Configuring QoS on Cisco Devices: Boost Performance & Ensure Traffic Priority [CCNP Enterprise]
I know those moments when your VOIP calls crackle or your video meetings lag during business hours—it’s like trying to have a conversation through a wall! Over the years, I’ve learned that configuring Quality of Service (QoS) on Cisco devices can be a true game-changer. Together, we’ll explore how to set it up, why it matters, and walk step-by-step through an Eve-NG lab. Grab your favorite chai, and let’s get your network humming smoothly again.
Table of Contents
Theory in Brief
What is QoS?
Quality of Service (QoS) refers to a set of tools and techniques network engineers use to control and prioritize traffic based on rules and policies. With QoS, crucial applications like voice, video, and critical data get priority handling over less important traffic like file downloads or social media.
Why do we need QoS?
In enterprise environments—where voice, video, cloud services, and data flows all coexist—unmanaged traffic leads to dropped packets, latency spikes, and jitter. QoS ensures that time-sensitive data is handled promptly, while less-critical flows are queued or limited.
How QoS works on Cisco devices
Cisco devices use a structured approach called Modular QoS CLI (MQC) where you:
- Classify traffic (class-maps),
- Mark or manipulate it (policy-maps),
- Apply policies to interfaces (service-policy).
You can also configure trust boundaries, policing vs. shaping, queues (LLQ, CBWFQ), and congestion-avoidance mechanisms like WRED. The result: more predictable, efficient networks.
Summary / Comparison / Pros & Cons
| Feature | Description | Pros | Cons |
|---|---|---|---|
| MQC (class-map) | Defines what traffic to match (ACLs, DSCP, NBAR) | Granular traffic matching, reusable | Initial config takes planning |
| policy-map | Defines actions like priority, queue, policing, shaping | Flexible—prioritize, police, shape | Misconfig can disrupt traffic flow |
| service-policy | Applies policy to interface, ingress or egress direction | Easy deployment, per-interface control | Must be applied in correct direction |
| LLQ | Strict priority queue for real-time traffic | Low latency/jitter for voice and video | Could starve other traffic if misconfigured |
| CBWFQ | Weighted queuing for fair bandwidth allocation | Prevents starvation, ensures fairness | No strict priority, not ideal for VoIP |
| Policing | Enforces rate limit by dropping excess packets | Controlled rate enforcement | Drops unwanted bursts, may disrupt apps |
| Shaping | Buffers excess to smooth bursts | Burst absorption without drops | Introduces delay, buffer management |
| Trust boundary | Controls which markings are honored | Prevents spoof, secures network | Must be defined and enforced across network |
| WRED | Random Early Drop to avoid buffer overflows | Smooth congestion avoidance | Needs careful tuning on thresholds |
Essential CLI Commands
| Task | Command Example | Purpose |
|---|---|---|
| View QoS policy on interface | show policy-map interface Gi0/1 | Displays applied policies and traffic stats |
| Debug classification | debug qos packet class-map VOICE | Real-time classification troubleshooting |
| Show queue statistics | show queueing interface Gi0/1 | Displays queue utilization and drops |
| Show class-map | show class-map | Shows classification definitions |
| Show policing and shaping stats | show policy-map interface Gi0/1 | Includes policing/shaping counters |
| Clear policy counters | clear policy-map interface Gi0/1 counters | Reset counters for fresh measurements |
| Trust state check | show mls qos interface Gi0/2 trust | Verifies if interface trusts DSCP or CoS |
| Show QoS config globally | `show running-config | section policy-map` |
| Show WRED table | show wred interface Gi0/1 | Shows WRED settings and profiles applied |
| Verify NBAR protocol match | show policy-map interface Gi0/1 class VOICE | Shows packet counts for class — confirms classification |
Real-World Use Case
| Scenario | Description | Solution Implemented | Outcome |
|---|---|---|---|
| VoIP and Video on WAN | Voice and video suffer latency during backups and file transfers | LLQ for voice, CBWFQ for video, policing for bulk traffic | Voice quality ensured, smooth video, bulk traffic delayed |
| Branch Office Internet | Guest browsing saturates bandwidth, affecting business-critical apps | Shape guest traffic, prioritize business-critical apps | Business apps get priority, browsing throttled without blocking |
| Data Center Backup | Large nightly backups compete with real-time replication traffic | Police backup pipeline during day, shape at night | Backup runs reliably off-hours, replication unaffected during day |
| Cloud Application Access | API calls to SaaS are slow during peak time | Class and prioritize API ports, shape general traffic | API latency stable, other traffic controlled |
Small EVE‑NG Lab
Lab Diagram
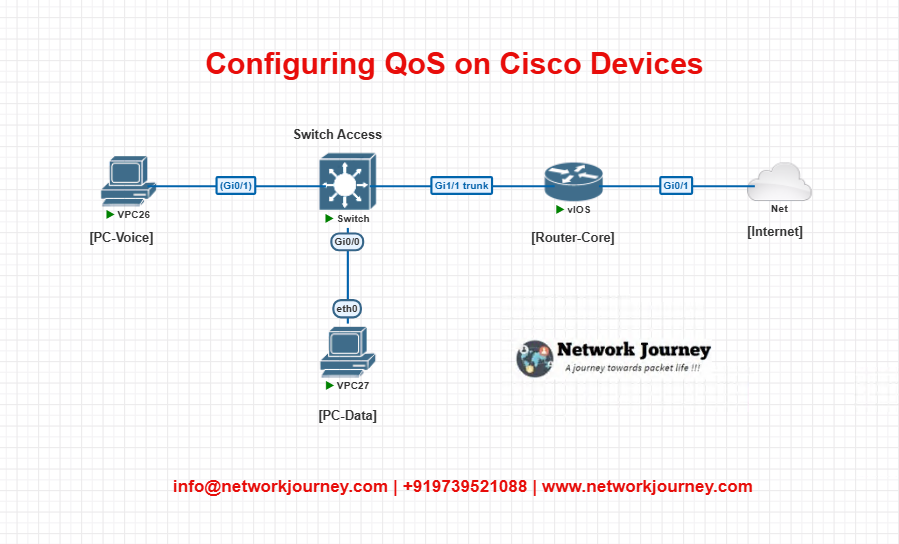
- Switch-Access: Connected to PC-Voice & PC-Data; VLAN 10 for voice
- Router-Core: Implements QoS on egress interface (toward Internet)
CLI Configuration
Switch-Access
interface Gi0/1 switchport mode access switchport access vlan 10 mls qos trust cos interface Gi0/2 switchport mode access switchport access vlan 20 mls qos trust none interface Gi1/1 switchport mode trunk mls qos trust dscp
Router-Core
class-map match-any VOICE
match ip dscp ef
class-map match-any BULK
match access-group 101
access-list 101 permit ip any any
policy-map WAN-QOS
class VOICE
priority percent 20
class BULK
police 50000000 conform-action transmit exceed-action drop
class class-default
fair-queue
interface Gi0/1
service-policy output WAN-QOS
Troubleshooting Tips
| Problem | Possible Cause | Troubleshooting Tip |
|---|---|---|
| Voice jitter and delay | Missing LLQ or incorrect percent reservation | Verify config with show policy-map interface; check preemptive order |
| Bulk traffic still congesting | Shaping not applied; policing insufficient | Confirm policing with show policy-map; adjust rate |
| Packets dropped unexpectedly | Queue overflow | Inspect queue stats via show queueing interface and WRED setup |
| DSCP not honored across switches | Trust boundary incorrect | Use show mls qos interface to verify and adjust trust |
| Counters not incrementing | Policy not applied correctly | Ensure policy is bound to correct interface/direction |
FAQs
1: What is QoS and why is it essential on Cisco networks?
Answer:
QoS (Quality of Service) is a set of technologies used to manage and prioritize network traffic. On Cisco networks, QoS helps ensure that critical applications like VoIP, video conferencing, or business-critical SaaS receive the necessary bandwidth, low latency, and minimal packet loss. Without QoS, all traffic is treated equally, which can cause poor performance for latency-sensitive services during congestion.
2: What is MQC (Modular QoS CLI), and how does it work?
Answer:
MQC is Cisco’s modular approach to QoS configuration. It breaks down QoS into three logical steps:
- Class-map – Identifies traffic based on criteria like DSCP, ACL, or NBAR protocols.
- Policy-map – Defines what to do with the classified traffic (e.g., prioritize, police, shape).
- Service-policy – Applies the policy to an interface (ingress or egress).
This modularity makes QoS configurations reusable, organized, and scalable.
3: How do I decide between policing and shaping?
Answer:
- Policing: Drops or marks traffic that exceeds a certain rate. It is more aggressive and used when you want strict bandwidth enforcement.
- Shaping: Buffers excess traffic and sends it later to smooth bursts. Ideal for outbound traffic to WAN links or MPLS providers.
Use shaping for outbound WAN links to avoid drops.
Use policing to restrict traffic from untrusted sources or enforce SLA contracts.
4: What is Low Latency Queuing (LLQ) and when should I use it?
Answer:
LLQ provides a strict priority queue for traffic that needs ultra-low delay and jitter—like voice and video.
In your policy-map, you’d use:
class VOICE priority percent 30
This guarantees bandwidth and always sends VOIP packets first. Be cautious—if misconfigured, it can starve other traffic, so always define bandwidth limits.
5: Where should QoS policies be applied—in ingress or egress?
Answer:
- Egress (outbound): Most QoS actions like queuing, shaping, and prioritization happen here. This is the most common place to apply policies.
- Ingress (inbound): Used for classifying, marking, or policing traffic as it enters the device. Limited actions supported.
Best practice: Apply policies at the egress of WAN interfaces and use ingress marking/policing at access switches or untrusted zones.
6: What are DSCP values, and how are they used in QoS?
Answer:
DSCP (Differentiated Services Code Point) is a 6-bit value in the IP header used to mark and classify packets.
Common DSCP values:
| DSCP | Value | Purpose |
|---|---|---|
| EF | 46 | Voice (Expedited Forwarding) |
| AF41 | 34 | High-priority Video |
| CS6 | 48 | Network Control |
| Default | 0 | Best Effort |
Cisco devices can match on DSCP values in class-maps and prioritize or restrict traffic accordingly.
7: What is a trust boundary and why does it matter in QoS?
Answer:
A trust boundary defines where QoS markings (CoS/DSCP) are either trusted (preserved) or overwritten.
- Trust known devices like IP phones (e.g., via CDP).
- Do not trust end-hosts like laptops or PCs—they may mark traffic unfairly.
You configure trust using:
mls qos trust dscp
or
mls qos trust cos
depending on whether the device is using Layer 3 or Layer 2 markings.
8: Can QoS work across the Internet?
Answer:
Generally, no. Most ISPs do not honor DSCP markings across the public internet. They may strip them or treat all traffic as best effort.
However, QoS works well in private WAN environments, such as:
- MPLS (where SLAs exist)
- SD-WAN (where DSCP can be mapped to tunnel classes)
- VPNs over Internet (when marked internally)
Always verify QoS behavior with your provider or SD-WAN vendor.
9: How can I verify that QoS is working correctly?
Answer:
Use Cisco CLI commands:
show policy-map interface Gig0/1– Displays traffic matching, drops, shaping stats.show class-map– View definitions of traffic classes.show queueing interface– See output queue lengths and drops.debug qos packet– (Use with care) for real-time matching logs.
Check if your VOICE or VIDEO classes are receiving traffic and not dropping packets unnecessarily.
10: What are common mistakes in QoS deployment?
Answer:
- Forgetting to apply the service-policy to the interface.
- Trusting end devices that shouldn’t be trusted (e.g., PCs).
- Using LLQ without bandwidth limits, starving other traffic.
- Policing instead of shaping on outbound WAN, causing unnecessary drops.
- Misclassification due to missing ACLs, wrong DSCP, or unsupported NBAR protocols.
To avoid these issues, test in labs like EVE-NG, validate configs with show commands, and monitor traffic over time.
YouTube Link
Watch the Complete CCNP Enterprise: Configuring QoS on Cisco Devices: Boost Performance & Ensure Traffic Priority Lab Demo & Explanation on our channel:
Final Takeaways
Understanding how to differentiate and implement Configuring QoS on Cisco Devices: Boost Performance & Ensure Traffic Priority is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![Configuring QoS on Cisco Devices: Boost Performance & Ensure Traffic Priority [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/Configuring-QoS-on-Cisco-Devices_Boost-Performance_Ensure-Traffic-Priority_networkjourney.png)
![Can ARP ACLs Replace DHCP Snooping for ARP Security? Let’s Find Out! [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-ARP-ACLs.jpg)
![NETCONF vs RESTCONF – Choosing the Right Protocol for Network Automation [CCNP ENTERPRISE]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/07/NETCONF-vs-RESTCONF-–-Choosing-the-Right-Protocol-for-Network-Automation-1.png)
![Mastering EtherChannel Load Balancing Methods: A Complete Guide with CLI & EVE-NG Lab [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/Mastering-EtherChannel-Load-Balancing-Methods_A-Complete-Guide_networkjourney.png)