[Day 82] Cisco ISE Mastery Training: Integrating Cisco FMC
Table of Contents
Introduction
Cisco Firepower Management Center (FMC) is the brain behind Cisco’s Next-Generation Firewalls (NGFWs). By integrating FMC with Cisco ISE using pxGrid, you allow FMC to consume contextual identity and group information (like usernames, endpoints, SGTs, compliance posture, threat scores).
This enables dynamic policy enforcement on the firewall — e.g., automatically blocking a compromised endpoint based on ISE Threat Intelligence feeds or posture.
This integration is a core part of Threat-Centric NAC in modern Zero Trust architectures.
Problem Statement
Enterprises often face:
- Firewalls enforcing policies only on IP addresses, not knowing who the user/device is.
- Security gaps because user identity changes dynamically (DHCP leases, roaming, VPN logins).
- No automated response to infected endpoints → security teams manually block IPs after incidents.
Solution Overview
By integrating Cisco FMC ↔ Cisco ISE:
- pxGrid shares contextual data (usernames, device type, SGT, posture compliance).
- ANC (Adaptive Network Control) actions in ISE can trigger dynamic blocking/quarantine in FMC.
- FMC can enforce identity-based access policies instead of just IP-based.
Outcome: Real-time, identity-driven security enforcement at the firewall layer.
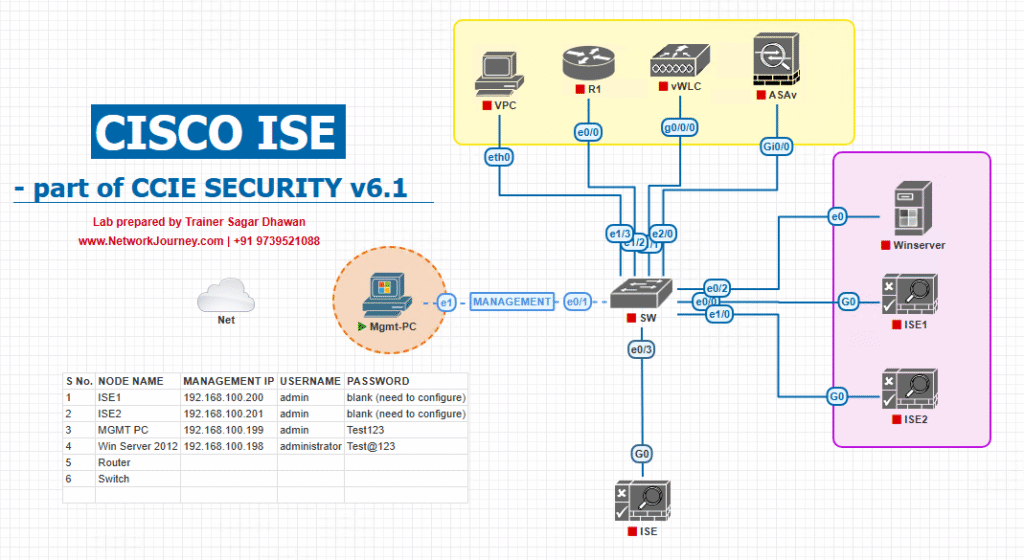
Sample Lab Topology
Environment (can be built in VMware Workstation / EVE-NG):
- Cisco ISE 3.2 (VMware ESXi / EVE-NG)
- Cisco FMC 7.x (VMware ESXi / EVE-NG)
- Cisco FTD Firewall (managed by FMC)
- Switch (L2 Access) with 802.1X enabled endpoints
- Wireless Controller (optional) for wireless integration
- Endpoints: Windows 10 laptop, Ubuntu client
- Active Directory for user authentication
Diagram:
Step-by-Step GUI & CLI Configuration Guide
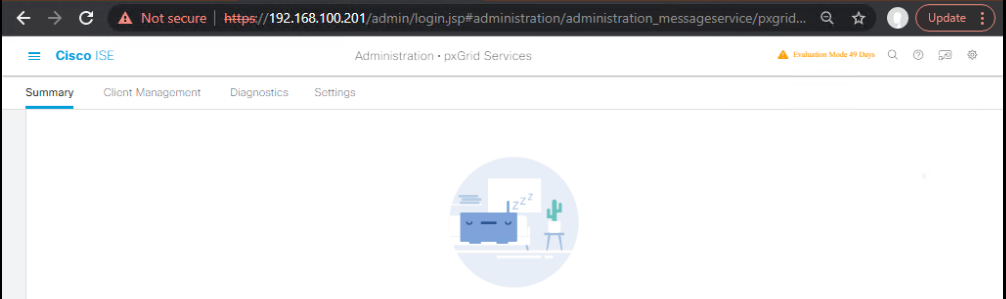
Step 1: Enable pxGrid in Cisco ISE
- Navigate: Administration > pxGrid Services.
- Enable pxGrid.
- Check Enable ISE node for pxGrid.
- Configure certificates (use ISE internal CA or external PKI).
- [Screenshot: ISE pxGrid Services Screen]
- Validate pxGrid status:
ise/admin# show application status ise | include pxGrid pxGrid Infrastructure : running pxGrid Publisher : running
Step 2: Register FMC as pxGrid Client in ISE
- In FMC, go to:
System > Integration > Identity Sources > Identity Services Engine. - Add new ISE node:
- Enter ISE FQDN/IP.
- Import ISE pxGrid certificate.
- Test connectivity.
- [Screenshot: FMC Add ISE Integration Window]
- On ISE → approve pxGrid client request:
Administration > pxGrid Services > Clients → Approve FMC.
Step 3: Configure ISE to Export Context to FMC
- In ISE: Administration > System > Deployment > pxGrid Services.
- Select Session Directory and Identity Groups → Enable sharing.
- Verify sessions being published:
Operations > pxGrid > Sessions.
Step 4: Configure FMC to Consume ISE Data
- FMC: Policies > Access Control > Identity Sources.
- Select ISE pxGrid as Identity Source.
- Create Access Control Rule:
- Condition: User Group = “Finance” (from AD via ISE)
- Action: Allow/Monitor
- Condition: Security Group = “Quarantined” (from ISE ANC)
- Action: Block
- [Screenshot: FMC Access Control Identity Rule]
Step 5: Validation
GUI Validation
- In ISE → Operations > Live Sessions
- Verify endpoint session details shared with pxGrid.
- In FMC → Analysis > Users > Active Sessions
- Verify user/endpoint identity received from ISE.
CLI Validation (ISE)
ise/admin# show logging application pxgrid.log | include FMC ise/admin# show pxGrid clients
CLI Validation (FMC CLI into FTD)
> show users > show conn detail | include <username>
Step 6: Trigger Test Scenario (ANC Quarantine)
- In ISE:
- Go to Operations > Active Sessions.
- Select endpoint → ANC → Quarantine.
- [Screenshot: ISE ANC Action Screen]
- Validate in FMC:
- Go to Analysis > Connections.
- Traffic from quarantined host should be blocked.
Step 7: Troubleshooting
- If FMC not visible in ISE pxGrid Clients → Check certificate trust.
- If FMC not receiving users → Verify ISE pxGrid Session Directory is enabled.
- If ANC not reflecting in FMC → Verify FMC is subscribed to ANC topics.
Step 8: Rollback / Deregister FMC from ISE
- In FMC: Remove ISE integration under Identity Sources.
- In ISE: Administration > pxGrid Services > Clients → Remove FMC client.
- CLI check:
ise/admin# show pxGrid clients | include FMC
Cisco ISE ↔ FMC Troubleshooting (Advanced with PCAP & TLS Analysis)
11. Verify pxGrid Traffic with Packet Captures
Use Case: FMC cannot connect to pxGrid on ISE — want to confirm network path & TLS handshake.
ISE CLI Capture:
ise/admin# tcpdump -i eth0 host <FMC_IP> and port 8910 -vvv -s0 -w /mnt/disc/pxgrid_tls.pcap
FMC CLI Capture (FTD):
> system support capture-traffic interface mgmt match ip host <ISE_IP> eq 8910 > show capture-traffic
Analysis in Wireshark:
- Open
pxgrid_tls.pcap. - Look for:
- Client Hello (FMC → ISE)
- Server Hello (ISE → FMC)
- Certificate Exchange
- TLS Key Exchange Success
If you see RST packets, check firewall/ACL between FMC & ISE.
If Alert: Unknown CA, re-issue pxGrid certs.
12. Debug pxGrid TLS Handshake Failures
Wireshark Filters:
tcp.port == 8910 ssl.handshake ssl.alert
Common TLS Failures:
Handshake Failure: Wrong certificate or CA not trusted.Unknown CA: Import ISE CA into FMC trust store.Expired Certificate: Reissue pxGrid certs.
Fix:
Re-generate pxGrid certificate in ISE:
ise/admin# crypto pki enroll ise-pxgrid
Re-import into FMC → System → Integration → Identity Sources → Certificates.
13. pxGrid HA Debugging (Multiple ISE Nodes)
Symptom: FMC connected to primary ISE, but fails when pxGrid client tries secondary node.
CLI Check (ISE):
ise/admin# show application status ise | include pxGrid pxGrid Publisher: running pxGrid Subscriber: running
Verify pxGrid Node Registration:
show pxGrid clients
Fix:
- Register FMC with pxGrid VIP (Load Balanced), not individual nodes.
- Ensure pxGrid services enabled on all ISE PSNs.
- Sync FMC with each ISE pxGrid node.
14. Identity Events Not Publishing to FMC
Symptom: FMC connected, TLS OK, but no user session updates.
Verification:
- Capture pxGrid Event Publish from ISE:
ise/admin# tcpdump -i eth0 port 8910 and dst <FMC_IP> -w pxgrid_events.pcap - Open in Wireshark → Check if JSON payloads are exchanged after TLS handshake.
If empty:
- ISE not publishing Session Directory events.
- Fix → GUI: Administration > pxGrid Services > Enable Session Directory.
15. Debug ANC (Adaptive Network Control) Flow
Symptom: ISE applies ANC (quarantine), but FMC does not enforce.
Flow Validation:
- ISE sends pxGrid ANC → FMC.
- FMC pushes access control → FTD.
- FTD enforces block.
ISE CLI Logs:
ise/admin# tail -f /var/log/ise/pxgrid.log | grep ANC
FMC CLI (FTD Debug):
> system support firewall-engine-debug > show users
PCAP on ISE:
tcpdump -i eth0 port 8910 and host <FMC_IP> -A
Look for ANC JSON messages (quarantine, unquarantine).
Fix:
- Enable ANC Actions in FMC Identity Source.
- Ensure FMC subscribed to
com.cisco.ise.config.anctopic.
16. Debugging Slow Updates (Latency >5 min)
Symptom: Identity updates delayed in FMC.
Wireshark Check:
- Filter pxGrid messages:
tcp.port == 8910 and ip.addr == <ISE_IP> - Look at Keep-Alive Interval in JSON.
Fix:
- Tune pxGrid Session Directory push interval:
ise/admin# conf t ise/admin(config)# pxgrid config push-interval 30 - Ensure NTP sync:
ise/admin# show ntp fmc> show ntp
17. Debug FMC FTD Enforcement Logs
Symptom: Identities visible in FMC, but policies not applied.
FTD CLI:
> show users > show running-config access-control
FMC Logs:
- System → Integration → Identity Sources → Test ISE Connection
Fix:
- Ensure access policy rule matches SGT/User.
- Enable Real-Time Event Updates in FMC ISE integration.
18. pxGrid Syslog-Level Debugging
If all else fails, crank pxGrid debug logs:
ISE CLI:
ise/admin# debug application pxgrid all ise/admin# tail -f /var/log/ise/pxgrid.log
FMC CLI (FTD):
> expert > tail -f /var/log/messages | grep pxgrid
Use this for lab root cause analysis.
Troubleshooting Scenarios with Steps
Scenario 1: FMC not connecting to ISE pxGrid
Step 1: Verify Connectivity
ise/admin# ping <FMC_IP> ise/admin# nc -zv <FMC_IP> 8910
- FMC GUI → System > Integration > Identity Sources > Test Connection
[Screenshot: FMC ISE Test Connection Status]
Expected: TCP 8910 open.
Fix: If blocked → check firewall/ACL.
Scenario 2: TLS Handshake Failure
Step 1: Run packet capture on ISE
ise/admin# tcpdump -i eth0 host <FMC_IP> and port 8910 -w /mnt/disc/pxgrid_tls.pcap
Step 2: Open in Wireshark
- Filter:
ssl.handshake - Validate Client Hello / Server Hello exchange.
Step 3: Validate Certificates
- ISE GUI → Administration > System > Certificates > System Certificates
- FMC GUI → Objects > Certificates > Trusted CAs
[Screenshot: FMC Trusted CA Import]
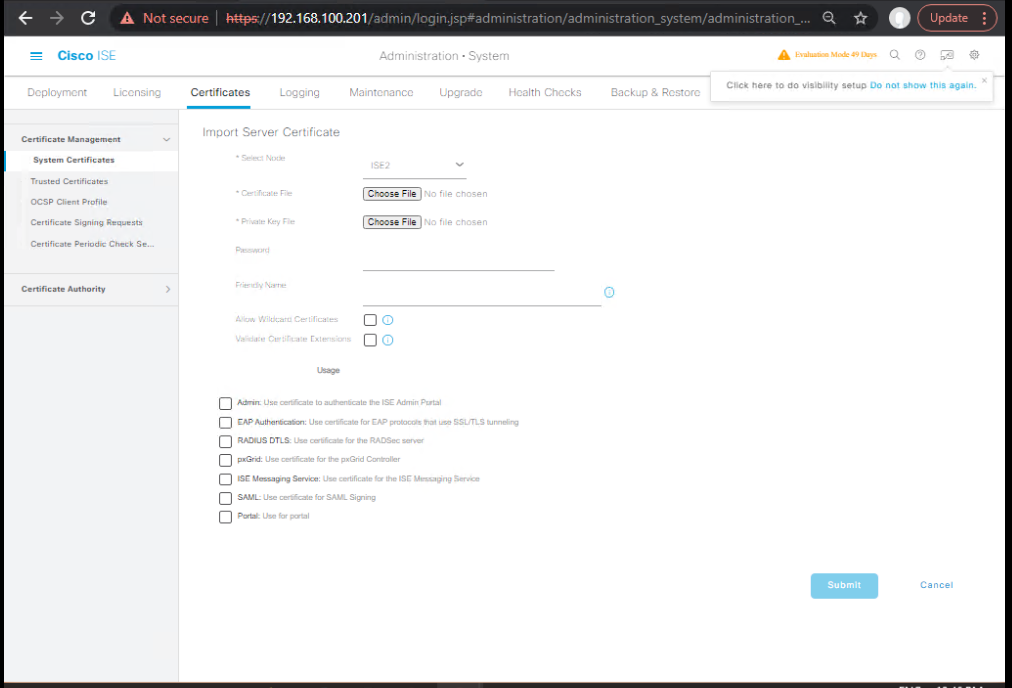
Fix: Import ISE CA into FMC trust store.
Scenario 3: No Identity Events in FMC
Step 1: Check pxGrid Events
ise/admin# tail -f /var/log/ise/pxgrid.log | grep session
Step 2: Confirm pxGrid Topics
ise/admin# show pxgrid clients
Step 3: FMC GUI Validation
- Analysis > Users > Active Sessions
[Screenshot: FMC User Sessions Dashboard]
Fix: Enable Session Directory in ISE →Administration > pxGrid Services > Enable Session Directory
Scenario 4: ANC Policy Not Enforced
Step 1: Apply ANC in ISE GUI
- Operations > Adaptive Network Control > Quarantine
[Screenshot: ISE ANC Policy Applied]
Step 2: Check pxGrid ANC Publish
ise/admin# tail -f /var/log/ise/pxgrid.log | grep ANC
Step 3: FMC Validation
- FMC GUI → Analysis > Users > Identity Events
- CLI on FTD:
> show users > show running-config access-control
Fix: Enable ANC subscription in FMC Identity Integration.
Scenario 5: FMC Sync Delay (>5 min)
Step 1: NTP Validation
ise/admin# show ntp fmc> show ntp
Step 2: Tune pxGrid Push Interval
ise/admin(config)# pxgrid config push-interval 30
Step 3: FMC GUI
- System > Integration > Identity Sources > pxGrid Settings
[Screenshot: FMC pxGrid Interval Settings]
Validation Checklist
- FMC → ISE connectivity test (TCP 8910)
- pxGrid client registered on ISE (
show pxgrid clients) - TLS handshake validated with Wireshark
- Active sessions visible in FMC dashboard
- ANC quarantine reflected in FTD CLI (
show users) - NTP sync across ISE, FMC, FTD
Pro Tips:
- Always keep Wireshark running with filters:
tcp.port == 8910(pxGrid)ssl.alert(TLS issues)
- Collect ISE pxGrid logs + FMC integration logs in every lab → great for showing students real packet flows.
- Use tcpdump inline in class to show live ANC JSON publish from ISE → FMC.
FAQs – Cisco ISE + FMC Integration
1. Do I need pxGrid licenses to integrate FMC with ISE?
Yes . To integrate FMC with ISE, pxGrid must be enabled on ISE. Starting ISE 2.4, pxGrid 2.0 is included by default in the Base license, so you don’t need a separate license anymore. Older ISE versions (pre-2.4) required Plus license for pxGrid.
2. Can FMC consume both User Identity and SGT (Security Group Tags) from ISE?
Yes. FMC can consume username → IP mappings and SGTs from ISE via pxGrid.
- User Identity comes from ISE Session Directory.
- SGTs come from ISE TrustSec pxGrid publisher.
This enables both identity-based policies and TrustSec-based policies in FMC.
3. How do I verify if FMC is successfully registered as a pxGrid client in ISE?
In ISE GUI:
- Navigate to Administration > pxGrid Services > Clients.
- Look for FMC → Status = Approved & Connected.
In CLI:
ise/admin# show pxGrid clients
You should see FMC with connected = true.
4. What certificates are required for ISE ↔ FMC pxGrid integration?
- ISE pxGrid Certificate must be trusted by FMC.
- FMC pxGrid Client Certificate must be trusted by ISE.
Tip: Use ISE’s built-in CA to generate pxGrid client certificates for FMC. Import into FMC truststore.
5. If ISE goes down, will FMC still enforce identity policies?
Partially.
- FMC will continue using cached identity mappings until the session timeout.
- New sessions will fall back to IP-only enforcement until ISE pxGrid is restored.
Recommendation: Always deploy ISE HA pair to avoid gaps.
6. How do I test ANC (Adaptive Network Control) between ISE and FMC?
- On ISE: Go to Operations > Live Sessions > Select Endpoint > ANC → Quarantine.
- On FMC: Check Analysis > Connections → The quarantined host should be dropped/blocked.
CLI validation on FTD:
> show users > show conn detail | include <username/IP>
The connection should show quarantined.
7. Can FMC trigger actions back into ISE (like ANC)?
No . Integration is unidirectional:
- ISE → publishes identity, posture, SGT, ANC actions.
- FMC → consumes them and enforces policies.
FMC cannot directly tell ISE to quarantine; it only enforces based on ISE signals.
8. What’s the difference between using AD integration on FMC vs. ISE → FMC pxGrid?
- Direct AD integration with FMC only gives usernames → IP mappings (no posture/SGTs).
- ISE integration provides rich context: usernames, device posture, security group, compliance status, threat scores, ANC.
Always prefer ISE ↔ FMC pxGrid for context-driven NAC.
9. How do I troubleshoot pxGrid connectivity issues between ISE and FMC?
- On ISE CLI:
show logging application pxgrid.log show pxGrid clients - On FMC GUI:
System > Integration > Identity Sources > ISE → Check status.
Common issues: - Wrong certificates (not trusted).
- DNS resolution mismatch.
- pxGrid service not running.
10. Can multiple FMCs integrate with the same ISE cluster?
Yes . ISE supports multiple pxGrid clients, including multiple FMCs. Each FMC must register separately as a pxGrid client.
Scale note: ISE pxGrid cluster sizing must be planned — large deployments may require dedicated pxGrid nodes for FMC, Stealthwatch, Firepower, etc.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
By integrating Cisco FMC with ISE via pxGrid, you transform firewall enforcement from IP-based to identity-based, with real-time threat response through ANC. This is a critical building block of Zero Trust & Threat-Centric NAC.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.
I run a focused 4-month instructor-led Fast-Track to Cisco ISE Mastery Pro course.
Course outline: https://course.networkjourney.com/ccie-security/
Seats are limited – secure your spot today and take your ISE journey to CCIE Security level mastery.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![EIGRP for IPv6 – Routing Smarter in the Next-Gen Network Era [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/EIGRP-for-IPv6-–-Routing-Smarter-in-the-Next-Gen-Network-Era_networkjourney-1.png)
![Ticket#8 - VOIP Choppy Audio – DSCP Marking Mismatch Fixed [QoS Real World] [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-Ticket-8.jpg)
