[Day 73] Cisco ISE Mastery Training: SGT Exchange Protocol (SXP) Configuration
Table of Contents
Introduction
Scalable Group Tags (SGTs) are the foundation of Cisco TrustSec—labels that identify “who” a packet belongs to, decoupled from IP or VLAN. The Scalable Group Tag eXchange Protocol (SXP) is the control-plane that ships IP↔SGT bindings from where they’re learned (typically access edges) to where they must be enforced (firewalls, distribution/cores, data centers).
When devices can’t insert inline SGTs in the data plane (no hardware tagging) or you need centralize/redistribute bindings, SXP fills the gap. In ISE-driven deployments, ISE can be the SXP route reflector (hub)—ingesting bindings from speakers and re-publishing to listeners—so your enforcement points always know “host 10.10.10.50 ⇒ SGT = HR”.
Problem Statement
- Edge learns identity, core enforces security. Access switches/WLCs authenticate users and learn SGTs, but your enforcement is on distribution/cores, DC switches, ASA/FTD, or firewalls that don’t see 802.1X.
- No inline tagging? Some platforms/paths can’t carry SGT in the frame.
- Policy needs “who,” not “where.” IPs/VLANs churn; SGTs should remain stable.
Challenge: Reliably propagate up-to-date IP↔SGT to all enforcement points—at scale, with convergence, and with validation.
Answer: Use SXP with ISE as a hub. Edges act as speakers (export bindings), enforcement devices act as listeners (import bindings), and ISE optionally speaks/listens to redistribute + visualize.
Solution Overview (ISE role)
- Central TrustSec brain: Define SGTs, build policy, and visualize bindings.
- SXP Topology (Hub-and-Spoke):
- Speakers: Access switches (and optionally ISE) export IP↔SGT.
- Listeners: DC/Distribution switches, firewalls (ASA/FTD), or any device that needs bindings.
- ISE Hub: Listens from edges, republishes to listeners (one-to-many).
- Transport: TCP (default port 64999), SXP version negotiation (commonly v4).
- Result: Enforcement points receive authoritative IP↔SGT mappings to apply SGACLs/Group-Based Policy.
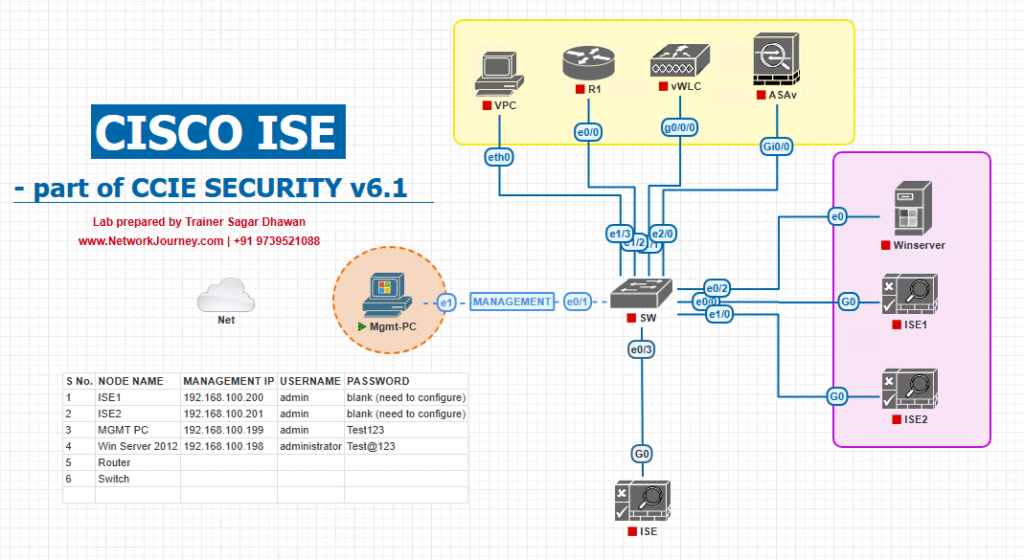
Sample Lab Topology
Emulator: VMware ESXi + EVE-NG
ISE: ISE 3.x (PAN+MnT in one VM)
Switches:
- C9300-A (Access): 802.1X/MAB, SXP speaker to ISE.
- C9500-D (Distribution): SXP listener (imports bindings for enforcement).
Firewall (optional): ASA/FTD as SXP listener.
WLC: 9800-CL in EVE-NG (clients authenticate to ISE; edge switch still the SXP speaker).
Endpoints: - Wired: Win10 VM (dot1x) + Printer (MAB).
- Wireless: Win11 laptop via WLC SSID.
IP sketch (mgmt/VLANs simplified):
Flow:
- Endpoints authenticate to ISE; access switch learns SGT.
- C9300-A exports IP↔SGT via SXP to ISE.
- ISE republishes to C9500-D and/or ASA/FTD.
- Listeners enforce SGACLs based on SGT.
Step-by-Step GUI + CLI Configuration Guide
A) Prereqs & Naming
- Time/NTP in sync across ISE & devices.
- RADIUS live (802.1X/MAB working).
- Define SGTs you’ll use: e.g., Employees (2), HR (10), Printers (15).
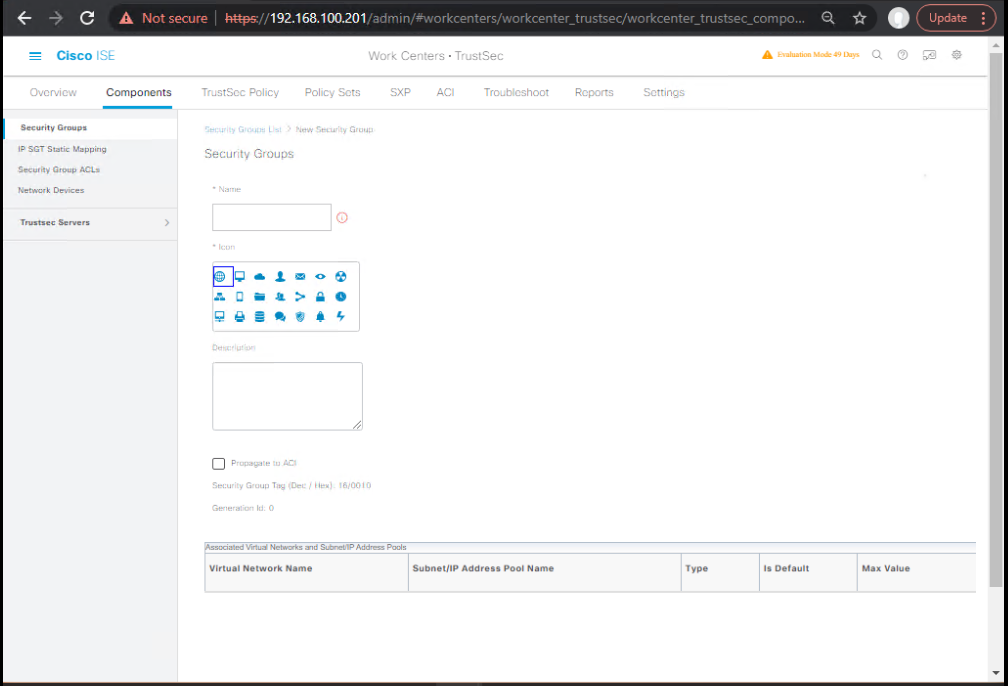
- ISE GUI: Work Centers → TrustSec → Components → Security Groups → Add
- [Screenshot: ISE SGTs List]
B) Enable TrustSec & SXP in ISE
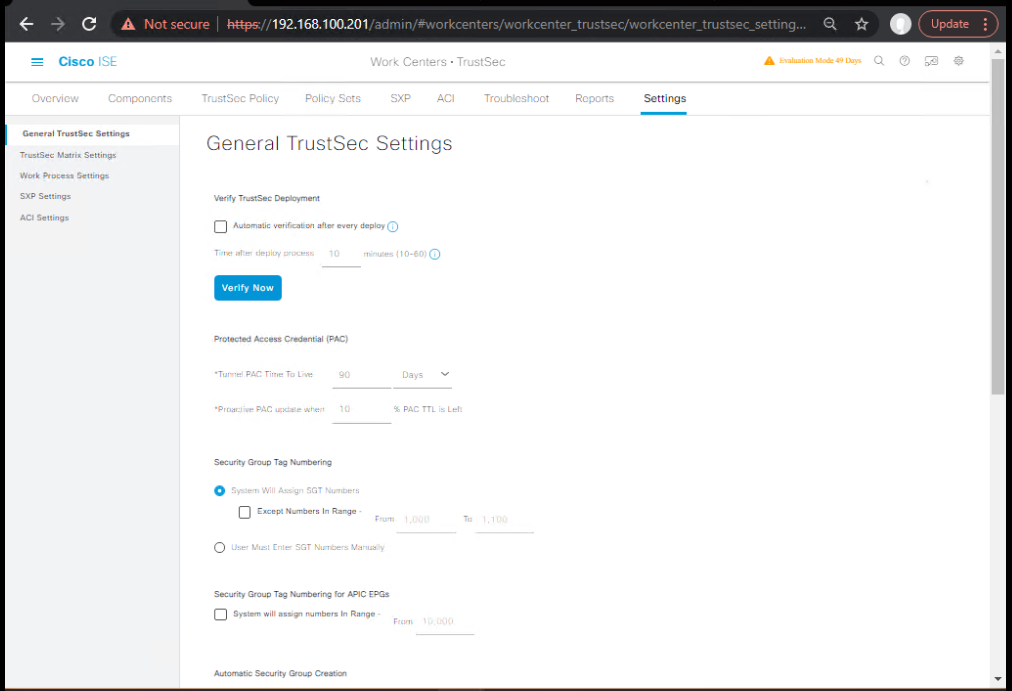
- Enable TrustSec services
- ISE GUI: Work Centers → TrustSec → Settings → General → Enable TrustSec.
- [Screenshot: ISE TrustSec General Settings]
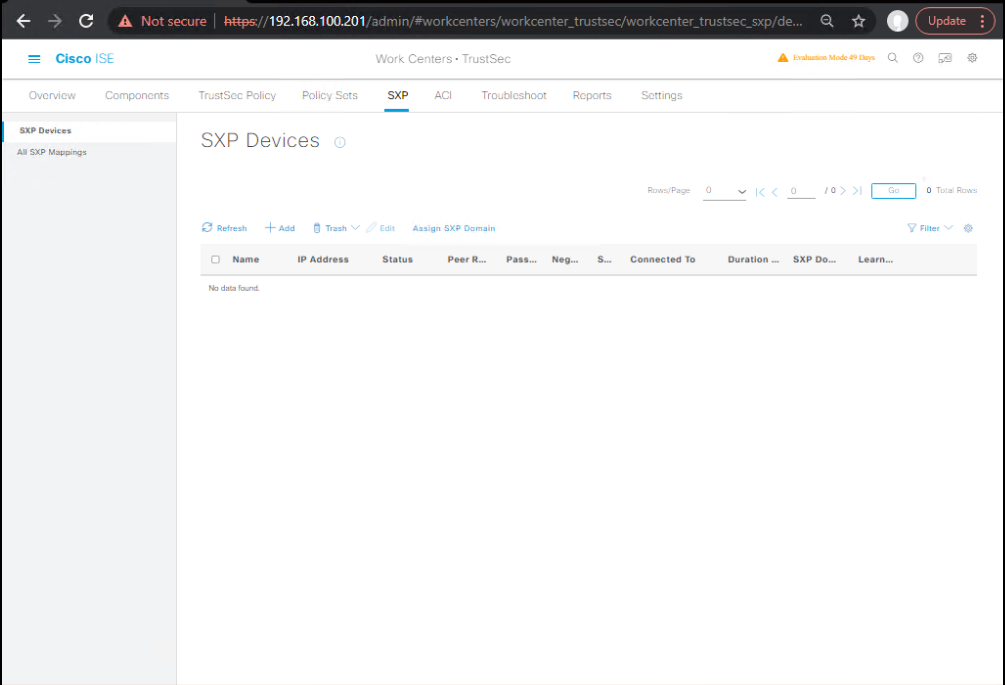
- SXP Global Settings
- Work Centers → TrustSec → SXP → Settings
- Confirm SXP State: Enabled, Default TCP Port: 64999 (change only if needed).
- Choose SXP Default Domain (e.g.,
DEFAULT). - [Screenshot: ISE SXP Settings]
C) Add Network Devices to ISE (for RADIUS & TrustSec)
- Add C9300-A & C9500-D
- Administration → Network Resources → Network Devices → Add
- Set IP, Device Type, RADIUS Shared Secret.
- Under TrustSec, check Enable TrustSec for the device.
- [Screenshot: ISE Network Device Add]
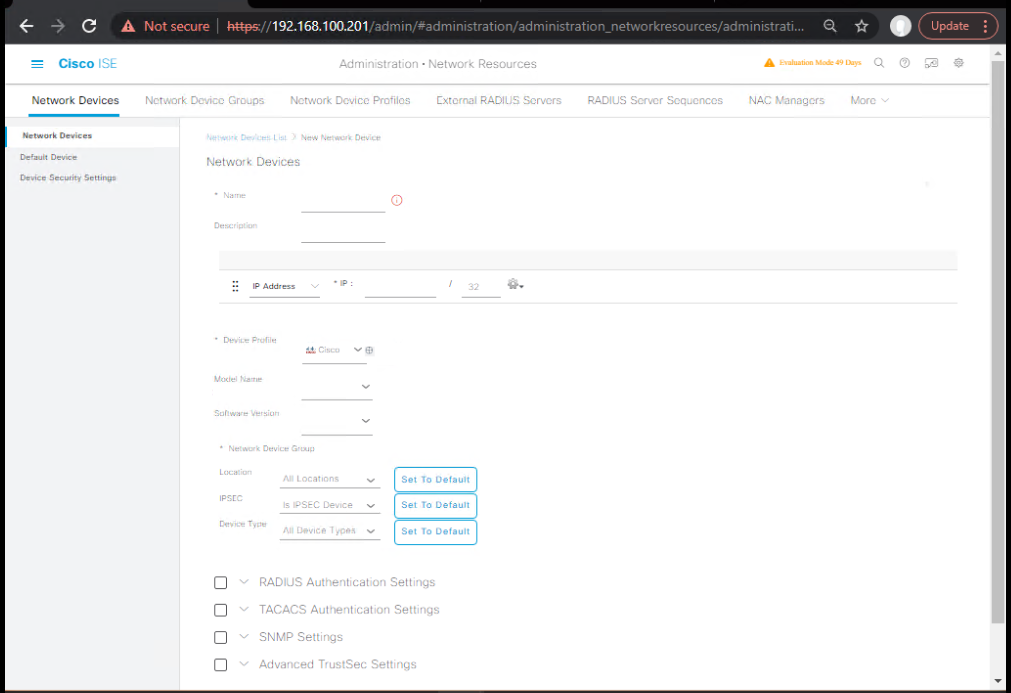
- (Optional) Add ASA/FTD similarly.
D) Configure SXP Peers in ISE
We’ll build ISE as hub with two directions:
- Listener toward the access switch (to ingest bindings).
- Speaker toward distribution/firewall (to redistribute bindings).
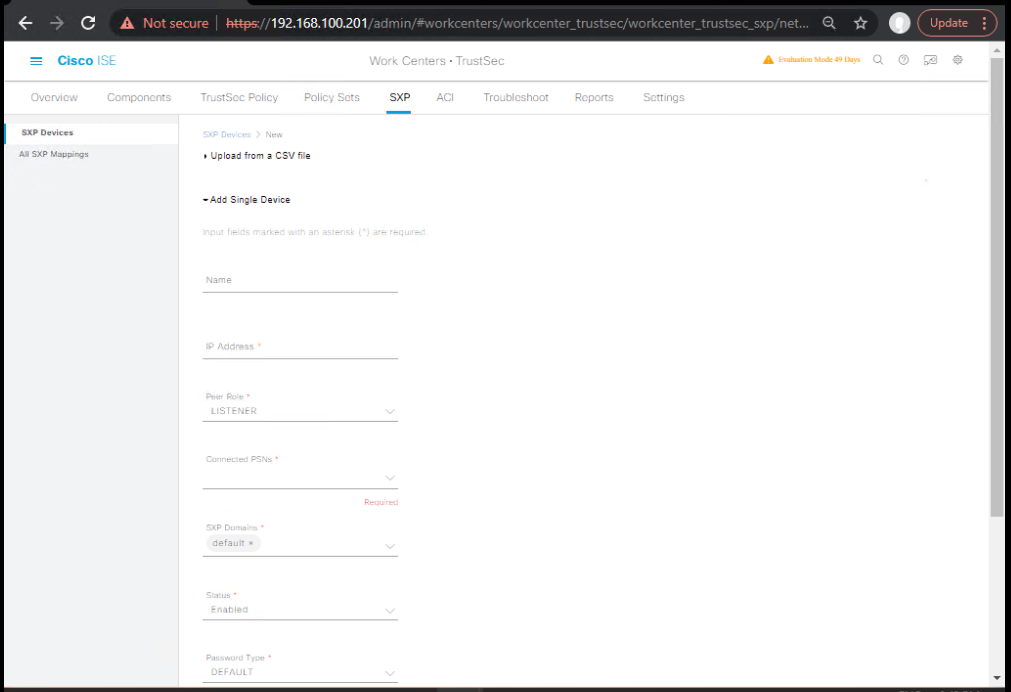
- Add SXP Device: C9300-A (ISE listens)
- Work Centers → TrustSec → SXP → SXP Devices → Add
- Name:
C9300-A - IP Address: Mgmt IP of the switch
- Connection Mode: Listener (ISE will listen)
- Password:
C!sco123(example; match on switch) - Version: Prefer v4 (or “Highest Available”)
- Domain:
DEFAULT - Save.
- [Screenshot: ISE Add SXP Device (Listener)]
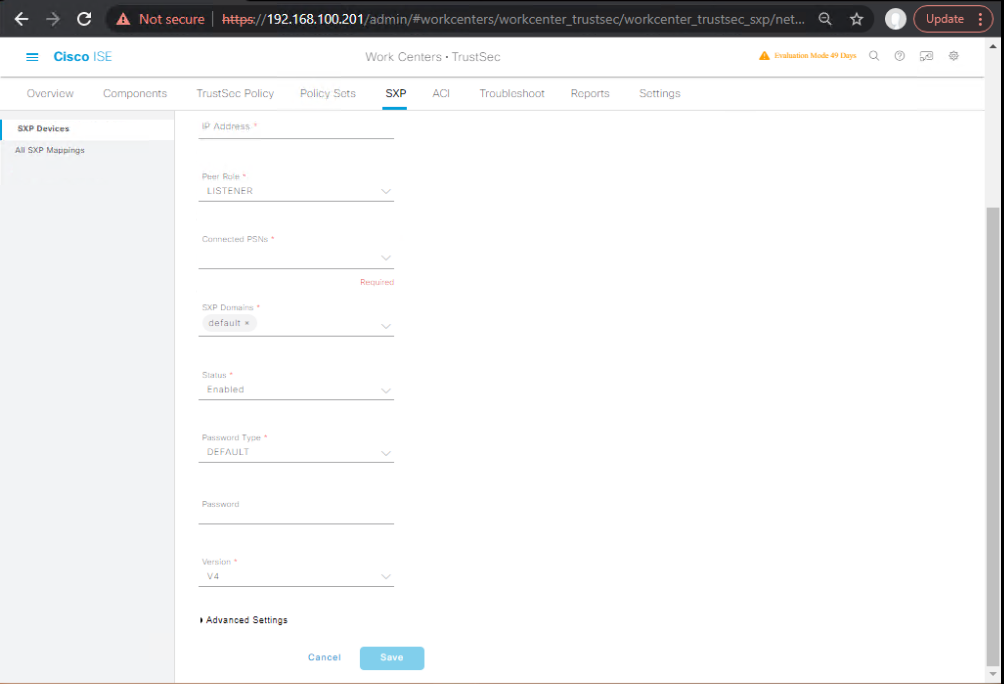
- Add SXP Device: C9500-D (ISE speaks)
- … → Add
- Name:
C9500-D - IP: Distribution switch
- Connection Mode: Speaker (ISE will speak to D-switch)
- Password:
C!sco123(match on C9500) - Version: v4
- Domain:
DEFAULT - Save.
- [Screenshot: ISE Add SXP Device (Speaker)]
- (Optional) ASA/FTD as Listener—repeat step 2 with firewall IP as Listener peer.
Tip: In ISE SXP Topology, confirm the adjacency states.
[Screenshot: ISE SXP Topology/Connections]
E) Create Static IP↔SGT (for lab validation)
Even before 802.1X flows, push a known binding to prove SXP works end-to-end.
- Work Centers → TrustSec → IP SGT Static Mappings → Add
- IP/Subnet:
10.10.20.50/32(your Win10 test host) - SGT:
Employees(2) - Description:
Lab test binding - Save.
- [Screenshot: ISE Add IP SGT Static Mapping]
- IP/Subnet:
Watch the Bindings counter on SXP devices after a few seconds/minutes.
F) Configure SXP on C9300-A (Speaker to ISE)
! Enable TrustSec/SXP feature-set conf t cts sxp enable cts sxp default source-ip 10.10.10.21 ! Optional: set default VRF if used ! cts sxp default vrf Mgmt ! Create SXP connection to ISE (ISE is Listener) cts sxp connection peer 10.10.10.10 password 0 C!sco123 mode speaker version 4 ! (Optional) tighten timers (example) ! cts sxp connection peer 10.10.10.10 hold-time 90 retry 30 end ! Validation show cts sxp connections show cts sxp summary show cts role-based sgt-map all show cts role-based sgt-map ip 10.10.20.50
Expected: SXP conn ON, State: UP, and binding table shows 10.10.20.50 -> Employees(2) locally (speaker advertises any mappings it has—static/dynamic).
If your mapping is created on ISE, C9300 won’t learn it back as speaker; that’s okay. Our enforcement listeners should learn it from ISE speaker adjacency.
G) Configure SXP on C9500-D (Listener from ISE)
conf t cts sxp enable cts sxp default source-ip 10.10.10.31 cts sxp connection peer 10.10.10.10 password 0 C!sco123 mode listener version 4 end ! Validation on listener show cts sxp connections show cts sxp summary show cts role-based sgt-map all show cts role-based sgt-map ip 10.10.20.50
Expected: You should see the mapping in the role-based sgt-map table on C9500-D (imported from ISE).
H) (Optional) SXP on ASA/FTD (Listener)
Use matching IP, password, port, and version. Verify with
show sxp connectionsand the SXP database/bindings command for your ASA/FTD version. Ensure the management interface can reach ISE and TCP/64999 is permitted.
I) Make Mappings Dynamic via 802.1X/MAB (Edge switch → ISE → SXP)
- Authorization Profiles (ISE):
- Policy → Policy Elements → Results → Authorization → Authorization Profiles → Add
- Include SGT = Employees (TrustSec attributes).
- [Screenshot: ISE Authorization Profile with SGT]
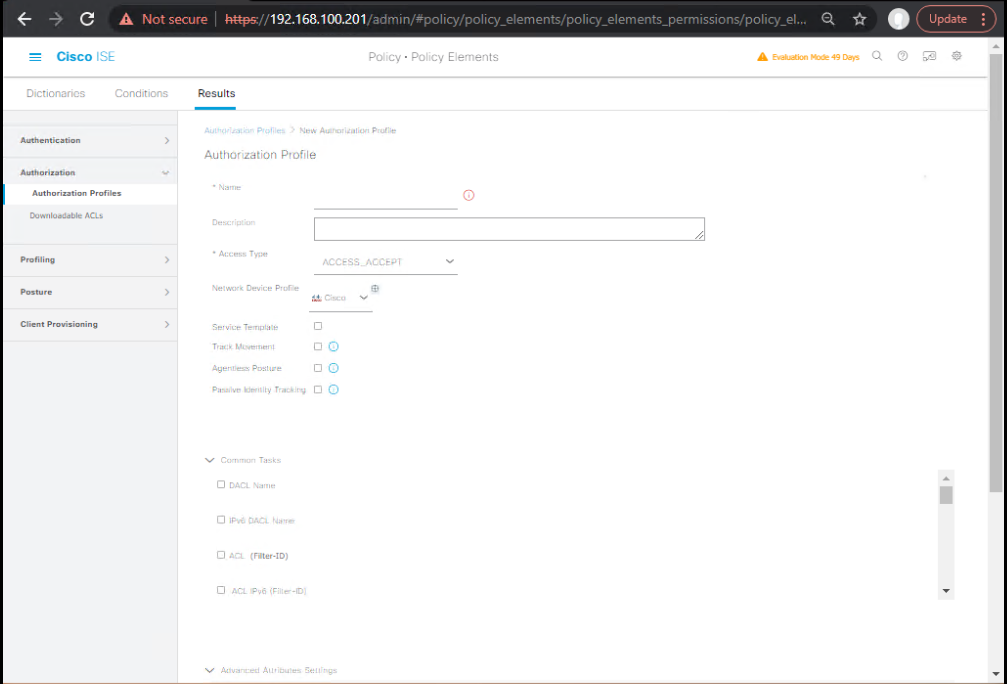
- Policy Set rule: Map matching endpoints to the above authz profile.
- [Screenshot: ISE Policy Sets Rule Mapping SGT]
- Connect Win10 and authenticate.
- On C9300-A, verify the endpoint got the SGT:
show authentication sessions interface Gi1/0/10 details show cts role-based sgt-map ip 10.10.20.50You should see an SGT assigned to the client. The switch (speaker) now exports this mapping to ISE via SXP, and ISE republishes to listeners.
J) End-to-End Validation Checklist (GUI + CLI)
On ISE (GUI):
- SXP → Connections: State Up for C9300-A (listener), C9500-D (speaker).
- [Screenshot: ISE SXP Connections Up]
- SXP → Bindings: Observe Binding Count increasing; search for
10.10.20.50.- [Screenshot: ISE SXP Bindings View]
- Context Visibility → Endpoints: Endpoint shows SGT.
- [Screenshot: ISE Endpoint with SGT]
On C9300-A (CLI):
show cts sxp connections show cts sxp summary show cts role-based sgt-map all | i 10.10.20.50 show authentication sessions
On C9500-D (CLI):
show cts sxp connections show cts role-based sgt-map all | i 10.10.20.50 show cts role-based sgt-map ip 10.10.20.50
(Optional) On ASA/FTD:
show sxp connections- View SXP database/bindings (command varies by release).
Traffic test (if SGACLs configured):
- From listener side, apply a simple SGACL permitting ICMP from
Employeesto a test server SGT; confirm ping success/deny as per policy. - On switches:
show cts role-based permissionsto see compiled SGACL matrices.
K) Hardening & Ops
- SXP Passwords: Use unique strong secrets per peer; limit SXP to mgmt VRF.
- Versioning: Prefer v4 where supported; otherwise pin to a mutually supported version.
- Scale: Keep ISE as hub; use multiple listeners downstream (DC, Firewalls).
- Visibility: ISE’s Bindings and SXP Topology are your NOC dashboards.
- Logging: Enable SXP syslogs; export ISE MnT logs to your SIEM.
- Timers: Tune hold/retry for faster convergence in labs; use defaults in prod unless justified.
C9300-A (Speaker to ISE):
conf t cts sxp enable cts sxp default source-ip 10.10.10.21 cts sxp connection peer 10.10.10.10 password 0 C!sco123 mode speaker version 4 end show cts sxp connections show cts role-based sgt-map all
C9500-D (Listener from ISE):
conf t cts sxp enable cts sxp default source-ip 10.10.10.31 cts sxp connection peer 10.10.10.10 password 0 C!sco123 mode listener version 4 end show cts sxp connections show cts role-based sgt-map all
ISE (GUI) Paths
- Enable TrustSec: Work Centers → TrustSec → Settings → General
- SXP Settings: Work Centers → TrustSec → SXP → Settings
- SXP Devices: Work Centers → TrustSec → SXP → SXP Devices → Add
- Static IP↔SGT: Work Centers → TrustSec → IP SGT Static Mappings → Add
- Policy Sets: Policy → Policy Sets → (your set) → Authorization rules
Sample IPs/passwords with you lab values. Keep TCP/64999 open between peers.
FAQs on Cisco ISE SXP
1. What is the main purpose of SXP in Cisco ISE?
SXP is a control-plane protocol that moves IP↔SGT bindings from one device (speaker) to another (listener). It’s needed when inline SGT tagging is not possible (older switches, firewalls, routed domains). Without SXP, downstream enforcement points (like ASA/FTD or core switches) wouldn’t know which IP belongs to which SGT.
2. How is SXP different from inline SGT propagation?
Inline tagging inserts the SGT directly into the Ethernet/Frame header as packets traverse the network. This is ideal but requires hardware support end-to-end.
SXP, by contrast, doesn’t touch live traffic—it just ships mapping tables (control-plane). Use SXP when hardware tagging is unavailable or to distribute bindings to remote enforcement points.
3. Can Cisco ISE act as both a Speaker and Listener at the same time?
Yes. ISE often acts as an SXP Hub:
- Listener for access devices (to receive IP↔SGT).
- Speaker toward distribution/core/firewalls (to redistribute).
This avoids building a full mesh of adjacencies among switches.
4. Which SXP version should I use (v1, v2, v3, v4)?
Always use the highest version supported by both peers.
- v4 is preferred—it carries IPv6 and multiple enhancements.
- If one peer only supports v2, both sides must downgrade.
Check withshow cts sxp connectionson switches to confirm negotiated version.
5. What TCP port does SXP use and can I change it?
Default is TCP/64999. You can change it globally in ISE (SXP settings) or per peer if devices require customization. But in most designs, keep the default for simplicity.
6. Why don’t I see my endpoint bindings on the listener switch even though the session shows “Up”?
Common causes:
- Wrong mode (speaker vs listener reversed).
- Wrong domain in ISE vs device.
- Endpoint did not actually get an SGT (check
show authentication sessions). - Binding only exists in ISE as static mapping, but you haven’t redistributed it.
- Password mismatch → adjacency shows “On” but no real data exchange.
7. What is the difference between static and dynamic IP↔SGT bindings?
Static bindings: Manually configured in ISE for lab/legacy devices (good for testing).
Dynamic bindings: Created automatically when endpoints authenticate via 802.1X/MAB and ISE assigns an SGT.
In production, you should rely mostly on dynamic bindings, but keep a few static for printers, IoT, or bootstrap tests.
8. How can I validate if SXP mappings are working end-to-end?
On ISE GUI:
- Work Centers → TrustSec → SXP → Bindings (search IP).
On Access switch (speaker): show cts sxp connections(should be Up)show cts role-based sgt-map ip <endpoint_IP>
On Distribution/Firewall (listener):- Same
show cts role-based sgt-map ip <endpoint_IP>should display the SGT.
9. What happens if the SXP session goes down? Do I lose all bindings?
If the SXP session drops, previously learned bindings stay cached until the hold-time timer expires (default 120 seconds). If session remains down beyond this, the listener flushes its binding table. That’s why reliable TCP connectivity and timer tuning matter.
10. Can SXP scale in large networks? What’s the recommended design?
Yes, but don’t do full-mesh adjacencies. The best practice is:
- ISE as a hub.
- Access switches (speakers) send bindings to ISE.
- ISE re-advertises to distribution/core/firewalls (listeners).
This scales better, centralizes visibility, and avoids configuration sprawl. For very large enterprises, you can deploy multiple ISE Policy Service Nodes (PSN) for SXP load sharing.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- SXP = identity plumbing. It moves IP↔SGT knowledge to the places that need it.
- ISE as hub simplifies scale and operations.
- Build confidence with static test mappings, then move to dynamic (802.1X/MAB).
- Always validate on ISE GUI and device CLIs; trust but verify.
Upgrade Your Skills – Start Today
Level up fast with Fast-Track to Cisco ISE Mastery Pro.
I run a focused 4-month, instructor-led program blending real-world labs, design reviews, and job-ready scenarios—perfect if you’re aiming for CCIE Security-grade mastery.
What you’ll get:
- 0→1 ISE foundations, TrustSec/SGT/SXP deep dives
- Production-style policy sets, profiling, posture, pxGrid integrations
- Brownfield migrations, troubleshooting playbooks, interview prep
- Live cohort + recordings, lab workbooks, review quizzes
Seats are limited. Join the interest list and get the detailed course outline: https://course.networkjourney.com/ccie-security/
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088


![QOS Diagnose & Fix Network Performance Issues [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/QOS_Diagnose_Fix-Network-Performance-Issues_networkjourney.png)
