[Day 21] Cisco ISE Mastery Training: Identity Source Sequences Explained
Table of Contents
Introduction
When deploying Cisco ISE in a real-world enterprise, authentication decisions often depend on multiple identity sources—like Active Directory (AD), internal ISE users, LDAP, or RADIUS token servers. But what happens when you need to query them in a specific order? That’s where Identity Source Sequences (ISS) come into play.
In wired/wireless 802.1X and MAB authentication, ISS decides which source gets queried first and what happens if it fails. This control is critical for reducing login delays, falling back to backups, and ensuring uptime in NAC deployments.
Problem Statement
In many organizations:
- Employees authenticate via AD.
- Guest accounts are stored in the internal ISE database.
- IoT/MAC devices are stored in an endpoint identity group.
If you don’t control the order of checks:
- AD failures can block guest or IoT logins.
- Slow queries to unused sources cause login delays.
- Troubleshooting becomes a nightmare.
Solution Overview
Cisco ISE’s Identity Source Sequence feature lets you:
- Create a priority list of authentication sources.
- Control failover behavior (stop after first match or continue).
- Combine multiple databases into a single logical authentication source.
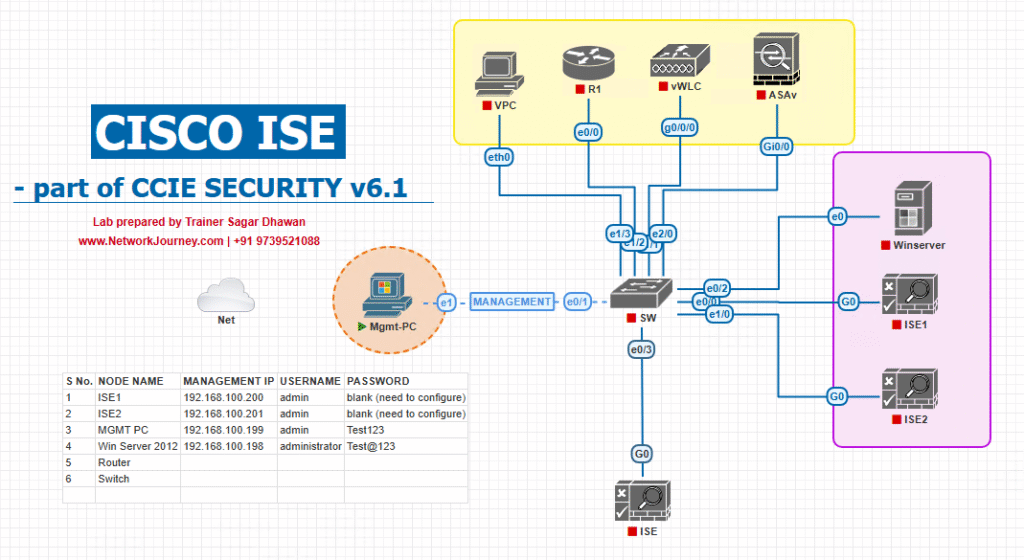
Sample Lab Topology
Text Description:
We’ll simulate a small enterprise environment in EVE-NG with:
- ISE Node (VMware/EVE-NG)
- Catalyst Switch (for wired access)
- Windows AD/DNS Server
- Test Endpoints (Windows laptop, guest device, IoT MAC device)
Lab Setup:
- ISE connected to AD via LDAP/Kerberos.
- Internal users in ISE internal DB.
- IoT MAC addresses stored in ISE endpoint database.
Topology Layout:
Step-by-Step GUI Configuration Guide
Step 1 – Create Identity Sources
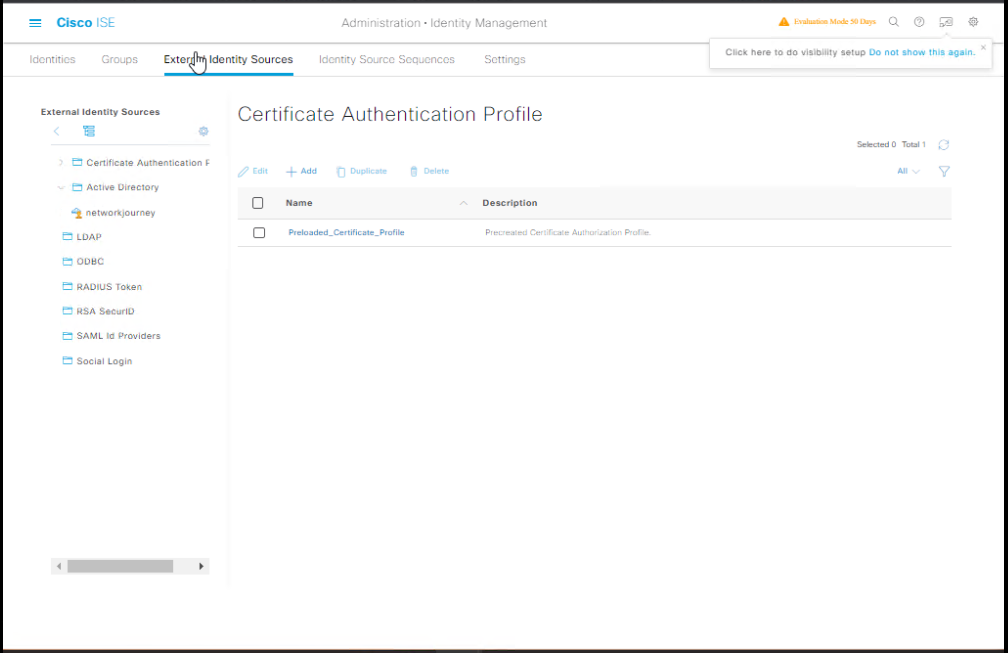
- Go to Administration → Identity Management → External Identity Sources.
- Configure Active Directory:
- Join domain:
corp.local - Check connectivity: [Screenshot: AD Join Success]
- Join domain:
- Add Internal ISE User (for guest):
- Go to Administration → Identity Management → Identities.
- Add MAC addresses for IoT devices:
- Work Centers → Network Access → Identities → Endpoints
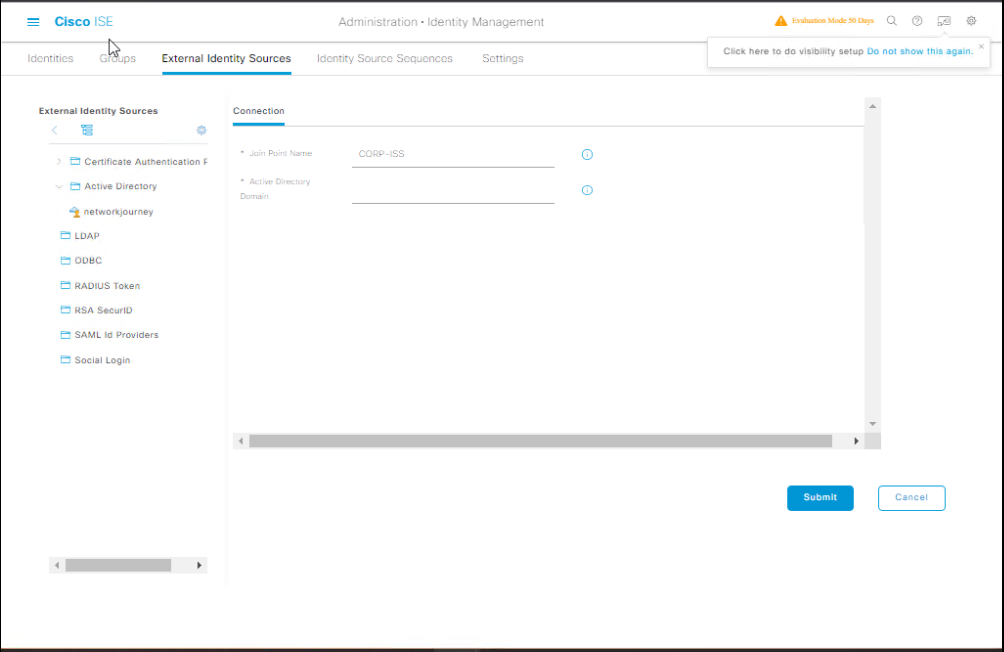
Step 2 – Create Identity Source Sequence
- Go to Administration → Identity Management → Identity Source Sequences.
- Click Add.
- Name:
Corp-ISS - Add sources in this order:
- Active Directory
- Internal Users
- Internal Endpoints
- Enable “Stop if found” (to avoid unnecessary queries).
- Save & Apply.
[Screenshot: ISS Order Config]
Step 3 – Apply in Authentication Policy
- Go to Policy → Policy Sets.
- Edit the desired policy set.
- In Authentication Policy, select Identity Source Sequence =
Corp-ISS.
[Screenshot: Policy Set Mapping]
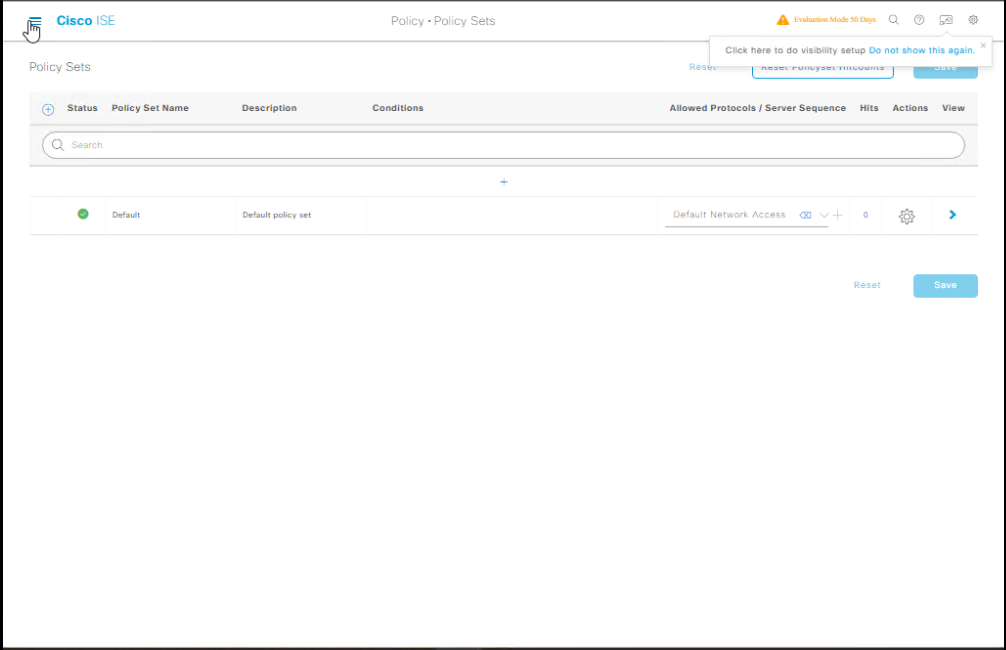
- Save & Deploy.
Step 4 – CLI Verification (Switch)
On the access switch:
show authentication sessions show authentication sessions interface Gi1/0/10 details
Check the Server Policies line for the chosen identity source.
Validation Steps
GUI:
- In ISE → Operations → RADIUS Live Logs, see the Identity Source column.
- Test by connecting:
- AD user → should match Active Directory.
- Guest → should match Internal Users.
- IoT device → should match Internal Endpoints.
CLI:
debug radius authentication
Look for:
[ISE] Authentication source: Active Directory [ISE] Authentication source: Internal Users
FAQs
1. What is an Identity Source Sequence in Cisco ISE?
An Identity Source Sequence is a logical list of identity stores (like AD, LDAP, Internal DB, or certificate-based repositories) that Cisco ISE checks in a specific order during authentication. It allows fallback to alternative sources if the primary source is unreachable or doesn’t have the user/device.
2. Why should I use an ISS instead of pointing directly to one identity source?
If you directly point to AD and AD goes down, authentication will fail entirely. An ISS ensures that if AD is unavailable, ISE will automatically try the next source, such as Internal Users or Internal Endpoints, reducing downtime.
3. Can I mix internal and external sources in the same ISS?
Yes. For example:
- Primary: Active Directory
- Secondary: Internal Users (for guest accounts)
- Tertiary: Internal Endpoints (for MAB)
This is the most common deployment strategy.
4. What happens if a user exists in multiple sources in the ISS?
ISE stops checking as soon as it finds a matching identity, provided the “Stop if found” option is enabled. If not enabled, it will check all sources and use the first match in priority order.
5. Does the order of sources affect authentication speed?
Yes. If the first source is slow to respond or unreachable, authentication delays occur until ISE times out before moving to the next source. Best practice: put the most frequently used and fastest sources first.
6. Can ISS be used for both wired and wireless 802.1X authentication?
Absolutely. ISS is independent of the access type. You can apply it to any authentication policy in ISE, including wired, wireless, and VPN authentications.
7. How do I troubleshoot when ISS is not working as expected?
- Check RADIUS Live Logs in ISE for the “Identity Source” column.
- Enable
debug radius authenticationon the switch/WLC. - Verify that the external source (like AD) is reachable via System → Logging → Test Connectivity.
8. Can ISS be used for MAC Authentication Bypass (MAB)?
Yes. For MAB, you can use ISS where the primary source is the Internal Endpoints database, with fallback to other sources if the MAC address is not found.
9. What’s the difference between an ISS and multiple separate authentication rules?
Multiple authentication rules can reference different sources, but that approach is less flexible and requires more policy maintenance. ISS lets you have one policy rule that can query multiple sources in a controlled order.
10. What is the best practice order for ISS in enterprise deployments?
- First: AD (for corporate users)
- Second: Internal Users (for guest/fallback accounts)
- Third: Internal Endpoints (for IoT/MAB devices)
- Avoid placing rarely-used or slow sources first to minimize delays.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Identity Source Sequences may look simple, but they’re one of the most powerful tools in Cisco ISE for resilient, flexible, and optimized authentication workflows. Correct configuration prevents unnecessary downtime and helps maintain seamless user experience.
Upgrade Your Skills – Start Today
Ready to master Cisco ISE and secure enterprise networks like a pro?
I run a focused 4-month, live, instructor-led CCIE Security training covering Cisco ISE, ASA, Firepower, VPNs, and more — with hands-on labs, real-world scenarios, and lifetime access to recordings.
- Limited seats — Enrollment Open Now!
- Full course outline → https://course.networkjourney.com/ccie-security/
Join now to get direct mentorship, interview prep, and real-world deployment case studies.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



