[Day 149] Cisco ISE Mastery Training: Troubleshooting Deep Dive (TAC Level)
Table of Contents
Introduction
Troubleshooting Cisco ISE is often considered the highest skill level for network engineers—equivalent to TAC (Technical Assistance Center) operations. Unlike simple GUI checks, TAC-level troubleshooting involves real-time session analysis, debug commands, packet capture, log correlation, and policy validation.
Why it matters:
- Enterprise networks depend on continuous authentication and authorization. Any policy, endpoint, or device misconfiguration can create widespread service disruption.
- Engineers must be able to pinpoint issues quickly, whether they are related to RADIUS, 802.1X, MAB, posture, profiling, or authorization conflicts.
- Mastering this topic develops problem-solving skills at the highest operational level, preparing engineers for real-world CCIE-level troubleshooting and TAC escalation scenarios.
In this Article, you will learn:
- How to systematically diagnose and resolve authentication issues in ISE.
- Advanced CLI and GUI commands for real-time troubleshooting.
- Lab-based simulation of common and complex errors.
- Expert techniques used by TAC engineers to resolve large-scale incidents.
- How to validate fixes, monitor endpoints, and ensure zero-impact resolution.
Problem Statement
Real-world networks often encounter these challenges:
2.1 Authentication Failures
- Endpoints cannot authenticate via 802.1X, MAB, or VPN.
- Causes can include misconfigured policies, certificate errors, or network misconfigurations.
2.2 Authorization Mismatches
- Users are successfully authenticated but receive wrong VLANs, ACLs, or privilege levels.
- Can occur due to policy conflicts or improperly mapped roles.
2.3 Posture & Profiling Issues
- ISE misclassifies devices or fails posture checks.
- Legacy devices or BYOD endpoints can trigger unexpected access denials.
2.4 Multi-Node HA Failures
- In distributed ISE deployments, PSN or PAN nodes may be out-of-sync.
- Authentication traffic can fail if node-to-node replication issues exist.
2.5 Network Device Misconfiguration
- Switches, WLCs, and firewalls may have incorrect RADIUS shared secrets, AAA configurations, or failover policies.
Impact: Without TAC-level troubleshooting skills, resolving these issues can take hours or even days, impacting security, compliance, and user productivity.
Solution Overview
Cisco ISE provides a combination of GUI, CLI, logs, and diagnostic tools to troubleshoot at TAC level:
- Policy Troubleshooter: Real-time evaluation of authentication/authorization flows.
- Live Authentication Reports: Immediate visibility into endpoint sessions.
- CLI Debug Commands:
debug radius all,show authentication sessions,show authorization sessions. - Packet Captures & Logs: Correlate AAA transactions with switch or WLC logs.
- Profiler & Posture Logs: Identify classification or posture issues.
By mastering these tools, engineers can rapidly identify root causes, isolate affected endpoints, and implement fixes without disrupting the broader network.
Sample Lab Topology
Lab Environment: VMware or EVE-NG
Components:
- ISE Nodes: PAN, 2x PSNs, MnT
- Switches: Catalyst 9300/9200
- WLC: Cisco 9800
- Endpoints: Windows/Linux laptops, iOS/Android, IoT devices
- Simulation Tools: radtest, eapol_test, traffic generators
Diagram :
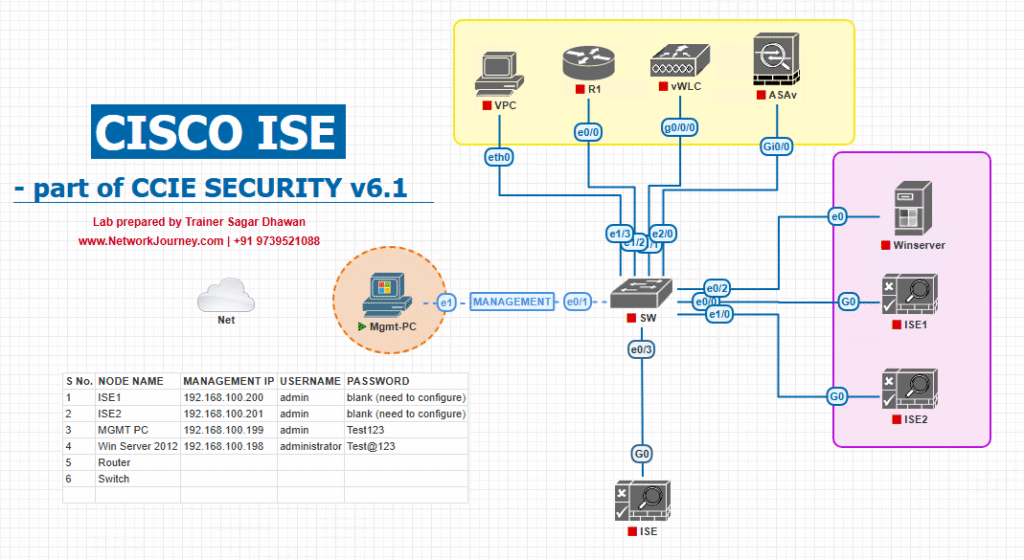
Lab Notes:
- VMware: Deploy PAN, PSN, MnT nodes
- EVE-NG: Use virtualized switches and endpoints to simulate authentication flows
- Generate authentication events using radtest or 802.1X supplicants
Step-by-Step GUI Configuration Guide
Step 1: Validate Node Health
- GUI: Administration → System → Deployment
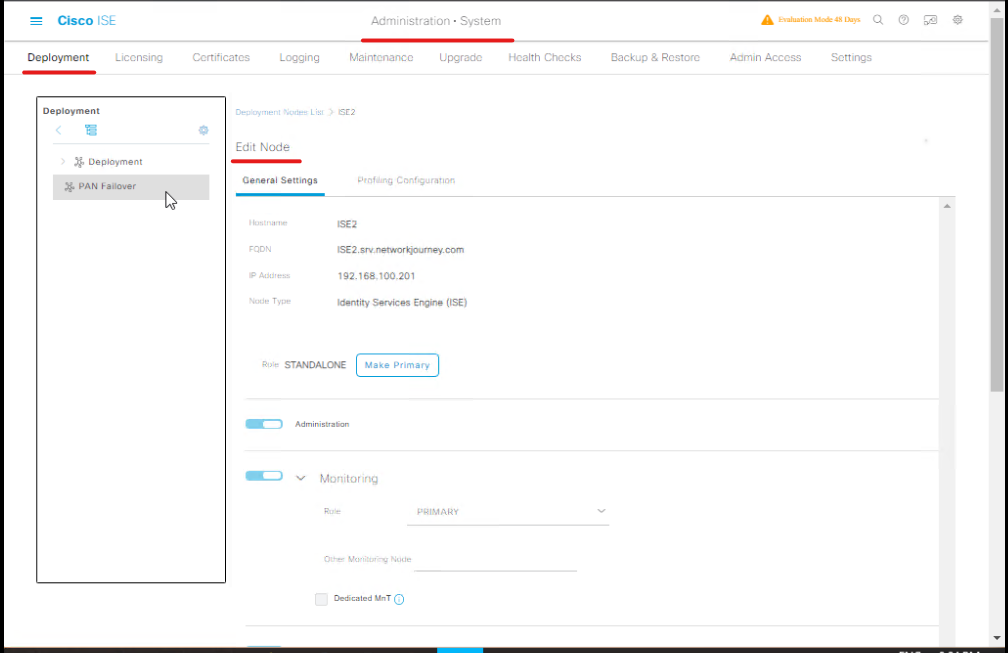
- Verify node status: PAN, PSNs, MnT are all active.
- CLI:
show application status ise show system resources show cluster summary
[Screenshot: Node Health GUI]
Step 2: Verify AAA Settings on Network Devices
- Switch:
show running-config | include radius show aaa servers
- WLC: Verify RADIUS server IPs, shared secrets, and failover priority
[Screenshot: AAA Configuration GUI]
Step 3: Authentication Troubleshooting
- GUI: Operations → RADIUS → Live Auth Sessions
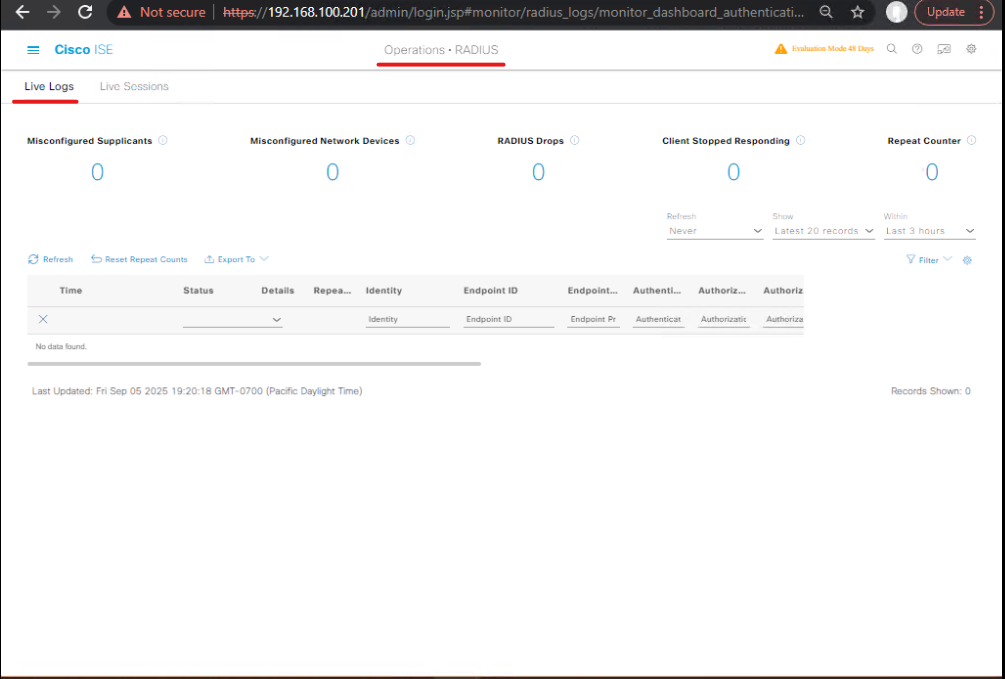
- Select failed endpoint and analyze policy hits
- CLI:
show authentication sessions details debug radius all
- Use
debug radius allonly during low-traffic periods to prevent performance impact.
[Screenshot: Live Auth Session GUI]
Step 4: Authorization Troubleshooting
- GUI: Operations → Policy Troubleshooter
- Input username or endpoint MAC
- Check authentication, identity source, and authorization profile applied
- CLI:
show authorization sessions show running-config ise
[Screenshot: Policy Troubleshooter GUI]
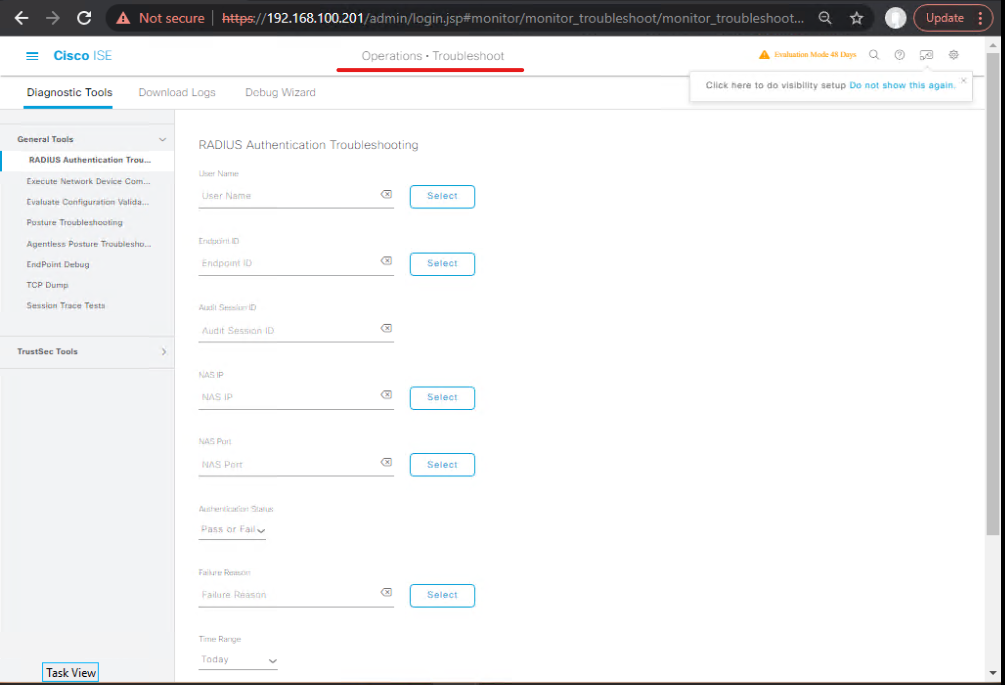
Step 5: Profiling and Posture Analysis
- GUI: Work Centers → Profiler → Profiler Cache
- Check device classification and active posture checks
- CLI:
show profiler cache show profiler statistics
- Identify misclassified devices or failed posture checks
[Screenshot: Profiler Validation]
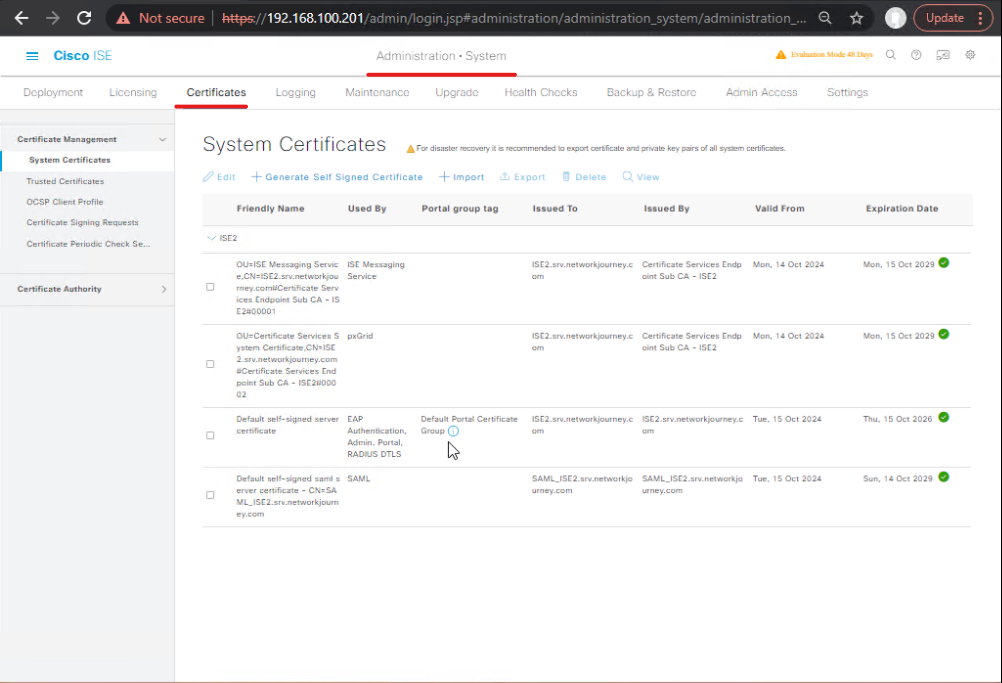
Step 6: Certificate Validation
- GUI: Administration → System → Certificates → Node Certificates
- Validate expiration, SAN entries, and CA chain
- CLI:
show crypto certificate
- Check for expired or untrusted certificates causing 802.1X failures
[Screenshot: Certificate GUI]
Step 7: Log and Debug Correlation
- GUI: Operations → Reports → RADIUS Accounting & Authentication Logs
- CLI:
show logging application ise debug radius all
- Correlate log events with switch or WLC logs for root cause analysis
[Screenshot: Log Correlation GUI]
Step 8: Packet Capture Validation
- Capture traffic between endpoint → switch → ISE PSN
- Analyze RADIUS packets for Access-Request, Access-Accept/Reject
- Validate attributes (VLAN, role, ACL) match policy expectations
Tools: Wireshark, packet-tracer
Step 9: Multi-Node and HA Validation
- CLI:
show cluster summary show replication status
- Ensure policy replication across PAN and PSNs
- Validate that failover triggers work as expected
Step 10: Troubleshooting Post-Fix Validation
- Test multiple endpoints with 802.1X, MAB, and VPN
- Validate authentication success using GUI + CLI
- Confirm correct VLAN, ACL, and posture evaluation
CLI Commands:
show authentication sessions summary show authorization sessions show profiler cache
[Screenshot: Post-Fix Validation]
Troubleshooting & Diagnostics
Scenario-Based TAC Troubleshooting Examples:
- 802.1X Failure due to EAP Mismatch
- Symptom: Endpoint rejects 802.1X authentication
- CLI:
debug radius all→ check EAP type - Fix: Match supplicant EAP type with ISE authentication policy
- MAB Endpoint Getting Wrong VLAN
- Symptom: MAC authenticated device assigned wrong VLAN
- CLI:
show authorization sessions→ check applied profile - Fix: Update authorization rules or profile mapping
- Profiler Misclassification
- Symptom: Device classified as Unknown
- CLI:
show profiler cache→ verify attributes - Fix: Adjust profiler rules or update fingerprint database
- Multi-PSN Replication Delay
- Symptom: New policies not hitting all PSNs
- CLI:
show replication status - Fix: Force replication or check HA communication
Lab Walkthroughs with Validation
Lab Exercise 1: Authentication Failure Simulation
- Simulate EAP mismatch on Windows laptop
- Validate policy troubleshooting and CLI debug workflow
Lab Exercise 2: Authorization Profile Mismatch
- Assign wrong ACL/VLAN to endpoint
- Use GUI + CLI to identify misapplied profile and correct it
Lab Exercise 3: Profiling Posture Issue
- Simulate BYOD endpoint failing posture check
- Adjust profiler rules and rerun authentication
Lab Exercise 4: Multi-Node Failover Test
- Take PSN offline
- Validate HA failover, replication, and policy enforcement continuity
Expert Level Use Cases
- Cross-Site Authentication Issue
- Map PSNs to site-specific switches
- Validate AAA policies and logs per site
- Mixed Authentication Deployment
- Test 802.1X, MAB, and VPN endpoints simultaneously
- Validate correct authorization, VLAN assignment, and logging
- High-Volume Endpoint Validation
- Simulate 1000+ concurrent sessions
- CLI:
show authentication sessions summary→ monitor PSN load
- TAC Escalation Simulation
- Collect logs, debug outputs, and packet captures
- Reproduce scenario in lab before live resolution
FAQs
1. Which CLI commands are essential for TAC-level troubleshooting in Cisco ISE?
Answer:
show authentication sessions→ Lists all active authentication sessions.show authorization sessions→ Shows applied authorization profiles.debug radius all→ Provides detailed RADIUS transaction logs.show profiler cache→ Displays endpoint classification information.show profiler statistics→ Summarizes profiling activity.show replication status→ Checks HA replication between PAN/PSNs.show logging application ise→ Retrieves ISE-specific log entries.
These commands allow engineers to isolate authentication, authorization, and replication issues efficiently.
2. How do I quickly identify failed 802.1X authentications?
Answer:
- GUI: Operations → RADIUS → Live Auth Sessions, filter for failed sessions.
- CLI:
show authentication sessions details debug radius all
- Check for common causes like EAP type mismatch, certificate errors, or identity store issues.
- Use Policy Troubleshooter to verify the authentication policy hit.
3. How to validate MAB endpoints that are assigned incorrect VLANs?
Answer:
- CLI:
show authorization sessions
- GUI: Operations → Policy Troubleshooter, enter endpoint MAC → verify assigned authorization profile.
- Cross-check the VLAN mapping in the Authorization Policy and update if needed.
4. How can I correlate ISE logs with switch/WLC logs for root cause analysis?
Answer:
- Match timestamps of failed authentication events in ISE logs with RADIUS logs on switches/WLCs.
- CLI on switch:
show logging | include RADIUS
- GUI: Packet captures can also validate the RADIUS Access-Request/Access-Accept flow.
5. How do I troubleshoot multi-node HA and replication issues?
Answer:
- CLI:
show cluster summary show replication status
- Verify all PSNs are reachable and policies are replicated.
- Use Operations → System Health in GUI to check node connectivity.
- Resolve any network or firewall issues preventing replication.
6. How do I fix profiler misclassification or unknown devices?
Answer:
- CLI:
show profiler cache show profiler statistics
- Identify endpoint attributes causing misclassification.
- Adjust profiler rules or update fingerprints in Work Centers → Profiler.
- Ensure MAC address, DHCP, HTTP headers, and SNMP attributes are correctly detected.
7. How can I resolve posture check failures on endpoints?
Answer:
- GUI: Work Centers → Posture → Posture Reports, check failed endpoints.
- CLI:
show posture sessions
- Verify compliance modules, update posture policies, and confirm endpoint connectivity.
- Ensure ISE can reach required resources (patch servers, antivirus checks, etc.).
8. How do I validate certificate-related issues affecting 802.1X?
Answer:
- GUI: Administration → System → Certificates → Node Certificates.
- CLI:
show crypto certificate
- Check for expired certificates, SAN entries, or untrusted CAs.
- Ensure supplicant certificates match ISE authentication policies.
9. How do I perform TAC-level packet capture for RADIUS debugging?
Answer:
- Capture traffic on the ISE PSN or switch port:
debug radius all
- Use Wireshark to analyze Access-Request and Access-Accept/Reject packets.
- Validate attributes like VLAN, Authorization Profile, EAP type match expected policy.
10. How to test and validate fixes without impacting production?
Answer:
- Use a lab or pilot endpoints to simulate issues.
- Validate using GUI: Policy Troubleshooter and Live Auth Sessions.
- CLI:
show authentication sessions summary show authorization sessions
- Confirm correct authentication, authorization, VLAN assignment, and posture evaluation before applying fixes network-wide.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- TAC-level troubleshooting combines GUI visibility, CLI commands, debug outputs, and log correlation.
- Systematic workflow: Node health → AAA validation → Authentication → Authorization → Profiler → Posture → Certificates → HA → Validation
- Lab-based exercises reinforce skills and simulate real-world incidents
- Mastery ensures fast resolution, minimal downtime, and zero-impact remediation
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to Network Journey on YouTube and join my instructor-led classes. Learn TAC-level troubleshooting workflows, policy validation, and multi-node high-scale authentication analysis.
Fast-Track to Cisco ISE Mastery Pro
4-Month Instructor-Led CCIE Security Program:
- Hands-On Labs: Authentication, Authorization, Profiling, Posture
- Expert Mentorship: TAC-level troubleshooting
- Exam-Oriented Guidance: Real-world scenarios
- Certification: Industry-recognized
- Register at: networkjourney.com/ccie-security
Solve ISE issues like a TAC engineer—master troubleshooting at scale.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



