[Day 53] Cisco ISE Mastery Training: Wireless Posture Assessment
Table of Contents
Introduction
Wireless posture assessment lets Cisco ISE validate endpoint health (AV/EDR, firewall, encryption, OS patch) before granting trusted access—on the same SSID. Using Cisco Secure Client (AnyConnect) with the Posture module, ISE can dynamically redirect, provision the agent, run checks, remediate, and then CoA users into the correct access class (Compliant vs Non-Compliant) with VLAN/dACL/SGT.
Problem Statement
Common problems in WLANs:
- Infected or unpatched devices gaining full access.
- BYOD/corporate laptops inconsistent in AV/firewall status.
- Security policies ignored due to lack of continuous verification.
- Heavy operational overhead to manually check and quarantine endpoints.
We need automated, recurring, identity + health gating—before devices reach sensitive apps.
Solution Overview (What you’ll build)
- Enable ISE Posture Service and create Client Provisioning Policy to deploy Cisco Secure Client + Posture.
- Create Posture Requirements (AV running/updated, Firewall ON, Disk Encryption).
- Build Authorization Profiles for Unknown → redirect to CPP, Non-Compliant → remediation access, Compliant → full access.
- Configure WLC 9800-CL for AAA Override and a pre-posture redirect ACL.
- Validate with ISE Live Logs, Posture audit, and WLC CLI.
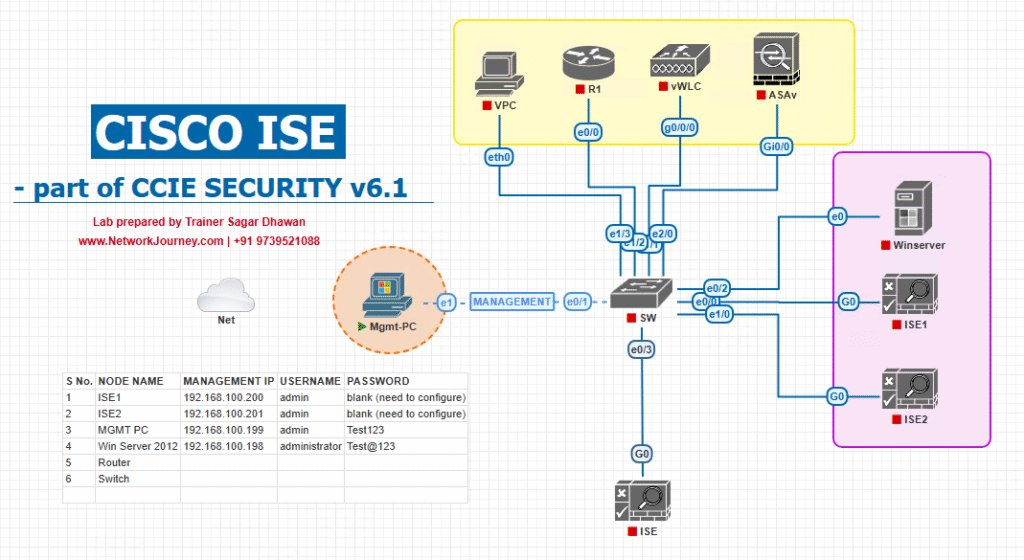
Sample Lab Topology
Platform (VMware/EVE-NG)
- Cisco ISE 3.x (PAN/PSN on one VM for lab)
- Cisco WLC 9800-CL (or AireOS 8.10+)
- Catalyst switch (SVIs + DHCP helper)
- Remediation servers: ISE, DNS/DHCP, Windows Update/WSUS (optional), AV update URLs
- Endpoints: Windows 11 laptop (primary), macOS (optional), iOS/Android (posture agent not supported—use MDM for mobile compliance)
Topology Layout:
Step-by-Step GUI Configuration Guide (with validation)
PREREQS
- Time/NTP & DNS aligned (ISE/WLC/clients).
- WLC added in ISE: Administration > Network Resources > Network Devices (RADIUS secret).
- On the switch: trunk allows target VLANs; SVIs & ip helper-address configured.
- Download Cisco Secure Client (AnyConnect) packages + Posture module and OPS/Compliance modules to your ISE (files ready on your admin PC).
A) ISE — Enable Posture Service & Feed
- Enable Posture on PSN
- Administration > System > Deployment > (Select PSN) > Edit
- Check Enable Posture Service → Save (services restart).
[Screenshot: ISE Deployment – Posture Service]
- (Optional) Feed Service for Posture/AV updates
- Administration > System > Settings > Feed Service → Enable.
[Screenshot: ISE Feed Service]
- Administration > System > Settings > Feed Service → Enable.
B) ISE — Client Provisioning (Deploy Cisco Secure Client + Posture)
- Upload Client/Modules
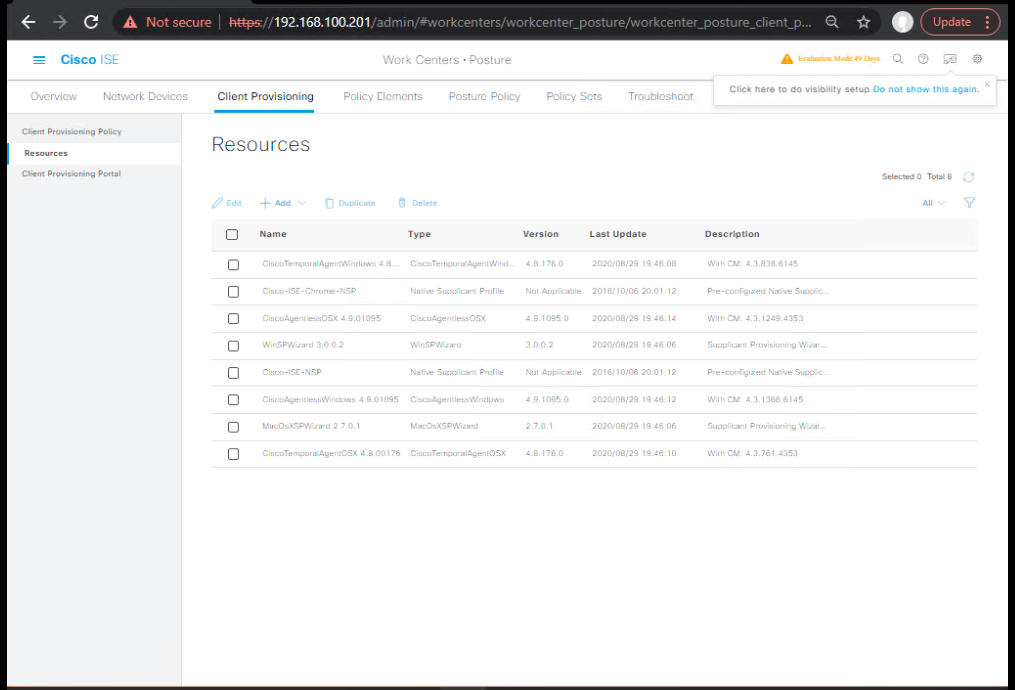
- Work Centers > Posture > Client Provisioning > Resources
- Add → upload:
- Cisco Secure Client (AnyConnect) Core (Win .pkg/.iso or web-deploy .pkg)
- Posture Module
- Compliance Module / OPS files (Windows).
[Screenshot: Client Provisioning Resources]
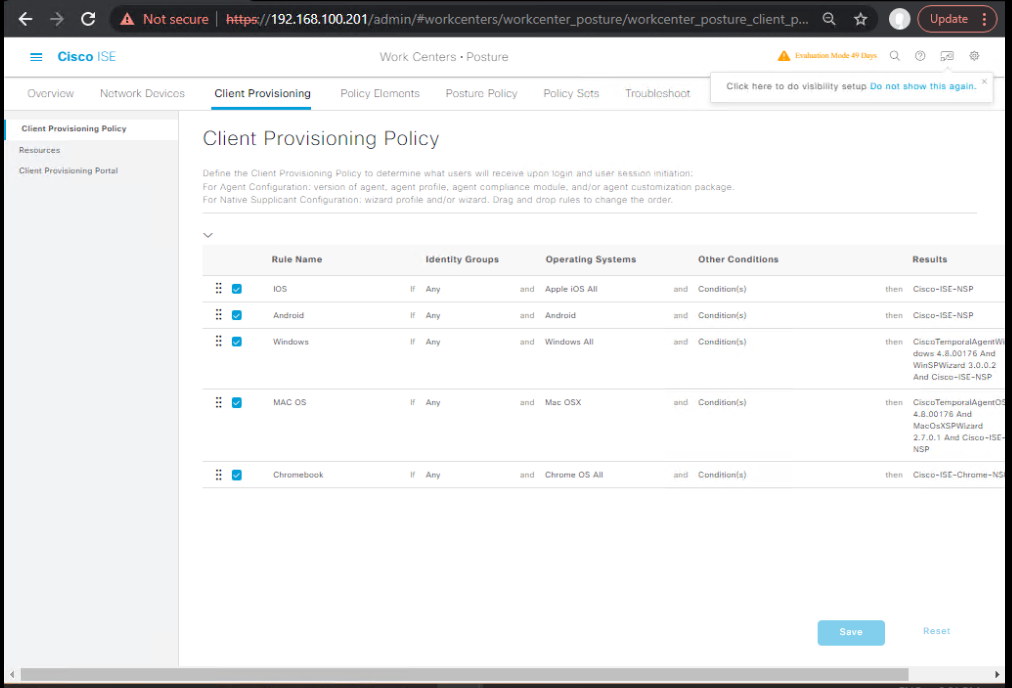
- Create Client Provisioning Policy
- Work Centers > Posture > Client Provisioning > Client Provisioning Policy > Add
- Conditions:
OS = Windows - Result: Cisco Secure Client + Posture + (Compliance Module version)
- Conditions:
- Repeat for macOS if used.
[Screenshot: Client Provisioning Policy]
- Work Centers > Posture > Client Provisioning > Client Provisioning Policy > Add
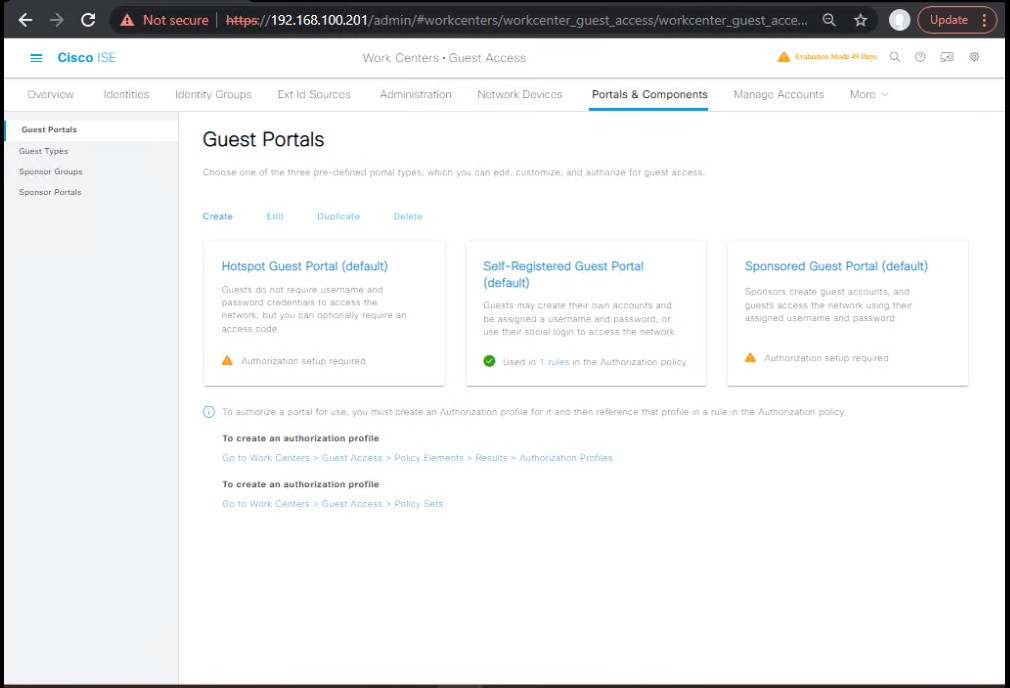
- Customize Client Provisioning Portal (CPP)
- Work Centers > Guest/Portals & Components > Portals > Client Provisioning
- Brand text/logo, verify Allowed Hosts (ISE FQDN, update URLs).
[Screenshot: Client Provisioning Portal]
C) ISE — Posture Requirements & Policy
- Define Posture Requirements
- Work Centers > Posture > Posture Requirements > Add
- Example requirements:
- Windows Firewall = Enabled (Win)
- Antivirus = Installed & Running (vendor-agnostic)
- AV Definition Age < 7 days
- Disk Encryption (BitLocker) = On
- Add Remediation steps where applicable (start service, prompt, URL to WSUS/AV).
[Screenshot: Posture Requirement Editor]
- Example requirements:
- Work Centers > Posture > Posture Requirements > Add
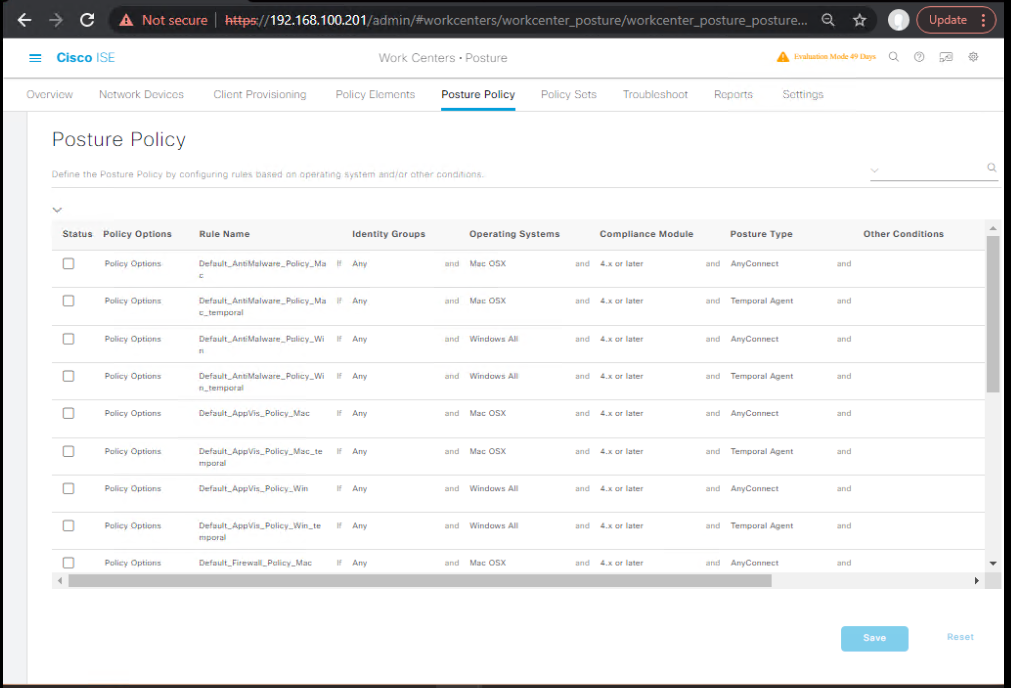
- Posture Policy
- Work Centers > Posture > Posture Policy
- Add rules per OS:
- If OS = Windows 10/11 → Apply (Firewall, AV, AV-Age, BitLocker)
- Actions: Compliant / Non-Compliant / Unknown outcomes feed Authorization.
[Screenshot: Posture Policy Table]
D) ISE — Authorization Profiles (Unknown / Remediate / Compliant)
- Create Redirect ACL on WLC (named) (we’ll do WLC GUI in section E; name it
ACL-PREPOSTURE). - Authorization Profiles → Policy > Policy Elements > Results > Authorization > Authorization Profiles > Add:
- AP-POSTURE-UNKNOWN-REDIRECT
- Common Tasks → ACL (Airespace-ACL-Name):
ACL-PREPOSTURE - Advanced Attributes Settings (Cisco AV-Pair):
url-redirect=https://<ISE_FQDN>:8443/guestportal/gateway?sessionId=...&action=cppurl-redirect-acl=ACL-PREPOSTURE
- (This forces HTTP/HTTPS to CPP to install Cisco Secure Client Posture)
[Screenshot: AuthZ Profile – URL Redirect]
- Common Tasks → ACL (Airespace-ACL-Name):
- AP-POSTURE-NONCOMPLIANT-REMEDIATE
- DACL or Airespace ACL:
ACL-REMEDIATE(permits ISE, WSUS, AV updates, DNS/DHCP/NTP; blocks corp apps) - Optional Recheck Timer (posture re-eval).
[Screenshot: AuthZ Profile – Remediation Access]
- DACL or Airespace ACL:
- AP-POSTURE-COMPLIANT-ACCESS
- VLAN/dACL/SGT for full corporate access.
[Screenshot: AuthZ Profile – Compliant Access]
- VLAN/dACL/SGT for full corporate access.
(If your 9800 image supports true dACLs for WLAN, you can return a dACL instead of Airespace ACLs.)
E) WLC 9800-CL — WLAN, AAA Override, Redirect ACL
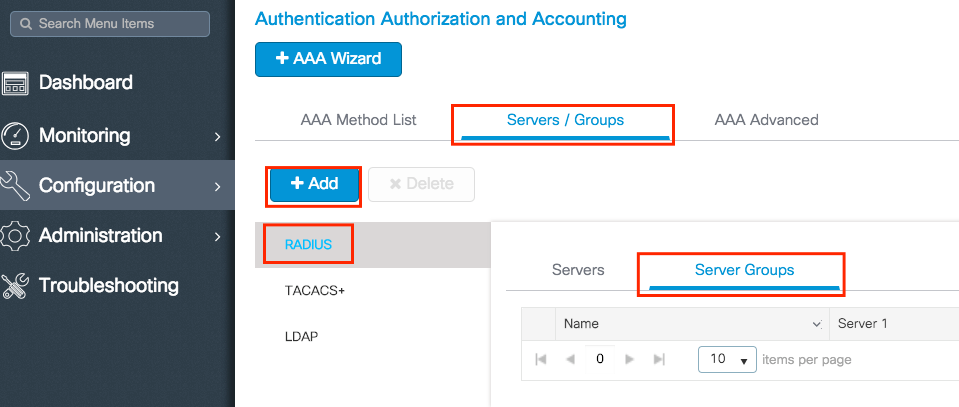
- RADIUS servers
- Configuration > Security > AAA > Servers > RADIUS → Add ISE for Auth & Accounting.
[Screenshot: WLC RADIUS Servers]
- Configuration > Security > AAA > Servers > RADIUS → Add ISE for Auth & Accounting.
- Create Redirect (Pre-Posture) ACL
- Configuration > Security > ACL > Add (IPv4) → Name:
ACL-PREPOSTURE - Rules (example):
permit udp any any eq 53(DNS)permit udp any any eq 67(DHCP client)permit udp any any eq 68(DHCP server)permit tcp any host <ISE_IP> eq 8443(CPP)permit tcp any host <ISE_IP> eq 443permit tcp any <WSUS/AV ranges> eq 80,443deny ip any any(redirect applies on denies)
[Screenshot: WLC ACL Editor]
- Configuration > Security > ACL > Add (IPv4) → Name:
- WLAN & Policy Profile
- Configuration > Tags & Profiles > WLANs →
CORP-POSTURE- Security > AAA: ISE for Auth/Acct (interim updates ON).
- Policy Profiles > :
- AAA Override = Enabled
- Central Switching = Enabled (for controller-switched)
- Default VLAN (guest/remediate fallback).
[Screenshot: Policy Profile – AAA Override]
- Configuration > Tags & Profiles > WLANs →
- Tagging
- Map WLAN ↔ Policy Profile via Policy Tag and push to APs.
[Screenshot: Policy Tag Mapping]
- Map WLAN ↔ Policy Profile via Policy Tag and push to APs.
9800 CLI Validation
show wlan summary show wireless client mac <client-mac> detail ! Look for: Policy Profile, AAA Override, IPv4 ACL (ACL-PREPOSTURE) during Unknown state show access-lists summary show access-list ACL-PREPOSTURE show logging | inc AAA|RADIUS|url-redirect|CoA debug wireless mac <client-mac> events debug aaa all undebug all
AireOS notes
- Create named ACLs and AAA Override on WLAN (Advanced).
- ISE returns
Airespace-ACL-Name+ URL-Redirect AV pairs.
F) ISE — Authorization Policy (Posture-Driven)
Policy > Policy Sets > (Wireless-Posture)
- Authentication: 802.1X EAP-TLS/PEAP (and MAB if you also have CWA guest).
- Authorization (top-down):
- IF
PostureStatus = Unknown→ AP-POSTURE-UNKNOWN-REDIRECT - IF
PostureStatus = NonCompliant→ AP-POSTURE-NONCOMPLIANT-REMEDIATE - IF
PostureStatus = Compliant→ AP-POSTURE-COMPLIANT-ACCESS - Else → Quarantine
[Screenshot: ISE Authorization Policy – Posture Conditions]
- IF
ISE Validation (GUI)
- Operations > RADIUS > Live Logs → entry shows Authorization Profile + Posture Status.
- Click Details → Posture tab shows requirements hit/miss.
[Screenshot: Live Logs – Posture Tab]
G) End-to-End Client Flow (What you should see)
- Client joins SSID → hits Unknown rule → gets URL-redirect &
ACL-PREPOSTURE. - Browser auto-redirects to CPP → Cisco Secure Client posture package offered.
- Agent installs and runs checks → reports to ISE.
- ISE marks Compliant or Non-Compliant and sends CoA.
- Client receives new Authorization Profile: full access (Compliant) or remediation (Non-Compliant).
Client Validation
- Cisco Secure Client UI > Posture: Status = Evaluating → Compliant/Non-Compliant.
- Windows: check services (Firewall ON), AV status center, BitLocker status.
- Logs:
C:\ProgramData\Cisco\Cisco Secure Client\logs\(posture/agent).
ISE Validation
- Operations > Live Logs: AuthC success → Posture status.
- Operations > Reports > Posture: Compliance reports & trend.
- Context Visibility > Endpoints: Posture state per endpoint.
WLC Validation
- During Unknown:
IPv4 ACL = ACL-PREPOSTURE - After CoA & Compliant: new VLAN/dACL/SGT as per final profile.
FAQs (Wireless Posture Assessment)
1. What is the purpose of Wireless Posture Assessment in Cisco ISE?
Wireless Posture Assessment ensures that endpoints connecting over Wi-Fi comply with the organization’s security policies (e.g., antivirus installed, OS patched, firewall enabled). ISE checks device compliance using the AnyConnect Secure Endpoint / NAC Agent before granting full access.
2. Which Cisco ISE license is required for Wireless Posture Assessment?
You need the Plus License for posture services. Base and Apex licenses are not sufficient for posture enforcement.
3. How does Cisco ISE perform posture checks on wireless devices?
ISE uses the AnyConnect ISE Posture Module installed on the client machine. Once the user connects, the NAC Agent communicates with ISE to run the posture checks. ISE then applies a CoA (Change of Authorization) to move the client from a quarantine VLAN or DACL to the compliant VLAN/DACL.
4. What happens if a device fails the posture assessment?
Non-compliant devices are placed in a remediation VLAN or given limited network access via a quarantine DACL. They are presented with remediation resources (e.g., update antivirus, enable firewall) via a web page before reattempting posture validation.
5. How is Wireless Posture different from Wired Posture in ISE?
The core posture mechanism is the same; however:
- Wired posture often uses switch port-based redirection.
- Wireless posture uses WLC redirection ACLs and CoA events to change WLAN access states.
6. Can posture assessment be performed without the AnyConnect NAC Agent?
No — for real-time posture compliance, the NAC Agent is required. There is a passive profiling option without the agent, but it’s not considered full posture enforcement.
7. How do I test posture assessment in a lab?
- Install AnyConnect with ISE Posture Module on a wireless endpoint.
- Connect to a WLAN configured for posture.
- Validate in ISE Live Logs that the posture state changes from Unknown → Non-Compliant → Compliant.
- Use a WLC debug command like
debug client <mac>to track redirection and CoA events.
8. How do I configure redirection ACLs for posture on a WLC?
Example on a 9800 WLC:
ip access-list extended REDIRECT_ACL permit tcp any any eq 80 permit tcp any any eq 443 deny ip any any
This ACL is applied in the WLAN configuration for the initial session before posture is complete.
9. How do I monitor posture assessment results in ISE?
- Operations > RADIUS > Live Logs to see authentication/posture status.
- Operations > Reports > Posture for historical compliance reports.
- Context Visibility > Endpoints to see endpoint compliance state.
10. Can posture checks be customized for different wireless SSIDs?
Yes — you can create different Policy Sets in ISE for each SSID, applying separate posture policies based on conditions like SSID name, endpoint group, or device type. This allows different compliance rules for corporate vs guest BYOD wireless networks.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
You now have a closed-loop posture flow: redirect → provision agent → assess → remediate → CoA. Pair this with VLAN/dACL/SGT for layered enforcement and use reports to prove continuous compliance. Your fastest RCA path is: Live Logs (Posture tab) → Agent logs → WLC client detail.
Upgrade Your Skills – Start Today
Turn this posture lab into a production-grade, audit-ready deployment with expert coaching.
Join 4-Month, Instructor-Led CCIE Security & Cisco ISE Mastery:
- Live builds: Posture, BYOD, Guest, Profiling, dACL/SGT, pxGrid
- EVE-NG topologies, graded lab workbooks, solution keys
- Done-for-you templates: Redirect ACLs, Posture Requirements, Remediation dACLs, CoA runbooks
- Career mentorship, recordings, mock interviews
Free Lead Magnet (on sign-up): Posture Kick-Start Pack
- Prebuilt Client Provisioning Policy, Windows posture requirements, WLC ACLs, and validation checklist
- Get the full syllabus & reserve your seat: https://course.networkjourney.com/ccie-security/
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![[Day 55] Cisco ISE Mastery Training: EAP-TLS Wireless Certificate Authentication](https://networkjourney.com/wp-content/uploads/2025/08/Day-55-–-Cisco-ISE-Mastery-Training-EAP‑TLS-Wireless-Certificate-Authentication.png)
![NETCONF vs RESTCONF – Choosing the Right Protocol for Network Automation [CCNP ENTERPRISE]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/07/NETCONF-vs-RESTCONF-–-Choosing-the-Right-Protocol-for-Network-Automation-1.png)
