[Day 145] Cisco ISE Mastery Training: Security Audit & Policy Review
Table of Contents
Introduction
In modern network architectures, visibility and control over endpoints are critical. Cisco Identity Services Engine (ISE) allows organizations to enforce consistent security policies across wired, wireless, and VPN networks. Security Audit & Policy Review is a pivotal feature in ISE, enabling administrators to proactively validate that all network access policies are aligned with compliance, security standards, and operational expectations.
This Article focuses on empowering engineers to perform a comprehensive security audit, validate policy configurations, identify gaps, and ensure real-time enforcement consistency. By the end of this session, learners will not only understand the theory but gain hands-on mastery in GUI and CLI-based validation, effective troubleshooting, and policy optimization.
Problem Statement
Organizations often struggle with the following challenges:
- Policy Drift: Over time, policies configured in ISE may diverge from intended corporate security mandates, leading to security gaps.
- Audit Compliance: Regulatory compliance frameworks (e.g., PCI-DSS, ISO 27001) require proof of access controls and monitoring.
- Endpoint Misclassification: Without regular audits, devices may be incorrectly classified, resulting in inappropriate network access.
- Complex Multi-Condition Policies: Large-scale networks implement multi-condition policies based on device type, posture, location, or user role, which can create hidden conflicts.
- Ineffective Enforcement: Misconfigured authorization rules can lead to endpoint access failures or over-permissive access.
Impact: Security breaches, compliance violations, and operational inefficiencies.
Solution Overview
Cisco ISE provides:
- Policy Validation Tools: Audit tools for endpoint, policy, and certificate validation.
- Real-Time Monitoring: Live authentication logs, session tracking, and policy hit counters.
- Reporting: Predefined and customizable compliance and policy reports.
- CLI & GUI Integration: Enables administrators to validate policies using GUI dashboards or detailed CLI queries.
- Policy Troubleshooter: Stepwise analysis of authentication and authorization flows.
By combining these features, engineers can proactively identify misconfigurations, verify enforcement, and document compliance, ensuring a secure and auditable network environment.
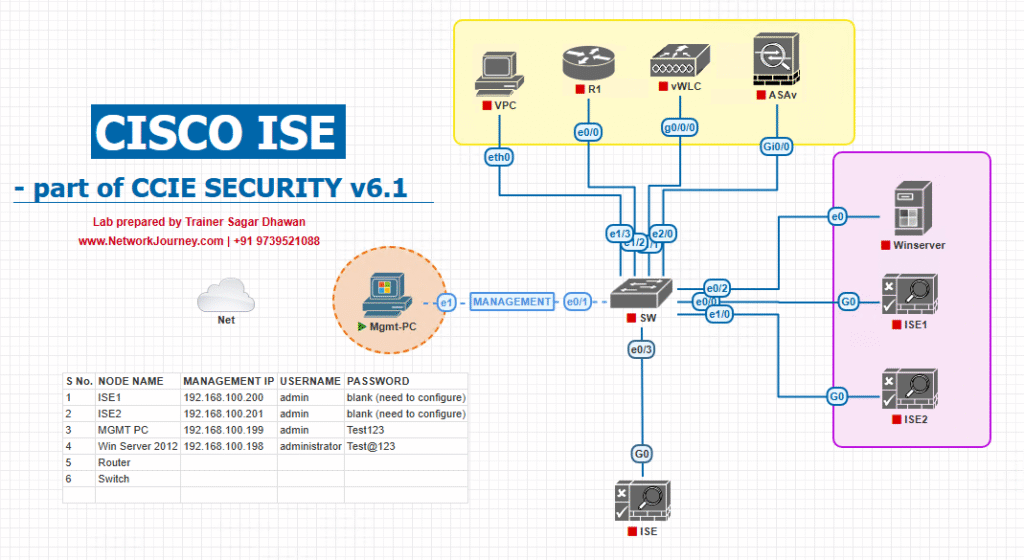
Sample Lab Topology
Lab Environment: VMware or EVE-NG
Topology Components:
- Cisco ISE: 2 nodes (Primary Admin + Secondary PSN)
- Core Switches: Cisco Catalyst 9300
- Access Switches: Cisco Catalyst 9200
- WLC: Cisco 9800 Wireless Controller
- Endpoints: Laptops, iOS/Android devices, IoT devices
- RADIUS/LDAP Servers: For identity validation
Diagram :
Step-by-Step GUI Configuration Guide
Objective: Validate and audit existing ISE policies and generate actionable reports.
Step 1: Log in to Cisco ISE GUI
- URL:
https://<ISE-IP>:9060/ - Credentials: Admin account with SuperAdmin privileges
- Navigate: Administration → System → Deployment
[Screenshot: ISE Dashboard]
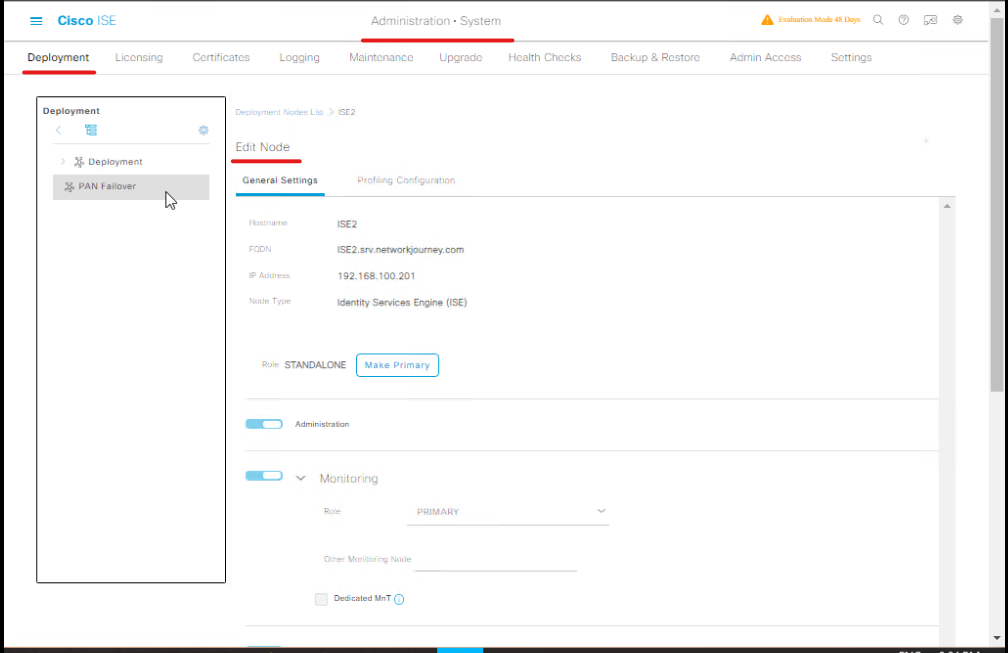
Step 2: Verify Node Health
- Go to Administration → System → Deployment
- Check PSN/ PAN status: Should be
Active - CLI Command:
show ise nodes
Validation: Node status should be UP and Reachable.
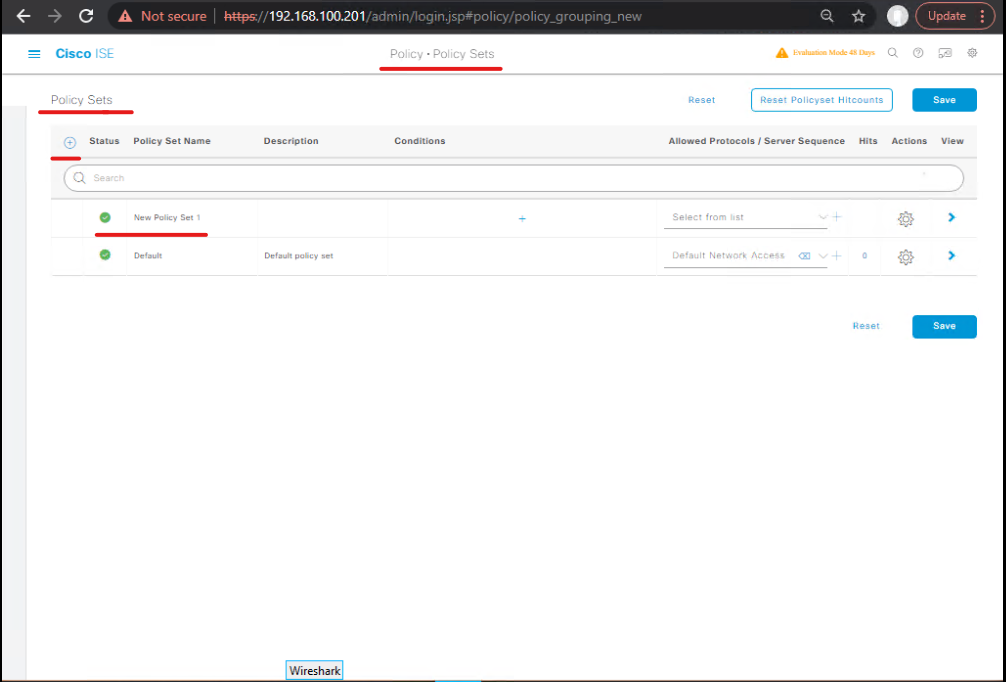
Step 3: Policy Set Review
- Navigate: Policy → Policy Sets
- Open each policy set
- Verify:
- Conditions (Device Type, User Group, Endpoint Identity)
- Authentication Methods (EAP-PEAP, 802.1X)
- Authorization Profiles
[Screenshot: ISE Policy Set Screen]
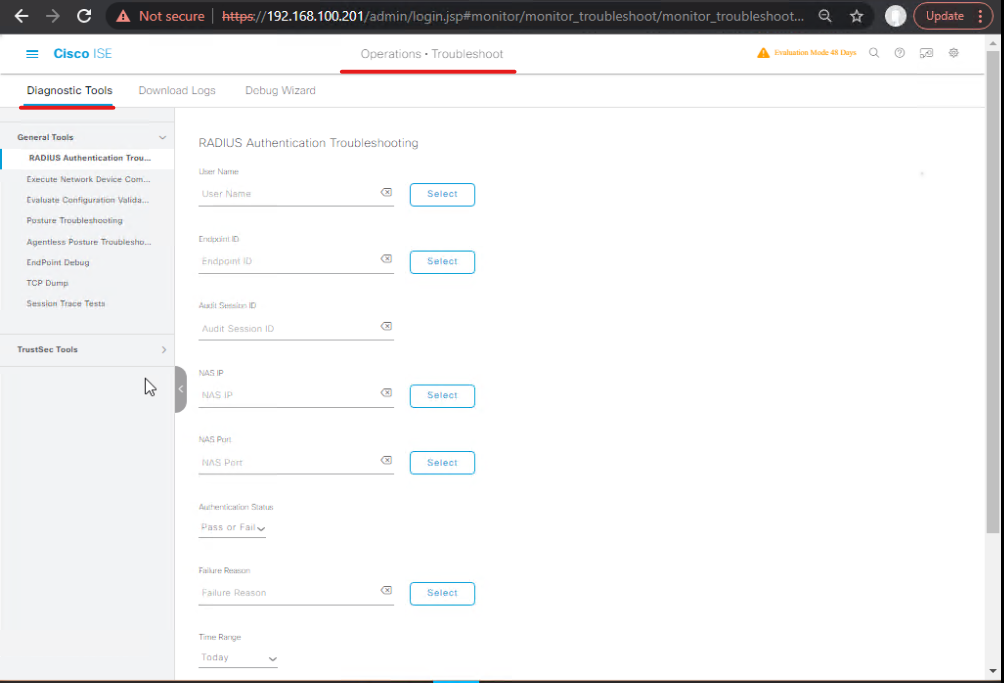
Step 4: Authorization Rules Audit
- Check for overlapping or conflicting rules.
- CLI Verification:
show running-config ise show authentication sessions
- Use Policy Troubleshooter:
- Navigate: Operations → Policy → Policy Troubleshooter
- Enter endpoint MAC/IP
- Analyze the flow step-by-step
[Screenshot: Policy Troubleshooter]
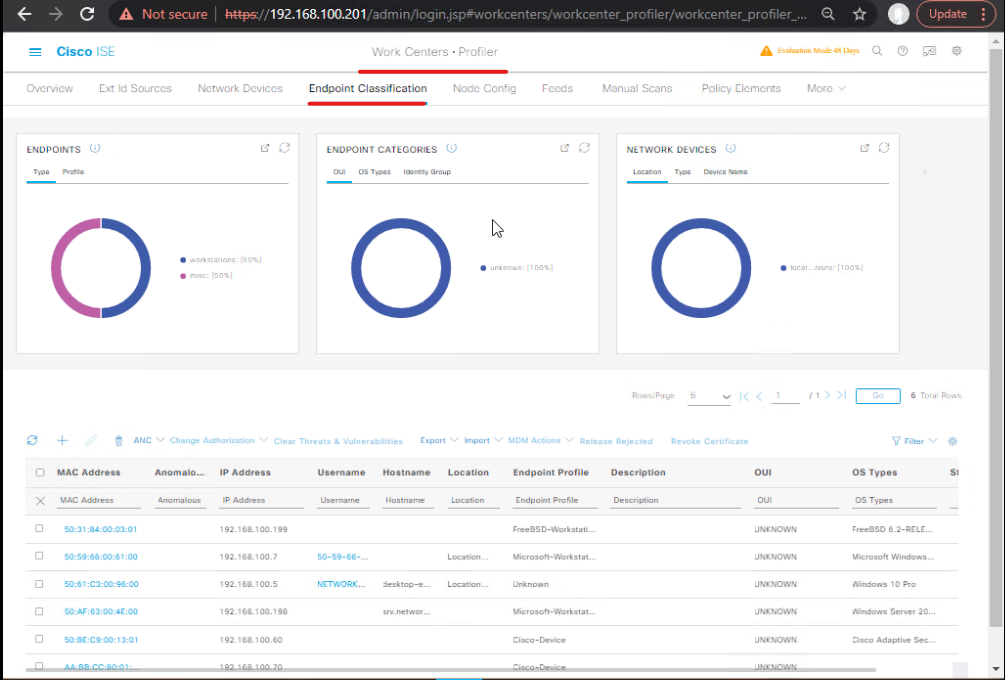
Step 5: Endpoint Classification Audit
- Navigate: Work Centers → Endpoints → All Endpoints
- Validate:
- Endpoint type
- Device profiling attributes
- Correct misclassified endpoints manually if needed
[Screenshot: Endpoint Classification]
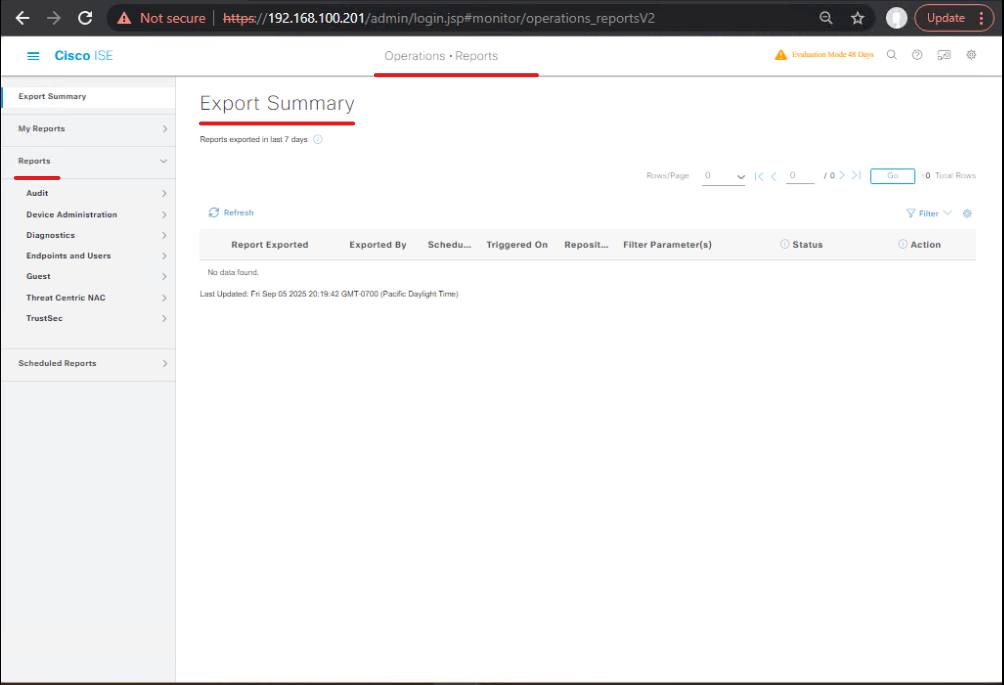
Step 6: Reports & Compliance Audit
- Navigate: Operations → Reports
- Generate reports:
- Authentication Success/Failure
- Authorization Hits
- Endpoint Device Profiling
- Compliance Reports
- Export to CSV or PDF for documentation
[Screenshot: Reports Module]
Step 7: CLI-Based Validation
show logging application ise show authentication sessions show radius statistics
Validation: Confirm authentication successes/failures, policy hits, and endpoint classifications.
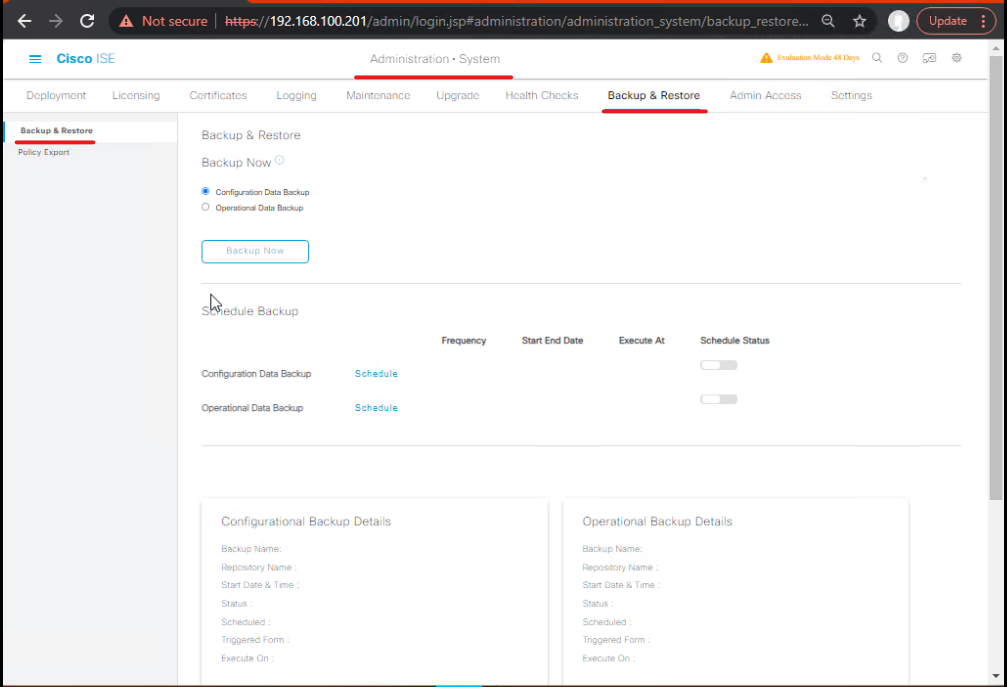
Step 8: Backup Configuration
- Navigate: Administration → System → Backup & Restore
- Schedule backup
- Ensure policy & endpoint database included
[Screenshot: Backup Config]
Troubleshooting & Diagnostics
Common Issues:
- Endpoint cannot authenticate
- Misclassification of devices
- Policy conflicts causing access denial
Diagnostics Steps:
- Use Policy Troubleshooter
- Check RADIUS logs (
show radius statistics) - Validate network device configuration for 802.1X or MAB
- Verify certificates for EAP methods
- CLI commands:
show logging application ise | include <endpoint> debug radius all show running-config ise
- Validate network connectivity to ISE nodes
Lab Walkthroughs with Validation
Scenario 1: Endpoint Denied Access
- Steps:
- Trigger authentication
- Use Policy Troubleshooter
- Identify which condition blocked the endpoint
- Correct the authorization profile
- Validation: Endpoint should be able to access the network
Scenario 2: Compliance Reporting
- Generate All Authentication Success/Failures
- Compare against policy documentation
- Validate reports match real-time endpoint sessions
Expert-Level Use Cases
- Multi-Condition Authorization Rule Mapping
- User from Guest VLAN with iOS device → Limited access
- User from Corporate VLAN with Windows → Full access
- Validate using Policy Troubleshooter → check policy hits
- Rogue Device Detection
- Configure ISE to detect unknown endpoints
- Assign quarantine VLAN
- Validate using endpoint hit logs
- Automated Compliance Checks
- Scheduled report generation
- Auto-alert on policy violations
- CLI validation with cron jobs
FAQs
1. How do I perform a comprehensive security audit in Cisco ISE?
Answer:
- Use Reports → Security Audits in the GUI to review authentication, authorization, posture, and endpoint compliance.
- CLI:
show logging application ise show authentication sessions summary show authorization sessions
- Identify deviations from security policy and misconfigurations.
2. How can I validate that my ISE policy sets are correctly implemented?
Answer:
- GUI: Policy → Policy Sets → Policy Troubleshooter, input an endpoint or username.
- Verify the policy hit sequence, authentication method, and applied authorization profile.
- CLI:
show running-config iseandshow authentication sessions details.
3. How do I detect conflicting authorization rules?
Answer:
- Use Policy Troubleshooter to see which rule is applied and which ones are bypassed.
- Audit policy sets for overlapping conditions that may cause unintended access.
- CLI:
show authorization sessionsto validate actual profile applied to endpoints.
4. How can I audit endpoint compliance for posture policies?
Answer:
- GUI: Work Centers → Posture → Posture Reports.
- Check failed and successful endpoints, including compliance modules such as antivirus, disk encryption, and OS patch level.
- CLI:
show posture sessionsandshow compliance details.
5. How do I review and audit profiler rules for accuracy?
Answer:
- GUI: Work Centers → Profiler → Profiler Cache to verify device classification.
- CLI:
show profiler cacheandshow profiler statistics. - Ensure that all endpoint types are classified correctly and no unknown devices are misidentified.
6. How can I audit ISE logs for potential security issues?
Answer:
- GUI: Operations → Reports → Event Logs.
- CLI:
show logging application ise show logging application ise | include ERROR
- Look for repeated authentication failures, unauthorized access attempts, or policy misapplications.
7. How do I ensure AAA configuration and network device integration are secure?
Answer:
- GUI: Administration → Network Resources → Network Devices, validate shared secrets and device IPs.
- CLI:
show running-config | include radius show aaa servers
- Confirm devices are grouped correctly and secrets comply with security standards.
8. How can I generate audit-ready reports for compliance purposes?
Answer:
- GUI: Reports → Authentication & Authorization Reports, export in CSV or PDF.
- Include summaries for failed sessions, VLAN assignments, posture compliance, and policy hits.
- CLI: Use log exports or API integrations for automated auditing.
9. How do I validate changes after security policy updates?
Answer:
- GUI: Use Policy Troubleshooter to test authentication and authorization flows.
- CLI:
show authentication sessions details show authorization sessions
- Validate that endpoints are mapped to correct profiles and policies are enforced as intended.
10. How do I detect policy violations or gaps in enterprise NAC deployment?
Answer:
- GUI: Reports → Security Audits, filter for endpoints with unauthorized access or policy violations.
- Monitor Live Auth Sessions for anomalies.
- CLI:
show authentication sessions summaryandshow authorization sessionsto correlate applied profiles versus intended policies.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- Regular policy audits prevent security gaps
- GUI + CLI validation ensures complete coverage
- Reports and compliance dashboards are key for documentation
- Endpoint classification accuracy is critical
- Troubleshooting using Policy Troubleshooter saves time
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes. Hands-on labs, real-world scenarios, and expert tips ensure you move from beginner to pro faster than self-study ever could.
Fast-Track to Cisco ISE Mastery Pro
Join my 4-month instructor-led CCIE Security-focused training:
- Intensive Hands-On Labs: VMware/EVE-NG, multi-condition policies, endpoint profiling, policy auditing
- Expert Mentorship: Real-time troubleshooting, best practices
- Exam-Oriented Guidance: Learn exactly how Cisco evaluates configurations and policies
- Certificate of Completion: Industry-recognized proof of skills
- Register today at networkjourney.com/ccie-security
Don’t just learn ISE; master it, validate it, and enforce it like a real-world network security expert.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![Mobility Groups & Roaming – Seamless Wireless in Action [CCNP Enterprise]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/07/Mobility-Groups-Roaming-–-Seamless-Wireless-in-Action-CCNP-Enterprise.png)

