:
show ntp nslookup ad.domain.local ping ad.domain.local - In ISE GUI: Administration → Deployment → Synchronize Time before retry.
3. Do I need a physical switch for 802.1X testing in the lab?
- No, IOSv-L2 in EVE-NG supports 802.1X & MAB commands for basic testing.
- But: Physical Catalyst switches offer full dot1x features, including voice VLANs, critical VLANs, and downloadable ACLs.
- CLI check:
show dot1x all show authentication sessions
4. My MAB authentication isn’t working — what should I check?
- Ensure endpoint MAC address is in ISE → Internal Endpoints with correct format (uppercase, no delimiters).
- Switch port must have:
mab authentication order mab dot1x - ISE Live Logs will show if RADIUS request is reaching ISE.
5. How do I capture RADIUS traffic for troubleshooting?
- On switch:
monitor session 1 source interface Gi1/0/1 monitor session 1 destination interface Gi1/0/2Connect Wireshark to Gi1/0/2, filter:udp.port==1812 || udp.port==1813 - Or capture on ISE CLI:
tcpdump -i eth0 port 1812 or port 1813 -w radius.pcap
6. What’s the difference between 802.1X, MAB, and WebAuth in ISE?
- 802.1X:
- Uses EAP with username/password or certificate.
- Most secure, supports posture and profiling.
- MAB:
- Uses MAC address lookup when 802.1X fails or is not supported.
- Often for printers, IP phones, IoT devices.
- WebAuth:
- Redirects users to a captive portal (common in guest Wi-Fi).
7. Can I assign ACLs dynamically from ISE?
- Yes — use Downloadable ACLs (dACLs).
- Create ACL in ISE:
Policy → Policy Elements → Results → Authorization → Downloadable ACLs - Assign in Authorization Profile.
- Switch must support
ip device trackingfor dACL enforcement.
8. Why is my endpoint stuck in “unauthorized” state?
- Possible causes:
- Missing
dot1x system-auth-controlglobally. - Port config missing
authentication port-control auto. - ISE policy mismatch (auth success but no matching authorization rule).
- Missing
- Validate:
show authentication sessions interface Gi1/0/1 details
9. Can I simulate BYOD onboarding in the lab?
- Yes, with:
- AD Certificate Services for issuing device certificates.
- Multiple SSIDs (one for onboarding, one for production).
- ISE MyDevices portal.
- BYOD flow works fully in EVE-NG with a WLC & simulated clients.
10. How do I reset the ISE admin password in a lab?
- Console into ISE VM:
- Reboot.
- At boot menu, select ISE Recovery Mode.
- Choose “Reset administrator password”.
- Or if logged in with another admin:
application reset-passwd ise admin
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
This lab builds a realistic Cisco ISE practice environment to:
- Learn wired & wireless NAC.
- Integrate with AD for identity-based access.
- Configure policies & validate results via GUI and CLI.
I run a focused 4-month instructor-led training covering CCIE Security skills. This program is designed for network engineers who want to master CCIE Security and advance their careers
Join the training here and take your first step towards becoming a CCIE Security expert.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 4] Cisco ISE Mastery Training: Lab Topology Design for ISE Practice](https://networkjourney.com/wp-content/uploads/2025/08/Day-4-Cisco-ISE-Mastery-Training-Lab-Topology-Design-for-ISE-Practice_networkjourney.png)

![[Day 7] Cisco ISE Mastery Training: Configuring Certificates (Self-Signed & CA-Signed)](https://networkjourney.com/wp-content/uploads/2025/08/Day-7-Cisco-ISE-Mastery-Training-Configuring-Certificates-Self-Signed-CA-Signed.png)
![[Day 9] Cisco ISE Mastery Training: Creating Internal Users & Groups](https://networkjourney.com/wp-content/uploads/2025/08/Day-9-Cisco-ISE-Mastery-Training-Creating-Internal-Users-Groups.png)