[Day 150] Cisco ISE Mastery Training: End‑to‑End Enterprise NAC Deployment Case Study
Table of Contents
Introduction
Enterprise networks are rapidly evolving with increasing device diversity, cloud integration, BYOD policies, and regulatory compliance requirements. Network Access Control (NAC) has become critical to ensure that only compliant and authenticated devices gain access to network resources. Cisco ISE (Identity Services Engine) is the industry-leading platform for centralized NAC, offering authentication, authorization, profiling, posture enforcement, and policy-based access control across wired, wireless, and VPN networks.
Why this case study matters:
- Provides a real-world deployment example, integrating multiple components such as switches, WLCs, endpoints, and ISE nodes.
- Demonstrates end-to-end NAC workflows from authentication to policy enforcement.
- Prepares engineers to design, deploy, validate, and troubleshoot large-scale NAC deployments.
- Bridges the gap between theoretical ISE knowledge and practical enterprise deployment scenarios, which is essential for CCIE Security mastery.
In this Article, you will learn how to:
- Plan and design an enterprise NAC architecture using Cisco ISE.
- Deploy ISE nodes, integrate network devices, and define policies.
- Configure authentication and authorization for wired, wireless, and BYOD endpoints.
- Implement profiling and posture enforcement.
- Validate policies, troubleshoot issues, and optimize performance.
Problem Statement
Enterprises face multiple challenges when implementing NAC:
2.1 Multi-Vendor Network Environment
- Network devices may come from different vendors with varying AAA capabilities.
- RADIUS integration must be validated per device type.
2.2 Device Diversity
- Employees use laptops, desktops, mobile devices, IoT endpoints, and BYOD devices.
- Each device type may require different policies, VLANs, and ACLs.
2.3 Security & Compliance
- Regulatory standards require granular access control and audit-ready reporting.
- Without centralized NAC, endpoint compliance cannot be enforced.
2.4 High Availability & Scalability
- ISE deployment must handle thousands of concurrent sessions with HA for PAN, PSN, and MnT nodes.
2.5 Troubleshooting Complexity
- Multi-site deployments and mixed authentication types can generate complex issues.
- TAC-level troubleshooting skills are essential for fast resolution.
Impact: Without a structured end-to-end deployment plan, organizations risk security gaps, compliance violations, and service disruptions.
Solution Overview
Cisco ISE addresses these challenges with a comprehensive NAC platform:
- Authentication & Authorization: Supports 802.1X, MAB, and VPN endpoints.
- Profiling: Automatically classifies devices by type, OS, and attributes.
- Posture Enforcement: Ensures endpoints meet security compliance before granting access.
- Policy Sets & Authorization Profiles: Flexible policy creation and mapping to network devices.
- HA & Scalability: PAN, PSNs, and MnT nodes provide redundancy and load balancing.
- Reports & Logs: Centralized reporting and auditing for compliance.
The case study walks through a complete deployment scenario, showing how ISE integrates with network infrastructure and enforces security policies across a large enterprise.
Sample Lab Topology
Lab Environment: VMware or EVE-NG
Components:
- ISE Nodes: PAN, 2x PSNs, MnT
- Network Devices: Catalyst 9300/9200 switches, Cisco 9800 WLC
- Endpoints: Windows, Linux, iOS, Android, IoT devices
- Simulation Tools: RADIUS test clients, eapol_test, traffic generators
Topology Diagram :
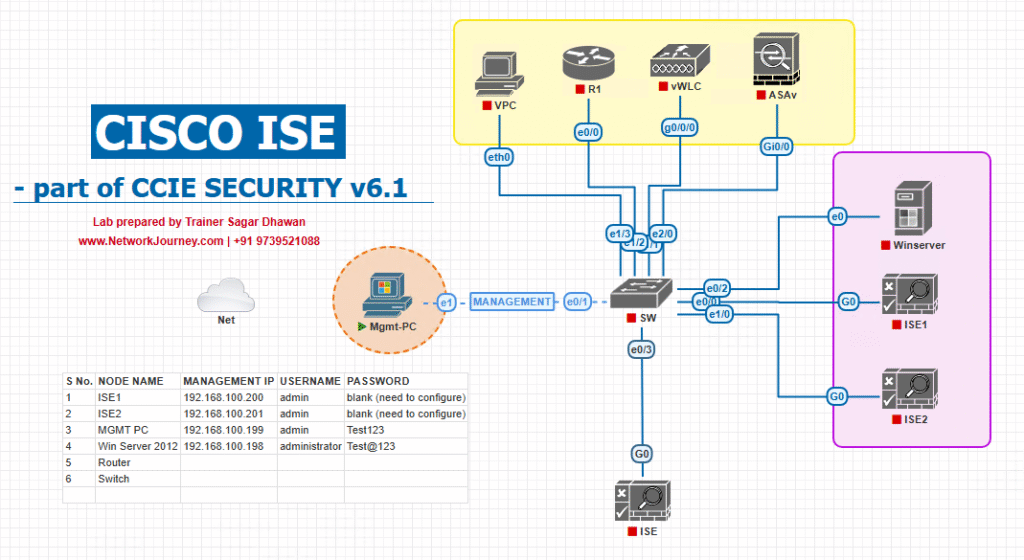
Lab Notes:
- VMware: Deploy ISE nodes (PAN, PSNs, MnT) for realistic HA and scalability testing.
- EVE-NG: Virtualized switches and endpoints to simulate authentication flows.
- Simulated traffic: Generate 50–500 endpoints for pilot testing and full-scale deployment validation.
Step-by-Step GUI Configuration Guide
Step 1: Pre-Deployment Planning
- Identify network segments, VLANs, and endpoint types.
- Map authentication methods (802.1X, MAB, VPN) to endpoint groups.
- Define authorization profiles with VLAN, ACL, and role assignments.
- CLI Verification:
show running-config show vlan brief
[Screenshot Placeholder: Planning Document]
Step 2: ISE Node Deployment
- Deploy PAN, PSNs, and MnT in VMware or EVE-NG.
- Assign IPs, DNS, NTP, and gateway.
- Configure HA (if applicable).
- CLI Verification:
show application status ise show cluster summary
[Screenshot Placeholder: Node Deployment GUI]
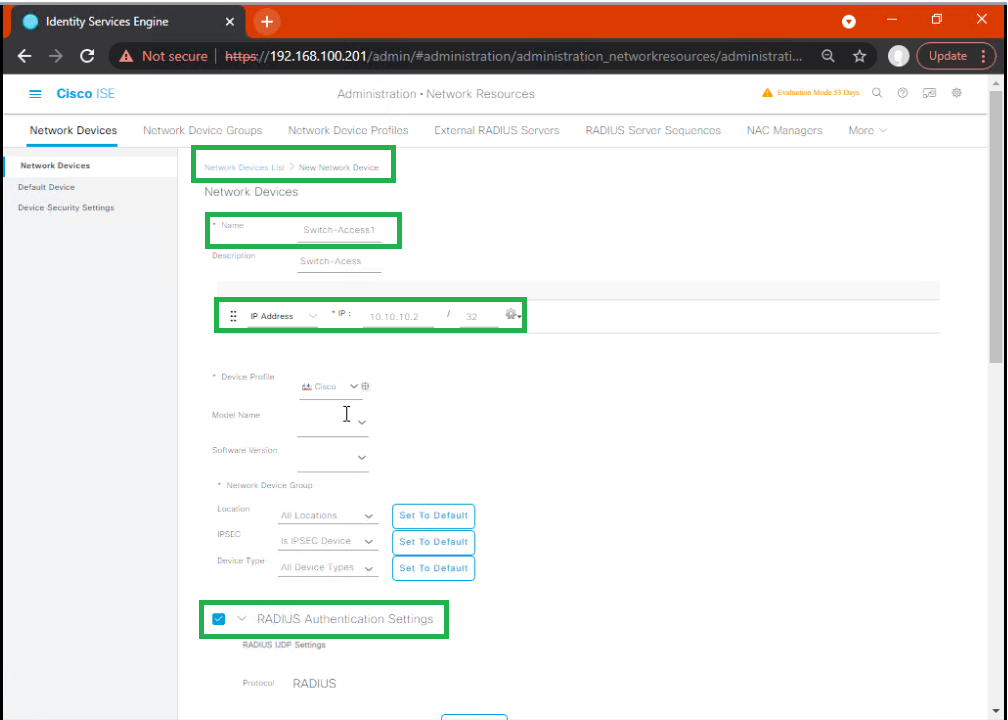
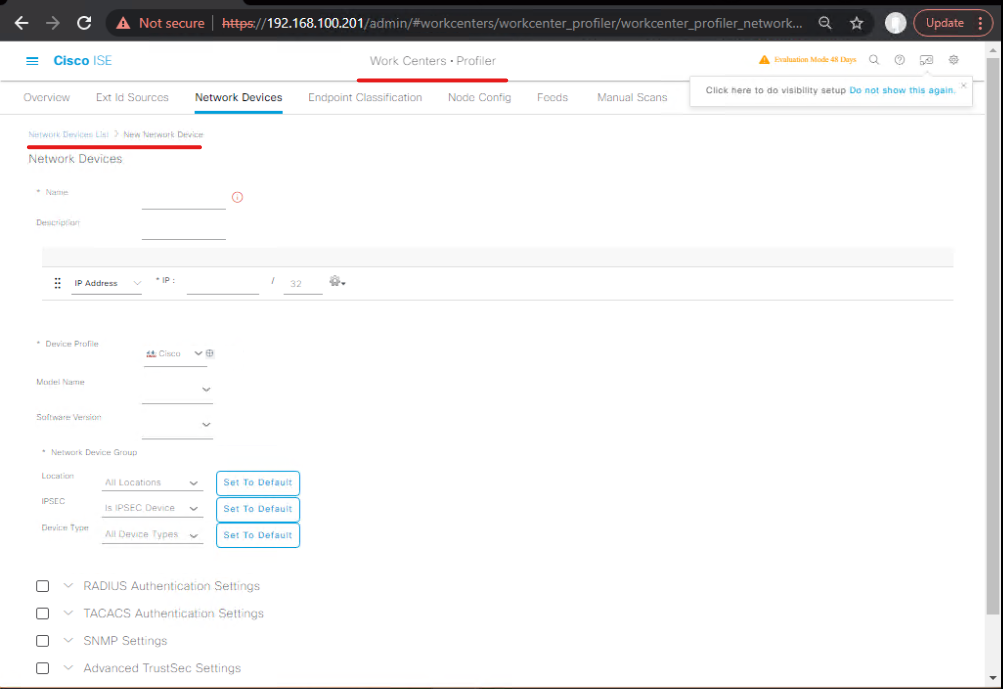
Step 3: Network Device Integration
- GUI: Administration → Network Resources → Network Devices → Add
- Add switches and WLCs with IP, shared secret, and device type.
- Assign to network device groups (by site, building, or floor).
- CLI: Verify RADIUS configuration on switches:
show running-config | include radius show aaa servers
[Screenshot Placeholder: Network Device Integration GUI]
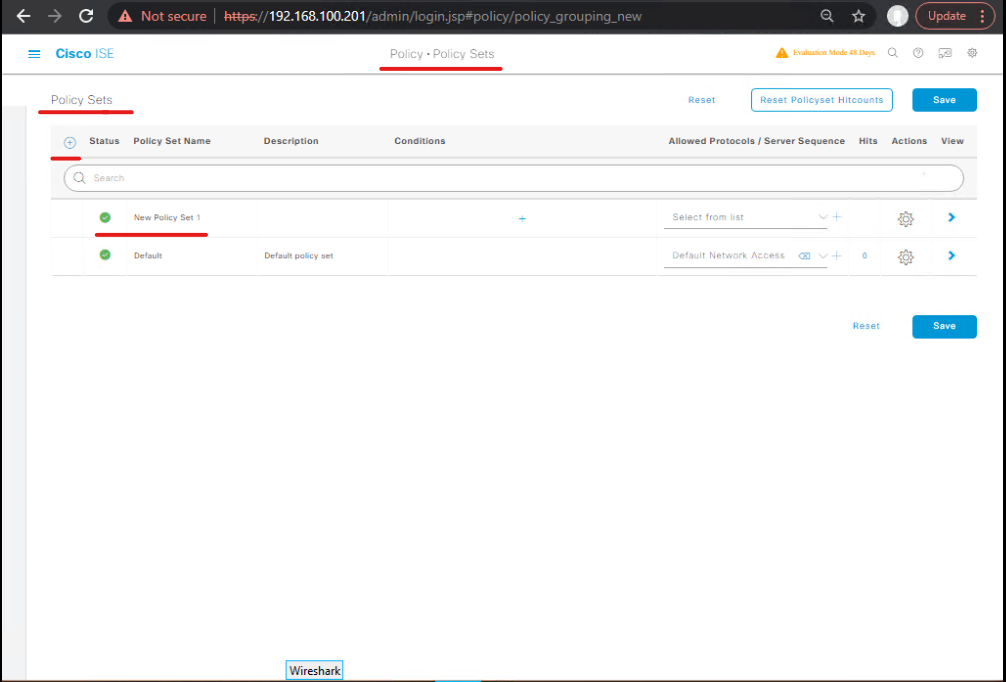
Step 4: Authentication Policy Configuration
- GUI: Policy → Policy Sets → New Policy Set
- Define policy conditions: network device groups, endpoint identity, location, time.
- Configure authentication methods: 802.1X (EAP-TLS/PEAP), MAB, VPN.
- CLI Verification:
show running-config ise show authentication sessions summary
[Screenshot Placeholder: Authentication Policy GUI]
Step 5: Authorization Policy Configuration
- GUI: Policy → Authorization
- Map authorization profiles to identity groups and conditions.
- Assign VLAN, ACL, downloadable ACLs, and roles.
- CLI Verification:
show authorization profiles show authentication sessions details
[Screenshot Placeholder: Authorization Policy GUI]
Step 6: Profiling and Posture Enforcement
- GUI: Work Centers → Profiler → Create device categories.
- Configure posture policies: compliance checks for antivirus, OS patches, disk encryption.
- CLI Verification:
show profiler cache show profiler statistics show posture sessions
[Screenshot Placeholder: Profiler/Posture GUI]
Step 7: Pilot Testing
- Select a subset of endpoints (50–100) for pilot deployment.
- Authenticate endpoints and validate policy hits using Policy Troubleshooter.
- CLI Validation:
show authentication sessions details debug radius all
[Screenshot Placeholder: Pilot Testing GUI]
Step 8: Full Deployment
- Gradually roll out policies to all endpoints.
- Monitor authentication, authorization, and posture enforcement.
- CLI Validation:
show authentication sessions summary show authorization sessions show profiler cache
Step 9: Post-Deployment Reporting
- GUI: Operations → Reports → Authentication & Authorization Success/Failure
- Verify all endpoints are authenticated and classified correctly.
- CLI:
show logging application ise
[Screenshot Placeholder: Post-Deployment Reports GUI]
Step 10: Optimization & Fine-Tuning
- Adjust policies for edge cases (BYOD, IoT, contractors).
- Monitor PSN performance and load balance if required.
- CLI:
show system resources show application status ise
[Screenshot Placeholder: Optimization GUI]
Troubleshooting & Diagnostics
In enterprise NAC deployments, troubleshooting and diagnostics are critical for maintaining security, availability, and compliance. The following section covers real-world troubleshooting workflows, aligned with ISE’s GUI and CLI tools.
6.1 Authentication Failures
Common Causes:
- Supplicant misconfiguration (wrong EAP type, invalid certificates).
- Incorrect AAA configuration on switches/WLCs.
- RADIUS shared secret mismatch.
Troubleshooting Steps:
- GUI:
- Operations → RADIUS → Live Auth Sessions → Filter failed sessions.
- Check “Authentication Result” column for FAIL or Reject Reason.
- Policy Troubleshooter:
- GUI: Policy → Policy Troubleshooter → Enter endpoint MAC or username.
- Validate Policy Hit, authentication method, and applied authorization profile.
- CLI Commands:
show authentication sessions details debug radius all show running-config | include radius
- Validation:
- Verify Access-Request/Access-Accept packets.
- Ensure authentication method matches the policy (e.g., PEAP, EAP-TLS).
6.2 Authorization Issues (Incorrect VLAN/ACL Assignment)
Symptoms:
- Endpoint connected but has wrong VLAN or restricted access.
Troubleshooting Steps:
- CLI Verification:
show authorization sessions show authentication sessions details
- GUI Verification:
- Operations → Policy Troubleshooter → Check authorization profile mapping.
- Resolution:
- Update Authorization Profile with correct VLAN/ACL/DACL.
- Ensure policy set conditions correctly match endpoint identity and network device group.
6.3 Profiling & Unknown Device Issues
Symptoms:
- Endpoint is listed as unknown or misclassified.
Troubleshooting Steps:
- CLI:
show profiler cache show profiler statistics
- GUI:
- Work Centers → Profiler → Profiler Cache → Validate endpoint attributes.
- Resolution:
- Adjust profiler rules or update device fingerprints.
- Ensure DHCP, HTTP headers, MAC OUI, and SNMP attributes are correctly configured.
6.4 Posture Enforcement Failures
Symptoms:
- Endpoints failing posture checks even when compliant.
Troubleshooting Steps:
- CLI:
show posture sessions show compliance details
- GUI:
- Work Centers → Posture → Posture Reports → Filter failed endpoints.
- Resolution:
- Verify that posture modules are accessible (e.g., antivirus, patch servers).
- Update policy conditions for OS versions or agent configuration.
6.5 HA and Replication Diagnostics
Symptoms:
- Policies not replicated, or PSN failover does not occur.
Troubleshooting Steps:
- CLI:
show cluster summary show replication status
- GUI:
- Administration → System → Deployment → Node Status
- Validate node reachability, HA group membership, and replication state.
- Resolution:
- Correct network connectivity issues between nodes.
- Verify system time synchronization (NTP) and firewall rules.
6.6 TAC-Level Log Correlation
Purpose:
- Analyze RADIUS transactions, endpoint identity, and policy hit flow.
Steps:
- Collect ISE logs:
show logging application ise
- Collect switch/WLC RADIUS logs:
show logging | include RADIUS
- Use timestamps to correlate events.
- GUI: Operations → Reports → Event Logs for visual verification.
Lab Walkthroughs with Validation
This section provides hands-on lab exercises to validate deployment and troubleshoot issues in a controlled environment (VMware or EVE-NG).
Lab 1: Wired 802.1X Authentication Validation
Objective: Verify correct authentication and authorization mapping for wired endpoints.
Steps:
- Connect a test endpoint to a switch port configured for 802.1X.
- GUI: Operations → Policy Troubleshooter → Enter endpoint MAC.
- CLI:
show authentication sessions details show authorization sessions
- Validate:
- Correct authentication method triggered (EAP-PEAP/TLS).
- Authorization profile applied correctly (VLAN, ACL).
- Test network access: Ping internal resources allowed by policy.
Lab 2: Wireless Endpoint Testing
Objective: Validate WLC integration and wireless endpoint policy enforcement.
Steps:
- Connect wireless client to SSID mapped to ISE.
- GUI: Policy Troubleshooter → Verify authentication and authorization profile.
- CLI on ISE:
show authentication sessions summary show authorization sessions
- Validation:
- VLAN assignment correct
- ACL restrictions enforced
- Device profiled and classified accurately
Lab 3: BYOD Endpoint Posture Enforcement
Objective: Ensure BYOD devices meet posture compliance before network access.
Steps:
- Install ISE posture agent on a test endpoint.
- Connect endpoint to corporate network.
- GUI: Work Centers → Posture → Posture Reports → Validate session.
- CLI:
show posture sessions
- Test validation:
- Non-compliant device should be blocked or limited.
- Compliant device granted full access.
Lab 4: IoT Device Profiling & Access Segmentation
Objective: Validate IoT device profiling and restricted access.
Steps:
- Connect IoT device (printer or camera) to test switch port.
- GUI: Profiler Cache → Check device classification.
- CLI:
show profiler cache show authorization sessions
- Validation:
- Device classified correctly as IoT
- Authorization profile assigns VLAN/ACL correctly
- Test that access to restricted resources is blocked
Lab 5: High Availability and Failover Simulation
Objective: Validate ISE HA deployment.
Steps:
- Take one PSN offline.
- CLI:
show cluster summary show authentication sessions summary
- GUI: Policy Troubleshooter → Validate endpoint authentication.
- Validation:
- Authentication sessions continue without disruption
- Policies replicated correctly to active PSN
- Failover occurs automatically
Lab 6: End-to-End NAC Scenario
Objective: Test full enterprise deployment including wired, wireless, BYOD, and IoT endpoints.
Steps:
- Authenticate multiple endpoints (mixed types).
- Validate each endpoint in GUI Live Auth Sessions.
- CLI:
show authentication sessions summary show authorization sessions show profiler cache show posture sessions
- Validation:
- Policies applied correctly for each endpoint type
- VLANs, ACLs, and DACLs are enforced
- Profiling and posture checks working as expected
- Logs show no failed sessions
Expert Level Use Cases: End-to-End NAC Deployment
Use Case 1: IoT Device Deployment with Dynamic VLAN Assignment
Scenario:
Deploy a fleet of IoT devices (e.g., printers, cameras, sensors) across multiple floors, ensuring network segmentation and restricted access.
Step-by-Step Mapping:
- Profiler Setup:
- GUI: Work Centers → Profiler → Profiling Policies → New Policy
- Define IoT device categories using MAC OUI, DHCP fingerprinting, and HTTP headers.
- Authorization Profile Creation:
- GUI: Policy → Authorization → Authorization Profiles → New Profile
- Assign VLAN:
IoT_VLAN - Configure ACL:
IoT_ACLto restrict access to only necessary services.
- Policy Set Mapping:
- GUI: Policy → Policy Sets → New Policy Set
- Condition:
Endpoint Type = IoT - Authentication:
MAB(MAC Authentication Bypass) - Authorization: Map to the IoT Authorization Profile.
Validation Steps:
- CLI:
show profiler cache show authentication sessions details show authorization sessions
- GUI: Operations → Live Auth Sessions, verify IoT devices are classified, authenticated, and assigned the correct VLAN and ACL.
- Test connectivity to ensure devices cannot reach restricted corporate resources.
Use Case 2: BYOD Endpoint with Posture Enforcement
Scenario:
Employees bring personal laptops and smartphones, requiring compliance validation before granting corporate network access.
Step-by-Step Mapping:
- Posture Policy Definition:
- GUI: Work Centers → Posture → Policy Sets → New Posture Policy
- Modules: Antivirus, OS patch level, disk encryption, firewall status.
- Endpoint Group Configuration:
- GUI: Administration → Identity Management → Identity Groups → BYOD
- Authorization Profile Mapping:
- GUI: Policy → Authorization → Authorization Profiles
- Assign VLAN:
Employee_VLAN - Configure DACLs to restrict non-compliant endpoints.
- Policy Set Mapping:
- GUI: Policy → Policy Sets → New Policy Set
- Condition: Endpoint Identity Group = BYOD
- Authentication: 802.1X (EAP-PEAP)
- Authorization: Map to BYOD Authorization Profile.
Validation Steps:
- CLI:
show posture sessions show authentication sessions details show authorization sessions
- GUI: Policy Troubleshooter for test endpoints.
- Test with compliant and non-compliant devices: ensure compliance checks block access for non-compliant endpoints.
Use Case 3: Multi-Site HA Deployment with Failover
Scenario:
Deploy ISE across two data centers to ensure high availability and policy replication.
Step-by-Step Mapping:
- Node Deployment:
- VMware: Deploy PAN, 2x PSNs, MnT in both sites.
- HA & Replication Setup:
- GUI: Administration → System → Deployment → Add Node → Configure HA
- Verify replication group membership for policy and monitoring data.
- Network Device Grouping:
- GUI: Assign switches and WLCs to site-specific network device groups.
- Policy Mapping:
- GUI: Policy → Policy Sets → New Policy Set
- Condition: Network Device Group = Site_A or Site_B
- Authentication & Authorization: Map per site policies.
Validation Steps:
- CLI:
show cluster summary show replication status show authentication sessions summary
- GUI: Policy Troubleshooter for endpoints in both sites.
- Simulate PSN failover: take one PSN offline and verify authentication continuity.
Use Case 4: High-Volume Endpoint Authentication Simulation
Scenario:
Test ISE scalability and performance by simulating 1000+ concurrent authentication sessions.
Step-by-Step Mapping:
- Lab Setup:
- Use radtest, eapol_test, or traffic generation scripts.
- Assign endpoints to different identity groups and device types.
- Policy Set Mapping:
- GUI: Policy → Policy Sets → Authentication & Authorization
- Map multiple endpoints to respective profiles (employee, guest, IoT).
Validation Steps:
- CLI:
show system resources show authentication sessions summary show authorization sessions
- GUI: Operations → Live Auth Sessions, monitor session distribution.
- Ensure no PSN is overloaded and authentication latency is acceptable.
Use Case 5: Contractor Network Access with Limited Permissions
Scenario:
Provide temporary network access for contractors without exposing sensitive resources.
Step-by-Step Mapping:
- Identity Group: Create
Contractorgroup under GUI → Identity Management. - Authorization Profile: Assign VLAN
Contractor_VLAN, DACL limiting access. - Policy Set Mapping:
- Condition: Identity Group = Contractor
- Authentication: 802.1X or MAB
- Authorization: Contractor Authorization Profile
Validation Steps:
- CLI:
show authentication sessions details - GUI: Policy Troubleshooter → verify endpoints receive correct VLAN and restrictions.
- Attempt access to corporate servers to confirm restricted access.
Use Case 6: Multi-Authentication Deployment (Wired + Wireless + VPN)
Scenario:
A single ISE deployment handling multiple authentication methods for diverse endpoints.
Step-by-Step Mapping:
- Policy Set Creation:
- GUI: Policy → Policy Sets → New Policy Set
- Condition: Network Device Type (Switch/WLC/ASA) or Endpoint Type.
- Authentication Configuration:
- 802.1X for wired users
- MAB for legacy devices
- VPN authentication via ASA or AnyConnect
- Authorization Profile Mapping:
- Assign appropriate VLANs, ACLs, or DACLs for each method.
Validation Steps:
- CLI:
show authentication sessions details show authorization sessions
- GUI: Policy Troubleshooter → test wired, wireless, and VPN endpoints.
- Ensure correct profiles applied per endpoint type.
Use Case 7: BYOD and IoT Mixed Environment
Scenario:
Secure network deployment where employees’ BYOD devices coexist with IoT endpoints.
Step-by-Step Mapping:
- Profiler & Posture Policies:
- Separate rules for IoT vs BYOD.
- Authorization Profiles:
- Employee BYOD → VLAN
Employee_VLAN, full access - IoT → VLAN
IoT_VLAN, restricted ACLs
- Employee BYOD → VLAN
- Policy Set Mapping:
- GUI: Map based on endpoint type and identity group.
Validation Steps:
- CLI:
show profiler cache show authorization sessions
- GUI: Live Auth Sessions → verify endpoints receive correct VLANs and access restrictions.
- Test simultaneous authentication from BYOD and IoT devices.
FAQs
1. How do I design VLAN and ACL mappings for multiple endpoint groups in an enterprise NAC deployment?
Answer:
- Plan endpoint groups by device type, user role, and location.
- Map each group to an Authorization Profile in ISE with VLAN, ACL, downloadable ACLs, and QoS policies.
- Use Policy Sets to conditionally apply profiles based on device identity, authentication method, and network device group.
2. How do I validate 802.1X and MAB authentication for pilot endpoints?
Answer:
- GUI: Operations → RADIUS → Live Auth Sessions, filter by endpoint MAC or username.
- CLI:
show authentication sessions details debug radius all
- Verify successful Access-Request and Access-Accept, assigned VLAN, and authorization profile.
3. How do I troubleshoot BYOD endpoints that fail posture or profiling checks?
Answer:
- Check profiler cache:
show profiler cache - Posture session status:
show posture sessions - GUI: Work Centers → Profiler/Posture Reports
- Adjust device fingerprint rules or posture policies as needed, and re-test.
4. How can I ensure high availability across multiple ISE nodes (PAN/PSN/MnT)?
Answer:
- CLI:
show cluster summary show replication status
- GUI: Administration → System → Deployment
- Verify all nodes are active, policies are replicated, and failover triggers work correctly.
5. How do I simulate high-volume endpoint authentication for load testing?
Answer:
- Use radtest, eapol_test, or traffic generation scripts to simulate multiple endpoints.
- Monitor PSN load:
show system resources - Verify authentication sessions:
show authentication sessions summary
6. How can I verify profiler device classification accuracy for IoT or unknown devices?
Answer:
- CLI:
show profiler cache→ check detected attributes (MAC, DHCP, HTTP headers). - Adjust profiler rules or update the fingerprint database.
- GUI: Work Centers → Profiler → Profiler Cache for live validation.
7. How do I validate authorization profile enforcement across wired and wireless networks?
Answer:
- GUI: Policy Troubleshooter → input endpoint or MAC → verify applied profile, VLAN, ACL, and role.
- CLI:
show authorization sessions→ confirm applied attributes. - Test connectivity to ensure proper network access and restrictions.
8. How do I perform TAC-level log correlation between ISE and network devices?
Answer:
- Collect timestamps of authentication events from ISE logs:
show logging application ise - Correlate with switch/WLC logs:
show logging | include RADIUS - Packet capture tools (Wireshark) can validate RADIUS Access-Request and Access-Accept/Reject flows.
9. How do I safely adjust policies during an active deployment?
Answer:
- Apply changes in pilot or test endpoint groups first.
- Validate using Policy Troubleshooter, Live Auth Sessions, and CLI commands:
show authentication sessions details show authorization sessions
- Roll out incrementally to minimize production impact.
10. How can I generate compliance-ready reports for enterprise NAC audits?
Answer:
- GUI: Operations → Reports → Authentication & Authorization Reports
- Export reports for endpoints, VLAN assignments, posture compliance, and failed sessions.
- Use these reports to demonstrate adherence to corporate security policies and regulatory standards.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- End-to-end enterprise NAC deployment requires planning, pilot testing, deployment, and validation.
- GUI + CLI validation ensures policy correctness and authentication continuity.
- Profiling, posture, and HA configurations must be continuously monitored.
- Mastering end-to-end deployment prepares engineers for real-world CCIE-level NAC challenges.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to Network Journey on YouTube and join my instructor-led classes. Learn full enterprise NAC deployment workflows, policy mapping, and zero-downtime validation strategies.
Fast-Track to Cisco ISE Mastery Pro
4-Month Instructor-Led CCIE Security Program:
- Hands-On Labs: Full NAC deployment, profiling, posture, HA, BYOD, IoT
- Expert Mentorship: End-to-end validation and troubleshooting
- Exam-Oriented Guidance: Real-world case studies and lab scenarios
- Certificate of Completion: Industry-recognized
- Register here: networkjourney.com/ccie-security
Master enterprise NAC deployment with confidence—apply real-world skills for CCIE Security success.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088


![Mastering STP Tuning: Optimizing Priority & Path Cost for Smarter Network Redundancy [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/Mastering-STP-Tuning_Optimizing-Priority_Path-Cost-for-Smarter-Network-Redundancy_networkjourney.png)
