[Day 144] Cisco ISE Mastery Training: Automated Remediation for Non‑Compliance
Table of Contents
Introduction
In modern enterprise networks, compliance is dynamic. Users’ devices may fall out of compliance due to outdated antivirus, missing patches, disabled firewalls, or unapproved apps. Manual remediation is slow, error-prone, and disrupts productivity.
Automated Remediation in Cisco ISE transforms NAC from static enforcement into dynamic, real-time endpoint governance. When a device is non-compliant, ISE can:
- Automatically quarantine or restrict access
- Trigger Change of Authorization (CoA) on network devices
- Notify users to remediate the issue
- Grant full access once compliance is restored
This Article covers complete hands-on lab implementation, GUI/CLI validation, troubleshooting, and real-world expert use cases.
Problem Statement
Enterprises face:
- Endpoints frequently falling out of compliance due to human error or automated updates
- Manual remediation consuming IT resources and delaying access
- Difficulty enforcing consistent policies across wired, wireless, and VPN networks
- Risk of data exposure or malware propagation from non-compliant devices
Without automated remediation, organizations lose control over endpoint security posture and risk policy violations.
Solution Overview
Cisco ISE addresses these challenges through:
- Continuous Posture Assessment: Using AnyConnect/NAC Agent, endpoints report compliance in real-time.
- Dynamic Enforcement via CoA: When non-compliance is detected, ISE sends CoA to NADs/WLCs to apply quarantine VLANs or restricted ACLs.
- User Notification & Self-Remediation: Endpoint agents notify users of required actions, reducing IT workload.
- Policy-Based Full Access Recovery: Once endpoints resolve non-compliance, ISE automatically restores full access.
- Reporting & Auditing: Live Logs and Posture Reports track compliance trends and remediation success.
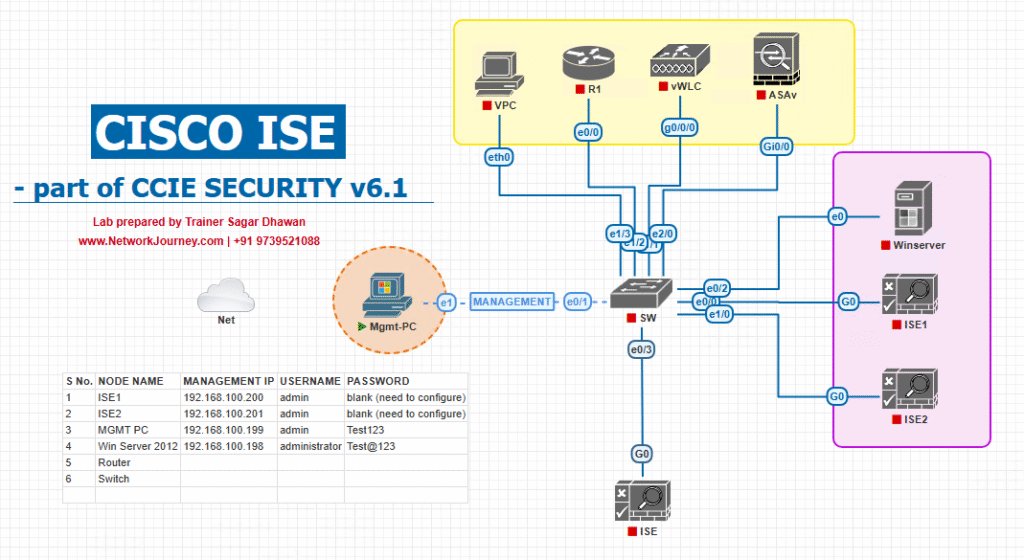
Sample Lab Topology
Lab Components:
- ISE Node (PAN/PSN) – 3.1+
- Endpoints – Windows 10, macOS, Android (with NAC/AnyConnect agent)
- Switch – Catalyst 9300 (802.1X + CoA)
- WLC – Cisco 9800 (Wi-Fi 802.1X + CoA)
- VMware/EVE‑NG – Lab network, DHCP/DNS, AD + PKI
- AD + PKI – For certificate-based authentication
Lab Topology:
Step‑by-Step GUI Configuration Guide
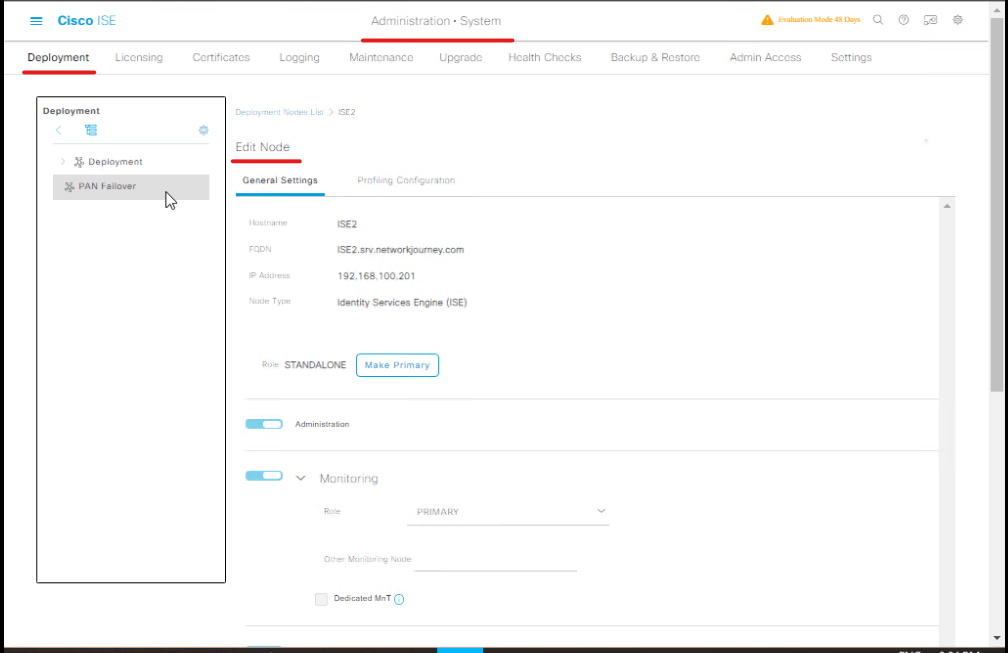
Step 1: Enable Posture Service
- Log in to ISE Admin GUI → Administration → System → Deployment.
- Select the ISE node (PAN/PSN).
- Click Edit Node → Services → Posture Service → Enable.
- Save changes and ensure Posture Service status is Running.
- [Screenshot: ISE Posture Service Enabled]
Validation:
- Navigate Operations → Posture → Endpoints → verify node is listed.
Step 2: Configure Endpoint Profiles
- GUI: Administration → Network Resources → Endpoints → Endpoint Profiles → Add
- Define profile for endpoint type: Windows, macOS, Android.
- Enable Posture Agent support → AnyConnect / NAC Agent.
- Save profile.
- [Screenshot: Endpoint Profile Configuration]
Validation:
- Connect test endpoint → Live Logs → Endpoint detected.
Step 3: Create Posture Conditions
Step 3a: Antivirus Check
- GUI: Policy → Policy Elements → Results → Posture → Conditions → Add
- Name:
AV_Compliant - Type: Endpoint Security → Attribute: Antivirus Status
- Operator: Equals → Value: Running / Up-to-Date
- [Screenshot: Posture Condition – Antivirus]
Step 3b: Firewall Enabled
- Add new condition → Name:
Firewall_Enabled - Type: Endpoint Security → Firewall Status → Equals → Enabled
- [Screenshot: Posture Condition – Firewall]
Step 3c: OS Patch Level
- Add new condition → Name:
OS_Patched - Type: OS → OS Version → Greater than or equal → e.g., 10.0.19042
- [Screenshot: Posture Condition – OS Patch]
Step 3d: Required Application Installed
- Add new condition → Name:
App_Check - Type: Application → Installed Applications → Equals → Zoom OR Slack
- Logical operator = OR (between apps)
- [Screenshot: Posture Condition – Application]
Validation:
- Operations → Posture → Posture Reports → simulate endpoint → ensure each condition evaluates.
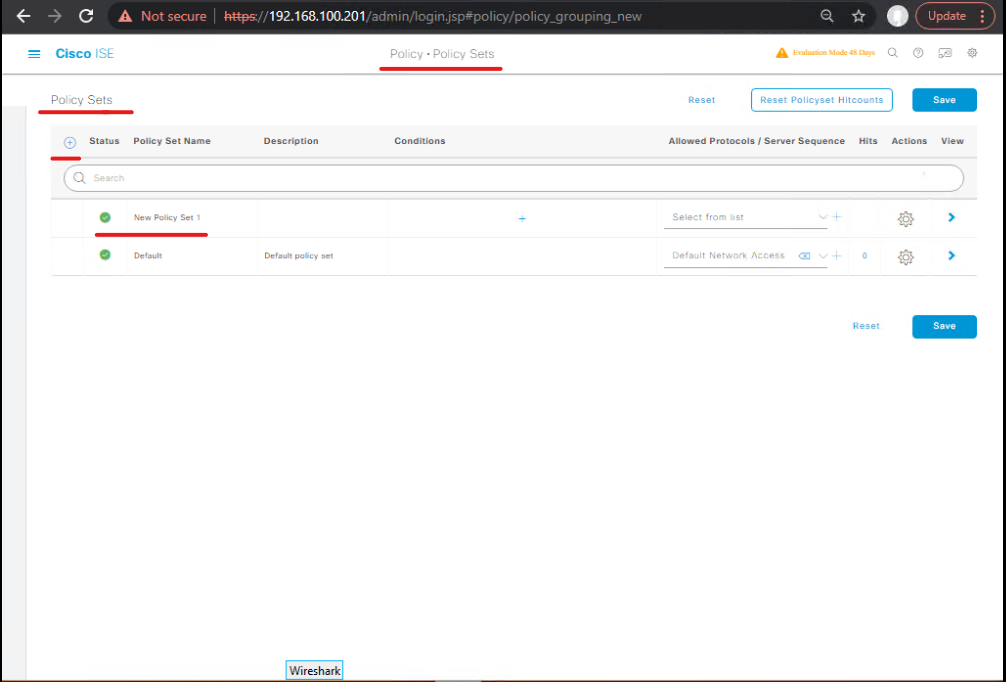
Step 4: Create Posture Policy with Automated Remediation
- GUI: Policy → Policy Sets → Posture Policy → Add New
- Name:
Automated_Remediation_Policy - Configure multi-condition logic:
IF (AV_Compliant = True) AND (Firewall_Enabled = True) AND (OS_Patched = True) AND (App_Check = True) THEN Full_Access_Profile ELSE Quarantine_Profile + CoA
- Enable Automated Remediation / CoA Trigger → sends change of authorization to NAD.
- [Screenshot: Automated Remediation Policy]
Validation:
- Connect a non-compliant endpoint → Live Logs → check that Quarantine Profile applied and CoA sent.
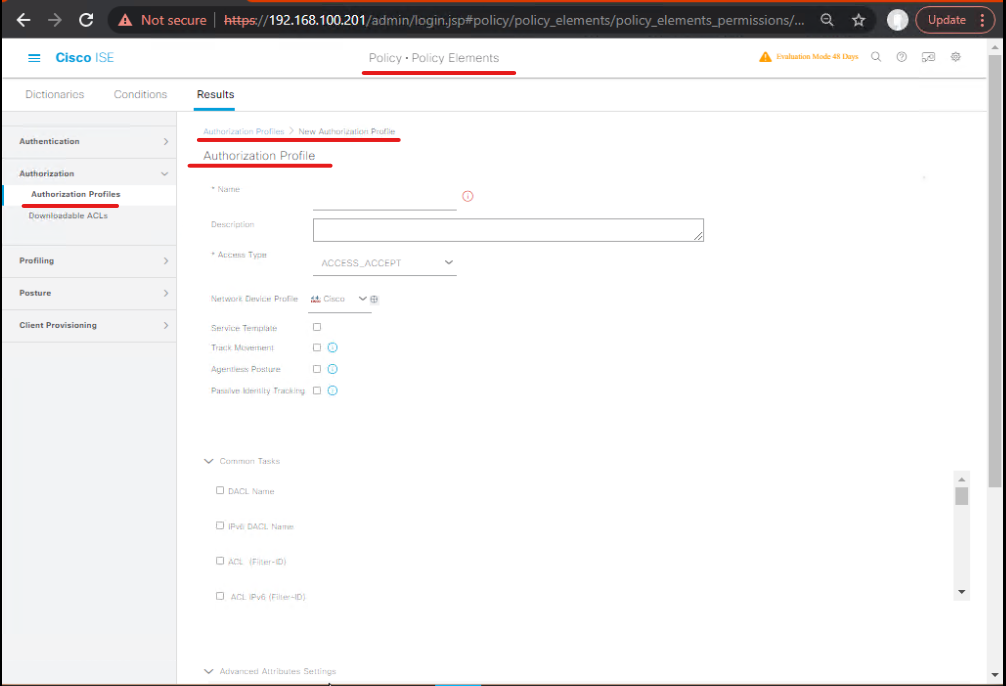
Step 5: Configure Authorization Profiles
Step 5a: Full Access
- GUI: Policy → Policy Elements → Results → Authorization → Authorization Profiles → Add
- Name:
Full_Access_Profile - Access: Permit → VLAN 20 / SGT 20
- Enable CoA for dynamic updates.
- [Screenshot: Full Access Authorization Profile]
Step 5b: Quarantine / Limited Access
- Add new Authorization Profile → Name:
Quarantine_Profile - Access: Deny / restricted VLAN (e.g., VLAN 99)
- Enable CoA for automated remediation.
- [Screenshot: Quarantine Authorization Profile]
Validation:
- Endpoint connects → Live Logs shows correct profile assigned → VLAN/ACL applied.
Step 6: Configure NAD (Switch/WLC) for 802.1X + CoA
Step 6a: Switch CLI
aaa new-model radius server ISE address ipv4 10.10.10.10 auth-port 1812 acct-port 1813 key VerySecret123 ! dot1x system-auth-control interface Gi1/0/10 switchport mode access authentication port-control auto dot1x pae authenticator mab
Validation:
- CLI:
show authentication sessions interface Gi1/0/10 detail→ Authorization Profile shows Quarantine / Full Access
Step 6b: WLC GUI
- Controller → Security → AAA → RADIUS → New
- Add ISE IP, Auth/Acct port, Shared Key
- WLAN → Security → Layer 2 → WPA2 802.1X → assign RADIUS server
- Enable CoA
- [Screenshot: WLC RADIUS + CoA]
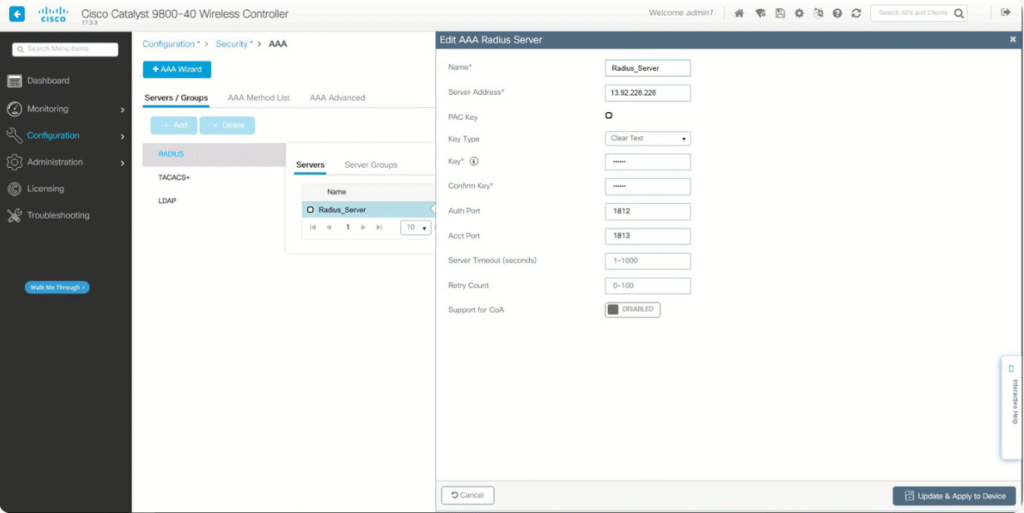
Validation:
- Wireless endpoint → Live Logs → Posture evaluation triggered → correct profile applied
Step 7: Endpoint Agent Configuration
- Install AnyConnect / NAC Agent
- Enable Posture Module
- Connect endpoint → ISE evaluates posture → applies Full Access or Quarantine
- [Screenshot: AnyConnect Posture Module]
Validation:
- Live Logs → Compliance status displayed
- Switch/WLC CLI → Authorization Profile updated
Step 8: Test Automated Remediation
- Scenario: Non-Compliant Endpoint
- Missing app → connects → quarantined VLAN 99
- Endpoint installs missing app → Posture Module detects compliance
- ISE sends CoA → VLAN updated → Full Access granted
Validation:
- Live Logs → Compliance = Compliant
- Switch CLI → Authorization Profile updated
- Endpoint → Network functional
Troubleshooting & Diagnostics
1. Key Diagnostic Tools
| Tool | Purpose | Location / CLI |
|---|---|---|
| ISE Live Logs | Real-time visibility into authentication and posture events | Operations → Live Logs → filter by Endpoint/Posture |
| Posture Reports | Track endpoint compliance history | Operations → Reports → Posture → Device Compliance |
| Endpoint Details | Per-endpoint posture evaluation | Operations → Endpoints → select endpoint → Posture Results |
| CLI Debugs | Detailed troubleshooting of CoA, posture, RADIUS | debug ise postureservice / debug radius / show authentication sessions interface GiX/X detail |
| Endpoint Agent Logs | Endpoint-side condition evaluation | AnyConnect/NAC Agent → Posture Module → logs |
2. Common Issues & Step-by-Step Diagnostics
| Issue | Symptom | Diagnostics | Resolution | Validation |
|---|---|---|---|---|
| CoA not triggering | Endpoint remains quarantined | GUI: Check CoA enabled in Authorization ProfileCLI: debug radius, show authentication sessions interface | Enable CoA on Authorization Profile and NAD; check UDP ports 1700/3799 | Live Logs → CoA sent; Switch CLI → profile updated |
| Endpoint stuck Non-Compliant | Fails AV, Firewall, or App conditions | Live Logs → check which condition failedEndpoint logs | Verify agent installed; adjust posture conditions or logic | Endpoint updates → Live Logs shows compliance |
| Fluctuating compliance | Endpoint alternates Compliant/Non-Compliant | Endpoint logs → check polling intervalNetwork stability | Adjust polling; ensure stable network connectivity | Live Logs stable, endpoint consistently Compliant |
| App detection fails | Required application not detected | GUI: Condition definitionEndpoint: agent logs | Correct condition syntax, verify app installed | Live Logs → condition True |
| Endpoint never reaches Full Access | Policy misconfigured | Posture Policy logic check (AND/OR, all conditions included) | Correct multi-condition logic | Live Logs → Full Access applied |
CLI Commands for Troubleshooting
- Check endpoint authentication & posture status
show authentication sessions interface GiX/X detail
- Debug radius / CoA issues
debug radius debug ise postureservice
- View live posture evaluations
show logging application ise postureservice
- Check CoA delivery and NAD response
debug dot1x all
GUI Validation Checklist
- Live Logs → Non-Compliant / Compliant endpoints
- Endpoint → Posture Module logs → condition results
- Authorization Profile → VLAN/ACL applied
- NAD → session shows correct authorization & CoA applied
- Reports → Posture → Device Compliance → historical validation
Lab Walkthroughs with Validation
Scenario 1: Non-Compliant Endpoint Automatically Remediated
- Endpoint missing a required app → connects → Quarantined VLAN applied
- Live Logs → Posture Evaluation = Non-Compliant
- User installs missing app → AnyConnect/NAC Agent detects fix
- ISE sends CoA → VLAN updated → Full Access granted
Validation:
- Switch CLI:
show authentication sessions interface GiX/X detail→ Full Access profile applied - Endpoint logs → Posture Module shows condition passed
- Live Logs → Compliance updated to True
Scenario 2: AV Outdated Endpoint
- Endpoint AV outdated → Quarantine Profile applied
- User updates AV → Agent detects compliance
- ISE triggers CoA → Full Access applied
Validation:
- Live Logs → AV_Compliant = True
- Switch/WLC → Authorization Profile updated
- Endpoint → Network access restored
Scenario 3: Multi-App Compliance
- Endpoint missing Finance App2 → Non-Compliant → VLAN 50 Quarantine
- User installs App2 → Agent reports compliance → CoA triggers
- VLAN restored → Full Access to Finance VLAN
Validation:
- Live Logs → Multi-condition evaluation per app
- Switch CLI → Authorization Profile shows Full Access
- Endpoint → App connectivity verified
Expert Level Use Cases (Step-by-Step Mapping + Validation)
Use Case 1: BYOD Automated Remediation
- Step 1: Endpoint Profile = BYOD
- Step 2: Posture Policy = AV, Firewall, OS, Required Apps
- Step 3: Authorization Profile = Quarantine VLAN if non-compliant
- Step 4: Endpoint updates app or patch → ISE triggers CoA → Full Access
- Validation: Live Logs → Compliance True; Switch/WLC → VLAN updated dynamically
Use Case 2: Corporate Laptops Full Access
- Step 1: Endpoint Profile = Corporate Device
- Step 2: Posture Policy = AV + Firewall + OS + App
- Step 3: Authorization Profile = Full Access VLAN
- Step 4: Endpoint connects → automatically evaluated → Full Access granted
- Validation: Live Logs → All conditions True; Endpoint → Network access functional
Use Case 3: Finance VLAN Multi-App Enforcement
- Step 1: Posture Policy = Finance App1 AND App2 + AV + Firewall
- Step 2: Authorization Profile = Finance VLAN (restricted)
- Step 3: Endpoint connects missing App2 → Non-Compliant → VLAN restricted
- Step 4: Install missing app → CoA triggers → Full Access restored
- Validation: Live Logs → Posture evaluation per app; Switch CLI → VLAN updated
Use Case 4: Dynamic Patch Compliance
- Step 1: Endpoint OS patch missing → Non-Compliant → Quarantine VLAN
- Step 2: Endpoint applies patch → Agent detects compliance
- Step 3: ISE triggers CoA → Full Access applied automatically
- Validation: Live Logs → OS_Patched condition True; Switch CLI → Authorization updated
Use Case 5: Custom Posture Modules (CPM)
- Step 1: Script checks for custom service/process
- Step 2: Include CPM in multi-condition policy
- Step 3: Endpoint executes script → ISE evaluates result
- Step 4: Non-compliant → Quarantine; Compliant → Full Access
- Validation: Live Logs → CPM condition evaluated; Endpoint logs → shows script result
FAQs – Automated Remediation for Non‑Compliance
1. Q: Why isn’t CoA triggering when a previously non-compliant endpoint becomes compliant?
A:
- Check Authorization Profile → CoA must be enabled.
- Ensure NAD supports CoA (UDP 1700/3799 open).
- Validate via CLI:
show authentication sessions interface GiX/X detail debug radius
- Live Logs: confirm CoA sent event.
2. Q: How do I differentiate BYOD from corporate devices for automated remediation policies?
A:
- Use Endpoint Profiles with ownership attribute (BYOD / Corporate).
- Assign different posture policies and Authorization Profiles per type.
- Validate by connecting a BYOD endpoint → ensure proper policy triggers in Live Logs.
3. Q: Can I enforce multiple applications alongside AV, firewall, and OS patch conditions?
A:
- Yes, create a multi-condition posture policy using AND/OR logic.
- Example:
AV AND Firewall AND OS AND (App1 OR App2) - Validate each condition via Posture Result Details in Live Logs.
4. Q: How can I verify that each condition in a multi-condition policy is evaluated correctly?
A:
- GUI: Operations → Posture → Live Logs → select endpoint → Posture Result Details
- Endpoint: AnyConnect / NAC Agent logs → each condition listed True/False
- CLI: debug postureservice → confirm evaluation sequence
5. Q: What happens if the NAD doesn’t support CoA?
A:
- Endpoint remains in its current VLAN/profile until next authentication
- Workarounds:
- Upgrade NAD firmware
- Use fallback VLAN / restricted ACL policy
- Validate by testing endpoint remediation → VLAN/profile change expected to fail
6. Q: How can I test automated remediation before production rollout?
A:
- Set up lab endpoints simulating non-compliance scenarios: missing apps, outdated AV, firewall disabled
- Connect endpoints → observe Live Logs for posture evaluation
- Fix issues → ensure CoA triggers and full access restored
- Validate via switch/WLC CLI and endpoint network access
7. Q: Can endpoint agents notify users automatically about non-compliance?
A:
- Yes, enable AnyConnect / NAC Agent notifications
- Configure Posture Module to display required actions (e.g., install app, enable firewall)
- Validation: endpoint user sees pop-up → completes remediation → Live Logs shows compliance
8. Q: How do I troubleshoot endpoints that fluctuate between compliant and non-compliant?
A:
- Check agent polling interval (too frequent can cause false negatives)
- Validate network stability between endpoint and ISE
- CLI:
show authentication sessions interface GiX/X detail,debug ise postureservice - Endpoint logs → review Posture Module evaluation timestamps
- Adjust settings → ensure stable compliance evaluation
9. Q: Does automated remediation work for VPN sessions as well?
A:
- Yes, if AnyConnect NAC Agent is installed and Posture Module enabled
- Posture policies can be applied to VPN connections → CoA triggers once compliant
- Validation: connect via VPN → check Live Logs → Authorization Profile update after remediation
10. Q: Can custom scripts (Custom Posture Modules) be used for automated remediation?
A:
- Yes, CPM can check custom processes, services, registry values, or files
- Include CPM in multi-condition posture policy
- Endpoint executes script → result evaluated by ISE → triggers remediation
- Validation: Live Logs → CPM condition True/False, endpoint profile updated, network access restored
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- Automated remediation reduces IT effort, increases security, and maintains productivity.
- Key components: Posture Service, Multi-Condition Policies, CoA, Authorization Profiles, Endpoint Agent.
- Validate every component: Live Logs, switch/WLC CLI, endpoint logs.
- Combine with BYOD, corporate devices, and multi-app policies for real-world production readiness.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join the instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro — 4-month live training. Full labs, real-world automated remediation scenarios.
Course outline: https://course.networkjourney.com/ccie-security/
- Hands-on labs
- Real-world posture and remediation enforcement
- CoA & dynamic policy training
- BYOD + corporate automated compliance
“Reserve Your Seat – Download Free Lab Workbook”
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088


![[Day 22] Cisco ISE Mastery Training: MAB (MAC Authentication Bypass) Configuration](https://networkjourney.com/wp-content/uploads/2025/08/Day-22-Cisco-ISE-Mastery-Training-MAB-MAC-Authentication-Bypass-Configuration.png)
