[Day 123] Cisco ISE Mastery Training: Integration with VMware Workspace ONE
Table of Contents
Introduction
When we talk about modern NAC (Network Access Control), the real battlefield isn’t just user authentication — it’s device trust, compliance, and dynamic enforcement. Traditional methods that relied on MAC addresses or static profiling are broken by today’s realities: MAC randomization in iOS/Android/Windows, multi-device users, and the need for real-time compliance checks.
This is where the integration between Cisco ISE and VMware Workspace ONE (formerly AirWatch) becomes a game-changer. Workspace ONE UEM manages the device lifecycle (enrollment, compliance, certificates), while ISE enforces secure access at the network edge (wired, wireless, VPN).
By integrating them, we get:
- Certificate-based authentication (EAP-TLS) with GUID as stable identity (not spoofable, not randomized).
- Dynamic MDM posture checks during login — compliant devices get full access, non-compliant get quarantined.
- Automatic remediation via CoA (Change of Authorization) without disrupting user productivity.
- Unified BYOD and corporate device onboarding with Workspace ONE + ISE portals.
This is not a theoretical exercise — it’s the real-world NAC enforcement enterprises demand today. In this deep-dive, we’ll build the full integration from scratch, configure both ends (ISE + Workspace ONE), wire it to network devices (Switch/WLC), and validate step-by-step with CLI and GUI so you walk away with production-grade mastery.
Problem Statement
Enterprises now face:
- MAC randomization (mobile OSes) that breaks MAC-based lookups.
- Need for certificate-based device identity + device posture to allow/deny access (Wi-Fi, wired, VPN).
- Requirement to enforce posture dynamically (CoA) when device compliance changes.
Workspace ONE + ISE integration solves this by delivering a device GUID (in cert SAN), posture/compliance attributes via MDM APIs, and letting ISE use that data inside authorization policies. (Cisco, VMware Blogs)
Solution Overview (how ISE addresses it)
High-level flow (what we will implement & validate):
- Workspace ONE UEM issues device certificates (SCEP/CA) that include GUID/DeviceUID in the certificate (CN or SAN). ISE can use that GUID instead of MAC. (Tech Zone, VMware Blogs)
- ISE is configured with the Workspace ONE UEM as an External MDM (MDM API v3) — ISE uses the MDM API to query device attributes at authentication/authorization time. (Cisco)
- Network devices (WLC / switch) send RADIUS auth requests to ISE (802.1X/EAP-TLS or EAP-PEAP + client certs). ISE performs an MDM lookup and evaluates policy = COMPLIANT → permit, NON-COMPLIANT → quarantine + CoA.
- ISE issues CoA to the NAD when posture changes or on scheduled polling. (pxGrid used for richer telemetry in some deployments — ensure pxGrid 2.0 compatibility). (Cisco)
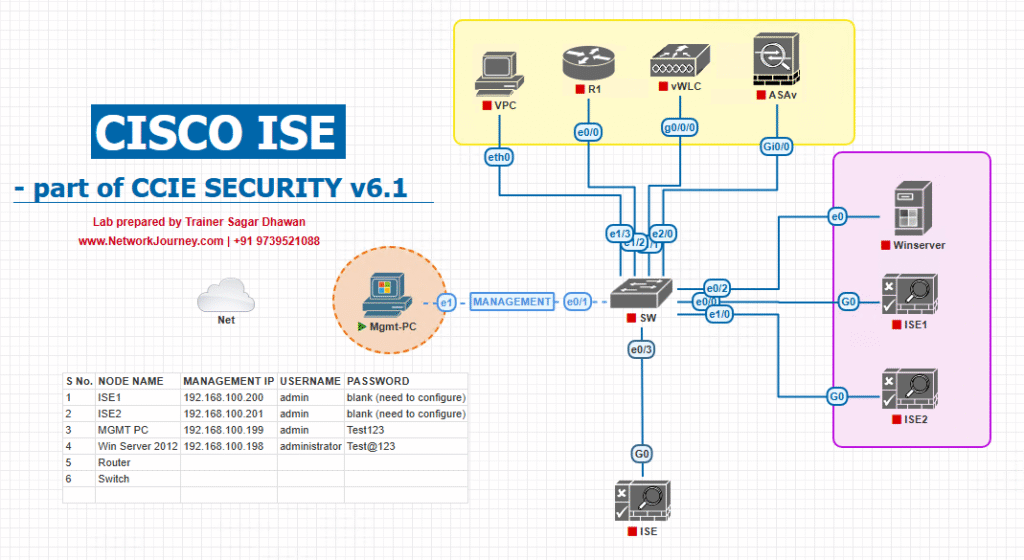
Sample Lab Topology
Lab mode: EVE-NG (VMware) or native VMware Workstation/ESXi with VM networking.
Top level (IP plan examples):
- ISE PAN: 10.10.10.10 (PAN/PSN in lab single node)
- Workspace ONE UEM (Cloud or on-prem test instance): ws1.lab.local (10.10.10.20) – API port 443
- AD + MS-CA (PKI): 10.10.10.30
- WLC (or Cisco 9800): 10.10.10.40
- Access Switch (Catalyst 9300): 10.10.10.50
- Test Client (Windows 10 / iOS / Android): DHCP via VLANs
- Lab Internet / DNS / NTP reachable by all nodes
Topology diagram (simple):
Notes:
- Use internal CA (MS-CA) for issuing device client certs; you’ll import the CA chain to both Workspace ONE and ISE.
- If using cloud Workspace ONE, ensure firewall rules permit ISE → Workspace ONE API.
- Use DNS names for all devices (cert validation).
Step-by-Step GUI Configuration Guide
(organized by component: Workspace ONE UEM → Cisco ISE → NADs (Switch/WLC) → Test & Validation)
5.A Prerequisites & version matrix
- Cisco ISE: 3.1+ recommended to use MDM API v3 (GUID support). If you are using older ISE, you will be limited to MAC lookup. (Cisco)
- Workspace ONE UEM: recent UEM release that supports pushing GUID into cert SAN (Omnissa/Workspace ONE documentation). Recommended: Workspace ONE UEM 2410 or later features noted in vendor docs. (Tech Zone, VMware Blogs)
- WLAN/WLC and Switch: controllers that support 802.1X and CoA. On WLC make sure RADIUS and CoA are enabled. (WLC / IOS XE steps later.)
- PKI: ADCS (Microsoft CA) or other CA used to issue device SCEP / client certs. Ensure Workspace ONE certificate template is set to include GUID/DeviceUid in SAN (URI/DNS/SN or other field as vendor recommends). (Tech Zone)
5.B Workspace ONE UEM — configuration steps (detailed)
Goal: create cert template that embeds DeviceUID/GUID in cert SAN, create API credentials for ISE to call Workspace ONE UEM REST APIs.
1) Create / integrate Certificate Authority (ADCS)
- Login to Workspace ONE UEM Console (Admin edit mode).
- Navigate: Devices (or Group & Settings) → Settings → System → Enterprise Integration → Certificate Authorities (path may vary by version). Click Add.
[Workspace ONE Console — Certificate Authorities] - Fill fields: CA server FQDN, credentials, template mapping. Save and test connection.
2) Create Certificate Template that pushes GUID into SAN
- In Workspace ONE: Devices → Certificates → Certificate Templates → Add (or Certificates → Request Templates).
[Workspace ONE — Add Certificate Template] - Template settings: choose the CA, issuing template name (e.g., WS1_Device_Cert). Important: include DeviceUid (or Device GUID variable) in the subject alternative name (SAN) — many docs call it “DeviceUid” or “GUID” and you can push it as a URI/DNS or serialNumber field depending on template options. Omnissa / VMware recommend a SAN with GUID for ISE lookup. Example fields:
- CN = ${EnrollmentUser} (or leave CN as username)
- SAN (otherName/URI or serialNumber) = DeviceUid (or variable like ${DeviceUid})
[Certificate Template SAN showing DeviceUid]
Why this matters: ISE MDM API v3 expects GUID delivered with the cert (SAN or CN) so ISE can look up device irrespective of MAC randomization. (Tech Zone, VMware Blogs)
3) Create / push a Device Profile to issue the cert
- Devices → Profiles & Resources → Profiles → Add. Choose platform (Windows, iOS, Android).
- Add a Certificate payload that references the template, SCEP settings if needed. Assign to Smart Group containing lab test devices.
[Workspace ONE — Profile > Certificate Payload]
4) Create API Admin user & REST API Key (for ISE to query UEM)
- Create an admin account for integration: Accounts → Administrators → Add Admin (role limited to REST API usage).
[Workspace ONE — Add Admin User] - Create REST API Key: Groups & Settings → All Settings → System → Advanced → API → REST API → Add. Enable API access, create a key. Copy the key now. This key is later passed as header
aw-tenant-codein API calls. (TechDocs)
[Workspace ONE — REST API Key]
5) Test Workspace ONE API
- Example (basic authentication):
# Example: get devices list (replace placeholders) curl -k -u "ws1ApiUser:Password" \ -H "aw-tenant-code: <API_KEY>" \ "https://ws1.lab.local/api/devices/search?pagesize=10"
- You should get JSON of devices; if not, check API user privileges and network connectivity. (If using OAuth, follow the OAuth client flow in your Workspace ONE version.)
Notes / Troubleshooting:
- If template variables differ in your UEM version, consult Workspace ONE API docs and your template variable list; test with a sample device and inspect certificate details on device to confirm GUID exists. (Tech Zone, Omnissa Documentation)
5.C Cisco ISE — configuration steps (detailed GUI + validation)
Objective: Add Workspace ONE UEM as an external MDM server, configure ISE to use MDM API v3 (GUID), create authorization profiles & policy rules that use MDM attributes.
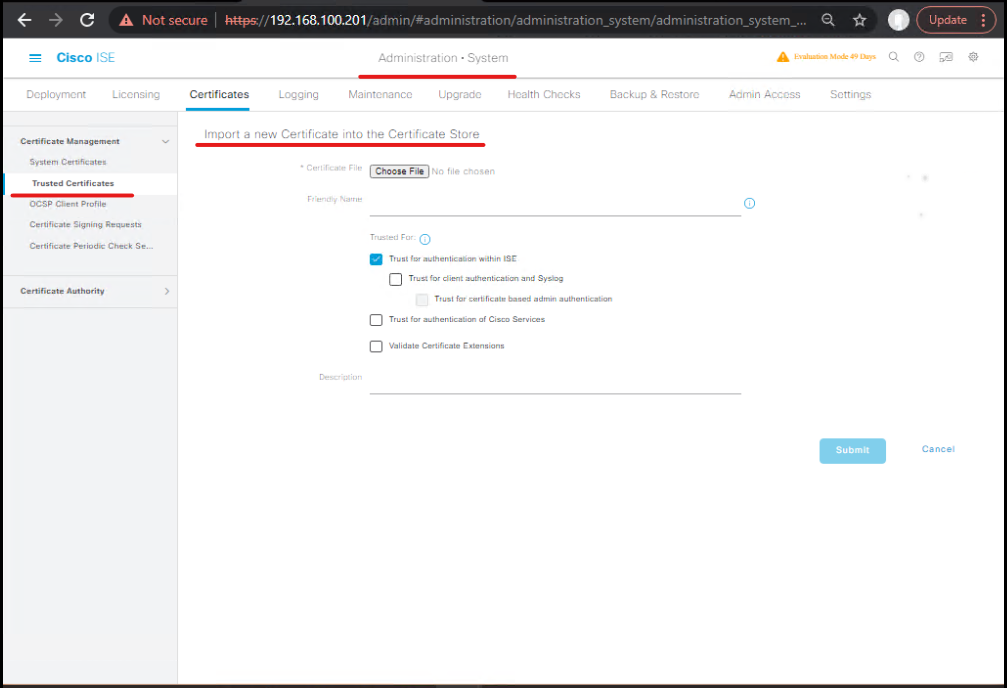
1) Add trusted CA certificate for the UEM server
- ISE GUI: Administration → System → Certificates → Trusted Certificates → Import. Upload Workspace ONE CA or issuing CA chain.
[ISE — Trusted Certificates Import]
2) Add the Workspace ONE UEM as an MDM Server in ISE
- ISE GUI: Administration → External MDM (label varies; some ISE guides show Administration → External MDM or Administration → Identity Management → External MDM). Click Add.
[ISE — Add External MDM Server]
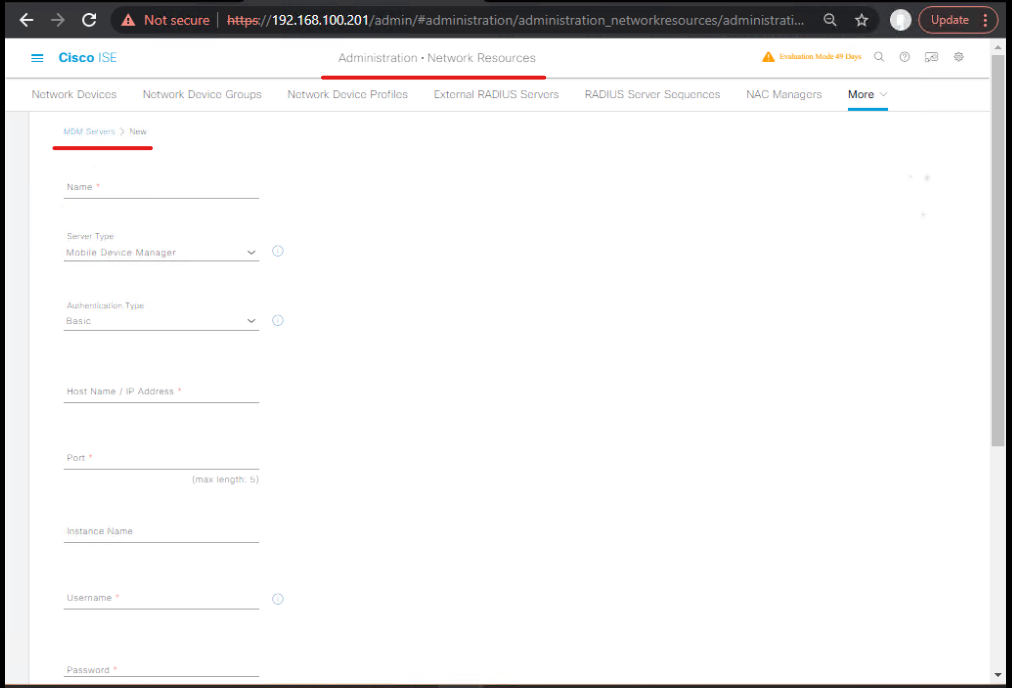
- Fill fields:
- Name: WS1-UEM-Lab
- Server Type: VMware Workspace ONE / Omnissa/AirWatch (select vendor profile if available)
- API URL: https://ws1.lab.local (or Workspace ONE API URL)
- Auth: Username and Password (the admin account you created) or OAuth/Cert method (if configured)
- API Key: add REST key (if required by your UEM)
- Lookup method: GUID (MDM API v3) — choose the API v3 option in the Add MDM screen (this tells ISE to use GUID rather than MAC)
- Click Save then Test Connection. ISE will call the UEM’s mdm server info API to discover features. Successful test = good.
[ISE — Test Connection success]
Behind the scenes ISE uses the MDM Server Info API and MDM Device Attributes Query API to query the UEM. See Cisco API docs. (Cisco DevNet, Cisco)
3) Verify MDM dictionary populated
- After adding the MDM server successfully, ISE will populate an MDM dictionary (Policy → Policy Elements → Dictionaries → MDM). Confirm attributes such as
mdm.compliance,mdm.enrollmentStatus, etc. These attributes are used in Authorization policy rules. (Cisco)
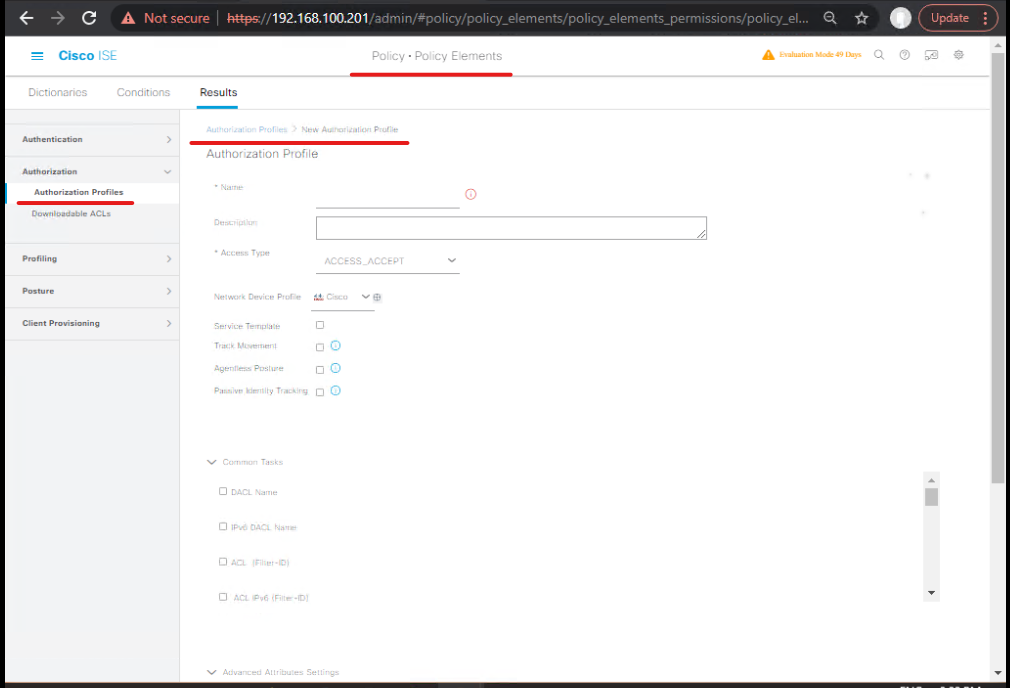
4) Authorization Profiles (create dACL / VLAN actions)
- Policy → Policy Elements → Results → Authorization → Authorization Profiles → Add.
Example profiles:MDM_COMPLIANT_ACCESS— Access Accept, assign VLAN or SGT or DACL for normal access.MDM_NONCOMPLIANT_QUARANTINE— Access Reject or Access Accept + redirect / dACL to quarantine (web redirect or limited ACL).
[ISE — Authorization Profile Add]
5) Authorization Policy Rule (use MDM attributes)
- Policy → Policy Sets → Select the PolicySet for WLAN (or create new). Edit Authorization rules.
- Create rule:
- Name:
MDM_COMPLIANT_RULE - Condition: MDM.Compliance == ‘Compliant’ OR MDM.EnrollmentStatus == ‘Enrolled’ AND MDM.Compliance == ‘Compliant’
- Result:
MDM_COMPLIANT_ACCESS
- Name:
- Create fallback rules:
MDM_NOT_REGISTERED→ redirect to BYOD portal (MDM onboarding page).MDM_NONCOMPLIANT→MDM_NONCOMPLIANT_QUARANTINE
[ISE — Policy Set Authorization Rules]
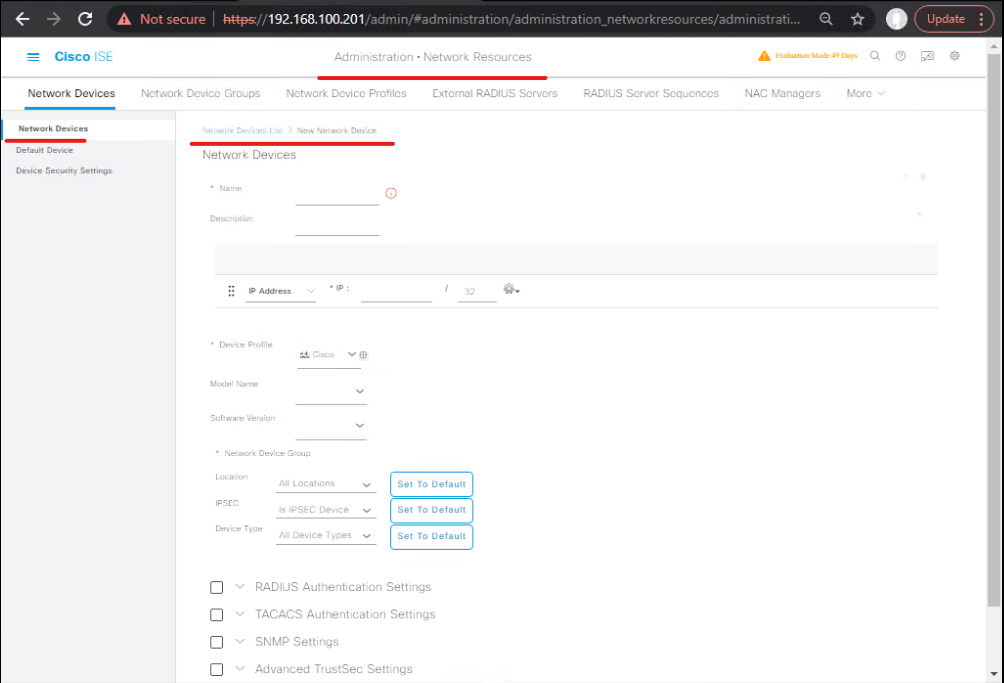
6) CoA / dACL settings for your NADs (ensure NAD supports CoA)
- Administration → Network Resources → Network Devices → Edit your NAD (WLC or Switch) → enable CoA and dACL for the device. Add dACL profiles in ISE if required.
[ISE — Network Device CoA settings] - Save and push changes.
7) Test ISE MDM lookup flow
- Start a test device (enrolled and cert installed). Connect to Wi-Fi (EAP-TLS). In ISE GUI: Operations → RADIUS → Live Logs. Filter by the username or MAC/GUID. You should see:
- Authentication request received (802.1X).
- ISE MDM lookup performed (ISE queries UEM, receives
compliance = Compliant), and Authorization decision matchesMDM_COMPLIANT_ACCESS.
[ISE — Live Log showing MDM result]
5.D Network Access Device (NAD) configuration — Switch & WLC (CLI & GUI)
Switch (Catalyst IOS XE) — sample config (802.1X + RADIUS + MAB)
! global AAA + RADIUS server + dot1x aaa new-model ! radius server ISE address ipv4 10.10.10.10 auth-port 1812 acct-port 1813 key VerySecret123 ! aaa group server radius ISE-GROUP server name ISE ! aaa authentication dot1x default group ISE-GROUP aaa authorization network default group ISE-GROUP aaa accounting dot1x default start-stop group ISE-GROUP aaa session-id common ! dot1x system-auth-control ! interface GigabitEthernet1/0/10 switchport mode access switchport access vlan 20 authentication port-control auto dot1x pae authenticator mab spanning-tree portfast
Validation (switch CLI):
# show authentication sessions (IOS XE) show authentication sessions interface GigabitEthernet1/0/10 detail # or (older): show access-session interface Gi1/0/10 details
Expect to see Status: Authorized and Username (or MAC). If EAP-TLS, you’ll see certificate CN info. Use clear authentication session interface Gi1/0/10 to reset. (Syntax varies by IOS; check your platform.) (Cisco)
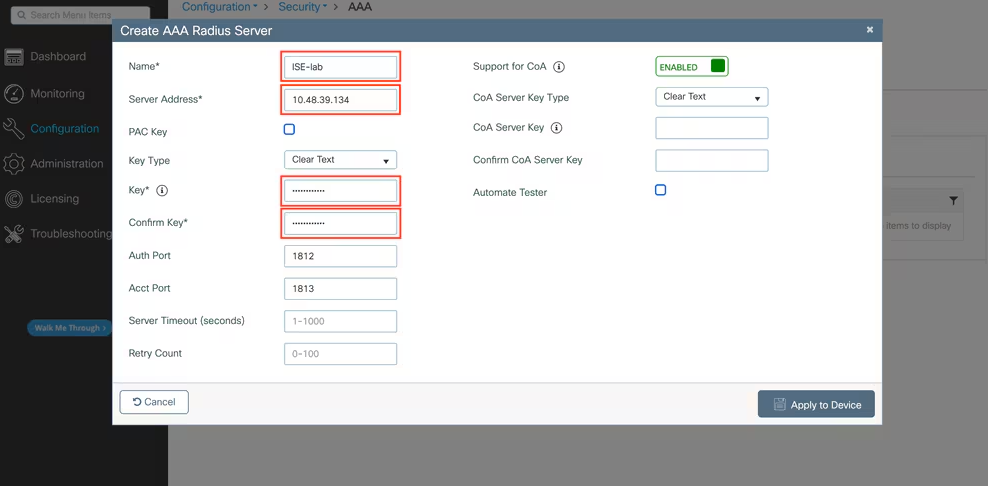
WLC (9800 / legacy WLC) — GUI steps
- WLC GUI: Configuration → Security → AAA → RADIUS → Authentication → Add ISE (Name, IP, Secret). [WLC — RADIUS Add]
- Configure WLAN: WLANs → Create “Corp-WPA2-EAP” → Security → Layer 2 (WPA2 Enterprise) → AAA Server Group → choose ISE. Set EAP method (EAP-TLS for certificate). Upload trusted CA(s) to WLC (System → Certificates) for EAP-TLS trust chain. (Cisco)
WLC CLI RADIUS example (older syntax):
# Example on legacy WLC (syntax varies) config radius auth add 1 10.10.10.10 1812 ascii VerySecret123 config radius acct add 1 10.10.10.10 1813 ascii VerySecret123
Validation (WLC CLI / GUI):
- CLI:
show aaa serversorshow radius summary(platform dependent). - GUI: RADIUS status page, check Authentication requests / counters. (Cisco)
5.E EAP profile & test device flow (SSID config)
WLAN: EAP-TLS (recommended for GUID cert)
- WLAN: Security → Layer 2: WPA2/WPA3 Enterprise → 802.1X with ISE RADIUS server.
- EAP method: EAP-TLS (client certificate). If using EAP-PEAP, the client will present cert in inner method only if configured — EAP-TLS is more direct for device certs.
- Assign VLAN or dynamic authorization behavior (ISE dACL / VLAN change).

Test steps:
- Ensure the device has device cert issued by Workspace ONE (check cert store).
- Connect to
Corp-WPA2-EAP. Watch ISE Live Logs for authentication attempt and MDM lookup. Confirm authorization result.
GUI check: ISE Live Logs (Operation → RADIUS → Live Logs).
CLI check (Switch):show authentication sessions interface ... detail.
[WLC WLAN profile, ISE Live Logs]
5.F Validation & Troubleshooting checklist (GUI + CLI)
1) Workspace ONE → ISE API basic connectivity
- From ISE server (or lab jump host):
curl -vk -u ws1ApiUser:Password -H "aw-tenant-code: <API_KEY>" https://ws1.lab.local/api/help→ should return API help JSON.
2) ISE GUI: Live Logs validation
- Operation → RADIUS → Live Logs: filter by username/device. Confirm:
- Authentication request received
- MDM lookup performed (look for MDM status in details)
- Authorization profile matched (MDM_COMPLIANT_ACCESS)
3) Switch CLI
show authentication sessions interface Gi1/0/10 detail # or show access-session interface Gi1/0/10 detail
Look for Status: Authorized and username or certificate CN/GUID present.
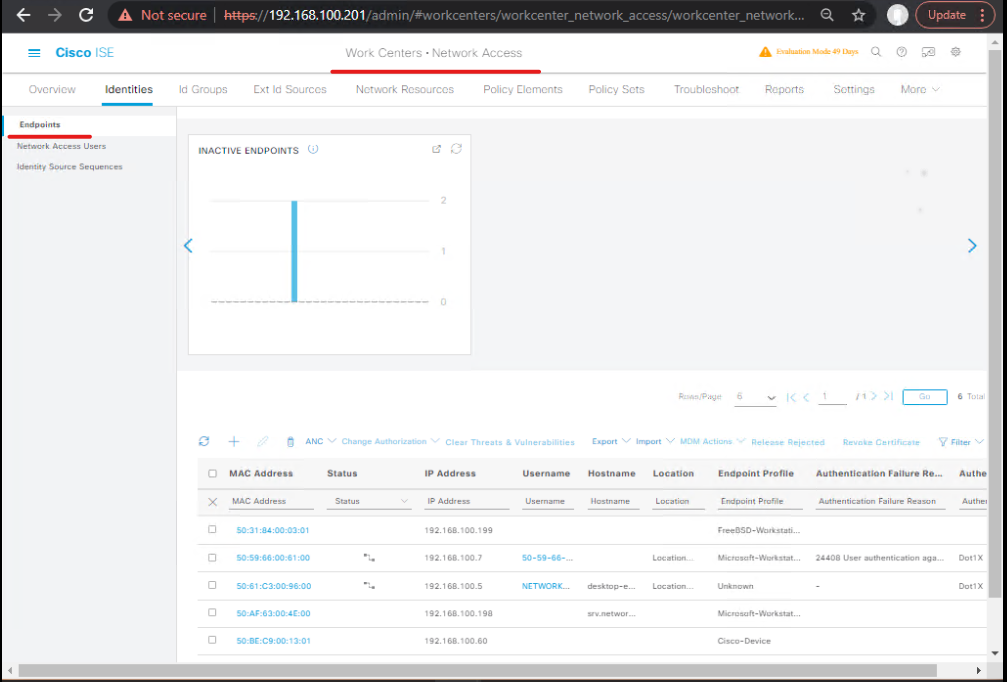
4) ISE Endpoints & Endpoint details
- Work Centers → Network Access → Identities → Endpoints (or Administration → Identities → Endpoints) — search by GUID or MAC to see MDM attributes and last compliance status.
5) If MDM lookup failing
- Confirm ISE → Workspace ONE network connectivity (port 443) and CA trust.
- Confirm API user &
aw-tenant-code(REST API key) valid. (TechDocs)
6) CoA not working
- NAD must support CoA and be configured in ISE Network Device entry for CoA. Check NAD logs and ISE “CoA” audit logs (Operation → Reports). Confirm firewall allows UDP 1700/3799 or the CoA port used.
Expert Level Use Cases
Use Case A — Certificate-based Wi-Fi for corporate devices (EAP-TLS + GUID lookup)
Steps
- Workspace ONE: Create certificate template with DeviceUid in SAN; push profile. (Tech Zone)
- ISE: Add UEM as MDM (MDM API v3; GUID lookup). (Cisco)
- WLC: Configure WLAN EAP-TLS to use ISE.
- Switch/AP: ensure 802.1X and RADIUS settings point to ISE.
Validation
- Device presents cert; ISE Live Logs shows MDM lookup and
compliance=Compliant. Switchshow authentication sessionsshows Authorized. ISE Endpoints shows device with MDM attributes.
Use Case B — Automated CoA quarantine on posture change
Steps
- Enable CoA on NADs and define quarantine dACL in ISE Authorization Profiles.
- Configure scheduled polling in ISE or event-driven CoA when UEM reports noncompliance.
Validation
- Force device noncompliant in Workspace ONE → ISE poll triggers → ISE issues CoA → switch/WLC logs show CoA received and dACL applied; client loses normal access.
Use Case C — BYOD onboarding via Workspace ONE + ISE redirect
Steps
- In ISE, create Authorization rule
MDM_Unregistered→ redirect to BYOD portal. - Configure WLC/Switch ACLs to allow access to Workspace ONE onboarding endpoints.
Validation
- Unenrolled device connects → ISE authorization returns web redirect → device browser opens BYOD onboarding page.
Use Case D — SAML SSO of ISE Admin Portal via Workspace ONE Access (optional)
Steps
- Configure Workspace ONE Access as an IdP for ISE admin SSO (SAML). On ISE go to Administration → System → Admin Access → Identity Source (create IdP connection). (Cisco)
Validation
- Admin logs into ISE using Workspace ONE Access SSO.
(Additional expert use cases: IoT onboarding, pxGrid telemetry sharing to EDR, cert lifecycle management via Workspace ONE, SCEP + device cert rotation. Tell me which 2 you want expanded and I’ll deliver step-by-step.)
Quick CLI cheat-sheet
Switch (Catalyst IOS XE)
aaa new-model radius server ISE address ipv4 10.10.10.10 auth-port 1812 acct-port 1813 key VerySecret123 aaa group server radius ISE-GROUP server name ISE aaa authentication dot1x default group ISE-GROUP aaa authorization network default group ISE-GROUP dot1x system-auth-control interface Gi1/0/10 switchport mode access authentication port-control auto dot1x pae authenticator mab
WLC (legacy CLI sample)
config radius auth add 1 10.10.10.10 1812 ascii VerySecret123 config radius acct add 1 10.10.10.10 1813 ascii VerySecret123
Workspace ONE API test (curl)
curl -vk -u "ws1ApiUser:Password" \ -H "aw-tenant-code: <API_KEY>" \ "https://ws1.lab.local/api/help"
ISE test: MDM Server Info (what ISE uses)
# Example: MDM Info endpoint schematic - the vendor docs show this endpoint pattern curl -k -u "ws1ApiUser:Password" "https://ws1.lab.local/ciscoise/mdminfo?ise_api_version=3"
(Exact endpoint variant depends on UEM vendor; test v
FAQs — Cisco ISE + VMware Workspace ONE Integration
1. Q: What exactly does Cisco ISE gain from integrating with Workspace ONE?
A: ISE gains real-time device compliance visibility. It can check if a device is enrolled, compliant, encrypted, or jailbroken before granting access. Without Workspace ONE, ISE only knows the identity (via 802.1X) but not the device’s health state.
2. Q: Why is GUID used instead of MAC address in this integration?
A: Modern OSes randomize MAC addresses (iOS, Android, Windows 10/11). GUID (Globally Unique Identifier) is embedded in the device certificate (issued by Workspace ONE) and stays consistent across all network connections. ISE queries Workspace ONE with this GUID to identify the device reliably.
3. Q: Which version of Cisco ISE supports Workspace ONE GUID integration?
A: ISE 3.1 and later supports MDM API v3, which enables GUID-based lookups. Older versions (2.x, 3.0) rely on MAC-based queries, which are unreliable in modern deployments.
4. Q: Do I need pxGrid for this integration?
A: No. ISE ↔ Workspace ONE integration uses the MDM REST API, not pxGrid. However, if you want Workspace ONE compliance events to also feed other systems (like Firepower, Splunk, or EDR), pxGrid may be used alongside.
5. Q: How does ISE know if a device is compliant during authentication?
A: During RADIUS authentication, ISE extracts the GUID from the client certificate and queries Workspace ONE via the MDM API. Workspace ONE replies with compliance attributes (e.g., Compliant, Non-Compliant, Not Enrolled). ISE then applies authorization rules based on those values.
6. Q: What happens if Workspace ONE is unreachable when a user authenticates?
A: Behavior depends on your ISE policy:
- Fail-Open → user gets network access (less secure, better user experience).
- Fail-Closed → deny or restrict access until MDM server responds (more secure, but user impact).
Best practice: create a fallback rule (limited VLAN/dACL for “MDM Unreachable”).
7. Q: How can I test if ISE ↔ Workspace ONE API communication works before deployment?
A: From the ISE CLI or a jump host, run:
curl -k -u "ws1ApiUser:Password" \ -H "aw-tenant-code:<API_KEY>" \ "https://<WS1-Server>/api/help"
If you receive JSON/XML output, the API integration is working. You can also use Test Connection in ISE’s External MDM settings.
8. Q: Where can I see Workspace ONE attributes inside ISE?
A: Navigate in ISE GUI:Policy → Policy Elements → Dictionaries → MDM.
Here you’ll see fields like ComplianceStatus, EnrollmentStatus, OSVersion, Ownership. These can be directly used in Authorization rules.
9. Q: How do I verify that the GUID is actually present in the certificate?
A: On the endpoint:
- Windows: Run
certutil -store -user My→ inspect SAN field forDeviceUidorGUID. - iOS/Android: Check installed profile details under “Certificates.”
If the GUID isn’t there, fix your Workspace ONE certificate template to include${DeviceUid}in the SAN.
10. Q: Can I apply different policies for corporate vs BYOD devices with this setup?
A: Yes. Workspace ONE passes the Ownership attribute (Corporate vs Employee/Personal). In ISE, build separate Authorization Rules:
Ownership=Corporate AND Compliance=Compliant→ full access.Ownership=Employee AND Compliance=Compliant→ limited VLAN or SGT.Ownership=Any AND Compliance=Non-Compliant→ quarantine dACL.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes (key takeaways)
- For modern mobile OS behavior, certificate + GUID is the robust approach. Implement Workspace ONE cert templates to push GUID into SAN, then configure ISE MDM API v3. (Cisco, Tech Zone)
- Always validate end-to-end: cert on device → RADIUS/EAP → ISE Live Logs → MDM lookup → Authorization decision. Use switch/WLC CLI to verify session state.
- CoA and dACLs are business critical for remediation — ensure NAD support and ISE is allowed to send CoA traffic.
- Keep ISE pxGrid and API versions in mind (pxGrid 2.0, ISE 3.1+ MDM API v3). (Cisco)
Upgrade Your Skills – Start Today
Fast-Track to Cisco ISE Mastery Pro — 4-month instructor-led training
Comprehensive CCIE Security / ISE Mastery bootcamp, instructor-led with labs and certification path.
Course outline & sign-up: https://course.networkjourney.com/ccie-security/
- “Hands-on labs, real-world projects (ISE, pxGrid, Workspace ONE), weekly live sessions, lifetime lab access.”
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![REST API Basics for Cisco Devices – Automate Smarter, Not Harder [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/REST-API-Basics-for-Cisco-Devices-–-Automate-Smarter_Not-Harder_networkjourney.png)

![[Day 41] Cisco ISE Mastery Training: Wireless 802.1X Authentication Overview](https://networkjourney.com/wp-content/uploads/2025/08/Day-41-Cisco-ISE-Mastery-Training-Wireless-802.1X-Authentication-Overview.png)