[Day 147] Cisco ISE Mastery Training: Upgrade Strategy & Downtime Reduction
Table of Contents
Introduction
Upgrading Cisco ISE in production environments can be a daunting task. ISE is central to authentication, authorization, and endpoint profiling for wired, wireless, and VPN networks, meaning that any downtime can directly impact users and services. The key to a successful upgrade lies in strategic planning, pre-validation, and downtime minimization.
This Article focuses on designing a robust upgrade strategy while ensuring zero or minimal disruption. Engineers will learn how to upgrade PAN, PSN, and MnT nodes, validate the upgrade, and implement rollback strategies using both GUI and CLI.
Mastering upgrade strategies ensures:
- Smooth migration to newer ISE versions
- Preservation of policies, certificates, and endpoints
- High availability continuity for large-scale networks
This day transforms learners into upgrade experts who can confidently manage ISE lifecycle in complex enterprise deployments.
Problem Statement
Organizations face multiple challenges during ISE upgrades:
- Service Disruption: PAN or PSN downtime can block authentication and authorization requests.
- Complex Topologies: Multi-node, multi-site deployments complicate upgrade sequencing.
- Policy Preservation: Existing authentication, authorization, profiling, and posture policies must remain intact.
- Certificate Compatibility: Certificates may fail after upgrade if not pre-validated.
- Rollback Planning: Without rollback procedures, failures can cause extended outages.
Impact: Authentication failures, policy enforcement gaps, compliance violations, and negative user experience.
Solution Overview
Cisco ISE provides upgrade mechanisms designed to minimize downtime:
- High Availability Awareness: PAN/PSN upgrades can be sequenced to maintain active authentication service.
- Pre-Upgrade Checks: Built-in Health Reports, Certificate Validation, and System Readiness tools.
- Backup & Restore: Full node and policy backups before upgrade.
- Stepwise Node Upgrade: Upgrade MnT → PSN → PAN for large deployments.
- Rollback Capability: Revert to previous version if upgrade fails.
By leveraging these mechanisms, engineers can implement a zero-downtime upgrade strategy while maintaining compliance and operational continuity.
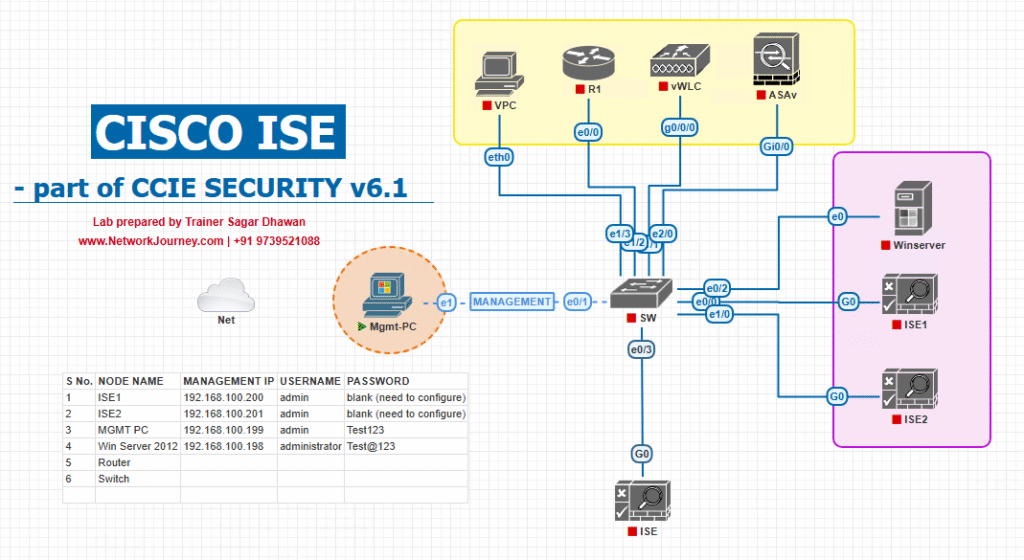
Sample Lab Topology
Lab Environment: VMware or EVE-NG
Components:
- ISE Nodes: PAN (Primary Admin Node), PSN1, PSN2, MnT node
- Switches: Catalyst 9300/9200
- WLC: Cisco 9800
- Endpoints: Windows/Linux laptops, IoT devices
- Simulated Authentication Traffic: 100–500 virtual endpoints
Diagram :
Notes:
- VMware: Full ISE appliances for upgrade testing
- EVE-NG: Virtual PSN and PAN nodes with simulated traffic
- Endpoints: Automated scripts for authentication simulation
Step-by-Step GUI Configuration Guide
Objective: Upgrade ISE nodes while minimizing downtime and ensuring rollback readiness.
Step 1: Pre-Upgrade System Validation
- Log in to ISE PAN GUI:
https://<PAN-IP>:9060/ - Navigate: Administration → System → Maintenance → Backup & Restore
- Take a full backup including:
- Configuration
- Policies
- Certificates
- Endpoints
[Screenshot: Backup Configuration]
CLI verification:
show backup status show running-config ise
Step 2: Pre-Upgrade Health Check
- Navigate: Administration → System → Health & Reports
- Validate:
- Disk space ≥ 20% free
- CPU < 60%
- Memory < 70%
- Resolve warnings before proceeding
[Screenshot: System Health Check]
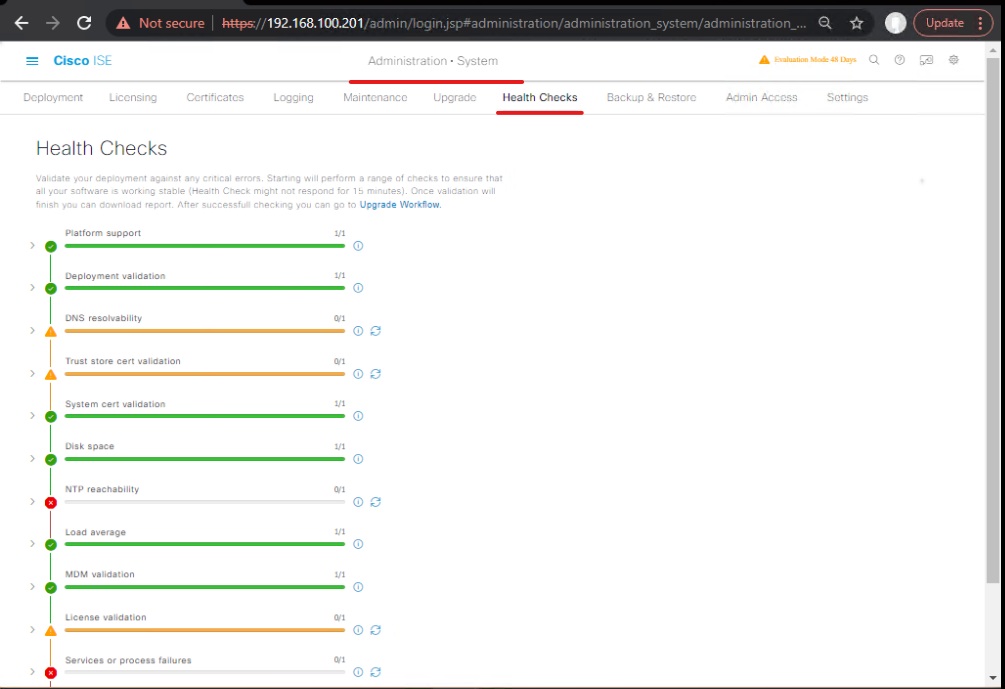
CLI:
show application status ise show system resources show logging application ise
Step 3: Certificate & Compatibility Validation
- Navigate: Administration → System → Certificates
- Check:
- Expiry dates
- Key lengths
- SAN matches
- Upgrade pre-requisites:
- OS and database versions compatible
- Licensing valid
[Screenshot: Certificate Validation]
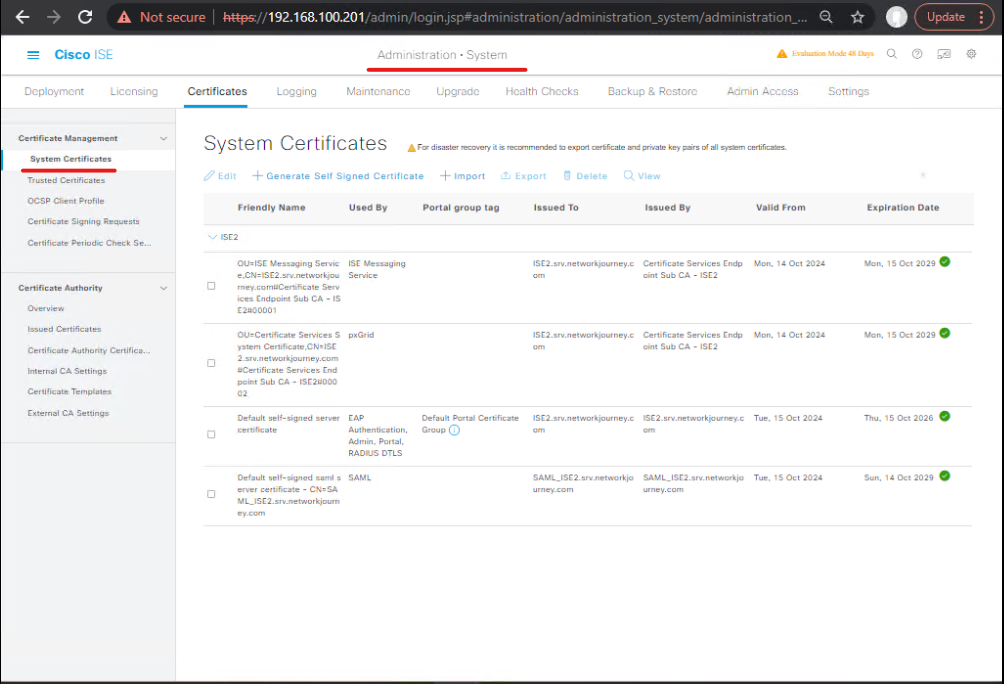
CLI:
show crypto certificate show license status
Step 4: Upgrade Planning & Sequencing
Recommended Sequence for High Availability:
- MnT node (monitoring and reporting)
- Secondary PSN
- Primary PSN
- PAN Node
This ensures active authentication continuity.
Step 5: MnT Node Upgrade
- Administration → System → Upgrade → Upload Image
- Select ISE ISO/Upgrade file
- Validate checksum
- Execute upgrade
- Monitor via GUI → Operations → Node Status
- CLI:
show application status ise show logging application ise
Validation: MnT is upgraded and functional.
Step 6: PSN Node Upgrade (Secondary First)
- Upload ISO
- Schedule upgrade (off-peak)
- Execute upgrade
- Monitor:
- Node availability
- Session throughput
- Authentication success
- CLI:
show running-config ise show authentication sessions show application status ise
Validation: PSN upgraded without interrupting authentication.
Step 7: PAN Node Upgrade
- Upload ISO
- Schedule upgrade during maintenance window
- Execute upgrade
- Monitor:
- GUI access
- Policy integrity
- Session continuity
- CLI:
show application status ise show system resources
Validation: All policies and endpoints remain intact.
Step 8: Post-Upgrade Validation
- Navigate: Operations → RADIUS → Live Auth Sessions
- Verify:
- All endpoints authenticated
- Policies applied correctly
- Generate post-upgrade reports for compliance documentation
[Screenshot: Post-Upgrade Reports]
Step 9: Rollback Procedure (if needed)
- Access backup via Administration → System → Backup & Restore
- Restore:
- Configuration
- Policies
- Certificates
- Reboot nodes sequentially to restore service
CLI:
backup restore ise reload ise
Validation: Service restored to pre-upgrade state.
Step 10: Optimization Post-Upgrade
- Validate:
- Profiling cache
- Authorization rule hit counts
- CPU/memory usage
- CLI:
show profiler cache show authentication sessions summary
Troubleshooting & Diagnostics
Common Issues:
- PAN node inaccessible after upgrade
- PSN authentication failures
- Policy mismatch or corruption
Diagnostics Steps:
- GUI: Operations → RADIUS → Live Auth Sessions
- CLI:
show application status ise show authentication sessions show running-config ise debug radius all
- Check backup integrity, certificates, and licensing
- Resolve by rolling back or patching node
Lab Walkthroughs with Validation
Scenario 1: Secondary PSN Upgrade
- Upgrade secondary PSN
- Validate active authentication continues via primary PSN
- CLI validation:
show authentication sessions summary
Scenario 2: PAN Upgrade
- Upgrade PAN node
- Validate GUI access, policy integrity, authentication continuity
- Post-upgrade reporting and monitoring
Expert-Level Use Cases
- Rolling Upgrade in Multi-Site Deployment
- Sequence: MnT → PSN (secondary) → PSN (primary) → PAN
- Validate each site individually
- CLI monitoring for distributed endpoints
- Zero-Downtime Upgrade with High Authentication Load
- Use simulated traffic (100–500 endpoints)
- Upgrade PSN nodes sequentially
- Validate live authentication with
show authentication sessions
- Certificate Renewal During Upgrade
- Upgrade while renewing expired or soon-to-expire certificates
- Validate authentication and policy hits post-upgrade
- Automated Upgrade Validation
- Scripts to validate:
- Policy application
- Session counts
- CPU/memory post-upgrade
- Scripts to validate:
FAQs
1. How can I minimize downtime during a PAN upgrade?
- Perform upgrades in a high-availability setup with multiple PANs if possible.
- Schedule upgrades during maintenance windows or off-peak hours.
- Upgrade secondary PAN first (if available) and switch over before upgrading the primary.
2. Can I upgrade PSN nodes without affecting authentication?
- Yes, by sequentially upgrading PSNs while others remain active.
- Ensure load balancing and HA configuration are validated before upgrade.
- Monitor live authentication sessions during the process.
3. What pre-checks are essential before performing an ISE upgrade?
- Backups of configuration, policies, endpoints, and certificates.
- System health checks: disk space, CPU, memory.
- Certificate validation: expiration dates, SAN entries, compatibility.
- License validation and OS/database version checks.
4. How do I validate certificates before an upgrade?
- Navigate: Administration → System → Certificates in GUI.
- Ensure all certificates are valid, unexpired, and supported by the target ISE version.
- CLI commands:
show crypto certificate show license status
5. What should I do if the upgrade fails?
- Immediately use the backup restore procedure:
- Administration → System → Backup & Restore → Restore
- Sequentially restore PAN, PSNs, and MnT if needed.
- Validate policies and authentication post-rollback.
6. Which CLI commands provide real-time node status during upgrade?
show application status ise show authentication sessions show system resources debug radius all
- These commands help monitor CPU, memory, session counts, and authentication flows.
7. How do I preserve policies and endpoints during an upgrade?
- Always take a full backup before the upgrade.
- Ensure backup includes:
- Configuration files
- Authentication & authorization policies
- Endpoint database
- Post-upgrade validation confirms policies and endpoints are intact.
8. How can I test the upgrade in a lab before production?
- Use VMware or EVE-NG to deploy replica nodes: PAN, PSNs, MnT.
- Simulate authentication traffic using radtest, eapol_test, or scripts.
- Perform the upgrade and validate GUI, CLI, and authentication workflows.
9. What is the recommended upgrade sequence in HA deployments?
- MnT node (monitoring/reporting)
- Secondary PSN
- Primary PSN
- PAN node
- This ensures authentication continuity and minimal downtime.
10. How do I verify successful upgrade and system health post-upgrade?
- GUI: Operations → RADIUS → Live Auth Sessions
- CLI:
show application status ise show authentication sessions summary show running-config ise show system resources
- Validate that all policies, endpoints, and certificates are correctly applied, and authentication is fully operational.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- Upgrades must be planned and sequenced carefully for minimal downtime
- Pre-upgrade backups, health checks, and certificate validation are mandatory
- Use GUI + CLI monitoring during upgrade for real-time validation
- Post-upgrade validation ensures policy integrity and service continuity
- Rolling upgrades and sequential node upgrades preserve high availability
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to Network Journey on YouTube and join my instructor-led classes. Learn step-by-step upgrade strategies, zero-downtime deployment, and advanced troubleshooting to become a Cisco ISE expert.
Fast-Track to Cisco ISE Mastery Pro
4-Month Instructor-Led CCIE Security Program:
- Hands-On Labs: VMware/EVE-NG upgrades, HA validation, multi-site scenarios
- Expert Mentorship: Stepwise guidance, troubleshooting, optimization
- Exam-Oriented Guidance: Real-world upgrade strategy simulations
- Certificate of Completion: Industry-recognized validation
- Register at networkjourney.com/ccie-security
Don’t risk downtime—master ISE upgrades with confidence.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088