[Day 106] Cisco ISE Mastery Training: Integrating Cisco DNA Center for SDA
Table of Contents
Introduction
Welcome to Day 106 of Cisco ISE Mastery Training, where we step into one of the most transformative areas of modern enterprise networking — the integration of Cisco Identity Services Engine (ISE) with Cisco DNA Center for Software-Defined Access (SDA).
Think of ISE as the brain for identity, policy, and access control and DNA Center as the controller and automation engine for SDA fabric. Separately, both are powerful. But when you integrate them, you unlock the full promise of zero trust networking: contextual access policies, identity-driven segmentation, automated provisioning, real-time visibility, and threat containment at scale.
Why does this matter?
Because in large enterprises today:
- Users are no longer fixed — they connect from offices, homes, and mobile devices.
- Workloads move dynamically between data centers, cloud, and edge locations.
- Security teams need policy consistency across every switch, WLC, and access layer.
The ISE + DNA Center integration ensures that the network fabric enforces security policies at wire speed, not just at the perimeter. It also enables macro-segmentation (VRFs, VNIs) and micro-segmentation (SGTs) with automation, so NAC is no longer just reactive — it becomes an adaptive, identity-driven, policy-based system.
This session is not just theory. We will go step-by-step, validate every stage with GUI and CLI outputs, and simulate real-world lab topologies that you can replicate on VMware/EVE-NG. By the end, you’ll not only understand the integration, but you’ll be ready to design, implement, and test it at enterprise scale.
Problem Statement
Enterprises face these practical problems when adopting SDA:
- Policy drift: DNAC and ISE configured separately — resulting in mismatched SGTs/SGACLs.
- Manual device config: Thousands of NADs (switches/WLC) require repeated AAA/RADIUS templates.
- Visibility gap: DNAC sees topology; ISE sees identity — but without integration you cannot correlate.
- Slow containment: Threats need fast quarantine (CoA/DACL) but lack orchestration.
We solve these by integrating DNAC↔ISE (pxGrid + ERS + APIs) so DNAC creates intent (SGTs, VNs), publishes to ISE, and ISE enforces identity and reports sessions back to DNAC for assurance/closed-loop actions.
Solution Overview
High level flow (what we implement):
- Enable pxGrid and ERS on ISE; ensure PKI trust (cert chains) between DNAC and ISE.
- Add ISE as an Authentication & Policy Server in DNAC (ERS credentials + pxGrid registration).
- Author SGTs & Group-Based Access Matrix in DNAC and Publish to ISE. (DNAC uses ERS/pxGrid.)
- DNAC provisions AAA templates to fabric devices (C9300/C9500, WLC) pointing to ISE VIP/PSNs.
- Validate enforcement at fabric edge (
show cts ...), on NAD (show authentication sessions), and in ISE Live Logs. - Test closed-loop: DNAC triggers quarantine (calls ISE/pxGrid) → ISE issues CoA → NAD enforces DACL/SGT.
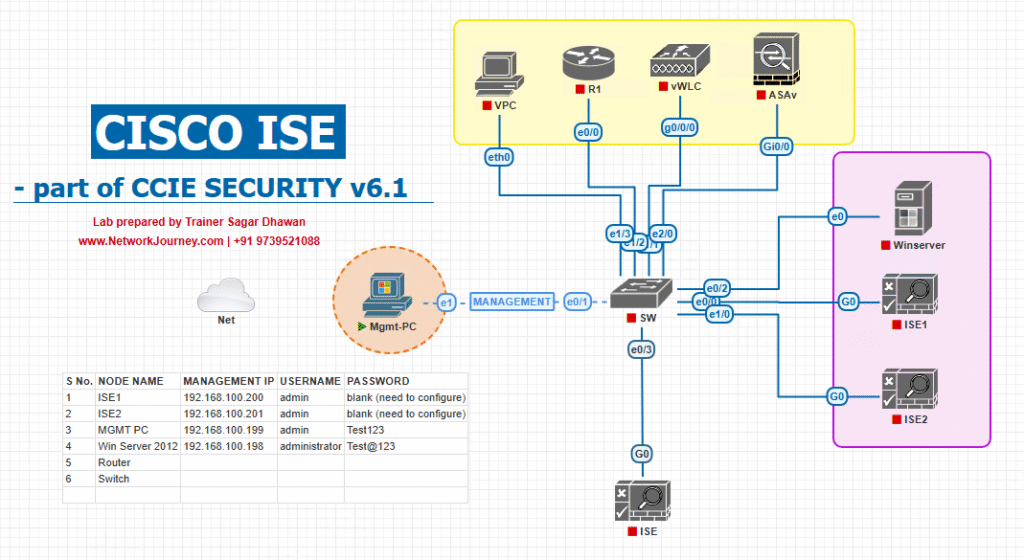
Sample Lab Topology (VMware/EVE-NG)
Lab VMs / Appliances
- DNAC appliance (single node)
- Cisco ISE cluster: PAN, MnT, PSN1, PSN2 (all reachable)
- WLC 9800-CL (virtual)
- Catalyst 9300 pair (edge) — SDA edge role in DNAC Fabric
- AD (Windows DC), Internal PKI (Active Directory Certificate Services), NTP, DNS
- Test endpoints: Windows 11 (dot1x EAP-TLS), iPhone (guest), IoT (MAB)
Topology diagram:
Step-by-Step GUI Configuration Guide
PREP: global prerequisites (do before Step 1)
- DNS entries for ISE PAN/PSN and DNAC resolvable both ways.
- NTP synchronized across DNAC, ISE, and devices (
chronyc/ntpstatverification). - PKI: export ISE CA certificate chain (root + intermediates) to a file.
- Create an ISE user for ERS (e.g.,
ersadmin) and a DNAC service account. - Decide RADIUS VIP (LB) or direct PSN IPs for AAA in DNAC templates.
Validation:
# From DNAC shell or a jump host nslookup <ise-pan-fqdn> ping -c3 <ise-pan-ip> ntpstat
[Screenshot: DNS & NTP checks]
STEP 1 — Prepare ISE: enable pxGrid, ERS, create ERS account, confirm certs
- GUI (ISE PAN)
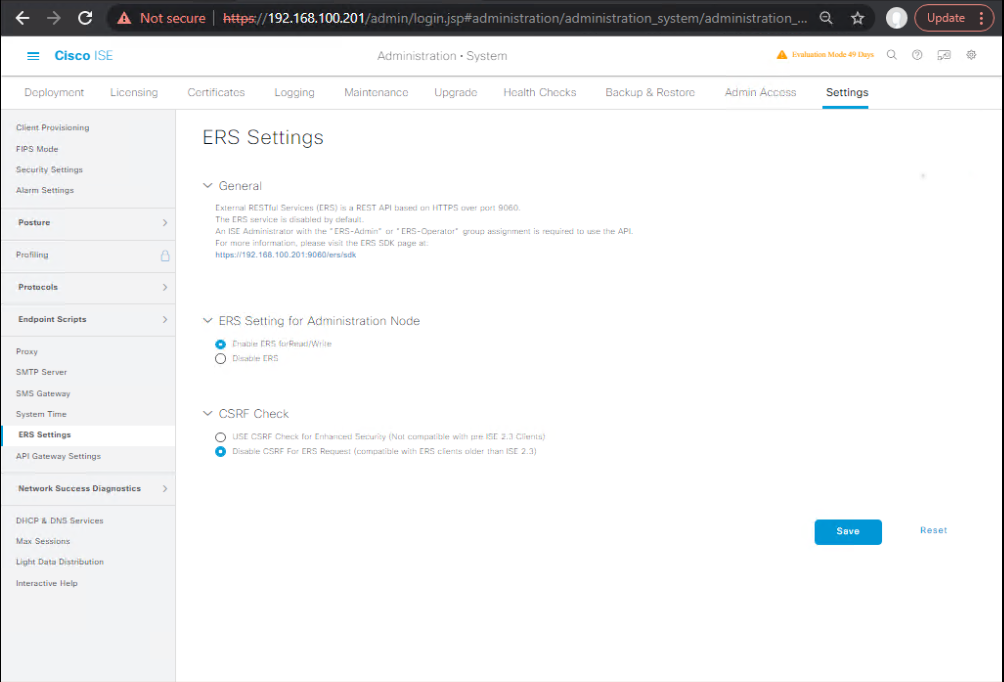
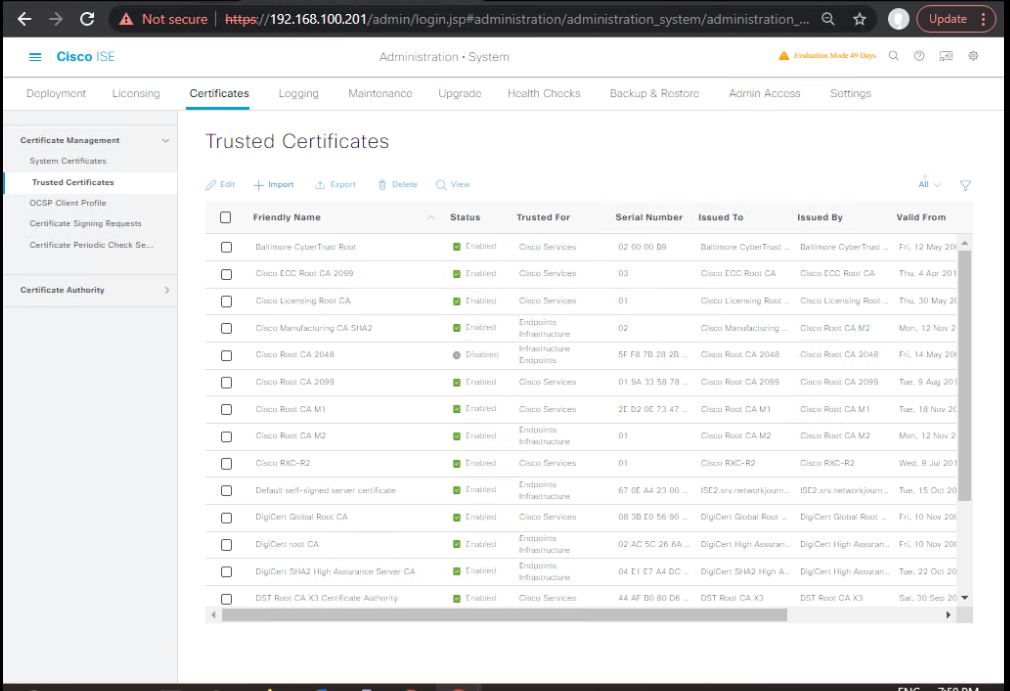
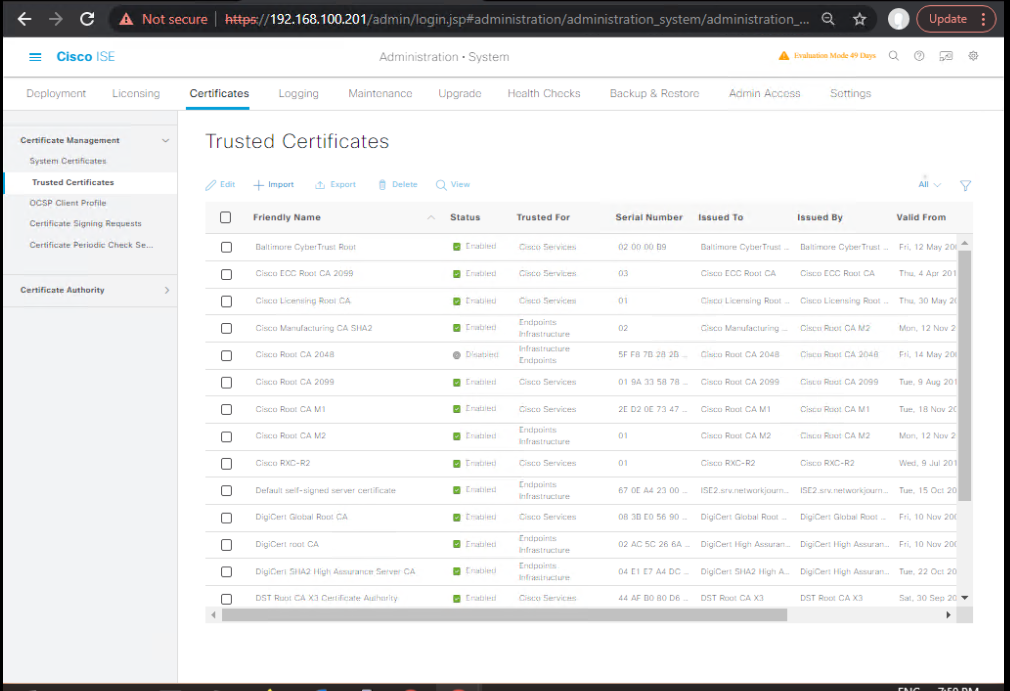
Administration → System → Settings → ERS Settings→ Enable ERS. Createersadminrole with permissions (ERS-Admin).Administration → System → Settings → pxGrid Services→ Enable pxGrid. Ensure pxGrid service is ON.Administration → System → Certificates → Trusted Certificates→ Import DNAC CA if DNAC uses its own CA. Ensure ISE has a valid node certificate for PXGRID (system certificate with correct FQDN SAN).- [Screenshot: ISE ERS Settings] [Screenshot: ISE pxGrid Services] [Screenshot: ISE System Certificates]
- Create ERS user (GUI)
Administration → System → Administrators → Add→ usernameersadmin→ RBAC: ERS Admin. Set a strong password. Save.
- CLI Validation (ISE PAN)
# ensure ISE processes are up show application status ise # check pxGrid/logging show logging application pxgrid.log tail 50 # check ERS listening netstat -an | include 9060
Expected: pxGrid service logs show no errors; ERS tcp port (9060) listening.
STEP 2 — Establish PKI trust (ISE ↔ DNAC)
- Export ISE CA chain (PAN GUI)
Administration → System → Certificates → Trusted Certificates → Export→ export root and intermediate as PEM(s). [Screenshot: Export CA]
- Import ISE CA into DNAC (DNAC GUI)
System → Settings → Security → Certificate Management→ Trusted Certificates → Upload ISE CA chain so DNAC trusts ISE. [Screenshot: DNAC Import CA]
- On DNAC, ensure DNAC also has a certificate trust chain that ISE will accept for pxGrid. If DNAC uses a private CA, import DNAC CA into ISE Trusted Certificates. [Screenshot: ISE Import DNAC CA]
- Validation (CLI)
# From DNAC or jump host openssl s_client -connect <ise-pan-fqdn>:8910 -showcerts </dev/null 2>/dev/null | openssl x509 -noout -subject -issuer -dates # verify expiry and issuer
Expected: Correct certificate chain; CN/SAN includes ISE PAN FQDN; openssl returns issuer including your ISE CA.
STEP 3 — Add ISE to DNAC (ERS + pxGrid registration)
- DNAC GUI:
System → Settings → Authentication and Policy Servers → Add→ select ISE.- Fill: ISE PAN IP/FQDN, ERS username (ersadmin) and password. Choose Enable pxGrid or Register via pxGrid option. (DNAC will attempt ERS login then pxGrid registration.)
- [Screenshot: DNAC Add ISE wizard]
- DNAC will: call ERS to create trust, and then initiate pxGrid client registration. Accept the pxGrid client in ISE (if manual approval is required).
- ISE GUI Validation:
Work Centers → pxGrid Services → Clients→ findCisco DNA Center→ Status Online/Allowed.Work Centers → pxGrid Services → Services→ ensure pxGrid services (Session Directory, Certificates, etc.) are listed.- [Screenshot: ISE pxGrid Clients list]
- CLI Validation (ISE PAN)
show logging application pxgrid.log tail 100 # look for DNAC registration events, client allowed/online messages
- DNAC Validation:
- DNAC should show
ISE Connectedin the Authentication Servers list. - Optionally test ERS API from DNAC shell:
# from DNAC appliance shell (or jump host with creds) curl -sk -u ersadmin:<password> https://<ise-pan-fqdn>:9060/ers/config/endpoint # expect XML/JSON or 200 response (maybe auth error if wrong creds)
Expected: successful ERS response; pxGrid client visible/online in ISE.
STEP 4 — Publish SGTs & Group-Based Access Control from DNAC to ISE
- DNAC GUI:
Policy → Group Based Access Control → Groups→ create groups (e.g.,Employees,Servers,IoT,Guest). [Screenshot: DNAC SGT Group Create]Policy → Group Based Access Control → Matrix→ create a policy matrix (Allow/Block/Trust with logging) mapping these groups. [Screenshot: DNAC Matrix]
- Publish: Click Publish or Push to ISE (DNAC will call ERS/pxGrid to create SGTs and SGACLs in ISE). [Screenshot: DNAC Publish]
- ISE GUI Validation:
Work Centers → TrustSec → Components → Security Groups→ created SGTs appear.Work Centers → TrustSec → Components → SGACLs→ SGACLs appear and are associated.- [Screenshot: ISE Security Groups / SGACLs]
- CLI Validation (ISE PAN / PSN)
# list SGTs show trustsec sgt # show SGACLs show trustsec sgacl # tail logs for ERS create events show logging application ise-trustsec.log tail 50
Expected: groups and ACL objects created; logs show ERS create events.
STEP 5 — Push AAA & Provision Fabric Devices from DNAC to Use ISE
- DNAC GUI:
Design → Network Settings → AAA→ add ISE as an AAA server (use VIP or PSN IPs). Set timeout=5–7s, retries=3. [Screenshot: DNAC AAA Settings]Provision → Devices → Select Fabric Edge(s)→ apply AAA template (DNAC will configureradius serverentries and AAA groups on switches/WLC). [Screenshot: DNAC Provisioning AAA]
- Validation (Edge Switch CLI):
# on Catalyst 9300 show run | section radius show run | section aaa show authentication sessions interface Gi1/0/10 details # after test auth show cts role-based permissions
- Validation (WLC CLI):
show radius summary show wlan id <ID> # verify AAA override/redirection configured for portal
- ISE Live Validation:
- Authenticate a test 802.1X client (Windows EAP-TLS). In ISE:
Operations → RADIUS → Live Logs→ confirm Authentication success, Policy Set, Assigned SGT. [Screenshot: ISE Live Logs EAP-TLS]
Expected: DNAC-pushed AAA is present on NADs; authentication uses ISE; SGT assigned per policy.
STEP 6 — Verify SGT enforcement on fabric edge & WLC
- On edge switch (CLI):
# check CTS / SGT mapping show cts role-based permissions show cts role-based counters show authentication sessions interface Gi1/0/10 details | include SGT|VLAN # for downloadable ACLs verify show ip access-lists dynamic
Validation: traffic matching policies should increment cts role-based counters.
- On WLC (for wireless SGT mapping):
show wireless client mac <mac> detail
Validation: wireless client shows ISE SGT or VLAN assigned via ISE.
- ISE Live Logs: confirm the node that handled auth, SGT value, and any authorization profile applied. [Screenshot: ISE Live Log with SGT]
STEP 7 — Closed-Loop Test: Quarantine a client from DNAC → ISE applies CoA
- From DNAC:
Assurance → Client 360→ select a client → Take action → Quarantine (or click ISE Quarantine). DNAC should call pxGrid/ERS to instruct ISE to apply quarantine. [Screenshot: DNAC Client 360 Quarantine] - ISE GUI Validation:
Operations → Live Logs→ see an authorization change for the client (QUARANTINE).Work Centers → Adaptive Network Control→ show recent ANC events. [Screenshot: ISE ANC event]
- Edge CLI Validation:
show authentication sessions interface Gi1/0/10 details | include DACL|SGT|Status show ip access-lists dynamic # verify DACL applied show cts role-based counters # check counter hit for quarantine rule
- CoA verification (on NAD):
- Check NAD logs for CoA or reauthorization events.
Expected: client moved to quarantine DACL/SGT; connectivity restricted.
STEP 8 — Assurance & Evidence collection
- DNAC Assurance: capture
Client 360screenshot showing ISE session details (SGT, endpoint identity, health). [Screenshot: DNAC Client 360 with ISE details] - ISE Reports:
Operations → Reports → RADIUS Authenticationexport PDF/CSV.
[Screenshot: ISE Report Export]
- Collect CLI outputs:
# ISE show application status ise show logging application pxgrid.log tail 100 show logging application ise-psc.log tail 50 # Edge show cts role-based permissions show cts role-based counters # NADs show radius statistics
Expert-Level Use Cases (consultant / SRE patterns)
- Automated Threat Containment: DNAC integrates with ISE + SIEM. SIEM alerts → DNAC triggers ISE quarantine via pxGrid → firmware/patch orchestration kicks off.
- Multi-tenant provisioning: DNAC templates create segmented VN + SGT per tenant; ISE enforces per-tenant SGACLs.
- CI/CD for Policy: GitOps pipeline posts policy changes to DNAC, which pushes SGTs to ISE and triggers verification tests.
- Edge Micro-segmentation: Use SGTs for east-west controls; firewalls import SGT mapping via ISE for L7 enforcement.
- IoT Zero-Trust: Auto-profile IoT in ISE → assign IoT-SGT → DNAC maps IoT VN + SGACL to block lateral movement.
- Hot DR for Fabric: pre-stage PSN images and DNAC device templates in cloud to spin up temporary PSNs during DC outage.
- Assurance-Driven Tuning: DNAC monitors auth failure spikes; auto-adjust RADIUS timeouts and re-provision templates to NADs.
- Blue/Green Portal Rollout: Deploy new portal certs on separate pool; DNAC orchestrates cutover with no client warnings via SAN overlap.
- PxGrid Multi-Consumer Model: multiple consumers (CASB, EDR) subscribe to ISE session directory for richer telemetry and automated response.
- SGT Federation (multi-DC): DNAC federates SGT taxonomy; ISE enforces consistent SGTs across global sites with GSLB for portal continuity.
Quick CLI validation block
ISE (PAN/PSN):
show application status ise show logging application pxgrid.log tail 100 show logging application ise-psc.log tail 50 show trustsec sgt show trustsec sgacl
DNAC (jump host to test ERS/pxGrid endpoints):
curl -k -u ersadmin:<pwd> https://<ise-pan-fqdn>:9060/ers/config/endpoint openssl s_client -connect <ise-pan-fqdn>:8910 -showcerts
Edge Switch (C9300):
show run | section radius show authentication sessions interface Gi1/0/10 details show cts role-based permissions show cts role-based counters
WLC 9800:
show radius summary show wireless client mac <mac>
FAQs – Cisco ISE + DNA Center SDA Integration
1. What roles do Cisco ISE and DNA Center play in an SDA deployment?
Answer:
- Cisco ISE → Provides identity-based authentication/authorization, policy enforcement, and SGT mapping.
- DNA Center → Orchestrates SDA fabric, assigns VNIs, VRFs, and configures fabric edge, control, and border nodes.
Validation:
- In DNA Center GUI → Navigate to Design > Network Settings > AAA and check ISE integration.
- In ISE GUI → Go to Work Centers > TrustSec > Components > SGTs and confirm mapping synced from DNA Center.
2. Which protocols are used for communication between Cisco ISE and DNA Center?
Answer:
- RADIUS → Authentication & authorization.
- pxGrid → Policy, context, and SGT exchange.
- REST APIs → DNA Center uses ISE APIs for pulling identity data.
Validation (CLI on ISE):
ise/admin# show application status ise ise/admin# show logging application pxgrid.log
Look for pxGrid registration from DNA Center.
3. How do I integrate ISE with DNA Center in the GUI?
Answer:
- In DNA Center GUI →
System > Settings > Authentication and Policy Servers→ Add ISE. - Provide ISE FQDN, pxGrid credentials, RADIUS key.
- Test connectivity.
- Approve DNA Center client request in ISE GUI > Administration > pxGrid Services.
Validation:
- DNA Center GUI: Green status next to ISE.
- ISE GUI: DNA Center shows under pxGrid Clients.
4. How do I validate that SGTs from ISE are available in DNA Center?
Answer:
- In DNA Center GUI → Go to Policy > Group-Based Access Control (GBAC).
- Confirm SGTs are imported from ISE.
CLI Validation (Edge Node Switch):
show cts role-based permissions show cts role-based sgt-map
5. What happens if DNA Center loses connection to ISE?
Answer:
- Authentication still works if NADs (switches/WLCs) point directly to ISE.
- Policy updates/SGT mappings won’t sync to DNA Center until the connection is restored.
Validation:
- Disconnect ISE temporarily → verify existing sessions continue but new group policies fail in DNA GUI Policy dashboard.
6. How are endpoint identities handled between DNA Center and ISE?
Answer:
- DNA Center does device discovery + fabric onboarding.
- ISE provides endpoint identity & posture context.
- DNA Center imports endpoint groups from ISE via pxGrid.
ISE GUI Validation:
Check Context Visibility > Endpoints → endpoints tagged with SGTs.
DNA GUI Validation:
Check Assurance > Client 360 → endpoint context matches ISE.
7. How do I apply micro-segmentation using ISE + DNA Center?
Answer:
- Create SGTs in ISE.
- Sync them to DNA Center.
- In DNA Center GUI > Policy > Group-Based Access Control, define Contract rules (Permit/Deny).
- DNA pushes to fabric edge switches as CTS policies.
CLI Validation (Switch):
show cts role-based permissions show cts role-based counters
8. How can I test if SDA + ISE integration is working?
Answer:
- Connect a test endpoint.
- Check ISE Live Logs → endpoint authenticated and assigned SGT.
- Check DNA Center Assurance → endpoint is visible in fabric with correct policy.
- Test micro-segmentation: e.g., try ping between two endpoints with different SGTs and verify block/allow.
9. What’s the difference between macro-segmentation and micro-segmentation in SDA with ISE?
Answer:
- Macro-segmentation → Fabric VN/VRF separation (e.g., IoT vs. Corporate).
- Micro-segmentation → SGT-based access control within the same VRF.
Validation:
- Macro: Verify VRF assignments in DNA GUI > Fabric > Host Onboarding.
- Micro: Verify
show cts role-based permissionson edge switches.
10. What are common troubleshooting steps if integration fails?
Answer:
- Check time sync (NTP) → mismatched clock breaks pxGrid.
- Ensure CA-signed certificates are used for pxGrid/REST integration.
- Verify ISE pxGrid services are running:
ise/admin# show application status ise | include pxgrid
- Check ISE logs (Operations > pxGrid Services) for DNA registration failures.
- In DNA Center, re-run ISE Connectivity Test.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes — key takeaways
- Trust first: PKI & DNS are the most common failure points — validate cert chains and SANs before ERS/pxGrid.
- DNAC as intent source: author SGTs & matrix in DNAC, publish to ISE — don’t edit the same objects in two places.
- Evidence every step: always capture ISE Live Logs, DNAC Client 360,
show ctscounters, NADshow radius statistics. - Test closed-loop: quarantine via DNAC → ISE CoA enforcement — that proves the integration end-to-end.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro
- I run a focused 4 months instructor-led CCIE Security track covering SDA + ISE, pxGrid, multi-DC, HA/DR, TrustSec, and runbook labs.
- Course & enrollment: https://course.networkjourney.com/ccie-security/
- Book readiness call → get SDA-ISE Runbook Pack (templates + CLI snippets) → reserve seat.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



