[Day 107] Cisco ISE Mastery Training: SDA Fabric Authentication
Table of Contents
Introduction
In the modern enterprise, networks are no longer static — they’re dynamic, software-defined, and built to handle mobile workforces, IoT, cloud integrations, and zero-trust requirements. Traditional VLAN-based segmentation, ACLs, and static security policies simply cannot keep up with the velocity of business change. This is where Cisco Software-Defined Access (SDA) combined with Cisco Identity Services Engine (ISE) becomes the gold standard for identity-driven networking.
At the heart of SDA is fabric authentication, a process where endpoints are not just connected to the network but are dynamically authenticated, profiled, and assigned context-aware access policies through ISE. Instead of managing VLANs, ACLs, and IP mappings manually, SDA + ISE allows you to deliver identity-based, policy-driven access consistently across wired, wireless, and remote users.
This is not just about “logging into the network” — it’s about enabling:
- Seamless user and device onboarding (wired, wireless, IoT, BYOD, guest).
- Dynamic segmentation through Scalable Group Tags (SGTs) — eliminating VLAN sprawl.
- End-to-end visibility and control across the SDA fabric.
- Zero Trust enforcement by binding authentication, authorization, and segmentation tightly together.
In this masterclass, we will go step-by-step through how Cisco ISE integrates with SDA for fabric authentication, validate configurations using both GUI and CLI, simulate real-world scenarios in the lab, and even perform troubleshooting checks to ensure reliability.
By the end of this session, you’ll not only understand the theory and architecture but will also have a hands-on workbook guide for deploying SDA Fabric Authentication with ISE — a skill highly demanded in enterprise and CCIE Security expert-level environments.
Problem Statement
Enterprise fabrics fail authentication requirements for several practical reasons:
- NADs (edge switches / WLC) are mis-configured for AAA templates or RADIUS timeouts → frequent auth failures.
- ISE and fabric are not synchronized (SGT taxonomy mismatch) → SGTs not enforced at edge.
- CoA / ANC not tested → quarantines or posture actions don’t apply.
- Lack of repeatable validation → teams “hope” auth works but cannot prove it under audit.
Objective: build a repeatable process that ensures wired/wireless devices authenticate via ISE through the SDA fabric, SGTs are assigned, policies are enforced, and CoA/quarantine works — validated via GUI + CLI and packaged for audit.
Solution Overview
We implement and validate:
- AAA templates from DNAC (or manually) on fabric devices to point to ISE (VIP or PSNs).
- ISE Policy Sets for EAP/TLS, PEAP, MAB and mapping to SGTs.
- SGT distribution to fabric via CTS (ISE + DNAC publish).
- Edge enforcement (CTS role-based permissions, downloadable ACLs or DACLs).
- Closed-loop controls: CoA / ANC to change session state and see edge apply DACL/SGT.
- A stepwise validation matrix with CLI commands and expected outputs.
You will test wired 802.1X (EAP-TLS), wireless (802.1X & CWA), and MAB (IoT).
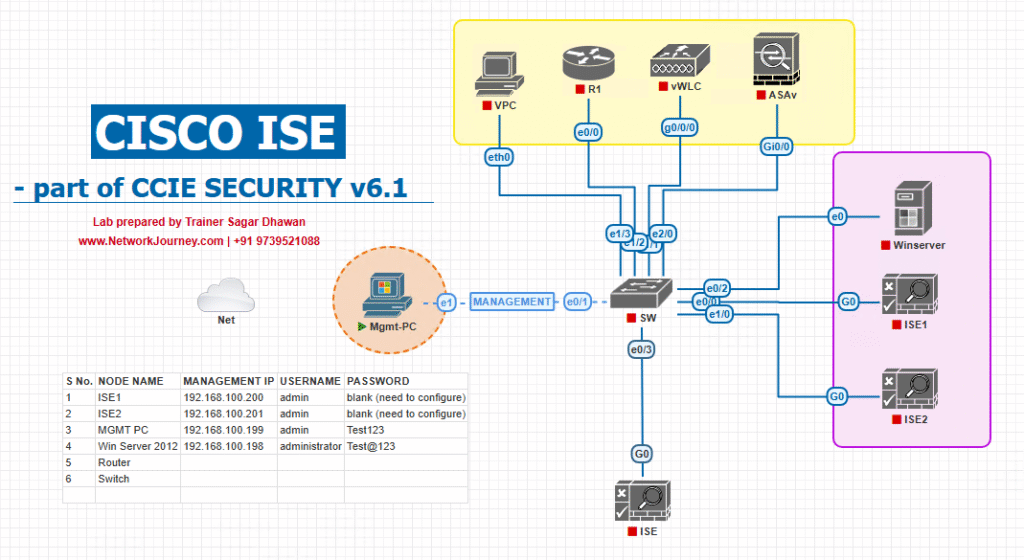
Sample Lab Topology (VMware / EVE-NG)
Virtual appliances / VMs
- Cisco ISE: PAN, MnT, PSN1, PSN2 (VMs)
- Cisco DNA Center (optional): for automation & AAA push
- WLC 9800-CL (virtual)
- Catalyst 9300 pair as fabric edge (SDA edge) + Catalyst 9500 fabric border (or EVE NG equivalents)
- AD (Domain Controller), PKI (ADCS), NTP, DNS
- Client VMs: Win11 (EAP-TLS client), Linux IoT simulator (MAB), iPhone for Guest
Logical diagram:
Lab notes
- Use VIP (LB) or list PSN IPs in AAA server groups on NADs.
- Ensure NTP and DNS consistent across all devices.
- Ensure EAP certs (client cert + ISE server cert and CA chain) are present.
Step-by-Step GUI Configuration Guide (numbered + validation)
PRECHECK: environment readiness (run before any change)
- Verify DNS & NTP from each device and ISE.
# On a jump host or ISE nslookup ise-pan.corp ping -c3 ise-pan.corp ssh admin@edge-switch show clock show ntp status - Check ISE services:
# on ISE (any node) show application status ise show running-config ise | include pxgridExpected: ISE servicesrunning.
STEP 1 — Configure AAA on Fabric Edge (Catalyst 9300) and WLC
Goal: Point the fabric to ISE (VIP or PSNs) and set RADIUS timeout/retries.
A. Catalyst 9300 (manual)
- CLI:
configure terminal aaa new-model radius server ISE-VIP address ipv4 10.10.10.100 auth-port 1812 acct-port 1813 key MyRadKey aaa group server radius ISE-GRP server name ISE-VIP ! radius-server vsa send accounting radius-server attribute 8 include-in-access-req # Framed-IP if needed aaa authentication dot1x default group ISE-GRP aaa authorization network default group ISE-GRP aaa accounting dot1x default start-stop group ISE-GRP radius-server timeout 5 radius-server retransmit 3
- Save config:
write memory.
Validation (Edge CLI):
show run | section radius show authentication sessions interface Gi1/0/10 details show radius statistics
Expected: radius server present; no interface auth yet until client connects.
B. WLC 9800 (verify AAA template)
- On WLC / DNAC provisioned: ensure RADIUS server entries include ISE VIPs.
show radius summary
Expected: RADIUS server reachable and active.
STEP 2 — ISE Policy Set: EAP, MAB, Authorization profile → SGT assignment
Goal: Configure policy for wired/wireless authentication and SGT assignment.
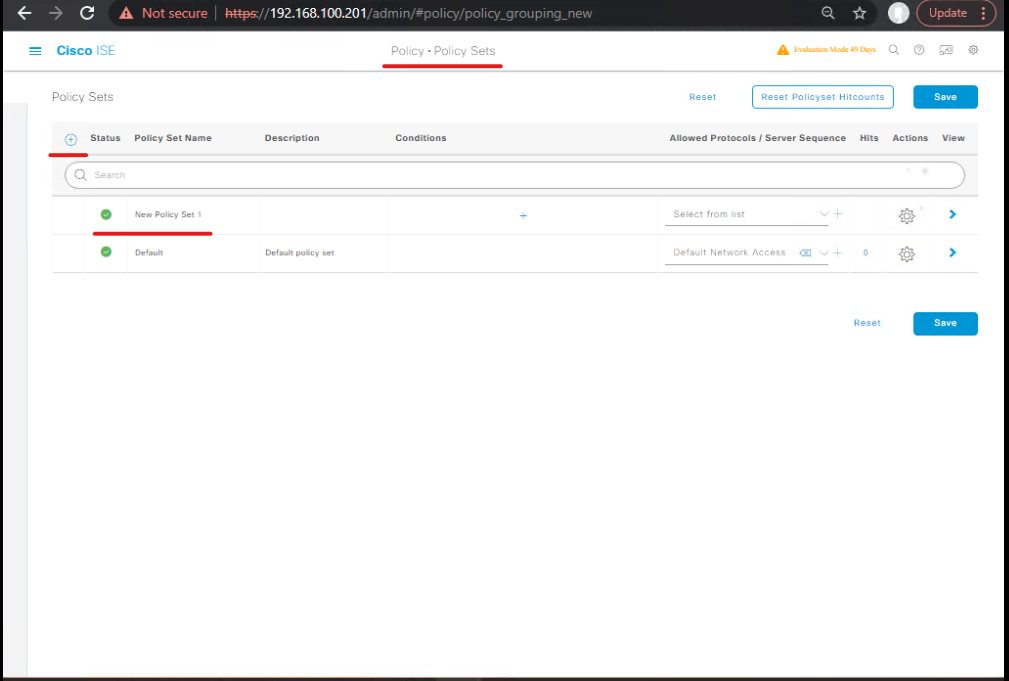
ISE GUI steps (PAN):
Policy > Policy Sets→ create or edit a policy set for your lab (e.g., “SDA-Fabric-Policy”).- Conditions: NAD IP (Network Device Group or device list) or identity store.
- Authentication Policy Nodes: Add Auth methods in order:
- EAP-TLS (for certificates)
- PEAP/MSCHAPv2 (optional)
- MAB (fallback)
- Authentication Profiles: Ensure EAP-TLS is correctly bound and server cert is present.
- Authorization Rules:
- Rule: EAP-TLS → Authorization Profile
Corp-Access→ assign SGT = Employees. - Rule: MAB → Authorization Profile
IoT→ assign SGT = IoT.
- Rule: EAP-TLS → Authorization Profile
ISE CLI validation:
# show policy mapping show running-config ise | include Policy # verify last auth events tail show logging application ise-radius.log tail 20
Expected: Authorization profiles include sgt attribute, or show SGT in GUI mapping.
STEP 3 — Verify SGT distribution to Fabric (CTS / DACL)
Goal: Ensure SGTs pushed to fabric and role-based permissions (RBAC) exist.
ISE GUI:
Work Centers > TrustSec > Components > Security Groups→ Confirm SGTs exist.Work Centers > TrustSec > Components > Policies→ Confirm SGACLs present.
Edge CLI (C9300):
show cts environment-data show cts role-based permissions show cts role-based counters
Expected: role-based permissions list matrix entries; counters typically zero until traffic generated.
STEP 4 — Client Onboarding & Test Auth (Wired EAP-TLS)
Goal: Authenticate a wired Windows 11 client using EAP-TLS and verify SGT assignment and edge enforcement.
Client prep:
- Install client certificate from enterprise PKI and ensure client trusts ISE root CA.
Procedure:
- Connect Win11 to access port configured for 802.1X.
- Initiate authentication.
Edge CLI validation:
show authentication sessions interface Gi1/0/10 details # expected fields: Method = EAP, Status = Authenticated, Authentication Server = ISE-VIP
ISE GUI validation:
Operations > RADIUS > Live Logs→ filter by client MAC or IP → show Authentication success, Authorization Profile, SGT assigned.
Edge enforcement check:
show cts role-based counters # see counters increment show ip access-lists dynamic # verify DACL if applied
Expected: counters increase; ACL applied (if downloadable ACLs used).
STEP 5 — Wireless Authentication (802.1X + CWA) via WLC
Goal: Validate wireless EAP & CWA flows with SGT mapping.
WLC steps (verify):
- Confirm SSID configured for 802.1X (or for Guest CWA) and AAA points to ISE VIP.
show wlan id <wlan-id> show wireless client mac <client-mac>
Test:
- Connect client to SSID; perform authentication or CWA portal flow.
ISE validation:
- Live Logs show wireless auth, show assigned SGT and NAD (WLC).
Edge/WLC enforcement:
# On WLC: show client detail <mac> # On fabric edge: show cts role-based counters
Expected: SGT on client session visible; counters increment.
STEP 6 — MAB (IoT) Test & Auto SGT assignment via Profiling
Goal: Demonstrate MAB fallback for non-802.1X devices (IoT) and auto-assign SGT via ISE profiling/endpoint identity groups.
Procedure:
- Configure switch port for MAB fallback on failed 802.1X.
- Connect IoT simulator (Linux VM) with MAC only.
Edge CLI:
show authentication sessions interface Gi1/0/11 details show radius statistics
ISE GUI:
Operations > RADIUS > Live Logs→ MAB auth show Accept, Authorization profile = IoT → SGT assigned.Operations > Identity > Endpoints→ Endpoint group shows assigned SGT.
Validation: Endpoint appears in ISE with SGT; edge counters show enforcement hits.
STEP 7 — CoA / ANC (Quarantine) Test — closed loop enforcement
Goal: Verify that ISE (or DNAC) can quarantine a client and that CoA is applied by the fabric.
Trigger flow (manual):
- In ISE GUI:
Operations > Adaptive Network Control→ create an ANC action for the chosen endpoint (e.g., apply DACL Quarantine). - Execute action on the endpoint.
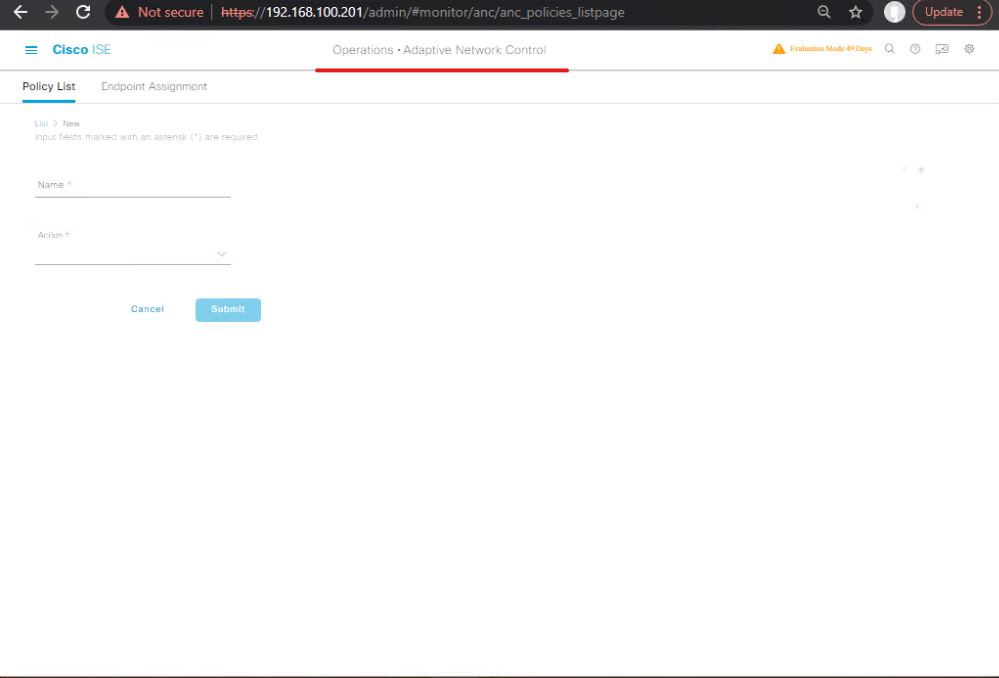
Validation (ISE GUI):
Live Logsshows Authorization change and CoA sent to NAD.
Edge CLI:
show authentication sessions interface Gi1/0/10 details | include DACL|Status|Reauth show ip access-lists dynamic
NAD logs should show incoming CoA request and application of DACL.
Expected: client access restricted/blocked per quarantine rule.
STEP 8 — Evidence Collection & Acceptance Criteria
For each test capture:
- Edge CLI output files:
edge_auth_<ts>.txt(outputs ofshow authentication sessions,show cts role-based counters) - WLC outputs for wireless tests:
wlc_client_<ts>.txt - List of steps executed and pass/fail per test case.
Acceptance criteria (must all be PASS):
- Wired EAP-TLS: client authenticated, SGT assigned, enforcement applied.
- Wireless 802.1X: auth passes, SGT assigned.
- MAB: IoT authenticated via MAB, SGT assigned.
- CoA / ANC: quarantine action results in DACL being applied by NAD.
- No unexpected authentication failures during tests.
Evidence Pack Template (CSV columns)
TestCase,Node,Action,ExpectedResult,ActualResult,GUI,CLI Output File,Pass/Fail,Notes
Use it to deliver audit-ready output.
Expert Level Use Cases (practical patterns)
- Zero-Trust IoT Onboarding: Automate MAB + profiling to assign IoT SGTs and put devices into segmented VN with limited East/West via SGACLs.
- Blue/Green SGT Rollout: Stage new SGT taxonomy in lab VN, publish to ISE, then switch fabric edges via DNAC orchestration — no user impact.
- Assurance-Driven Timeout Tuning: Use DNAC Assurance metrics (auth latency spikes) to auto-adjust RADIUS timeouts via templates.
- Scale Test Harness: Orchestrate containerized
radtestworkload to validate PSN capacity and LB behavior pre-cutover. - Automated Incident Containment: EDR raises alert → SIEM triggers DNAC/ISE quarantine playbook → CoA blocks host via DACL and triggers remediation ticket.
- Multi-Site CoA Matrix: Maintain ACLs to allow CoA from PSN subnets in every site; nightly synthetic CoA verification for each NAD.
- Guest Portal High Availability: Deploy global portal FQDN with GSLB to nearest portal VIP; ensure SAN includes GSLB names.
- Endpoint Lifecycle Automation: New employee provisioning pipeline automatically issues client cert, ISE endpoint record, assigns SGT, and DNAC applies network access via AAA templates.
- Split Fabric Enforcement: Offload micro-segmentation enforcement to next-gen firewalls using ISE SGT-to-FW mapping for complex L7 policies.
- DR Playbook: Cold-standby PSNs in cloud to handle auth during primary DC outage; DNS swing + LB cutover + evidence script to validate.
FAQs – SDA Fabric Authentication with Cisco ISE
1. What is the role of Cisco ISE in SDA fabric authentication?
ISE acts as the policy decision point (PDP) in the SDA fabric. It authenticates endpoints (wired, wireless, IoT, guest), profiles devices, and assigns Scalable Group Tags (SGTs) or authorization policies. These policies are then enforced by the fabric edge nodes (switches/WLCs) acting as policy enforcement points (PEPs). Without ISE, SDA cannot provide identity-driven access.
2. Which authentication methods are supported in SDA fabric with ISE?
SDA supports:
- 802.1X (EAP-based authentication) → for secure enterprise endpoints.
- MAB (MAC Authentication Bypass) → for IoT devices without supplicant.
- Guest Authentication → via web-portal redirect.
- Device profiling → using RADIUS attributes, DHCP probes, HTTP, etc.
ISE can enforce multi-auth policies on a single fabric edge port (e.g., phone + PC behind it).
3. How do Scalable Group Tags (SGTs) get assigned in SDA fabric authentication?
SGTs can be:
- Dynamically assigned by ISE during authentication (based on user/device policy).
- Manually mapped to IP or MAC in ISE or DNA Center.
- Propagated across the fabric via Cisco TrustSec/SGACLs.
This eliminates the need for VLAN sprawl, since SGT-based segmentation is identity-driven, not IP-driven.
4. What happens if Cisco ISE is unreachable during fabric authentication?
- If ISE is down and critical authentication is configured on the edge, endpoints may be placed in a critical VLAN or denied access depending on policy.
- SDA fabric relies heavily on ISE availability → hence redundant ISE nodes (PAN/MnT/PSN) are recommended.
CLI validation:
show authentication sessions show cts environment-data
5. Can I integrate Active Directory (AD) with SDA fabric authentication?
Yes. ISE integrates with AD for user identity lookups. When a user authenticates through SDA fabric (802.1X, MAB, guest), ISE queries AD to validate credentials and applies policy sets.
Validation: [ISE External Identity Sources – Active Directory]
6. How do I troubleshoot failed SDA fabric authentications?
Key tools:
- On ISE: Operations > RADIUS Live Logs → see success/failure reasons.
- On CLI (fabric edge switch):
show authentication sessions interface GigabitEthernet1/0/1 show cts role-based sgt-map show access-session details
- DNA Center Assurance → gives endpoint onboarding journey visualization.
7. What is the difference between VLAN assignment and SGT assignment in SDA?
- VLAN Assignment → legacy method, endpoint placed in VLAN X based on ISE authorization.
- SGT Assignment → modern SDA method, endpoint can be in the same VLAN as others but segmentation is enforced by SGTs & SGACLs, not VLANs.
This provides microsegmentation at scale.
8. Do wireless clients in SDA fabric authenticate differently from wired clients?
- Wired: Authentication happens at the fabric edge switch.
- Wireless: Authentication happens at the fabric WLC.
Both forward RADIUS requests to ISE, which applies identity-based policies.
Verification:
show wireless client mac <mac-address> detail
9. How does posture assessment work in SDA fabric authentication?
Posture assessment is supported when ISE + AnyConnect (with posture module) are integrated. After authentication, ISE checks the endpoint posture (AV, firewall, patch compliance). Non-compliant endpoints can be assigned to quarantine SGTs for remediation before full access.
10. What licenses are required for SDA fabric authentication with ISE?
- Cisco ISE: Base + Plus (for TrustSec/SGTs) or Advantage license.
- Cisco DNA Center: DNA Advantage license on switches/WLCs.
Without the right licensing, SGT-based policy enforcement won’t work.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes — key takeaways
- Trust & timing: NTP + PKI + DNS are prerequisites — failures here cause the majority of issues.
- Template & automation: Use DNAC to push AAA templates to edges where possible to avoid config drift.
- Validate every hop: client → switch/WLC → ISE → CoA → NAD. Save GUI + CLI evidence.
- Runbooks: Run test matrix regularly: EAP wired, wireless, MAB, CoA. Keep results for audits.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro
I run a focused 4-month instructor-led course covering CCIE Security topics including SDA + ISE, pxGrid, multi-DC, HA/DR, TrustSec, and lab runbooks.
See course outline & enroll: https://course.networkjourney.com/ccie-security/ — book a readiness call and request the SDA Fabric Authentication Runbook Pack.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 107] Cisco ISE Mastery Training: SDA Fabric Authentication](https://networkjourney.com/wp-content/uploads/2025/08/Day-107-–-Cisco-ISE-Mastery-Training-SDA-Fabric-Authentication.png)
![[Day 16] Cisco ISE Mastery Training: Understanding 802.1X Authentication Flow](https://networkjourney.com/wp-content/uploads/2025/08/Day-16-–-Cisco-ISE-Mastery-Training-Understanding-802.1X-Authentication-Flow.png)

