[Day 17] Cisco ISE Mastery Training: Wired 802.1X vs MAB vs WebAuth
Table of Contents
Introduction
In enterprise networks, controlling who gets access to the wired LAN is as important as controlling wireless access. Cisco ISE provides multiple authentication methods — 802.1X, MAC Authentication Bypass (MAB), and WebAuth — to ensure every device is authenticated, whether it supports 802.1X or not.
Understanding when and how to apply these methods is crucial for network engineers aiming to design secure and user-friendly access control. Today’s lab will walk you through configuring, validating, and troubleshooting all three methods in a wired environment.
Problem Statement
Not all devices are created equal:
- Corporate laptops can handle 802.1X.
- Legacy printers, IP phones, and IoT devices often require MAB.
- Guest users might need WebAuth before being allowed on the network.
The challenge? Seamlessly integrating all three authentication methods so that authorized users connect instantly, unauthorized users are blocked, and guests get easy but controlled access.
Solution Overview
Cisco ISE solves this by allowing multi-method authentication policies. You can:
- Use 802.1X for devices with supplicants.
- Fall back to MAB for devices without supplicants.
- Redirect unknown endpoints to a WebAuth portal for guest login.
ISE’s policy engine lets you define precise VLAN assignments, ACLs, and posture checks per method.
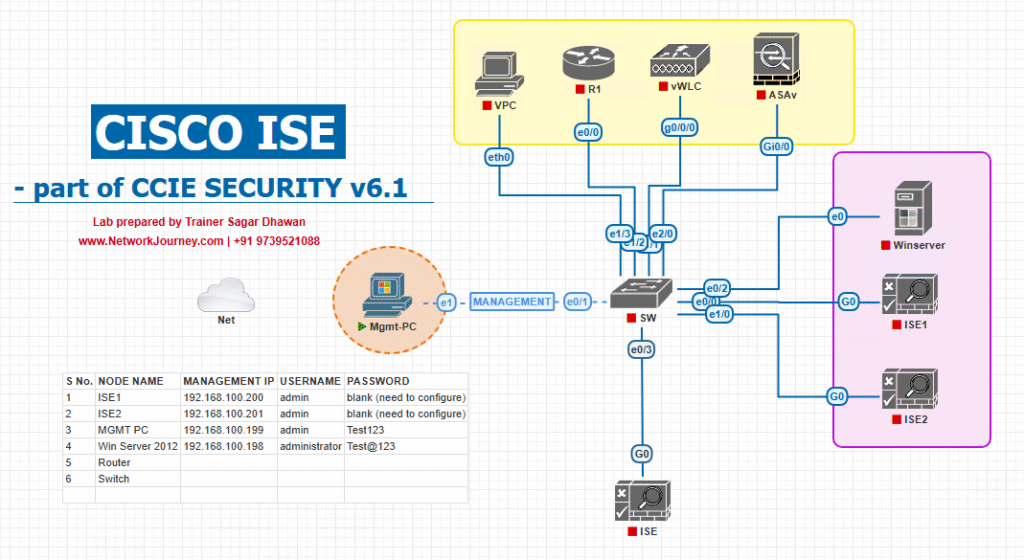
Sample Lab Topology
Lab Environment:
- Platform: EVE-NG running Cisco Catalyst 9300v switch + Cisco ISE 3.x.
- Endpoints:
- Windows 10 laptop with supplicant enabled (802.1X).
- Printer (MAB).
- Guest laptop (WebAuth).
- VMware for endpoint virtualization.
- Connections:
- SW1 → ISE via RADIUS (TCP/UDP 1812/1813).
- SW1 → Endpoints on access ports.
Diagram Description:
- Admin laptop uses 802.1X (EAP) to authenticate — supplicant communicates EAPOL to the switch which proxies RADIUS to ISE.
- Printer has no supplicant; switch uses MAB (MAC authentication) — the switch sends the MAC to ISE for lookup.
- Guest laptop is redirected via WebAuth (HTTP redirect) to the ISE Guest Portal for credential entry or sponsor approval.
- Switch sends RADIUS (UDP 1812/1813) and TACACS+ (TCP 49 for device admin) to ISE. ISE may consult Active Directory (LDAP/LDAPS) for user/group membership during policy decisions.
Topology Layout:
Step-by-Step GUI & CLI Configuration Guide
A. Switch Configuration
! Enable AAA aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius ! RADIUS Server radius server ISE address ipv4 10.10.10.5 auth-port 1812 acct-port 1813 key cisco123 ! Enable 802.1X dot1x system-auth-control ! Interface Configurations interface Gi1/0/1 switchport mode access switchport access vlan 10 authentication order dot1x mab authentication priority dot1x mab authentication port-control auto mab dot1x pae authenticator interface Gi1/0/2 switchport mode access switchport access vlan 20 authentication order mab authentication port-control auto mab interface Gi1/0/3 switchport mode access switchport access vlan 30 authentication order mab authentication port-control auto mab
B. ISE GUI Configuration
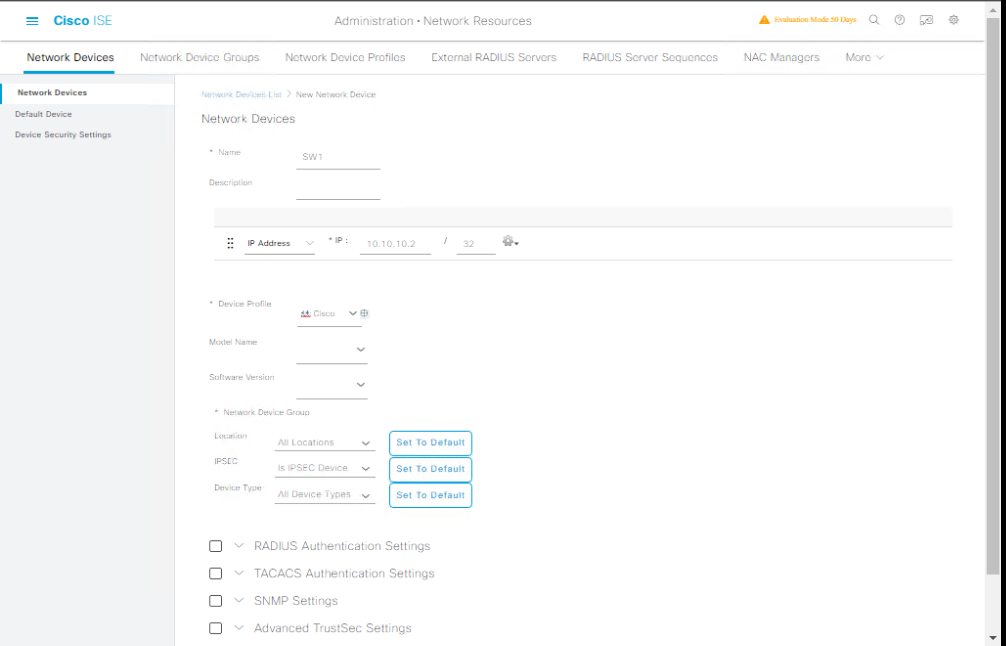
Step 1 – Add Network Device
- Navigate: Administration > Network Resources > Network Devices
- Click Add
- Name: SW1
- IP:
10.10.10.2 - RADIUS Key:
cisco123
[Screenshot: Add Network Device Screen]
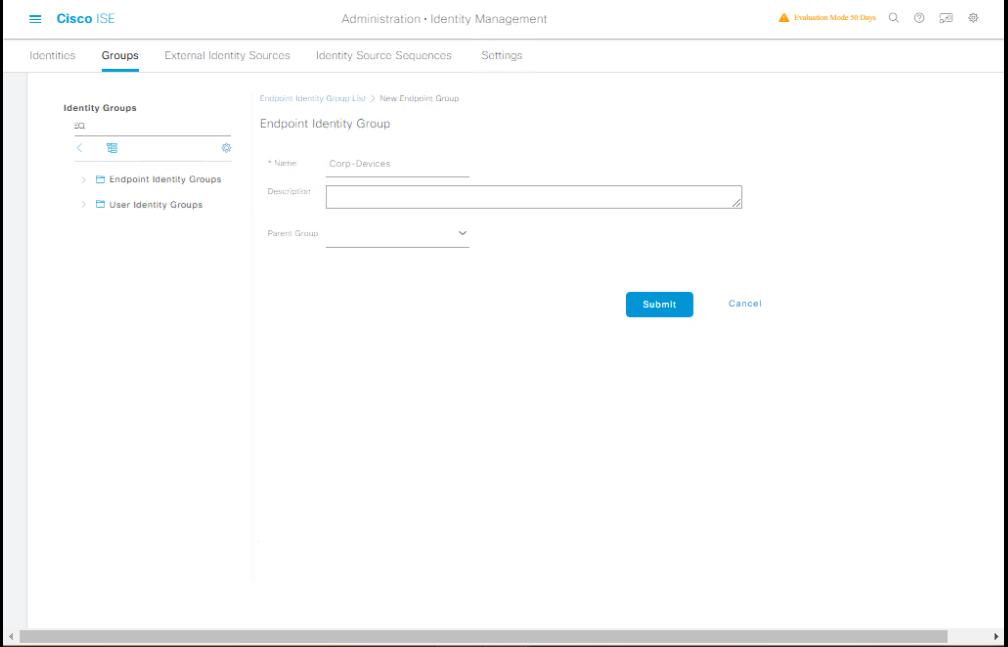
Step 2 – Configure Identity Groups
- Go to Administration > Identity Management > Groups.
- Create:
Corp-DevicesPrintersGuests
[Screenshot: Identity Groups Screen]
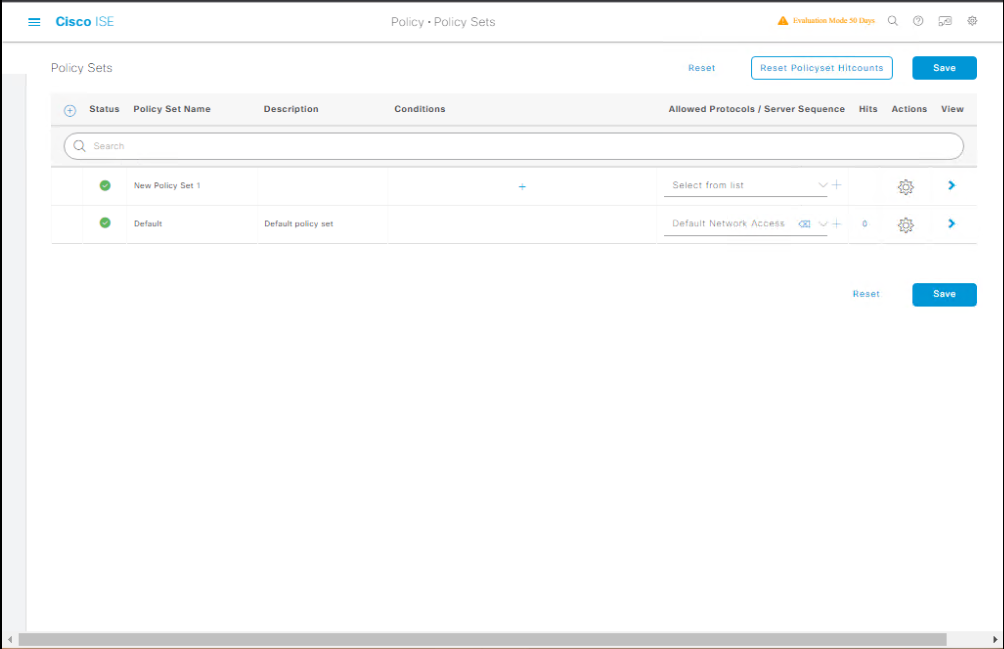
Step 3 – Create Authentication Policy
- Navigate: Policy > Policy Sets
- Create Wired-Access Policy Set
- Authentication Rules:
- 802.1X: If
Wired_Machine_802.1X→ use AD. - MAB: If
Wired_MAC→ use Internal Endpoints DB. - WebAuth: If
Wired_Guest→ redirect to Guest Portal.
[Screenshot: Policy Set Screen]
- 802.1X: If
Step 4 – Create Authorization Profiles
- Go to Policy > Policy Elements > Results > Authorization > Authorization Profiles.
- Profiles:
CorpVLAN10– VLAN 10PrinterVLAN20– VLAN 20GuestRedirect– Redirect ACL + Guest Portal URL
[Screenshot: Authorization Profile Screen]
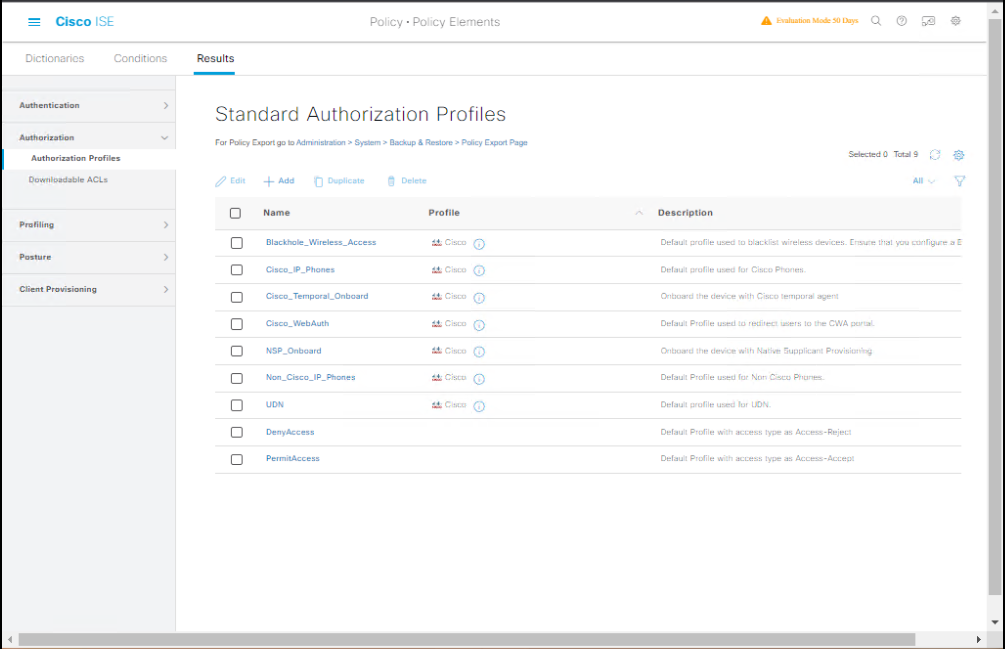
Step 5 – Bind Rules in Authorization Policy
- In Wired-Access Policy Set, define:
- 802.1X → CorpVLAN10
- MAB (Printer) → PrinterVLAN20
- WebAuth (Guests) → GuestRedirect
[Screenshot: Authorization Rules Screen]
C. Validation – CLI
Check sessions:
show authentication sessions show authentication sessions interface Gi1/0/1 details
Force re-authentication:
clear authentication sessions interface Gi1/0/1
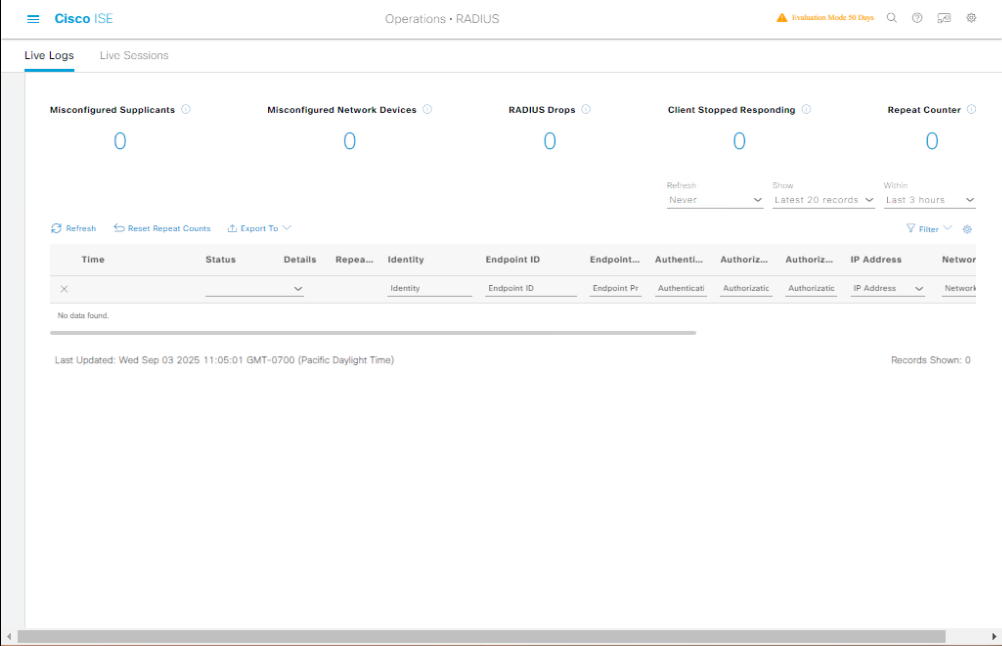
D. Validation – GUI
- Navigate to Operations > RADIUS > Live Logs in ISE.
- Check:
- 802.1X log – EAP Success.
- MAB log – MAC matched.
- WebAuth log – Redirect to portal.
[Screenshot: ISE Live Logs Screen]
Comparison table for Wired 802.1X vs MAB vs WebAuth in the context of Cisco ISE:
| Feature / Criteria | 802.1X | MAB (MAC Authentication Bypass) | WebAuth (Captive Portal) |
|---|---|---|---|
| Authentication Method | EAP over LAN (EAPOL) | MAC address lookup in ISE | HTTP/HTTPS redirect to ISE portal |
| Client Requirement | Supplicant software required (e.g., Windows, macOS) | None – device only needs a MAC address | Web browser with HTTP/HTTPS access |
| Security Strength | High – uses credentials or certificates | Low – MAC address can be spoofed | Medium – depends on portal credentials |
| Use Case | Corporate endpoints, laptops, domain-joined PCs | Printers, IP phones, IoT devices without supplicant support | Guest access, contractor devices, BYOD onboarding |
| Protocol | IEEE 802.1X (EAP variants like EAP-TLS, PEAP) | RADIUS (MAC as username/password) | RADIUS (with redirect ACL) |
| Fallback Capability | First attempt; can fall back to MAB if no response | Can fall back to WebAuth if configured | Last resort if MAB or 802.1X fails |
| Switch Configuration | authentication port-control auto + dot1x settings | mab command on interface | Redirect ACL + authentication host-mode multi-auth |
| Certificate Requirement | Yes (server-side, sometimes client-side) | No | Yes (for HTTPS portal) |
| User Interaction | None after supplicant setup | None | Yes – user must log in via browser |
| Visibility in ISE | Live Logs → Auth Method shows dot1x | Live Logs → Auth Method shows mab | Live Logs → Auth Method shows webauth |
| Example CLI Verification | show authentication sessions int Gi1/0/1 details | show authentication sessions | show authentication sessions + browser redirect test |
FAQ: Wired 802.1X vs MAB vs WebAuth
1. What’s the main difference between 802.1X, MAB, and WebAuth in Cisco ISE?
- 802.1X: Uses EAP over LAN (EAPOL) for authentication; requires a supplicant on the endpoint.
- MAB: Uses the endpoint’s MAC address as the identity; no supplicant needed.
- WebAuth: Redirects unauthenticated clients to a captive portal for login.
- They differ in security level (802.1X is strongest) and use cases.
2. When should I use MAB over 802.1X?
Use MAB for non-supplicant devices like printers, IP phones, cameras, or IoT devices that cannot run 802.1X clients.
3. Can I run 802.1X and MAB on the same interface?
Yes — configure the switch port for multiple authentication methods (often called multi-auth or MDA). The switch will try 802.1X first, then fall back to MAB if no EAPOL response is detected.
4. Is WebAuth only for wireless?
No. WebAuth works on wired networks too. For wired guests, the switch applies a redirect ACL to send HTTP/HTTPS traffic to the ISE Guest Portal.
5. How can I verify which method was used for authentication?
In ISE: Operations → RADIUS → Live Logs → Check the “Authentication Method” column.
On the switch:
show authentication sessions interface Gi1/0/1 details
Look for “Current Method” (e.g., dot1x, mab, webauth).
6. What’s the order of operations if all three methods are configured?
Typically:
- 802.1X attempt.
- If no EAPOL response → MAB attempt.
- If MAB fails and WebAuth is configured → redirect to WebAuth portal.
7. Can 802.1X, MAB, and WebAuth all point to different authorization policies in ISE?
Yes. You can create separate Policy Set rules in ISE to apply different VLANs, ACLs, or downloadable ACLs (dACLs) based on the authentication method.
8. How do I troubleshoot when a device is stuck in WebAuth redirect?
- Verify the redirect ACL on the switch matches the ACL name in ISE’s Authorization Profile.
- Check ISE Live Logs for failed authorization conditions.
- Confirm DNS resolution for the redirect FQDN from the endpoint.
- Make sure the endpoint’s browser accepts the portal certificate.
9. Do I need certificates for all three methods?
- 802.1X: Usually requires server certificates (EAP-TLS also needs client certs).
- MAB: No certificates required.
- WebAuth: Requires a server certificate for the portal (HTTPS).
10. How can I validate 802.1X, MAB, and WebAuth on the CLI and GUI?
CLI on Switch:
show authentication sessions show authentication sessions interface Gi1/0/1 details debug dot1x all debug authentication all
ISE GUI:
- Go to Operations → RADIUS → Live Logs to view authentication type, result, and applied policy.
- Check Operations → Reports → Endpoints and Users for historical data.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Today’s lab covered how to configure, validate, and troubleshoot wired 802.1X, MAB, and WebAuth in Cisco ISE.
By mastering this, you can design adaptive, secure wired access that fits both corporate and guest needs without compromising security.
Upgrade Your Skills – Start Today
Master Cisco ISE Like a Pro in 4 Months!
Join Instructor-Led CCIE Security Mastery Program — the ultimate deep-dive into ISE, Firepower, VPNs, ASA, and more.
- Live labs on VMware/EVE-NG
- Real-world troubleshooting scenarios
- 1:1 mentorship and career guidance
- Limited seats — enroll now: Click Here to See the Full Course Outline
- Transform from engineer to security architect in just 120 days.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![Your First Step into IPv6: Address Types, Labs, CLI & Real-World Use Cases [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-IPV6.jpg)

![CAPWAP Overview – Bridging Access Points and Controllers [CCNP Enterprise] _networkjourney](https://networkjourney.com/wp-content/uploads/2025/07/CAPWAP-Overview-–-Bridging-Access-Points-and-Controllers-CCNP-Enterprise.png)