[Day 148] Cisco ISE Mastery Training: Migration from Legacy NAC
Table of Contents
Introduction
Legacy NAC solutions—like Cisco NAC Appliance, Aruba ClearPass old versions, or third-party NAC tools—are often limited in flexibility, scalability, and integration with modern enterprise networks. Migrating to Cisco Identity Services Engine (ISE) is critical for organizations aiming to centralize policy enforcement, enable advanced profiling, and ensure compliance.
This Article dives deep into the step-by-step migration process, including planning, data import, policy replication, and endpoint continuity. You will learn to map legacy NAC policies into ISE, validate them using GUI and CLI, and troubleshoot any migration issues, all while maintaining network access continuity.
Mastering this topic empowers engineers to modernize network access control safely, avoiding authentication failures and minimizing downtime.
Problem Statement
Organizations migrating from legacy NAC often face these real-world challenges:
- Policy Translation: Legacy NAC policies may not map one-to-one to ISE authorization rules.
- Endpoint Continuity: Ensuring all existing endpoints remain authenticated during migration.
- Profiling & Posture: Legacy NAC may lack modern profiling; migrating these capabilities requires careful validation.
- Certificate Management: Existing 802.1X certificates must be migrated or reissued.
- Multi-Vendor Environment: Mixed switches, WLCs, VPN gateways require consistent RADIUS integration.
Impact: Migration errors can cause authentication failures, policy enforcement gaps, and potential security violations.
Solution Overview
Cisco ISE addresses migration challenges with:
- Policy Mapping Tools: Stepwise creation of policy sets, authentication, and authorization rules from legacy NAC.
- Endpoint Import: Bulk import of endpoints from CSV or APIs to preserve access.
- Profiler & Posture Integration: Advanced profiling and posture assessment replace legacy capabilities.
- Certificate and 802.1X Management: Easy certificate import/export and EAP configuration.
- GUI + CLI Validation: Verify migration success, authentication flows, and policy hits post-migration.
By leveraging these tools, engineers can migrate safely with minimal impact on users and network security posture.
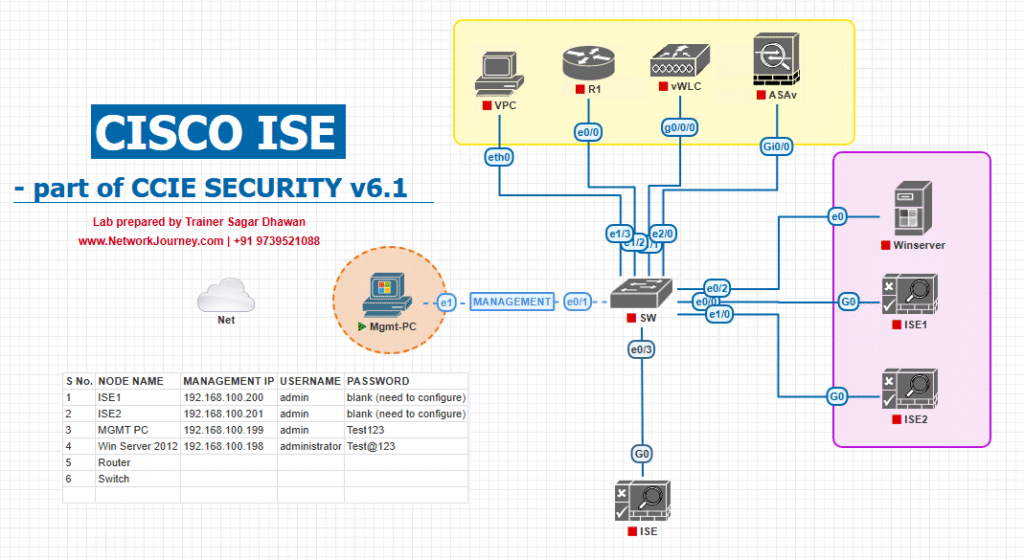
Sample Lab Topology
Lab Environment: VMware or EVE-NG
Components:
- ISE Nodes: PAN, 2x PSNs, MnT
- Legacy NAC: Cisco NAC Appliance or simulated CSV policy data
- Switches: Catalyst 9300/9200
- WLC: Cisco 9800
- Endpoints: Windows/Linux laptops, iOS/Android devices, IoT devices
- Migration Data Source: CSV export from legacy NAC or API integration
Diagram :
Notes:
- VMware: Legacy NAC & ISE nodes as VM appliances
- EVE-NG: Virtual PSNs + PAN + endpoints
- Simulate authentication traffic using scripts for validation
Step-by-Step GUI Configuration Guide
Objective: Safely migrate legacy NAC policies, endpoints, and authentication flows to ISE.
Step 1: Pre-Migration Backup
- Backup ISE configuration (if ISE already has policies)
- Administration → System → Backup & Restore
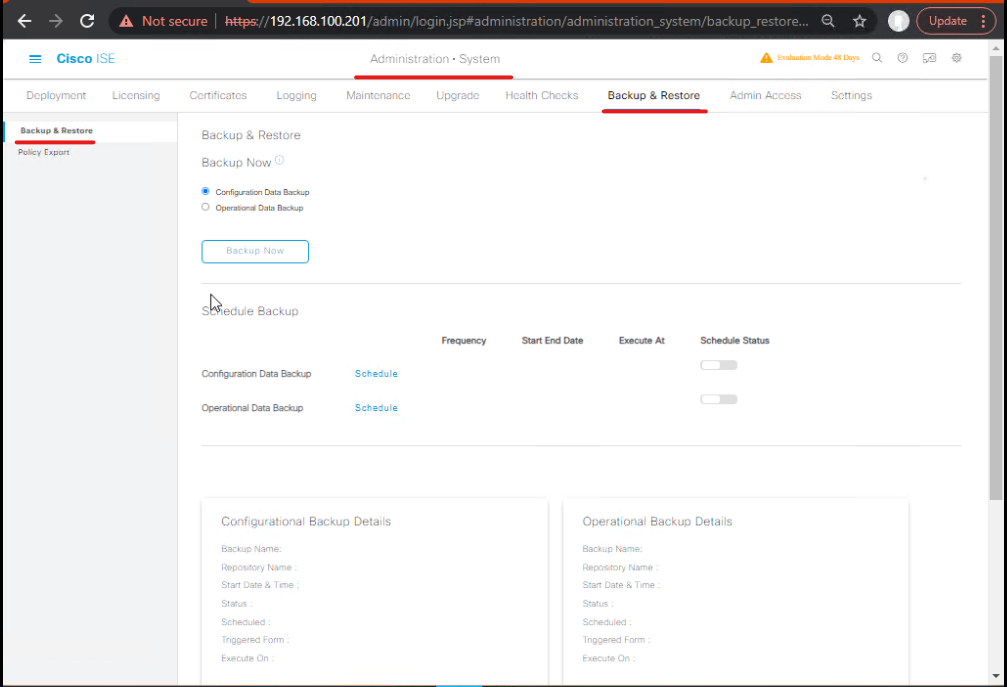
- Include:
- Configurations
- Endpoints
- Policies
CLI Validation:
show backup status
[Screenshot: Backup Configuration]
Step 2: Extract Legacy NAC Policies
- Export legacy NAC policies to CSV or API-based format
- Identify:
- VLAN mappings
- Authentication methods (802.1X, MAB, VPN)
- Authorization roles
- Map legacy rules to ISE policy sets
Step 3: Endpoint Migration
- Navigate: Work Centers → Endpoints → Import → CSV
- Map columns:
- MAC address
- IP address
- Endpoint identity group
- CLI Verification:
show endpoint all
Validation: All endpoints imported successfully
Step 4: Authentication Policy Setup
- Navigate: Policy → Policy Sets → Create New
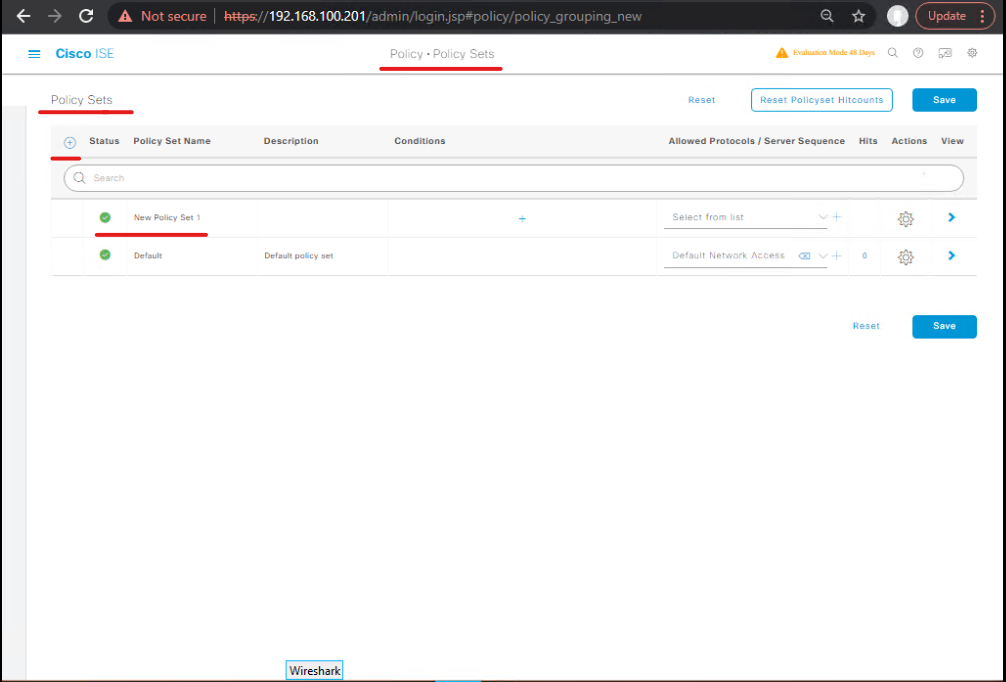
- Conditions:
- Network Device Groups (Legacy switch mappings)
- Identity Sources (Internal LDAP/AD, RADIUS)
- Authentication Methods:
- 802.1X (PEAP, EAP-TLS)
- MAB (MAC Authentication Bypass)
- CLI Verification:
show running-config ise
[Screenshot: Authentication Policy GUI]
Step 5: Authorization Policy Mapping
- Navigate: Policy → Authorization
- Map legacy roles to ISE authorization profiles
- Ensure:
- VLAN assignments match legacy policies
- ACLs applied consistently
- CLI Verification:
show authorization profiles show authentication sessions details
[Screenshot: Authorization Policy Mapping]
Step 6: Profiling & Posture Integration
- Navigate: Work Centers → Profiler
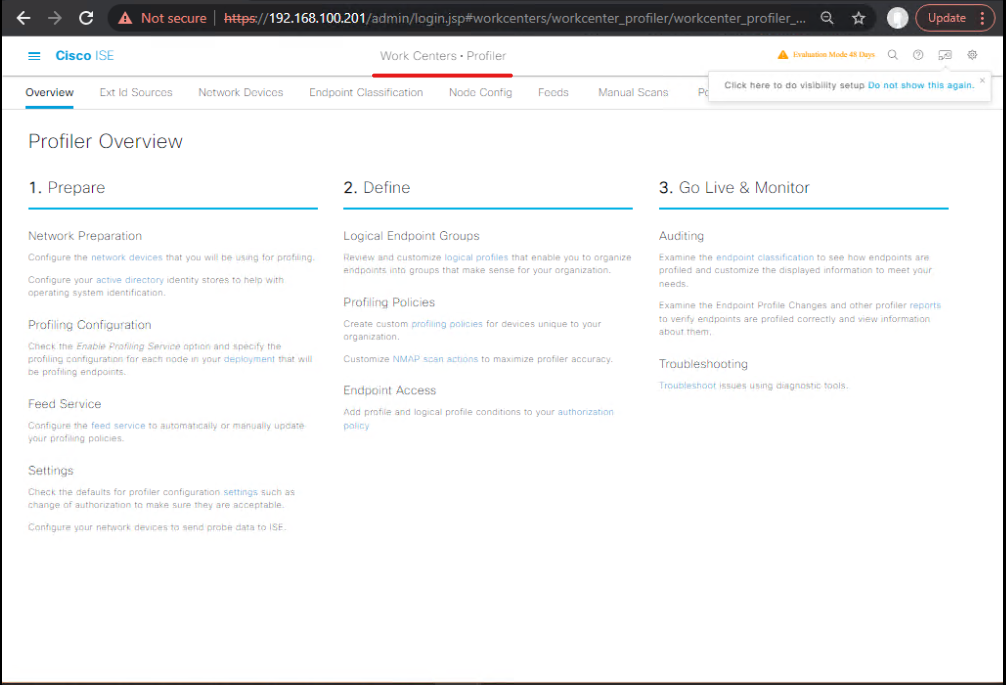
- Define profiles based on legacy NAC device categories
- Enable posture checks if legacy NAC enforced posture
- CLI Validation:
show profiler cache show profiler statistics
Step 7: Test Migration in Lab
- Select a subset of endpoints for pilot migration
- Authenticate through ISE
- Validate:
- Policy hits
- VLAN assignment
- Access permissions
- CLI:
show authentication sessions summary debug radius all
[Screenshot: Policy Troubleshooter Test]
Step 8: Full Migration Execution
- Gradually migrate all endpoints
- Monitor logs, sessions, and authorization hits
- Ensure all endpoints have continuity without disruption
Step 9: Post-Migration Validation
- Operations → Reports → Authentication & Authorization success
- Verify policy enforcement matches legacy NAC expectations
- CLI:
show authentication sessions show authorization sessions
[Screenshot: Post-Migration Reports]
Step 10: Clean-Up Legacy NAC
- Decommission legacy NAC once all endpoints validated
- Ensure DNS, VLANs, and ACLs no longer reference legacy NAC
Troubleshooting & Diagnostics
Common Issues:
- Endpoints fail to authenticate post-migration
- Policy mismatch between legacy NAC and ISE
- Profiling inconsistencies
Diagnostics Steps:
- GUI: Operations → RADIUS → Live Auth Sessions
- CLI:
show authentication sessions show endpoint all debug radius all
- Validate VLAN, ACL, and authorization profile assignments
- Adjust policy rules or re-import endpoints if needed
Lab Walkthroughs with Validation
Scenario 1: Pilot Migration
- Select 50 endpoints
- Map legacy VLANs & roles → ISE profiles
- Test authentication via GUI + CLI
- Validate policy hits
Scenario 2: Full-Scale Migration
- Bulk import endpoints (1000+)
- Verify authorization & VLAN assignments
- Generate authentication success/failure report
Expert-Level Use Cases
- Multi-Site Migration
- Map legacy NAC policies per site
- Validate authentication continuity site-wise
- CLI validation per PSN
- Legacy NAC to ISE with Mixed Authentication
- Migrate endpoints using both MAB and 802.1X
- Validate policy triggers using Policy Troubleshooter
- Automated Endpoint Sync
- Use API or scripts to sync endpoints from legacy NAC
- Validate import using
show endpoint all
- Policy Conflict Resolution
- Identify conflicting legacy roles
- Map to unique authorization profiles
- Validate live policy hits and session logs
FAQs
1. How do I map legacy NAC VLANs to ISE authorization profiles?
- Identify VLAN assignments in the legacy NAC policies.
- Create matching authorization profiles in ISE with the same VLAN, ACLs, and QoS policies.
- Use Policy Troubleshooter or
show authorization sessionsto validate policy hits after migration.
2. Can I migrate endpoints in bulk without causing downtime?
- Yes, by using CSV import or API integration into ISE.
- Validate a pilot group first, then gradually import all endpoints.
- Monitor authentication sessions during migration to ensure continuity.
3. How do I test migration before decommissioning legacy NAC?
- Perform a pilot migration with a subset of endpoints.
- Validate authentication, authorization, VLAN assignment, and policy hits using GUI and CLI.
- Use Policy Troubleshooter to check policy mapping against legacy behavior.
4. Which CLI commands verify imported endpoints?
show endpoint all show endpoint summary show authentication sessions summary
- These commands allow you to check endpoint presence, identity groups, and authentication status.
5. How to validate 802.1X and MAB policies post-migration?
- GUI: Operations → RADIUS → Live Auth Sessions → filter by endpoint
- CLI:
show authentication sessions details debug radius all
- Verify authentication type matches expected (802.1X or MAB) and correct authorization profile is applied.
6. What if legacy NAC policies conflict with ISE roles?
- Identify conflicting rules during pilot migration.
- Consolidate or create new ISE authorization profiles.
- Validate policy triggers using Policy Troubleshooter before full-scale migration.
7. Can I automate migration using CSV or API?
- Yes, bulk endpoint import via CSV or REST API is supported.
- Map identity groups, VLANs, and roles in CSV headers.
- CLI verification ensures endpoints are correctly imported:
show endpoint all
8. How to ensure profiling and posture policies replicate legacy behavior?
- Use Profiler Work Center → create device categories based on legacy NAC profiling.
- Enable posture policies similar to legacy posture checks.
- CLI:
show profiler cache show profiler statistics
- Validate endpoint identification and posture evaluation post-migration.
9. How to rollback migration if endpoints fail authentication?
- Restore a backup taken prior to migration: Administration → System → Backup & Restore → Restore
- Verify endpoints authenticate correctly post-rollback.
- Use CLI to monitor:
show authentication sessions
10. How to validate reports post-migration to ensure policy accuracy?
- Operations → Reports → Authentication & Authorization Success/Failure
- Filter by migrated endpoints or policies
- Compare with legacy NAC reports to ensure behavior is consistent.
- CLI:
show authentication sessions summary show authorization sessions
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- Legacy NAC migration requires careful planning, policy mapping, and endpoint validation
- GUI + CLI verification ensures authentication continuity
- Pilot migration reduces risk and allows validation before full-scale rollout
- Profiling and posture integration ensures modern security posture
- Decommission legacy NAC only after thorough validation
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to Network Journey on YouTube and join my instructor-led classes. Learn step-by-step migration strategies, zero-downtime deployment, and advanced troubleshooting to become an ISE expert.
Fast-Track to Cisco ISE Mastery Pro
4-Month Instructor-Led CCIE Security Program:
- Hands-On Labs: Legacy NAC → ISE migration, policy mapping, endpoint import
- Expert Mentorship: Troubleshooting, validation, HA deployments
- Exam-Oriented Guidance: Real-world migration simulations
- Certificate of Completion: Industry-recognized validation
- Register at networkjourney.com/ccie-security
Migrate confidently—modernize NAC with ISE without service disruption.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088


![[Day 22] Cisco ISE Mastery Training: MAB (MAC Authentication Bypass) Configuration](https://networkjourney.com/wp-content/uploads/2025/08/Day-22-Cisco-ISE-Mastery-Training-MAB-MAC-Authentication-Bypass-Configuration.png)
