[Day 100] Cisco ISE Mastery Training: Full Integration Scenario
Table of Contents
Introduction
Welcome to Day 100 – Cisco ISE Mastery Training: Full Integration Scenario.
This is not just another lab; this is the grand finale—where everything you’ve learned about Cisco ISE so far comes together into a single, unified production-grade design.
In the real world, no ISE deployment runs in isolation. Enterprises depend on switches, wireless LAN controllers, firewalls, Active Directory, PKI, MDM platforms, and SIEM systems all working in harmony. The challenge? Ensuring these integrations are secure, scalable, and resilient without introducing authentication delays, policy mismatches, or operational blind spots.
This integration scenario will push you to think like an ISE Solutions Architect—designing policies that align with business intent, optimizing performance for scale, and validating every single component using both GUI and CLI. By the end of this workbook, you will not only understand how to configure full-stack integrations but also how to validate, troubleshoot, and fine-tune them like an expert.
Think of this as your capstone project: where theory meets practice, and practice meets enterprise-grade reality.
Problem Statement
Modern networks mix managed laptops, mobile BYOD, contractors, IoT/voice, and remote users. Security teams must continuously verify: who is connecting, with what posture, from where, and to what. Without a unified NAC brain, you get:
- Fragmented auth policies, inconsistent access across wired/wireless/VPN.
- Manual firewall rules (no identity/context), slow threat response.
- Guest and BYOD sprawl, poor auditability.
- Unscalable operations: break/fix during logon storms and upgrades.
Solution Overview
Cisco ISE solves this by centralizing Authentication (RADIUS/TACACS+), Authorization (dACL/VLAN/SGT/ACL), Posture/BYOD, Guest, Profiling, pxGrid context sharing, and MDM compliance. You’ll implement separate Policy Sets for Wired/Wireless/VPN/Guest/TACACS and glue them with Identity Sources (AD + MDM), Results (AuthZ Profiles/dACL/SGT/VLAN/Redirect), TrustSec, and pxGrid to your NGFW/SIEM—then prove it with GUI + CLI.
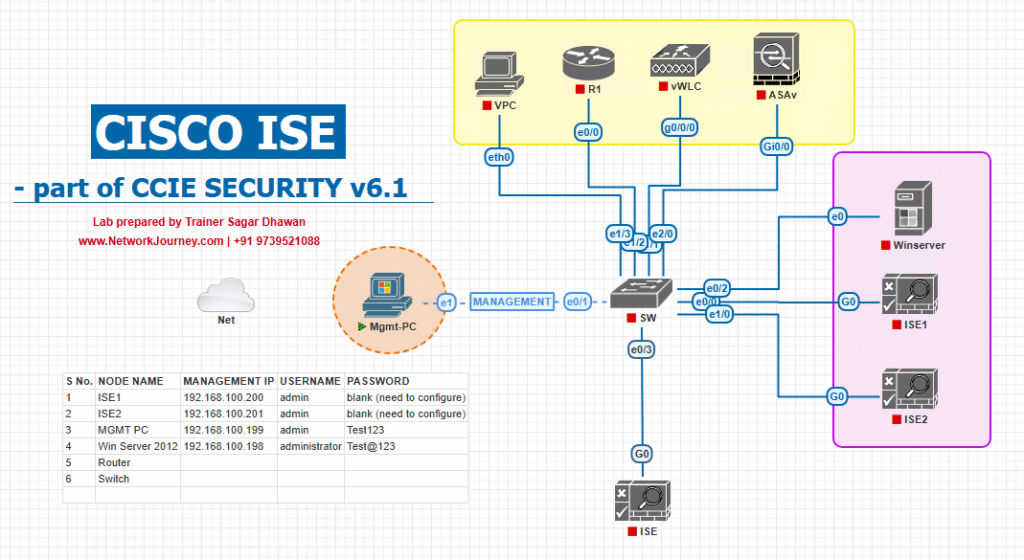
Sample Lab Topology (VMware/EVE-NG)
Compute / VMs
- ISE-PAN/MnT (Primary), ISE-PSN1, ISE-PSN2
- AD/LDAP + CA (ADCS)
- MDM (e.g., Intune connector / mock)
- FMC/FTD (or ASA) for VPN + NGFW policy
- Stealthwatch/SIEM (optional) via pxGrid/syslog
- SFTP (ISE repository)
- Jump host (OpenSSL/cURL), Win 11, macOS, iPhone, IoT printer, IP phone
Network
- Catalyst 9300 (wired 802.1X/MAB/SGT)
- WLC 9800 (SSIDs: Corp-8021X, Guest-Portal, BYOD-Onboard)
- LB (optional) in front of PSNs for RADIUS
Step-by-Step GUI Configuration Guide
A) Pre-Flight Baseline & Hygiene
Checklist
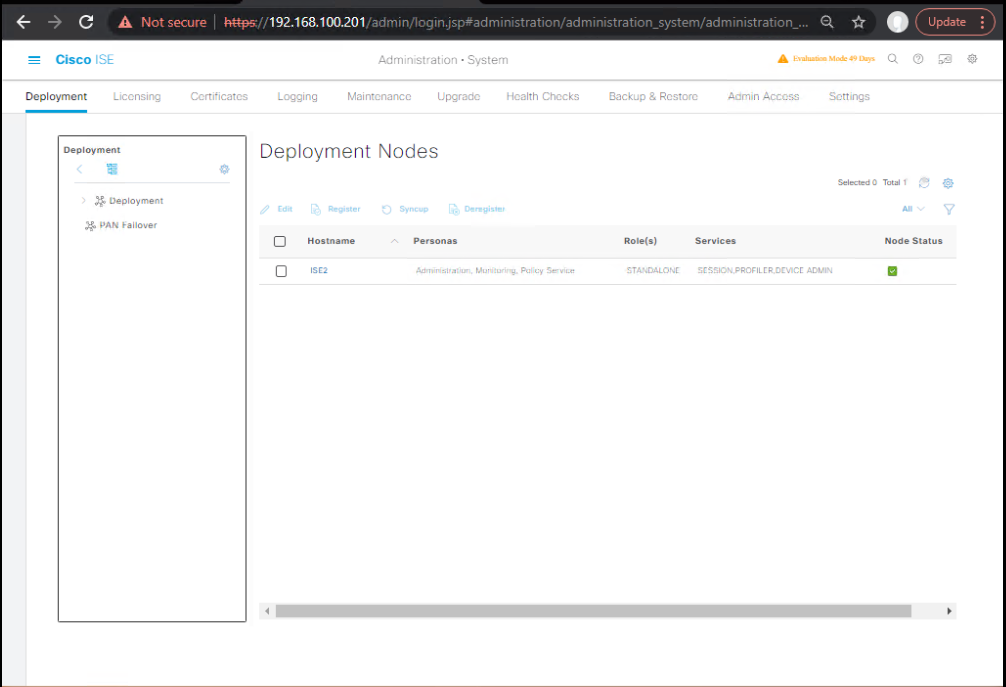
- ISE nodes Green: Administration → System → Deployment
- NTP/DNS/PKI validated across ISE/PSNs/NADs.
- EAP/Portal certificates installed; full chain trusted.
- Identity Sources: AD joined and tested.
- Repositories (SFTP) configured for backup.
- Network Devices (NADs) added with correct RADIUS shared keys and NDG mapping.
- Allowed Protocols tailored (EAP-TLS/PEAP/MAB only if that’s all you use).
ISE CLI Quick Checks
show application status ise show ntp show dns show crypto pki certificates show logging application | include (error|radius|ad)
B) Certificates & Identity Sources
- Install/Bind EAP & Portal Certificates
GUI: Administration → System → Certificates → System Certificates → Import
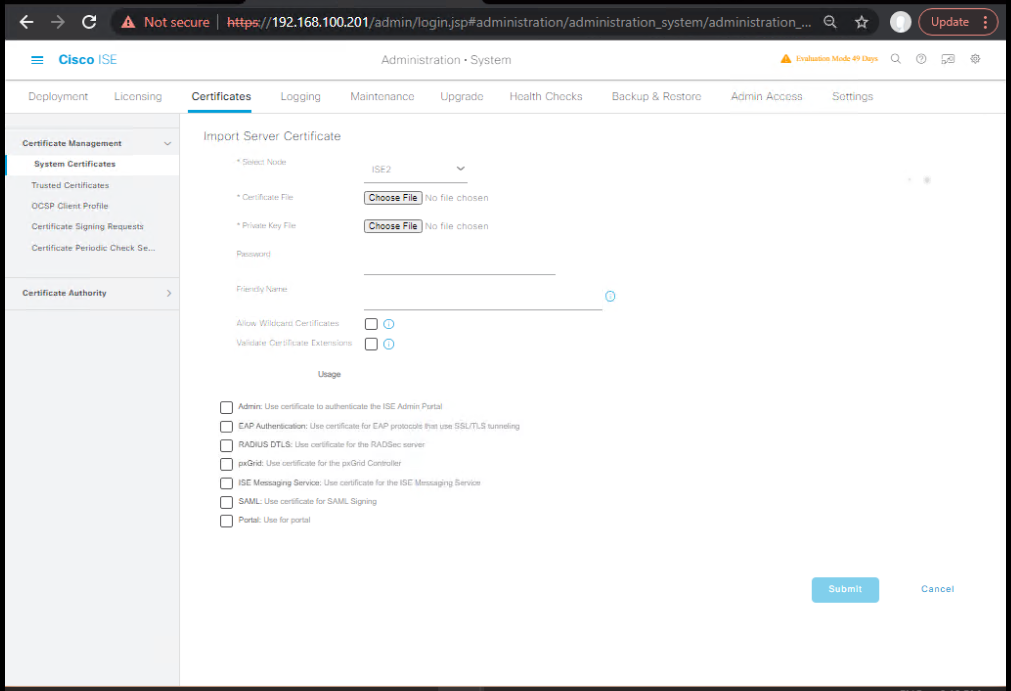
- Bind usages: EAP Authentication, Admin/Portal.
- Import Root/Intermediate under Trusted Certificates.
Validation
- Client TLS test:
openssl s_client -connect <psn-fqdn>:443 -showcerts </dev/null | openssl x509 -noout -issuer -subject
- Join AD
GUI: Administration → Identity Management → External Identity Sources → Active Directory → Join
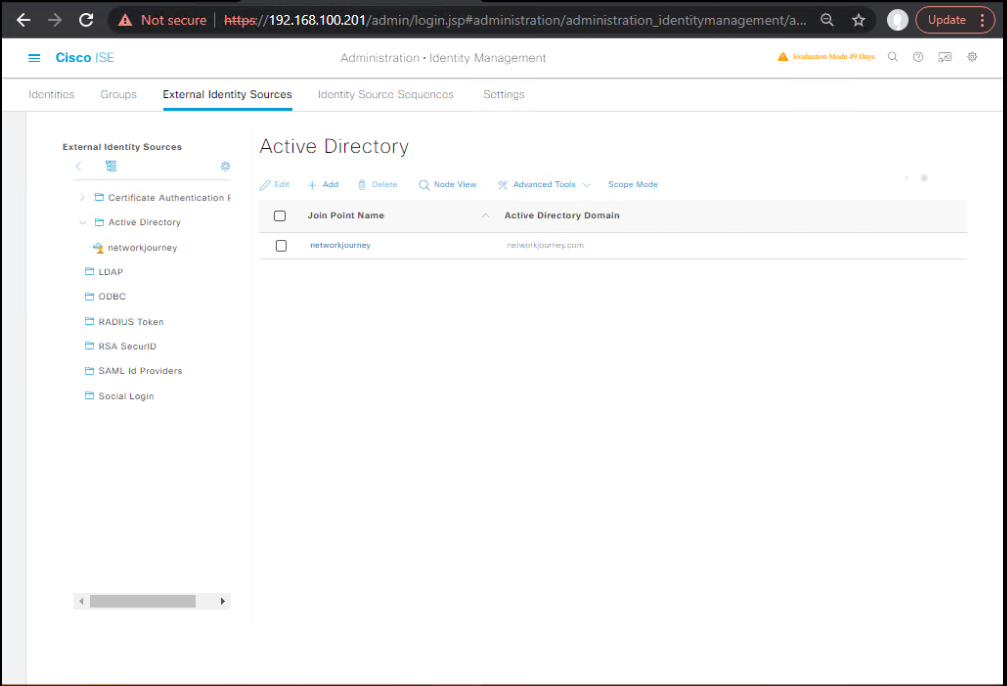
- Map Groups: Domain Users, Contractors, NetOps, etc.
Validation
- CLI:
show logging application ise-psc.log | include ad
C) Add Network Devices (Switch/WLC/FTD/ASA/VPN)
GUI: Administration → Network Resources → Network Devices → Add
- Define Device Type/Location (NDG) for routing to correct Policy Set.
- Add both PSNs as RADIUS servers on NADs.
NAD CLI Snippets
Catalyst
aaa new-model radius server ISE1 address ipv4 <PSN1> auth-port 1812 acct-port 1813 key <secret> radius server ISE2 address ipv4 <PSN2> auth-port 1812 acct-port 1813 key <secret> aaa group server radius ISE-GRP server name ISE1 server name ISE2 aaa authentication dot1x default group ISE-GRP aaa authorization network default group ISE-GRP aaa accounting update periodic 15 aaa accounting dot1x default start-stop group ISE-GRP dot1x system-auth-control interface Gi1/0/10 authentication order mab dot1x authentication priority dot1x mab authentication port-control auto mab authentication periodic authentication timer reauthenticate 3600 spanning-tree portfast
WLC 9800
radius server ISE1 address ipv4 <PSN1> auth-port 1812 acct-port 1813 key 7 <secret> radius server ISE2 address ipv4 <PSN2> auth-port 1812 acct-port 1813 key 7 <secret> aaa authentication dot1x default radius aaa accounting dot1x default start-stop radius
ASA/FTD (RADIUS for VPN)
aaa-server ISE protocol radius aaa-server ISE (inside) host <PSN1> key <secret> aaa-server ISE (inside) host <PSN2> key <secret> tunnel-group Corp-AnyConnect general-attributes authentication-server-group ISE accounting-server-group ISE
Validation
# Catalyst show aaa servers show radius statistics # WLC show radius summary # ASA test aaa authentication ISE host <PSN1> username test password <pwd>
D) Policy Elements (Results) First
GUI: Policy → Policy Elements → Results
- Authorization Profiles
- EMP-FULL: dACL
ALLOW-CORPor VLANCorp-Data, SGTEmployees. - CONTRACTOR-LIMIT: dACL
CONTRACTOR+ SGTContractors. - QUAR-POSTURE: dACL
QUAR+ URL-Redirect to posture portal. - GUEST-INTERNET: WLC Airespace ACL or dACL allowing only Internet.
- VOICE-VLAN: VLAN 20 +
device-traffic-class=voice. - VPN-FULL: (for VPN) assign SGT or ACL result (FMC integration).
- Downloadable ACLs (dACLs)
ALLOW-CORP:permit ip any 10.10.0.0 0.0.255.255 permit udp any any eq 53 permit tcp any any eq 443 deny ip any anyQUAR:deny ip any 10.0.0.0 0.255.255.255 permit tcp any any eq 80 permit tcp any any eq 443
- SGT (TrustSec)
Work Centers → TrustSec → Components → Security Groups
- Employees, Contractors, Guests, Printers, Phones, VPN-Users
- Time Conditions
Policy Elements → Conditions → Date & Time → BusinessHours
E) Build Policy Sets (RADIUS – Wired/Wireless/VPN/Guest)
E1. RADIUS-Enterprise (Wired + Corp WLAN)
GUI: Policy → Policy Sets → Add
- Condition:
Device:Device Type IN [Switch, WLC]ANDProtocol = RADIUS - Allowed Protocols: Custom (EAP-TLS/PEAP/MAB)
Authentication Policy (order)
- Wireless DOT1X:
Airespace:SSID = "Corp-8021X"→ Identity: AD_Sequence - Wired DOT1X:
UseCase = WiredDOT1X→ AD_Sequence - MAB:
AuthenticationMethod = MAB→ Identity: Internal Endpoints
Default: Deny
Authorization Policy (order)
- EAP-TLS + AD Domain Users → EMP-FULL
- Posture NonCompliant → QUAR-POSTURE
- Printer (Profiled / Group) → IoT-Printer-Limited
- IP Phone → VOICE-VLAN
- Contractors + BusinessHours → CONTRACTOR-LIMIT
Default: Deny or Very-Limited
Validation
- GUI: Operations → RADIUS → Live Logs; check Matched Rule + Result.
- Catalyst:
show authentication sessions interface Gi1/0/10 details show access-lists dynamic show cts role-based sgt-map all - WLC:
show wireless client mac <MAC> detail
E2. VPN Policy Set (AnyConnect/ASA or FTD)
- Condition:
Device:Device Type = VPN-HeadendANDProtocol = RADIUS - AuthN: AD_Sequence (and/or Cert if doing EAP-TLS for VPN)
- AuthZ Rules:
AD-Group = Corp\Domain Users→ VPN-FULL (assign SGTVPN-Users)AD-Group = Contractors→ CONTRACTOR-LIMIT (VPN)
Validation
- ASA:
show vpn-sessiondb anyconnect show aaa-server ISE - ISE Live Logs show VPN sessions, SGT/ACL pushed.
E3. Guest Policy Set (WebAuth/Hotspot/Sponsor)
- Condition:
UseCase = WirelessMABANDSSID = "Guest-Portal" - AuthN: MAB / Internal Users (guest accounts)
- AuthZ:
- Pre-auth → Guest-Redirect (Portal)
- Authenticated → GUEST-INTERNET
Validation
- WLC pre-auth ACL present; client redirected to ISE Guest Portal.
- ISE Live Logs show WebAuth steps/handoff.
F) BYOD & Posture
- BYOD Onboarding
- Work Centers → BYOD → Portals → Onboarding Portal → create & publish.
- Add AuthZ rule:
Endpoint Identity Group = RegisteredDevices→ EMP-FULL (or limited per policy).
- Posture (AnyConnect)
- Client Provisioning: Policy → Client Provisioning → Map OS to AnyConnect + Posture module.
- Posture Policy: Policy → Posture → Requirements (AV/Firewall/Updates).
- AuthZ rule:
PostureStatus = NonCompliant→ QUAR-POSTURE (redirect), Compliant → EMP-FULL.
Validation - Client shows posture scan; ISE Live Logs show NonCompliant → Compliant with CoA.
G) Profiling
- Work Centers → Profiler → Settings → Enable DHCP + RADIUS probes (others only if needed).
- Profiling Policies: ensure specific vendors (HP-Printer, IP-Phone) above generic.
Validation - Live Logs show Profiled endpoints; check Endpoint Identity Group updates.
H) TrustSec / SGT → NGFW (FMC/FTD)
- Assign SGT in ISE AuthZ Profiles (done above).
- SGT propagation:
- Classic CTS: SXP between ISE and network devices/firewall or
- SDA/Fabric: Fabric edge assigns SGT natively.
- FMC: build Access Control Policy using user/SGT context.
Validation
- Switch:
show cts role-based sgt-map all show cts role-based permissions - FMC/FTD: verify policy matches on SGT.
I) pxGrid Integrations (NGFW/SIEM/Analytics)
- Enable pxGrid: Work Centers → pxGrid Services → Settings → Enable.
- Approve clients (FMC/SIEM/Stealthwatch).
- On consumer (FMC/SIEM), import ISE pxGrid cert and connect; subscribe to Session Directory / SGT Mappings.
Validation
- pxGrid clients Online in ISE.
- FMC/Stealthwatch shows active ISE sessions/SGTs.
J) MDM (e.g., Intune) Compliance
- Add MDM: Administration → Identity Management → External MDM → Add (URL, credentials, cert trust).
- Enable MDM attributes in Policy.
- AuthZ rule example:
MDM:Compliant = True→ EMP-FULL; else → MDM-Remediate (redirect).
Validation
- Endpoint MDM status appears under Context Visibility.
- Live Logs show MDM attributes evaluated.
K) TACACS+ Device Administration
- Enable Device Admin: Administration → Device Administration → Settings → Enable.
- Results:
- Shell Profiles: Priv15, Priv5
- Command Sets: NetOps-Full, Ops-RO
- Policy Set (TACACS):
- AuthN: AD or Internal Users
- AuthZ:
AD-Group = NetOps→ Priv15/Full;Ops-RO→ Priv5/RO
Validation
- Switch/Router:
test aaa group tacacs+ netops_user <pwd> new-code - ISE: Operations → TACACS → Live Logs show Shell/Command Set.
L) Load Balancer (Optional)
- Health checks using real RADIUS Access-Request.
- Persistence by Calling-Station-ID or Framed-IP.
Validation - Even distribution across PSNs; ISE radius logs show balanced load.
M) End-to-End Validation Walk-Through (Golden Tests)
- Wired Employee (EAP-TLS)
- Plug Win11 → 802.1X success → EMP-FULL (dACL/VLAN/SGT).
- Check:
- ISE Live Logs: EAP-TLS, AuthZ=EMP-FULL
- Switch:
show authentication sessions int Gi1/0/10 details show access-lists dynamic show cts role-based sgt-map all
- Wireless Corp SSID (PEAP)
- PEAP user → EMP-FULL.
- Check: WLC client details show ACL/VLAN; ISE Live Logs rule hit.
- Non-Compliant Posture
- Disable AV → connect → QUAR-POSTURE redirect → comply → CoA → EMP-FULL.
- Check: Live Logs posture transition, CoA events.
- Guest
- Connect to Guest-Portal → web-auth portal → Internet only.
- Check: ISE Guest reports; WLC Airespace ACL applied.
- BYOD
- Onboard mobile → device appears in RegisteredDevices → EMP-FULL/Limited per your rule.
- Check: Context Visibility shows device; Live Logs show BYOD steps.
- VPN User
- AnyConnect auth → ISE returns VPN-FULL (SGT).
- Check: ASA/FTD shows session + ISE hit; NGFW policy matches SGT.
- TACACS
- NetOps vs Ops-RO: confirm command authorization.
- Check: ISE TACACS Live Logs show Shell/Command Set.
- pxGrid
- FMC/SIEM sees user/IP/SGT/session from ISE.
- Check: pxGrid client state Online; events arriving.
FAQs
1. Q: How do I verify if Cisco ISE is properly integrated with Active Directory?
A:
- GUI Validation:
- Navigate to Administration > Identity Management > External Identity Sources > Active Directory.Check Join Status = Connected.Run Test User against AD to validate bind and group membership.
- CLI Validation:
ise/admin# show application status ise ise/admin# show logging application ad_agent.log- Look for successful Kerberos ticket acquisition and LDAP bind messages.
2. Q: What is the most common cause of WLC/ISE integration failure for wireless 802.1X clients?
A:
- Typically, mismatched RADIUS Shared Secrets or incorrect NAS IP in ISE Network Devices list.
- Validation:
- On ISE GUI: Administration > Network Resources > Network Devices → confirm WLC entry.
- On WLC CLI:
(Cisco Controller) > show radius summaryEnsure WLC is sending RADIUS requests to ISE’s IP with correct key.
3. Q: How do I validate that SGTs (Security Group Tags) are being assigned and propagated correctly?
A:
- GUI Validation:
- Navigate: Operations > RADIUS > Live Logs.
- Check Authorization Result column → must show correct SGT.
- CLI Validation:
- On Catalyst Switch:
Switch# show cts role-based sgt-maps Switch# show cts role-based counters - Verify that packets are tagged and forwarded properly.
- On Catalyst Switch:
4. Q: What steps ensure ISE is properly integrated with MDM (e.g., Intune, AirWatch)?
A:
- GUI Validation:
- Administration > pxGrid Services > MDM.
- Connection status must show Online.
- CLI Validation:
ise/admin# show logging application mdm.log- Confirm tokens are exchanged and posture compliance info is synced.
5. Q: How do I confirm pxGrid integration with Firewalls (Cisco FTD/Palo Alto)?
A:
- GUI Validation:
- On ISE: Administration > pxGrid Services > Clients. Ensure Firewall shows as a Subscribed Client.
- CLI Validation:
ise/admin# show logging application pxgrid.log- Look for session establishment events.
- On Firewall side, check session subscription to ISE topics (SGT mapping, identity info).
6. Q: How can I troubleshoot failed wired 802.1X authentication in an integrated environment?
A:
- CLI (Switch):
Switch# show authentication sessions interface Gi1/0/5 details Switch# debug dot1x all- Verify the EAP method and RADIUS result.
- ISE GUI:
- Operations > RADIUS > Live Logs → drill into the failed session → look for reasons (e.g., Invalid Certificate, No Matching Policy).
7. Q: How do I verify syslog/SIEM integration from ISE?
A:
- GUI Validation:
- Administration > System > Logging > Remote Logging Targets. Ensure SIEM server is listed.
- CLI Validation:
ise/admin# show logging ise/admin# tcpdump -i eth0 host <SIEM_IP> and port 514- Confirm ISE is actively exporting syslog messages.
8. Q: What should I check if client endpoints fail posture assessment?
A:
- Ensure AnyConnect ISE Posture Module is installed.
- GUI Validation:
- Operations > Posture > Live Sessions. Verify compliance status.
- CLI Validation:
ise/admin# show logging application posture.log- Look for posture negotiation errors.
9. Q: How do I make sure policies are applied consistently when multiple integrations exist (AD, SGT, MDM)?
A:
- Always follow Policy Set order (top-down evaluation).
- Validation:
- Policy > Policy Sets → review rules.
- Use Policy > Policy Sets > Preview Policy Matching to test inputs (user, endpoint, MDM compliance, SGT).
- CLI double-check via live session:
Switch# show authentication sessions interface Gi1/0/10 details
10. Q: After full integration, how can I baseline performance to ensure ISE cluster is not overloaded?
A:
- GUI Validation:
- Operations > Reports > System Reports > System Summary.
- Track RADIUS Authentications per Second, CPU, Memory.
- CLI Validation:
ise/admin# show cpu ise/admin# show memory ise/admin# show application status ise- Compare against Cisco’s recommended hardware sizing guide.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
A full ISE integration succeeds when each plane validates cleanly: Identity (AD/MDM), Control (Policy Sets/Results), Data (NAD timers/CoA), Visibility (pxGrid/SGT). Keep specific→general rule order, minimize CoAs, and measure after every change with Live Logs and device CLIs.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro
- I run a focused 4-month instructor-led CCIE Security track—weekly live labs on Wired/Wireless/VPN NAC, BYOD/Posture, Guest, pxGrid→NGFW/SIEM, MDM, SGT/TrustSec, TACACS, Scale & Performance.
- Outcome: Production-ready runbooks, graded capstone, interview prep.
- Course outline & enrollment: https://course.networkjourney.com/ccie-security/
- Next step: Complete the intake form → free readiness call → lab access checklist → secure your seat.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



