[Day 101] Cisco ISE Mastery Training: Large-Scale Distributed Deployment Design
Table of Contents
Introduction
Designing Cisco ISE for large-scale enterprise deployments is not a simple “add another node” exercise. It’s about engineering a security access fabric that:
- Serves hundreds of thousands of endpoints concurrently.
- Stays resilient across multiple data centers.
- Ensures authentication latency stays low even under load.
- Provides real-time visibility & troubleshooting without performance trade-offs.
A Large-Scale Distributed Deployment (LSDD) typically includes:
- Dedicated Policy Service Nodes (PSNs): Scalable authentication engines.
- Policy Administration Nodes (PANs): Centralized control + redundancy.
- Monitoring Nodes (MnTs): Centralized logging/visibility with redundancy.
- Load Balancers: To distribute RADIUS/TACACS load across PSNs.
- Replication & Synchronization: PAN → PSNs, MnT cluster consistency.
This workbook is designed as a practical masterclass:
Every section includes step-by-step GUI configuration and CLI validation so you don’t just configure — you also verify and troubleshoot like TAC engineers.
Problem Statement
The Challenge:
Small ISE clusters scale poorly in enterprise environments. Problems include:
- Authentication bottlenecks when thousands of users log in simultaneously.
- Single points of failure when PAN/MnT is not redundant.
- Slow policy propagation across nodes.
- Logging gaps when MnT fails.
- Inefficient RADIUS load balancing without proper PSN design.
Without a distributed design, enterprises risk:
- User downtime due to overload.
- Compliance failures (missing logs).
- Weak security enforcement at global scale.
Solution Overview
Cisco ISE Large-Scale Deployment Architecture provides:
- PAN redundancy → Primary & Secondary.
- PSN scalability → Multiple PSNs behind load balancers (F5, ACE, Citrix).
- MnT clustering → Active/Standby or Split for log redundancy.
- Replication model → PAN is the single point of config changes → syncs to PSNs/MnTs.
- Geo-redundancy → Deploy nodes across multiple DCs.
- CLI & GUI health checks → Validate node sync, replication, session load.
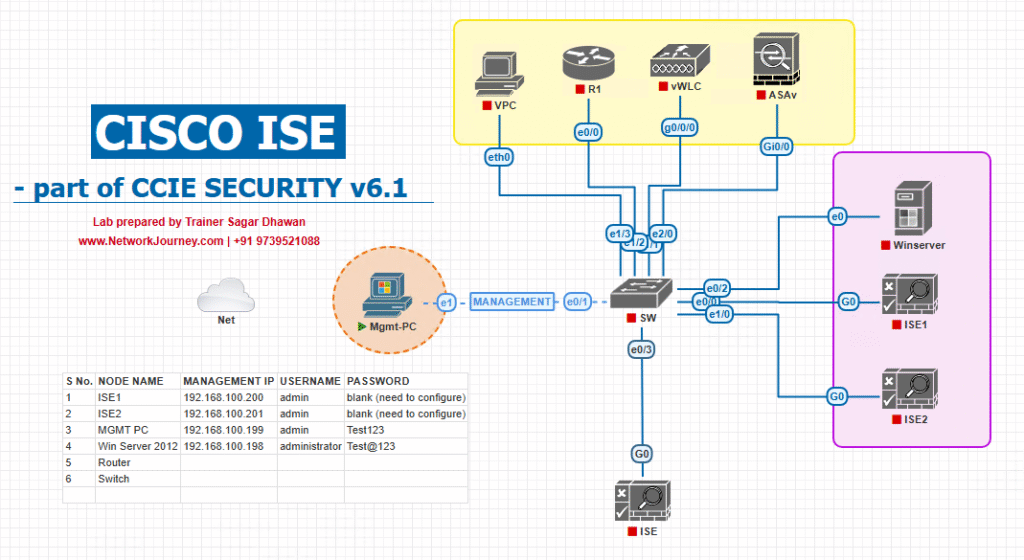
Sample Lab Topology
Lab Environment:
- Platform: VMware ESXi / EVE-NG.
- Nodes:
- 2x PAN (Primary + Secondary).
- 4x PSN (behind load balancer).
- 2x MnT (Active/Standby).
- Network Devices:
- Cisco Switch with 802.1X + MAB enabled.
- Cisco WLC for wireless integration.
- Endpoints:
- Windows 10 laptops.
- BYOD + corporate devices.
Topology Diagram:
Step-by-Step GUI & CLI Configuration Guide
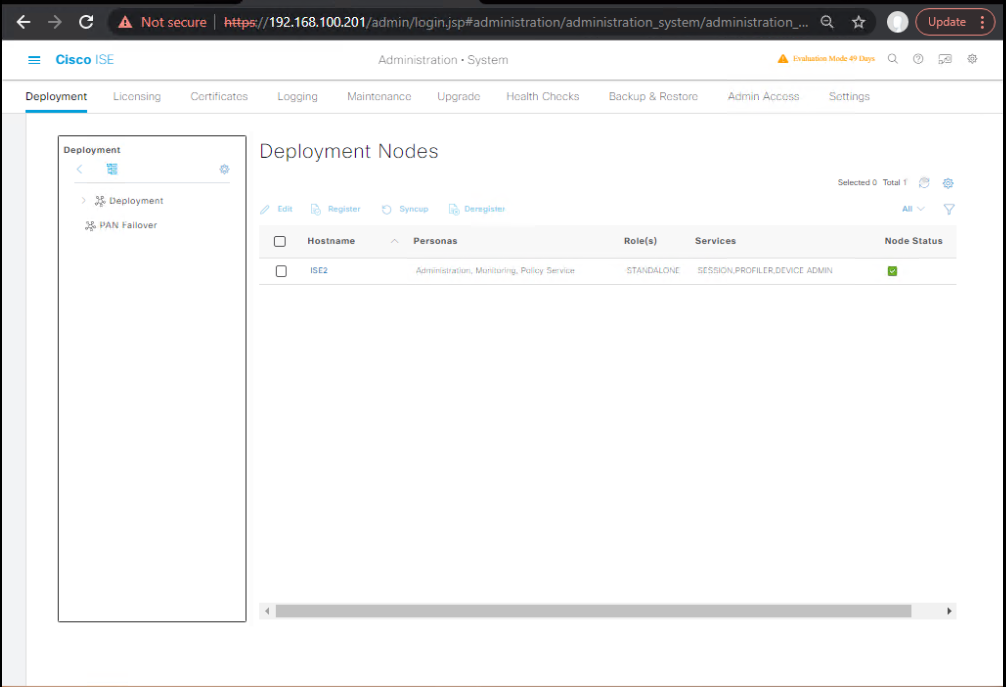
Step 1: Enable Large Deployment Mode
- GUI:
- Navigate to Administration > System > Deployment.
- Select Enable PAN & MnT redundancy.
- Apply changes.
- CLI Validation:
ise/admin# show application status ise ise/admin# show running-config ise
Step 2: Add Secondary PAN
- GUI:
- Go to Administration > System > Deployment.Register new node. Assign Admin role → mark as Secondary PAN.
- CLI Validation:
ise/admin# show logging system ise/admin# show application status ise | include Admin
Step 3: Add Multiple PSNs
- GUI:
- Register node. Assign PSN role.
- Repeat for all nodes.
- Add them behind load balancer.
- CLI Validation (on PSN):
ise/psn# show application status ise ise/psn# show radius statistics ise/psn# show sessions
Step 4: Configure MnT Clustering
- GUI:
- Register MnT node → select Monitoring role.
- Configure one as Active, other as Standby.
- CLI Validation:
ise/mnt# show logging system ise/mnt# show running-config ise
Step 5: Verify Replication & Node Health
- GUI:
- Administration > System > Deployment → Node Status
- CLI:
ise/admin# show replication status ise/admin# show application status ise
FAQs – Large-Scale Cisco ISE Distributed Deployment
1. How many nodes can a single Cisco ISE deployment support?
Answer:
- Cisco ISE supports up to 50 nodes in a single deployment (ISE 3.x).
- You can have 2 PANs (Primary + Secondary), 2 MnTs, and multiple PSNs depending on scale.
- Node roles are distributed:
- PAN: Centralized configuration.
- PSN: Authentication/Authorization runtime.
- MnT: Centralized logging.
Validation:
- GUI: Administration > System > Deployment → Check node list.
- CLI:
ise/admin# show application status ise ise/admin# show running-config ise
2. What is the recommended node role distribution in a large deployment?
Answer:
- PAN (2 nodes) → 1 Primary + 1 Secondary (DR site).
- MnT (2 nodes) → 1 Active + 1 Standby.
- PSN (Scalable) → Usually 4–20 nodes behind load balancers.
- Keep PAN/MnT roles separate from PSN in production to reduce overhead.
Tip: PAN+MnT can coexist, but in large-scale >25k endpoints, separate them.
3. How does load balancing for PSNs work in practice?
Answer:
- Use external load balancer (F5, Citrix, ACE) to distribute RADIUS/TACACS+ requests across PSNs.
- Load balancer must support persistence (“stickiness”) so the same session stays on one PSN.
- Recommended method: Source-IP based persistence.
Validation:
- GUI: Operations > RADIUS > Live Sessions → Session distribution.
- CLI:
ise/psn# show radius statistics ise/psn# show sessions
4. What happens if the Primary PAN fails?
Answer:
- The Secondary PAN remains in standby mode until you promote it manually.
- Configuration changes can only be made on active Primary PAN.
Failover Test:
- GUI: Administration > System > Deployment → Promote Secondary PAN.
- CLI:
ise/admin# application configure ise
5. Can PSNs be geographically distributed across multiple data centers?
Answer:
- Yes, PSNs are often deployed at branch/DC sites for local authentication.
- Latency requirement: RADIUS/EAP must be <300 ms round trip.
- All PSNs sync policies from the PAN automatically.
Tip: Always use local PSNs in large campuses to reduce WAN latency.
6. How does ISE replication work between nodes?
Answer:
- PAN → PSNs & MnTs push replication.
- Config changes are done only on Primary PAN → auto-sync to other nodes.
- MnT log replication works in active/standby mode.
Validation:
- GUI: Administration > System > Deployment → Replication Status.
- CLI:
ise/admin# show replication status
7. What are the hardware/sizing guidelines for LSDD?
Answer:
- PAN: 16 vCPUs, 32 GB RAM, 600 GB disk (for >25k endpoints).
- PSN: 8–16 vCPUs, 32 GB RAM.
- MnT: 16 vCPUs, 64 GB RAM, 2 TB disk (for long-term log storage).
Reference: Cisco ISE Performance & Scale guide.
8. What’s the best way to monitor PSN load and session health?
Answer:
- GUI: Operations > Live Sessions → Per-PSN session view.
- CLI:
ise/psn# show sessions ise/psn# show radius statistics ise/psn# show application status ise
- Use SNMP/REST APIs for external monitoring tools (SolarWinds, Splunk, etc).
9. Can MnT nodes be deployed across data centers?
Answer:
- Yes, but ensure latency <300 ms.
- Logs replicate between active/standby.
- In large-scale, often one MnT per DC for local log redundancy.
Tip: Always integrate MnT with external syslog/SIEM for compliance.
10. What are the top failure scenarios to validate in LSDD labs?
Answer:
- Primary PAN failure → Secondary PAN promotion.
- PSN outage → Load balancer reroutes sessions.
- MnT failover → Verify logs continue in standby.
- WAN link failure → Local PSN handles authentication.
- Replication break → Policies not updating on remote PSNs.
CLI Tools:
ise/admin# show logging system ise/admin# show application status ise ise/psn# show radius statistics
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Large-Scale Deployment of Cisco ISE is about scalability, high availability, and distributed control.
- Separate roles (PAN, PSN, MnT) for efficiency.
- Use load balancing for PSNs.
- Always validate replication and session load via GUI + CLI.
By mastering LSDD, you’re operating at the CCIE-level of ISE expertise, capable of building carrier-grade NAC infrastructures.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led 4-month CCIE Security training.
Course outline: https://course.networkjourney.com/ccie-security/
Take the Fast-Track to Cisco ISE Mastery Pro and become the engineer that enterprises trust to run their global NAC deployments.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088


![[Day 32] Cisco ISE Mastery Training: Configuring Cisco AnyConnect NAM for Wired Auth](https://networkjourney.com/wp-content/uploads/2025/08/Day-32-–-Cisco-ISE-Mastery-Training-Configuring-Cisco-AnyConnect-NAM-for-Wired-Auth.png)
