[Day 127] Cisco ISE Mastery Training: RADIUS Change of Authorization (CoA)
Table of Contents
Introduction
Imagine a user connecting to your network. At first, they get limited access — maybe just Internet. A few minutes later, Security updates their compliance posture: antivirus updated, corporate certificate installed, endpoint compliant.
Now, instead of asking the user to disconnect and reconnect, Cisco ISE pushes a Change of Authorization (CoA) to the switch or wireless controller. Instantly, their session re-authenticates, applying the new authorization policy. No reboot. No downtime. No complaints to IT.
This is CoA: ISE telling the network to change what a user/device is allowed to do, dynamically, mid-session.
It is used for:
- Guest Onboarding – Move from guest to employee VLAN after sponsor approval.
- Posture/Compliance – Apply ACLs/dACLs after antivirus/patch validation.
- Incident Response – Quarantine a compromised host immediately.
- Zero Trust NAC – Continuously enforce policies based on identity and posture.
Mastering CoA is critical for real-world NAC deployments, because static policies are useless without dynamic enforcement.
Problem Statement (real-world challenges)
Networks are dynamic: user roles, device posture and risk change continuously. Without dynamic enforcement you’re stuck with static decisions made at the time of authentication. Common problems:
- A contractor finishes work — sessions remain active.
- A host fails posture — but remains on the network until reauth or manual action.
- Guest gets approved but client never receives full access because reauthorization didn’t trigger.
- Security teams need immediate disconnects for compromised endpoints.
CoA solves these by allowing a RADIUS server (ISE) to send unsolicited RADIUS messages to network devices to change an existing session’s authorization state (reauth, disconnect, port-bounce, VLAN/ACL update).
Technical constraints: CoA requires NAD (switch/WLC/AP) support for RFC-3576, matching shared secrets and reachable CoA ports; design must consider firewalls, NAT, and DTLS for controllers. (IETF Datatracker, Cisco)
Solution Overview (how ISE implements CoA)
- CoA is standardized by RFC-3576 (Dynamic Authorization Extensions to RADIUS). It defines the protocol mechanics and standard port usage. (IETF Datatracker)
- Cisco ISE acts as the CoA server: it can send reauthentication and disconnect commands and other dynamic auth messages to NADs (switches, WLC/APs). ISE exposes both GUI actions (Live Logs → Reauth/Disconnect) and REST API endpoints (Monitoring / CoA APIs) for automation. (Cisco DevNet)
- NADs must be configured to accept CoA (enable dynamic-author support, configure client keys and CoA port — historically some systems used port 1700 by default; RFC standard is 3799; check your NAD vendor). (Cisco, IETF Datatracker)
Key enforcement actions possible with CoA:
- REAUTH (force client to re-authenticate and receive a new authorization profile).
- DISCONNECT (terminate session).
- PORT-BOUNCE or SHUTDOWN (administratively flap or disable port).
- Apply new VLAN/ACL/DACL via authorization profile changes (sent as Access-Accept attributes on reauth). (Cisco, Cisco DevNet)
Sample Lab Topology
Use VMware (ESXi/Workstation) or EVE-NG. I’ll give a reproducible topology and IP plan.
Components
- ISE Cluster: PAN (admin) + Monitoring/PSN (ise-psn1) — VMs (use 3.x/3.4).
- NADs:
- Catalyst 9300 switch (wired NAC).
- Catalyst 9800 virtual (or 9800-CL) WLC for wireless CWA/CoA flows.
- Optionally: Aruba/Meraki APs or Meraki for comparison.
- Clients: Laptop (for 802.1X), Guest phone (open SSID), Windows host for posture flows.
- Cloud/Automation host: Ubuntu VM running Postman/curl / Python for REST API calls.
- Management network: 10.10.10.0/24; Guest VLAN: 172.16.110.0/24
Example IPs
- ISE PAN: 10.10.10.10
- ISE PSN (monitoring): 10.10.10.11
- Catalyst 9300 management: 10.10.10.20
- Catalyst 9800 WLC: 10.10.20.10
- Client A: 172.16.110.100
Topology:
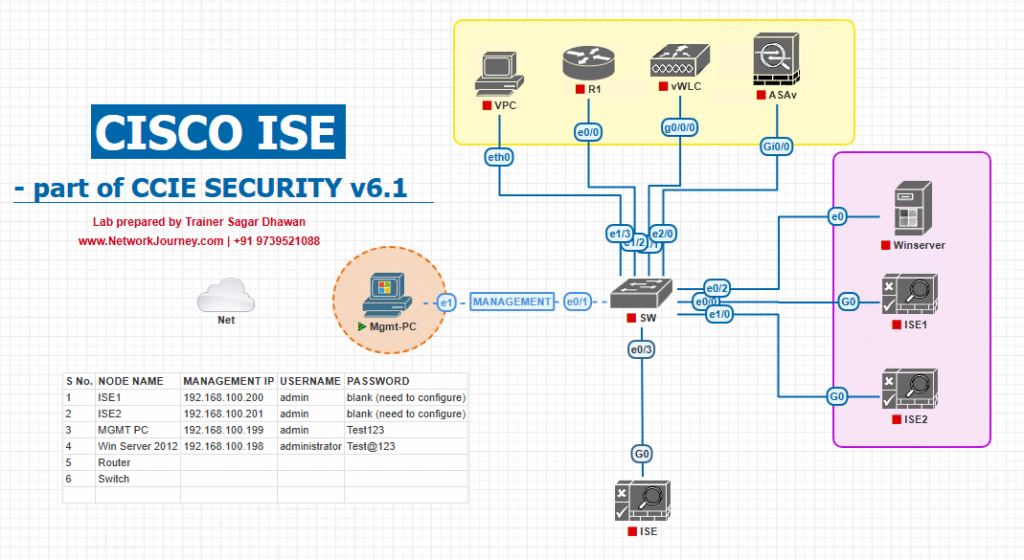
Notes for EVE-NG: import ISE ova(s), 9300 or NX-OSv/IOS-XE L2 images, 9800 image (if available), and a Debian/Ubuntu host for REST tests. Ensure the automation host can reach PSN admin ports (443/9060) or the monitoring node admin URL (for CoA API).
Step-by-Step GUI Configuration Guide (numbered + validation + CLI)
Quick plan: 1) Prepare NADs to accept CoA 2) Configure ISE network device entries and authorization profiles 3) Create policy and test reauth/disconnect via GUI & API.
A — NAD (switch & WLC) preparation — CLI examples
A.1 Catalyst 9300 (IOS XE) — enable CoA support
configure terminal ! Define radius server with normal auth/accounting radius server ISE address ipv4 10.10.10.11 auth-port 1812 acct-port 1813 key ISE_SHARED_SECRET exit ! Configure dynamic-authorization (RFC-3576/CoA) aaa server radius dynamic-author client 10.10.10.11 server-key ISE_SHARED_SECRET exit ! Optional: source interface for radius/CoA ip radius source-interface Loopback0 end
- Validation:
show aaa server radius dynamic-authororshow aaa server radius dynamic-author 10.10.10.11. Useshow authentication sessions interface <int> detailsandshow radius statisticsto confirm. (Cisco)
A.2 Catalyst 9800 WLC — dynamic author config (example)
config t aaa server radius dynamic-author client 10.10.10.11 server-key ISE_SHARED_SECRET end
- On the 9800 GUI: Configuration → Security → AAA → RADIUS → add ISE servers and enable CoA / dynamic-author in the AAA settings. Validation:
show wireless client mac <mac>shows CoA events when triggered. (Cisco)
Note: For some WLCs you may need DTLS config for CoA; Cisco docs show DTLS support for dynamic author. (Cisco)
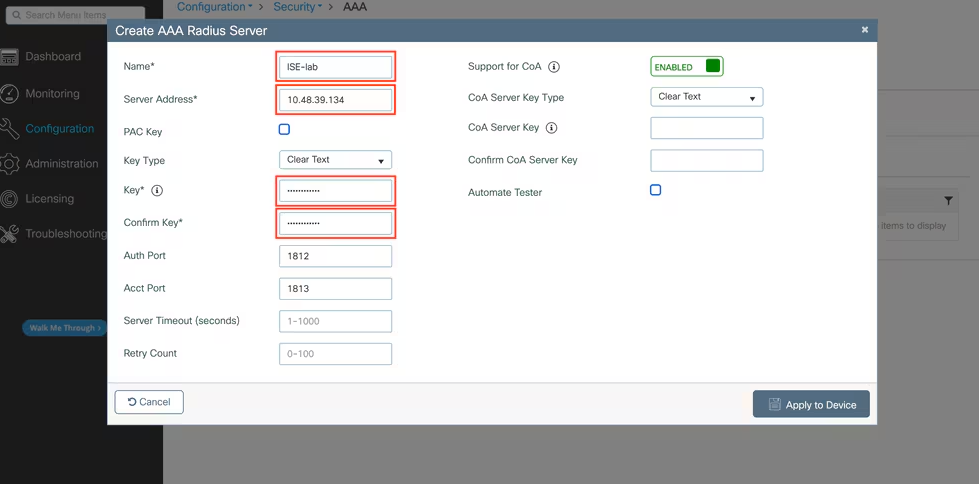
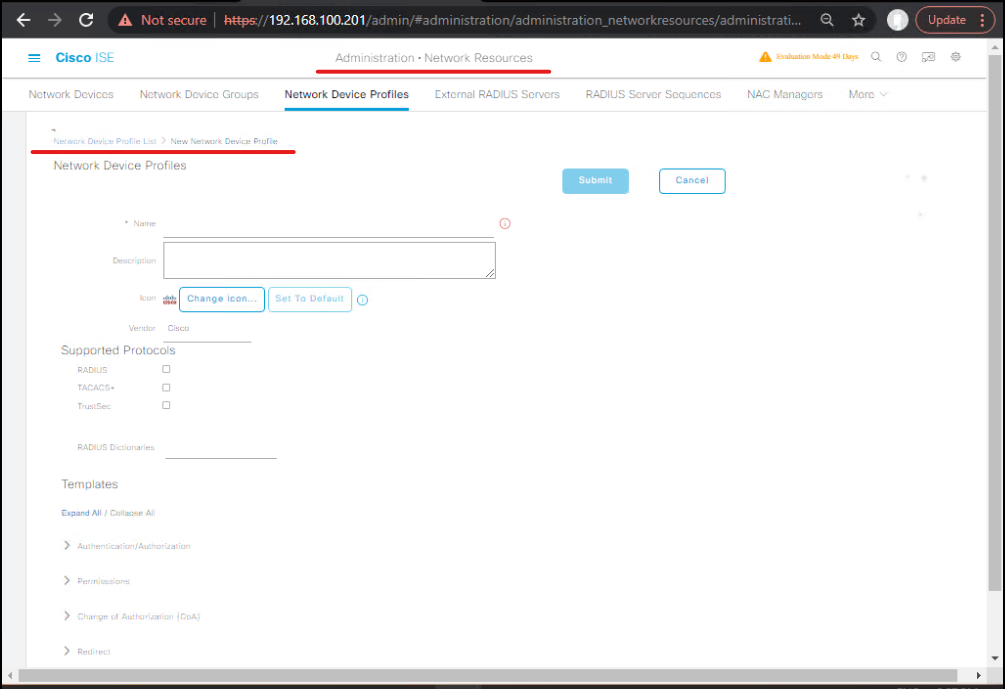
B — ISE: network devices & CoA settings (GUI)
- Administration > Network Resources > Network Device Profiles → create/verify the right vendor profile (this profile prepopulates CoA attributes). [Network Device Profiles]. (Cisco)
- Administration > Network Resources > Network Devices > Add → Add Catalyst 9300 and 9800 with management IPs; in the device entry ensure the RADIUS Shared Secret matches the NAD config. [Add Network Device]
- Advanced: If your ISE version exposes CoA port or dynamic auth options per device profile, set them here. (NADs historically accepted CoA on ports 1700 or 3799 — match vendor docs). (Cisco, IETF Datatracker)
- Submit & Save.
Validation: ISE will display network device reachability in Monitoring → Network Devices; verify RADIUS traffic in Operations → RADIUS → Live Logs when a test auth occurs.
C — ISE: Authorization profiles & policy
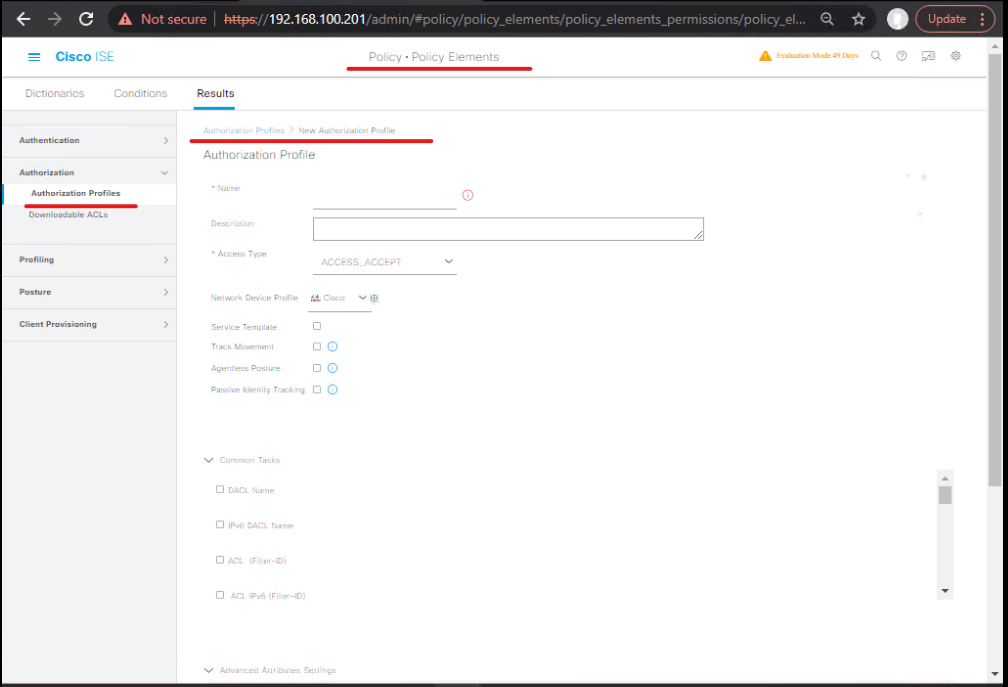
C.1 Create Authorization Profiles (GUI)
- Policy > Policy Elements > Results > Authorization > Authorization Profiles > Add
- Create
Guest_Full_Access— Access Type: ACCESS_ACCEPT, set VLAN/DACL name or common tasks (Assign VLAN, Use DACL, etc). [Authorization Profile – Full Access] - Create
Guest_Quarantine— Access Type: ACCESS_ACCEPT, DACL =DENY_ALLor VLAN guest quarantine. [Authorization Profile – Quarantine]
- Create
- Save.
C.2 Policy Set (GUI)
- Policy > Policy Sets → Create
Guest_SSIDor edit existing. Add conditionWireless SSID == Guest_SSIDor for wired use criteria per interface. [Policy Set] - Authentication: allow fallback (MAB/EAP) as needed.
- Authorization: Use rules:
- If
endpoint posture == Compliant→Guest_Full_Access - If
posture == NonCompliant→Guest_Quarantine
- If
- Save.
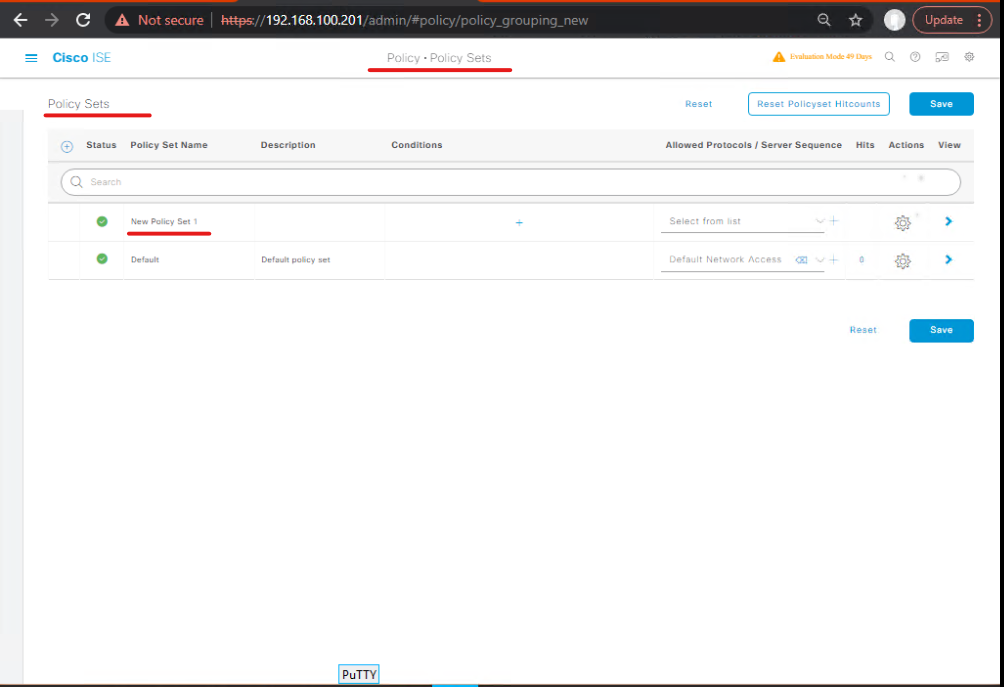
Validation: Operations > RADIUS > Live Logs — after a user authenticates you should see the Authorization result applied. If you later trigger CoA and change the authorization profile, Live Logs should show CoA events with success/failure.
D — Triggering CoA: GUI & API
D.1 GUI (fast test)
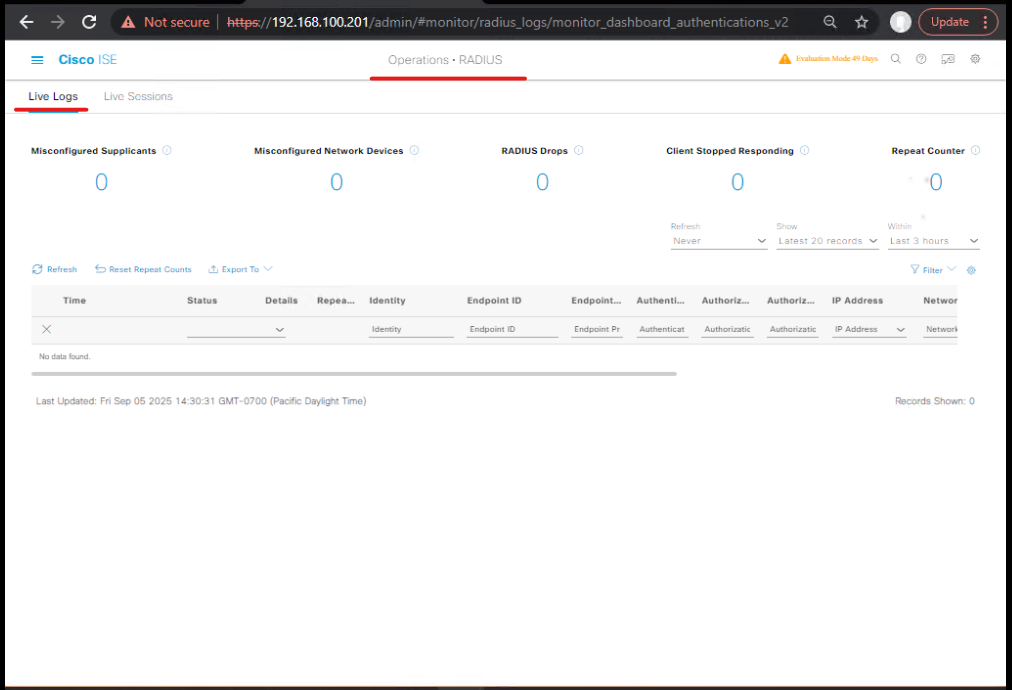
- Operations > RADIUS > Live Logs → locate the session (filter by username or MAC), click the session to expand detail. You’ll see a Take Action menu (or Action buttons) to Reauthenticate or Disconnect. Use those to trigger CoA from the ISE console. [Live Logs – Take Action]
- Validate: On switch:
show authentication sessions interface <if> detailsorshow authentication sessions mac <mac>should show the port flapping/reauth or changed authorization. On WLC:show wireless client mac <mac>or GUI Clients view. (Network Journey, Cisco)
D.2 REST API (programmatic) — DevNet Monitoring CoA endpoints
ISE exposes Monitoring / CoA API endpoints that run on a Monitoring ISE node. Examples from DevNet:
- Reauth (Reauthentication):
HTTP GET (browser or curl): https://<ISE_MONITOR>/admin/API/mnt/CoA/Reauth/<serverhostname>/<macaddress>/<reauthtype> Example: https://ise-psn1.example.com/admin/API/mnt/CoA/Reauth/ise-psn1/00:11:22:33:44:55/1
- Disconnect:
https://<ISE_MONITOR>/admin/API/mnt/CoA/Disconnect/<serverhostname>/<macaddress>/<disconnecttype>/<nasipaddress>/<destinationip>
Note: These endpoints must be executed on a Monitoring node; administration node is not required. Use basic auth (admin) over HTTPS. Detailed schema and behaviour on DevNet. (Cisco DevNet)
Sample curl (Reauth):
curl -k -u admin:ISE_ADMIN_PASS \ "https://10.10.10.11/admin/API/mnt/CoA/Reauth/ise-psn1/00:11:22:33:44:55/1"
- Response
trueindicates success. Iffalse, check ISE logs and NAD logs.
Important: There are also ERS/Monitoring endpoints under /ers or /admin depending on version — use DevNet docs for your exact ISE release. (Cisco DevNet, Cisco Community)
E — Validate with CLI & packet captures (step checks)
- Before: Authenticate client; confirm
Access-Acceptand initial authorization inOperations > RADIUS > Live Logs. Note the MAC & NAS IP. [Live Logs – details] - Trigger: From ISE GUI or API, trigger Reauth/Disconnect for MAC. [API curl response / Live Logs Reauth].
- Switch CLI: run:
show authentication sessions interface GigabitEthernet1/0/10 details show authentication sessions mac 00:11:22:33:44:55 show aaa server radius dynamic-author
Confirm reauth or port bounce events, and new authorization (VLAN/ACL). (Cisco)
- WLC CLI:
show wireless client mac 00:11:22:33:44:55 show aaa servers
Confirm WLC logged a CoA and the client reauth status. (Cisco)
- Packet capture: On the NAD (or capture point), tcpdump to see RADIUS CoA packets (UDP 3799 or configured CoA port). Example filter:
# on a Linux capture host in path sudo tcpdump -i eth0 udp and port 3799 -w coa.pcap
Open in Wireshark; you should see RADIUS-CoA-Request and CoA-Ack/CoA-NAK** responses. (If your environment uses port 1700, capture that port too). (IETF Datatracker, Cisco)
F — Common configuration gotchas & remediation (quick checklist)
- Shared secret mismatch between ISE and NAD → CoA will fail.
- CoA Port mismatch — historical ISE default 1700 vs RFC 3799 → ensure NAD and ISE agree. (Cisco, IETF Datatracker)
- Firewall/NAT blocking CoA UDP → allow UDP 3799 (or configured CoA port) and RADIUS ports.
- NAD vendor quirks: reauth vs port-bounce support vs required attributes vary per vendor (Aruba/Meraki/Cisco differ) — check NAD docs. (Airheads Community, Cisco Meraki Documentation)
Expert Level Use Cases
Use Case A — Posture remediation (isolate until clean)
- Goal: Device fails posture → isolate immediately, then reauth after remediation.
- Flow: Posture policy sends authorization result → Quarantine Authorization Profile applied. ISE triggers CoA Reauth after remediation (or automation calls Reauth).
- Validation: ISE Live Logs show
Authorization: QuarantinethenReauth succeededand switch shows VLAN change. CLI:show authentication sessions mac <mac>and ISE Live Logs verify new auth. (Cisco)
Use Case B — Guest sponsor approval -> grant full access
- Cloud portal creates guest via ERS → ISE stores guest. Sponsor approves → ISE triggers CoA to lift redirect ACL and assign Full Access profile.
- Validation: Client browser now can access internet;
show aaa server radius dynamic-authorshows CoA transactions; ISE Live Logs show sponsor approve → CoA reauth success. (Network Journey, Cisco DevNet)
Use Case C — AD group change promotes user to higher role
- AD membership change triggers automation that calls ISE API to run reauth on user’s MAC. ISE reauth runs and returns new Authorization Profile (higher VLAN).
- Validation:
show authentication sessions interfaceshows new VLAN; check syslogs for successful CoA. (Cisco DevNet)
Use Case D — Emergency disconnect for compromised device
- SOC identifies compromised IP or username → call ISE CoA Disconnect API (or use GUI Live Logs Disconnect).
- Validation: NAD logs show session termination; client loses connectivity. Use packet capture to observe CoA-Request/CoA-Ack exchange. (Cisco DevNet)
FAQs – Cisco ISE RADIUS CoA
Q1. Why is CoA critical in Cisco ISE deployments?
Answer:
Without CoA, users remain stuck in their initial authorization state until session termination. CoA allows on-demand reauthorization — enabling posture changes, guest upgrades, or quarantine instantly, without forcing users to disconnect.
Q2. What RADIUS ports are used for CoA?
Answer:
- Default UDP port: 1700 (older NADs)
- Newer platforms: 3799 (RFC 5176 compliant)
Check on switch:
show running-config | include dynamic-author
You’ll see port 1700 or port 3799.
Q3. How do I check if CoA is enabled on my Catalyst switch?
Answer:
Run:
show aaa servers
Look for:
- Dynamic author enabled
- CoA requests successfully processed
If missing, configure:
aaa server radius dynamic-author client <ISE_IP> server-key <key> port 1700
Q4. My ISE says “CoA Sent” but the switch didn’t reauthorize. Why?
Answer:
Common causes:
- Wrong CoA port (1700 vs 3799 mismatch).
- NAD not configured with ISE’s IP in
aaa server radius dynamic-author. - ACL/dACL download failed — verify with:
show ip access-lists show access-session interface Gi1/0/10 details
Q5. Can CoA push dACLs and VLAN changes simultaneously?
Answer:
Yes. CoA can deliver multiple authorization attributes:
- VLAN ID change
- Downloadable ACL (dACL)
- SGT (TrustSec)
But some NADs may need a Port Bounce CoA to apply VLAN change correctly.
Q6. How do I verify that a CoA packet actually reached the switch?
Answer:
- On ISE → Operations > RADIUS > Live Logs (look for CoA Sent).
- On switch → enable debug:
debug radius debug aaa authorization
Expected message: Received CoA Request from x.x.x.x.
Q7. Does CoA work for both wired and wireless clients?
Answer:
Yes.
- Wired (Catalyst Switches) → CoA applies dACL/VLAN changes.
- Wireless (WLC/9800) → CoA applies VLAN/dACL, may also trigger session reauth.
Validation on WLC:
show client detail <MAC>
Q8. Is CoA required for Posture assessment with AnyConnect?
Answer:
Absolutely. Posture uses initial limited access (Quarantine ACL) → then after compliance → ISE triggers CoA Reauth → new ACL or VLAN applied. Without CoA, posture workflows fail.
Q9. How do I troubleshoot if CoA fails intermittently?
Answer:
- Confirm NAD and ISE time are in sync (NTP).
- Check for CoA retransmissions:
show aaa servers show radius statistics - Ensure no firewall/ACL blocks UDP 1700/3799 between ISE and NAD.
- Wireshark capture on ISE → filter
udp.port == 1700.
Q10. Can CoA be used in Incident Response (Security Automation)?
Answer:
Yes — this is an advanced use case.
- ISE integrates with Firepower/Stealthwatch/pxGrid.
- If a compromised host is detected → ISE sends CoA Session-Terminate or Port Bounce → moves device to Quarantine VLAN.
This gives SOC teams instant containment without waiting for user logout.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes (key takeaways)
- CoA is essential for dynamic, real-time enforcement — it’s how ISE changes the network experience after authentication. (IETF Datatracker)
- CoA requires careful NAD configuration (dynamic-author client entries, matching secrets, correct CoA port) and reliable network reachability (firewall/VPN/DTLS as appropriate). (Cisco)
- Test thoroughly: GUI Live Logs, NAD CLI
showcommands, and packet captures for CoA packets. For automation, use DevNet Monitoring/CoA REST APIs on the Monitoring node. (Cisco DevNet, Cisco)
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro
I run a focused 4-month instructor-led training covering CCIE Security skills. This program is designed for network engineers who want to master CCIE Security and advance their careers
Join the training here and take your first step towards becoming a CCIE Security expert.
RESERVE YOUR SPOT :
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



![[Day 121] Cisco ISE Mastery Training: Automated Guest User Creation via API](https://networkjourney.com/wp-content/uploads/2025/08/Day-121-Cisco-ISE-Mastery-Training-Automated-Guest-User-Creation-via-API.png)