[Day 108] Cisco ISE Mastery Training: SGT-Based Access Control in SD-Access
Table of Contents
Introduction
In today’s enterprise networks, the battle for security and agility is being fought not at the perimeter, but inside the network fabric itself. With the explosion of IoT devices, mobile endpoints, contractors, and cloud-connected applications, traditional IP-based segmentation is no longer enough. Static VLANs and ACLs are rigid, complex to manage, and error-prone at scale.
This is where Cisco ISE’s Security Group Tags (SGTs) combined with Software-Defined Access (SD-Access) delivers a next-generation policy framework. Instead of binding access rules to IP addresses or VLANs, SGTs allow policies to follow the identity of the user or device — dynamically, across the entire fabric.
Think of SGTs as digital labels (like VIP, Guest, IoT, HR, Finance) that move with the traffic, no matter where the device connects — wired, wireless, or VPN. When combined with ISE + DNA Center, these tags are automatically assigned and enforced throughout the SDA fabric using SGACLs (Security Group Access Control Lists).
For a network security engineer, SGT-based access control is a game-changer because:
- It provides micro-segmentation without redesigning IP addressing.
- It scales seamlessly across multi-campus and multi-DC environments.
- It reduces ACL sprawl and simplifies compliance reporting.
- It enables a true zero-trust model inside the LAN/WLAN.
In this Article, we won’t just talk about SGTs — we’ll design, configure, validate, and test them step by step using both GUI (ISE + DNA Center) and CLI (Switches/WLCs). By the end of this session, you’ll be confident in building SGT-based policies inside an SD-Access fabric, validating them with real traffic, and troubleshooting like an expert.
Problem Statement (Real-world issue solved)
Enterprises struggle with:
- VLAN sprawl and brittle ACLs when scaling segmentation.
- Manual policy drift across hundreds of switches and WLCs.
- Slow containment for compromised devices.
- Lack of a single authoritative identity-to-policy pipeline.
SGT-based control solves these by centralizing identity and policy in ISE, authoring in DNAC (optionally), and enforcing on fabric edges so policy is consistent, auditable, and rapid to change.
Solution Overview (How ISE addresses it)
- ISE: authenticates users/devices, profiles endpoints, assigns SGTs, publishes SGTs & SGACLs via ERS/pxGrid (if DNAC used) and propagates to network via CTS.
- Fabric Edges (C9300/C9500/WLC): enforce SGACLs (downloadable ACLs or hardware tag enforcement).
- DNAC: creates SGT taxonomy, matrix, and pushes to ISE; provisions AAA templates and ensures consistent deployment.
- Result: Identity -> SGT -> SGACL applied -> enforcement at wire speed; CoA/ANC for remediation.
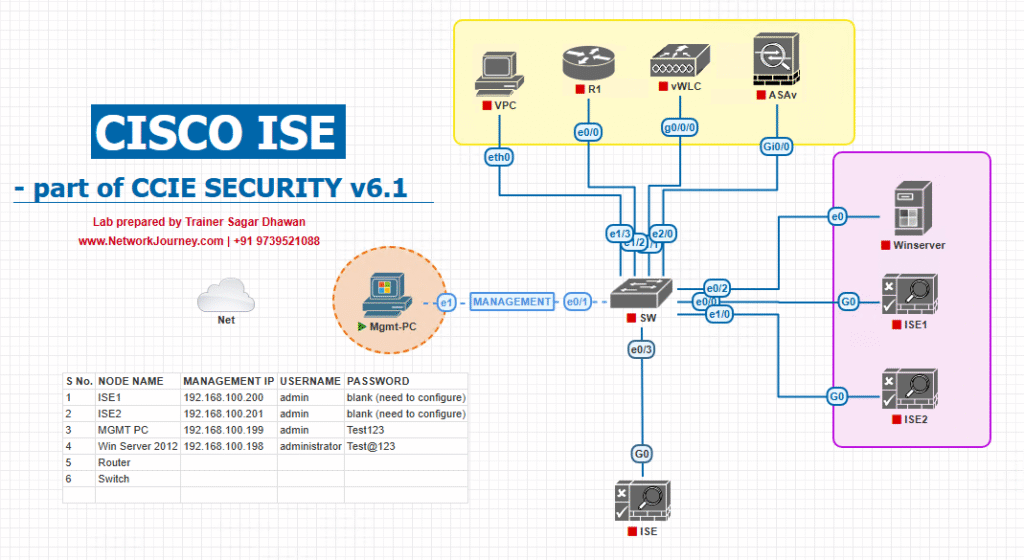
Sample Lab Topology (VMware/EVE-NG + devices)
Components (lab VMs & devices):
- Cisco ISE cluster (PAN, MnT, PSN1, PSN2) — VMware
- Cisco DNA Center (optional) — VMware
- Fabric: Catalyst 9500 (border), Catalyst 9300 pair (edge) — IOS-XE
- WLC 9800-CL (wireless)
- AD / PKI / NTP / DNS (Windows VM)
- Test endpoints: Windows 11 (EAP-TLS), Linux IoT (MAB), iPhone (Guest)
- LB VIP for ISE PSNs (optional)
Topology diagram:
Lab notes:
- Use DNAC to provision AAA, SGTs, and SGACLs where possible.
- If DNAC isn’t used, create SGTs and SGACLs directly in ISE and configure CTS on switches.
Step-by-Step GUI Configuration Guide (Numbered; GUI placeholders & CLI validation)
PRE-CHECKS (must pass before changes)
- NTP: verify all nodes have correct time (±1s).
# on ISE / DNAC / jump host ntpstat OR chronyc sources - DNS: forward/reverse resolution for all FQDNs.
nslookup ise-pan.corp nslookup dnac.corp - ISE basics:
# on ISE show application status ise show versionExpected: services running; correct version. - Edge device connectivity: SSH to C9300, run
show clock,show ntp status.
PHASE A — Create SGT Taxonomy (ISE or DNAC)
Option A: Create in DNAC (recommended)
- DNAC GUI:
Policy → Group-Based Access Control → Groups→ Create groups:Employees,Servers,IoT,Guest,Quarantine. - DNAC:
Policy → Group-Based Access Control → Matrix→ build allow/deny rules (Employees→Servers: Allow; IoT→Servers: Deny; Guest→Internet-only). - Publish to ISE (Push/Publish button).
Validation (ISE GUI):
Work Centers → TrustSec → Components → Security Groups→ verify groups exist.
CLI (ISE):
# on PAN show trustsec sgt show trustsec sgacl
Expected: SGT IDs + names; SGACL objects visible.
PHASE B — Create SGACLs in ISE (if DNAC not used)
- ISE GUI:
Work Centers → TrustSec → Components → SGACLs → Add- Create a SGACL that allows Employees→Servers (permit) and blocks IoT→Servers.
- Create a SGACL that allows Employees→Servers (permit) and blocks IoT→Servers.
- Map SGACL to policy enforcement (name it e.g.,
SGACL-V1).
CLI Validate:
show trustsec sgacl
PHASE C — Configure Authorization Profiles to Assign SGTs
- ISE GUI:
Policy → Policy Sets → <policy> → Authorization- Add Authorization Profile
Employees-Authz: Set SGT = Employees, DACL if required. - Add
IoT-Authz: Set SGT = IoT. - Add
Quarantine-Authz: SGT=Quarantine + DACL Quarantine.
- Add Authorization Profile
CLI Verify:
# show config for authz show running-config ise | include Authorization # tail recent auth logs show logging application ise-radius.log tail 50
PHASE D — Provision AAA to Fabric Edges (via DNAC or manual)
If DNAC:
- DNAC GUI:
Design → Network Settings → AAA→ Add ISE AAA server (VIP or PSNs), set timeout 5–7s, retries 3. - DNAC:
Provision → Devices→ select edge switches/WLC → apply AAA template (push).
Manual: (on C9300)
configure terminal aaa new-model radius server ISE-VIP address ipv4 10.10.10.100 auth-port 1812 acct-port 1813 key MyRadKey aaa group server radius ISE-GRP server name ISE-VIP aaa authentication dot1x default group ISE-GRP aaa authorization network default group ISE-GRP aaa accounting dot1x default start-stop group ISE-GRP radius-server timeout 5 radius-server retransmit 3 write memory
Validation on C9300:
show run | section radius show radius statistics
Expected: RADIUS servers configured; reachable.
PHASE E — Enable CTS on Fabric Edges & Confirm SGT Awareness
- On C9300 (if not already):
configure terminal cts server 10.10.10.100 # optional registration; or CTS learns via ISE cts authorization update exit
(Most modern designs use ISE push; DNAC handles CTS enablement via provisioning)
- Verify installed SGT map & RBAC matrix:
show cts role-based permissions show cts role-based sgt-map show cts role-based counters
Expected: role-based permissions list entries corresponding to SGACLs; counters zero until traffic flows.
PHASE F — Test Cases & Validation (evidence-driven)
Test 1 — Wired EAP-TLS (Employee → SGT=Employees → Can reach Servers)
Pre-state: Edge port configured for 802.1X, client has machine/user cert.
Action: Connect Win11 to access port; trigger EAP-TLS.
ISE GUI validation:
Operations → RADIUS → Live Logs→ entry: Access-Accept, Authorization profileEmployees-Authz, Assigned SGTEmployees.
Edge CLI validation:
show authentication sessions interface Gi1/0/10 details # Expected: Authenticated, Method = EAP, Authorization = Employees-Authz, SGT=Employees show cts role-based counters # counters increment on allowed flows show ip access-lists dynamic # if DACL applied
Network test: ping server (expected pass).
Acceptance: Success and evidence captured.
Test 2 — IoT MAB (MAC only → SGT=IoT → Denied to Servers)
Action: Connect IoT device to MAB port.
ISE GUI: Live Logs show MAB, Authorization Profile IoT-Authz, SGT=IoT.
Edge CLI:
show authentication sessions interface Gi1/0/11 details show cts role-based counters show ip access-lists dynamic # observe Quarantine DACL if applied
Network test: attempt to reach server (expected fail per SGACL). Validate blocked.
Acceptance: IoT cannot access servers; SGACL enforced.
Test 3 — Guest (CWA) mapped to Guest SGT and Internet only
Action: Connect phone to Guest SSID, complete captive portal.
ISE Live Logs: portal login accepted, Authorization profile Guest-Authz, SGT=Guest.
WLC Validation: show wireless client mac <mac> detail shows session, ISE as NAD.
Edge Fabric validation: show cts counters for Guest→Internet allow.
Test 4 — CoA / ANC Quarantine (ISE triggers DACL via CoA)
Action: In ISE, Operations → Adaptive Network Control → select client → Quarantine (Apply Quarantine DACL or set SGT=Quarantine).
ISE GUI validation: Live Logs show Authorization change and CoA event.
Edge CLI validation:
show authentication sessions interface Gi1/0/10 details | include DACL|SGT|Status show ip access-lists dynamic
Result: client is restricted by Quarantine DACL (verify blocked access). CoA log present.
Test 5 — SGACL change (policy change) and propagation
Action: Modify DNAC matrix or ISE SGACL to deny Employees→Servers during maintenance; publish.
Validation: show cts role-based permissions should reflect updated SGACL. Test connectivity (should be blocked). Document timestamps and config deltas.
PHASE G — Troubleshooting & Diagnostics (commands + what to look for)
ISE checks
show application status ise show logging application ise-radius.log tail 100 show logging application ise-psc.log tail 100 show trustsec sgt show trustsec sgacl
Look for: RADIUS rejects, missing SGT mapping, ERS errors.
Edge checks
show authentication sessions interface Gi1/0/10 details show radius statistics show cts role-based permissions show cts role-based counters show ip access-lists dynamic
Look for: RADIUS timeouts, no SGT on session, DACL not applied, CoA not received.
CoA troubleshooting
- Verify UDP port allowed (CoA often UDP/3799 or per vendor).
- Check NAD logs for CoA receipt.
- Check ISE Live Logs for CoA sent success/failure.
Evidence Pack (deliverable)
For audit, produce a zip containing:
- CLI captures:
edge_auth_<timestamp>.txt,ise_logs_<timestamp>.txt,cts_permissions.txt. - Test matrix CSV (columns below).
- Time-stamped change log.
Evidence CSV columnsTestCase,PreState,Action,Expected,Actual,Edge_CLI_File,Result,Notes
Expert-Level Use Cases (consultant / SRE patterns)
- Automated Threat Containment: On EDR detection, SIEM triggers ISE Quarantine (via pxGrid) — CoA applies Quarantine DACL across any NAD in seconds.
- Blue/Green SGT Migration: Stage new SGT taxonomy in lab, publish, map old→new SGTs temporarily, cutover with no user impact.
- SGT for Multi-Cloud Workloads: Map cloud VPC endpoints to SGTs for consistent policy across on-prem and cloud via SD-WAN + SGT federation.
- IoT Zero-Trust: Auto-profile IoT, place into restricted VN, SGT=IoT, deny east-west to servers; limited internet access only.
- SGT to Firewall Integration: Export ISE SGT mapping into NGFW (FTD) for L7 micro-segmentation on top of fabric enforcement.
- Periodic CoA Matrix Test: Nightly synthetic CoA test from each PSN to sample NADs; auto-alert failures.
- Policy CI/CD: Manage SGTs/Matrix in Git, run pre-publish tests (DNAC sandbox), then push to ISE & fabric with automated verification.
- Assurance-Driven Tuning: Use DNAC Assurance metrics to auto-tune RADIUS timeouts/retransmit via templates.
- Cross-Site Quarantine Orchestration: Combine GSLB + SGT taxonomy to ensure quarantines behave correctly across regions after DNS failover.
- SGT Federation for Mergers: During M&A, map partner SGTs to corporate SGTs, apply translation rules during transition.
FAQs SGT-Based Access Control in SD-Access
1. What exactly is an SGT, and how is it different from VLANs or IP ACLs?
Answer:
- VLANs segment based on Layer 2 boundaries.
- ACLs segment based on IP addresses at Layer 3/4.
- SGTs (Security Group Tags) operate at Layer 2.5 — they are metadata labels attached to traffic at ingress.
- These tags are carried across the fabric (via VXLAN) and enforced dynamically by SGACLs (Security Group ACLs).
Validation: - GUI: In ISE → Work Centers > TrustSec > Components > Security Groups
- CLI:
show cts role-based sgt-mapon fabric edge or WLC.
2. How are SGTs assigned to endpoints in an SDA fabric?
Answer:
SGTs can be assigned by:
- Static assignment in ISE (per MAC, IP, or user group).
- Dynamic assignment via ISE authorization policies.
- Propagation through DNA Center’s SDA integration.
Validation:
- ISE GUI: Policy > Policy Sets > Authorization Results
- CLI: On fabric edge →
show cts role-based sgt-maps all.
3. What role does DNA Center play in SGT deployment?
Answer:
DNA Center acts as the central orchestrator:
- Pushes SGT-to-IP mappings to fabric nodes.
- Distributes SGACLs consistently across SDA fabric.
- Provides visualization of TrustSec matrix (who can talk to whom).
Validation: - DNA Center GUI → Policy > Group-Based Access Control (Matrix)
4. How do SGACLs differ from traditional ACLs?
Answer:
- Traditional ACLs = static IP-based rules, local to the device.
- SGACLs = identity-based, portable, centrally defined in ISE, enforced by all fabric devices.
CLI Validation: show cts role-based permissions→ shows SGACLs applied.- Compare with
show run | i access-list(no IP ACL explosion).
5. How do I validate that an endpoint is correctly tagged with an SGT?
Answer:
- Authenticate endpoint through ISE (wired/wireless).
- Check session details:
- ISE GUI → Operations > Live Sessions.
- Switch CLI →
show authentication sessions interface x/x details. - WLC CLI →
show wireless client mac <client-mac> detail.
- Look for assigned SGT ID.
6. What happens if an SGT mapping is missing or incorrect?
Answer:
- If missing: Traffic falls into default SGT (often 0 – Unknown).
- If incorrect: Policy may over-permit (security risk) or over-restrict (connectivity break).
Validation: - CLI:
show cts role-based sgt-map - GUI: ISE → Work Centers > TrustSec > Components > Security Groups.
7. Can I apply SGT-based policies across WAN or between Data Centers?
Answer:
Yes — using SGT Exchange Protocol (SXP) or fabric-based VXLAN encapsulation.
- SXP propagates SGT-IP bindings to remote devices.
- SDA fabric uses VXLAN to carry SGT metadata end-to-end.
Validation: - CLI:
show cts sxp connections - GUI: ISE → Work Centers > TrustSec > SXP.
8. How do I troubleshoot SGACL enforcement when traffic is blocked?
Answer:
Step-by-step:
- Verify endpoint is tagged →
show auth session. - Verify SGACL mapping →
show cts role-based permissions. - Use packet-tracer (ASA) or ACL hit counters (switch) →
show cts role-based counters. - Check DNA Center Policy Matrix for configured rule.
9. Can I integrate SGTs with firewalls and third-party security devices?
Answer:
Yes. Cisco Firepower, ASA, and even third-party firewalls can consume SGTs via:
- Inline tagging (VXLAN or 802.1AE MACsec).
- SXP-based IP-to-SGT mappings.
This ensures end-to-end identity-based enforcement.
Validation: - Firepower CLI:
show cts role-based sgt-map - Firepower GUI: Objects > Security Group Tags.
10. What’s the difference between scalable groups in DNA Center and SGTs in ISE?
Answer:
- DNA Center Scalable Groups = abstraction layer for defining intent (user, IoT, server).
- ISE SGTs = actual security tags that map to those scalable groups.
DNA Center → ISE sync ensures both stay aligned.
Validation: - DNA Center GUI → Policy > Groups.
- ISE GUI → TrustSec > Security Groups.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes (Key takeaways)
- SGT-based access control replaces brittle VLAN/ACL models with identity-driven segmentation.
- Design (DNAC SGT taxonomy) → Policy (ISE SGACL/Authz) → Enforcement (fabric edge) → Assurance (DNAC/ISE logs).
- Always validate via GUI + CLI and produce an evidence pack for audits.
- Automate provisioning (DNAC) and test containment (CoA/ANC) regularly.
Upgrade Your Skills — Start Today
For in-depth Cisco ISE Mastery, subscribe to Network Journey on YouTube and join my instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro
- I run a focused 4-month instructor-led CCIE Security track (covers TrustSec/SGT, SDA, pxGrid, multi-DC HA/DR, policy migration).
- Course outline & enroll: https://course.networkjourney.com/ccie-security/
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



