[Day 109] Cisco ISE Mastery Training: Integration with Cisco ASA VPN
Table of Contents
Introduction
Welcome to Day 109 of Cisco ISE Mastery Training — today, we tackle one of the most business-critical integrations in secure access: Cisco Identity Services Engine (ISE) with Cisco Adaptive Security Appliance (ASA) VPN.
Why is this so important? Because in the modern enterprise, remote access VPNs are no longer just about connectivity — they are about secure, identity-driven access control. Employees, contractors, and partners connecting through VPN must be validated not only for who they are but also for what device they’re using, its security posture, and what level of access they should be granted.
Cisco ASA remains one of the most widely deployed VPN platforms worldwide, and when integrated with Cisco ISE, it unlocks a powerful policy-based access control model where:
- VPN users are authenticated against centralized identity sources.
- Endpoints undergo posture assessment (AV/OS/firewall status).
- Users and devices are dynamically assigned to Security Group Tags (SGTs) or ACLs.
- Role-based, context-aware policies determine access to sensitive applications.
Think of it like moving from a basic VPN tunnel to a zero-trust remote access architecture powered by ISE. In this session, we’ll go step-by-step — both GUI and CLI — into configuring ASA and ISE integration, validating each step, and building a lab workbook scenario you can replicate for real-world deployments.
By the end of this lecture, you’ll not only know the theory but also be able to:
- Build the ASA–ISE trust relationship.
- Configure ASA to use ISE for authentication and authorization.
- Enforce posture validation on remote VPN clients.
- Assign dynamic access policies using downloadable ACLs and SGTs.
- Troubleshoot with real CLI and live logs.ote Access, test AnyConnect (SSL/TLS) and ASA IPSec flows, validate authorization attributes, and prove CoA/DACL remediation — with GUI and CLI evidence at each step.
Problem Statement (Real-world challenge)
Typical pain points when integrating ASA VPN with ISE:
- ASA uses local or multiple siloed RADIUS servers → inconsistent access rules.
- No central authorization mapping → operator changes on ASA drift and get lost.
- Posture and endpoint health not enforced at login → compromised endpoints gain access.
- No dynamic remediation → admin must manually lock or disconnect sessions.
We solve this by centralizing authentication and authorization in ISE, using RADIUS for auth, ERS/pxGrid for telemetry/closed-loop actions, and CoA for dynamic session change/cleanup.
Solution Overview (How Cisco ISE addresses it)
- Authentication: ASA forwards RADIUS requests (AnyConnect SSL or IPSec) to ISE (PSNs or VIP). ISE supports EAP, PEAP, MSCHAPv2, and certificate validation.
- Authorization: ISE returns RADIUS attributes or Authorization Profiles (Group Policy name, DACL/Filter-Id, or custom AV-pairs) that ASA maps to group-policies and downloadable ACLs.
- Accounting & Visibility: ISE MnT captures auth/accounting logs; DNAC/ SIEM can consume via pxGrid or syslog.
- Remediation: ISE issues CoA to ASA for session change (revoke, reauth, apply DACL).
- Posture (optional): ISE can run posture checks (AnyConnect posture) and place endpoints in quarantine group-policies until compliant.
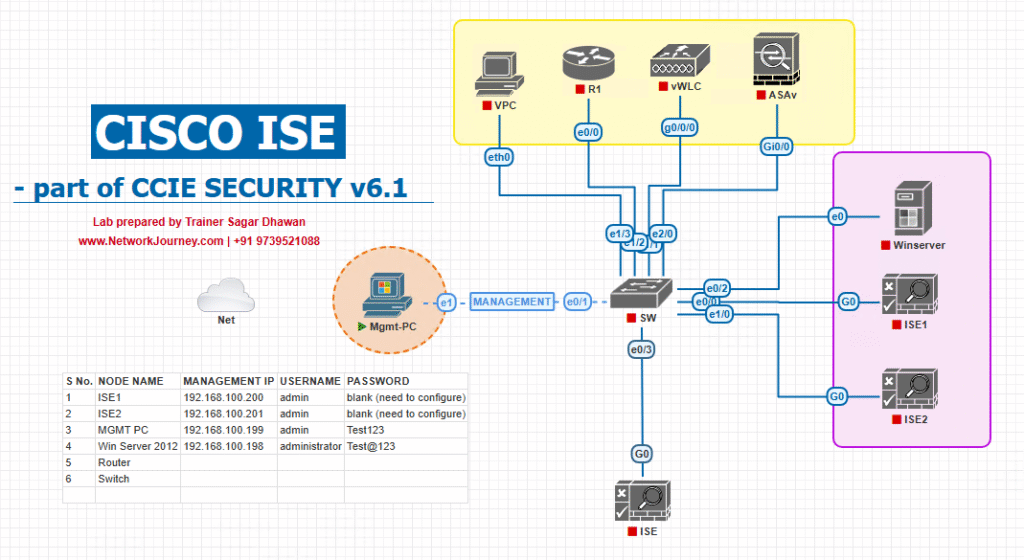
Sample Lab Topology (VMware/EVE-NG + devices)
VMs / Appliances
- Cisco ISE cluster (PAN, MnT, PSN1, PSN2) — VMware
- Cisco ASA (9.x/9.12+) — VM in EVE-NG or physical
- AnyConnect client (Windows 10/11 VM)
- AD (Windows AD) + PKI (ADCS), NTP, DNS
- Optional: SIEM or DNAC for pxGrid integration
Logical diagram:
Step-by-Step GUI Configuration Guide
PREP: baseline checks (do BEFORE changes)
- NTP & DNS: on ASA and ISE ensure NTP sync and DNS resolution.
# Jump host or ASA (exec) ping <ise-pan-fqdn> show ntp status # ASA: `show ntp status` # ISE CLI show application status ise - Versions: Ensure ASA and ISE versions are compatible (ASA 9.8+ recommended with ISE 2.4/2.6/3.x).
STEP 1 — Register ASA as a Network Device in ISE (GUI)
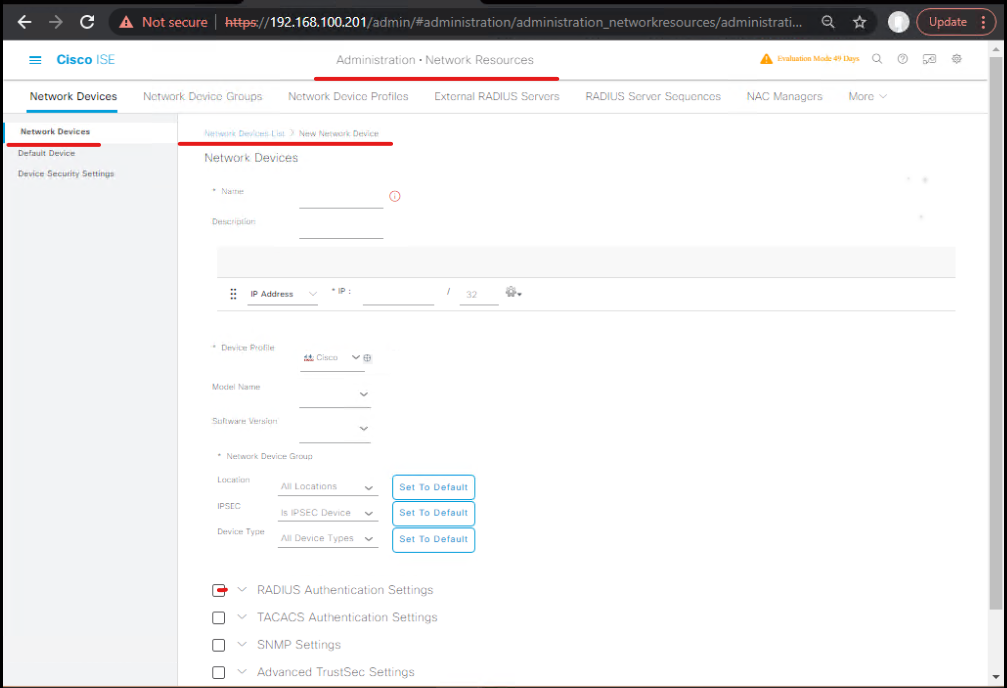
- ISE GUI:
Administration → Network Resources → Network Devices → Add- Name:
ASA-VPN - IP Address: ASA management/internal IP (or 0.0.0.0 with subnets)
- RADIUS Shared Secret:
<MyRadKey>(store securely) - Enable RADIUS Authentication (checkbox)
- Name:
- Validation (ISE GUI): After saving, confirm device listed and reachability test passes.
- CLI check (ISE):
show application status ise show logging application ise-psc.log tail 20
STEP 2 — Configure ASA to use ISE as RADIUS AAA Server (ASA CLI)
- On ASA:
! create RADIUS AAA server group and host aaa-server ISE-RADIUS protocol radius aaa-server ISE-RADIUS (inside) host 10.10.10.15 key MyRadKey timeout 10
(replace interface name (inside) with ASA interface used for ISE reachability; use VIP if LB in front of PSNs)
- Set ASA VPN tunnel-group to use the AAA group:
tunnel-group AnyConnect-VPN general-attributes address-pool VPN_POOL default-group-policy DfltGrpPolicy ! tunnel-group AnyConnect-VPN ppp-attributes authentication-server-group ISE-RADIUS
or map authentication for webvpn:
tunnel-group DefaultRAGroup general-attributes authentication-server-group ISE-RADIUS
- Validation (ASA CLI):
show aaa-server ISE-RADIUS show running-config tunnel-group
STEP 3 — Configure ISE Policy Set for ASA VPN (ISE GUI)
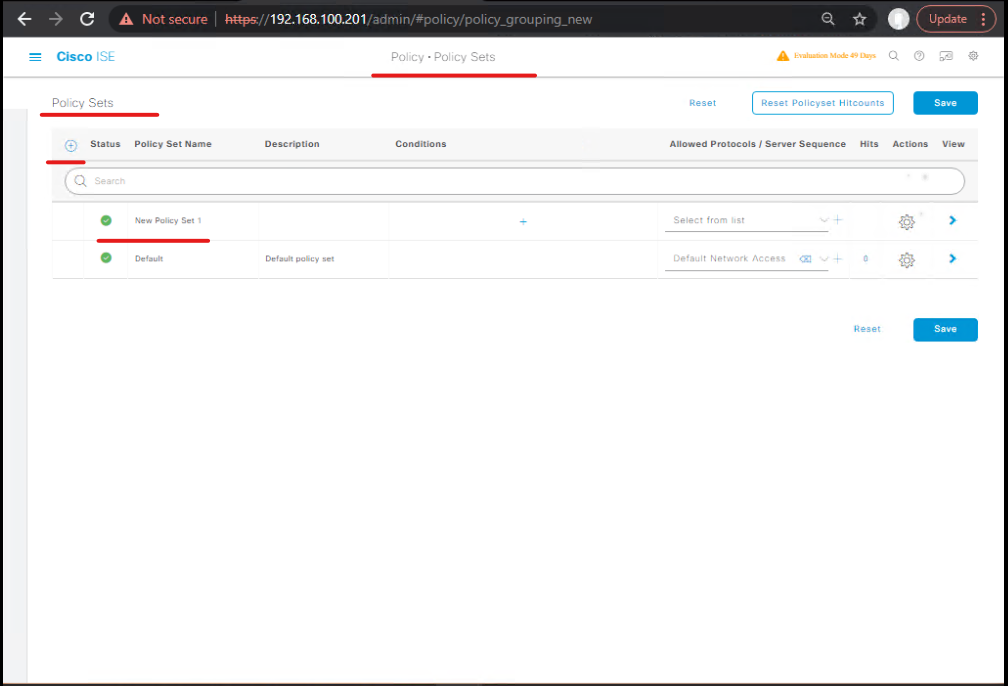
- Policy Sets:
Policy → Policy Sets → Add Policy Set- Name:
ASA-AnyConnect - Condition: Network Device: selected
ASA-VPNor NAD group (use network device group or FQDN to scope).
- Name:
- Authentication Policy (within Policy Set):
- Order: EAP-TLS (if using certs) → PEAP/MSCHAPv2 (username/password) → PAP (if required).
- Order: EAP-TLS (if using certs) → PEAP/MSCHAPv2 (username/password) → PAP (if required).
- Authorization Policy: Add rules mapping to Authorization Profiles:
If AD group = VPN-Employees → Authorization Profile = VPN-Employees-Authz(returns group-policy name / DACL / SGT)If Device Profile = Noncompliant → Authorization Profile = VPN-Quarantine-Authz
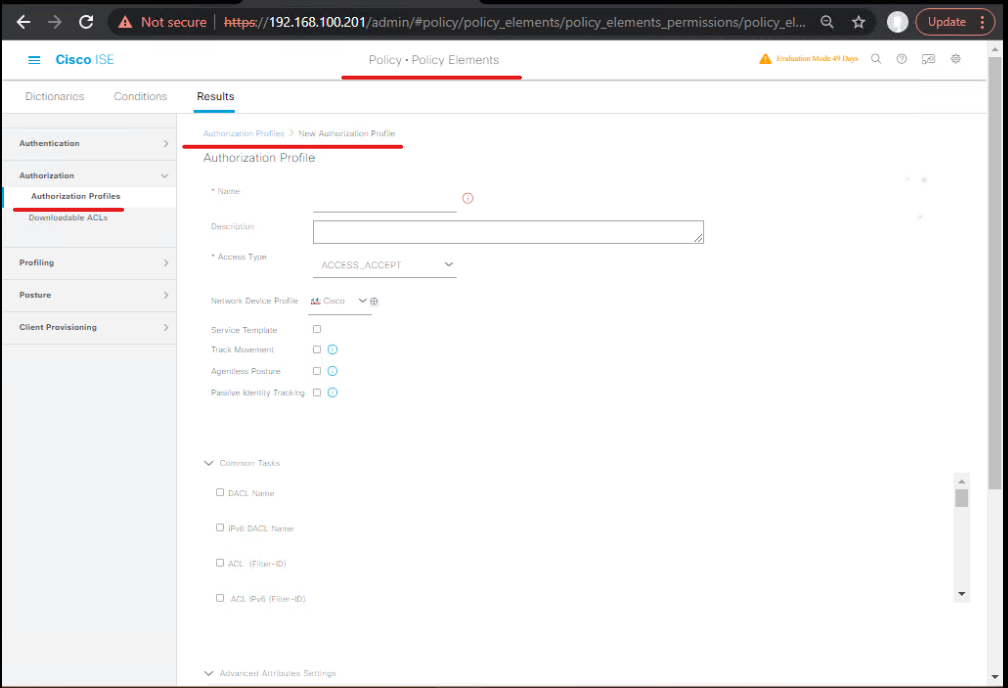
- Create Authorization Profiles:
Policy → Authorization → Authorization Profiles → Add- VPN-Employees-Authz: (Example attributes)
- RADIUS attribute: Filter-Id = ACL_VPN_EMPLOYEES (or use
Cisco-AVPairto setgroup-policy=GPolicy_Employees) - Or set SGT (if ASA supports SGT enforcement via TrustSec/other)
- Set sessionTimeout or other RADIUS attributes as needed.
- RADIUS attribute: Filter-Id = ACL_VPN_EMPLOYEES (or use
- VPN-Quarantine-Authz: Filter-Id =
ACL_QUARANTINEor setgroup-policy=GPolicy_Quarantine.
- VPN-Employees-Authz: (Example attributes)
Notes on attributes: ISE can return multiple RADIUS attributes. For ASA, common approaches:
- Return a group-policy name (via Cisco-AVPair) so ASA applies that group policy. Example AV-pair:
cisco-avpair = "gp:GroupPolicy=GPolicy_Employees"(GUI creates this under Authorization Profile → Advanced RADIUS Attributes). - Return Filter-Id (RADIUS attribute 11) which ASA maps to named ACLs.
- Use Downloadable ACL (dACL) by returning
Filter-Idor other accepted attributes if ASA supports them.
Validation (ISE GUI): Ensure Authorization Profiles have the right attributes set.
STEP 4 — ASA Group-Policy and ACLs (ASA CLI)
- Create ASA group policies and ACLs that match the ISE returned values:
access-list ACL_VPN_EMPLOYEES extended permit ip any 10.0.10.0 255.255.255.0 access-list ACL_QUARANTINE extended deny ip any 10.0.10.0 255.255.255.0 access-list ACL_QUARANTINE extended permit ip any any eq 53 ! group-policy GPolicy_Employees internal group-policy GPolicy_Employees attributes split-tunnel-policy tunnelspecified split-tunnel-network-list value SPLIT_TUNNEL_LIST dns-server value 10.10.10.5 ! group-policy GPolicy_Quarantine internal group-policy GPolicy_Quarantine attributes vpn-filter value ACL_QUARANTINE
- Map group-policy names to tunnel group if needed (ASA earlier used default group policy). If ISE returns group-policy via AV-pair, ASA will apply it automatically.
Validation (ASA CLI):
show running-config access-list ACL_VPN_EMPLOYEES show running-config group-policy
STEP 5 — Test AnyConnect VPN Authentication (client)
Client steps
- Install AnyConnect client.
- Connect to ASA external IP / FQDN with credentials (or certificate if EAP-TLS).
- Choose appropriate authentication method when prompted.
ISE GUI Validation
Operations → RADIUS → Live Logs→ filter by client IP or username:- Look for Access-Request → Access-Accept, show Authorization Profile and returned RADIUS attributes (group-policy / Filter-Id).
- Look for Access-Request → Access-Accept, show Authorization Profile and returned RADIUS attributes (group-policy / Filter-Id).
ASA CLI Validation
show vpn-sessiondb anyconnect detail show vpn-sessiondb detail username <user> # shows applied group-policy, ACL show log # view syslog lines for auth
Expected: session established; group-policy seen; split-tunnel/list etc applied.
Evidence to capture
- ASA
show vpn-sessiondboutput saved.
STEP 6 — Test Authorization Variations (Quarantine / Posture)
Scenario A: Compliant user → full access
- Ensure user in AD group
VPN-Employees; ISE Authorize →VPN-Employees-Authzreturned → client can access server ranges.
Scenario B: Non-compliant / posture fail → Quarantine
- If using posture: configure AnyConnect posture policies in ISE and upload posture agent to client.
- Simulate non-compliance (disable AV or make registry change) and attempt connection. ISE should return
VPN-Quarantine-Authz(group-policy Quarantine).
ISE Validation
Operations → Live Logsshows posture result and Authorization change.Work Centers → Postureshows last assessment details.
ASA Validation
show vpn-sessiondb anyconnect detail | include Quarantine show running-config access-list ACL_QUARANTINE
Expected: Quarantine ACL applied; user unable to reach protected servers.
STEP 7 — CoA (Change of Authorization) Tests
Purpose: Ensure ISE can alter an active ASA VPN session (e.g., move to quarantine or revoke).
- From ISE GUI:
Operations → Live Sessions→ find session → select Change Authorization → chooseVPN-Quarantine-Authz. - ISE CLI Validation (logs):
show logging application ise-radius.log tail 100 # look for CoA / Disconnect messages
- ASA CLI Validation:
show vpn-sessiondb detail remote | include username # then check session details to see new group-policy / vpn-filter applied show vpn-sessiondb anyconnect detail username <user>
Expected: ASA receives CoA and applies new group-policy or DACL; session behavior changes accordingly (reduced access or disconnection).
Notes: CoA often uses UDP 3799 or RADIUS CoA attributes; ASA expects CoA from configured RADIUS servers — ensure firewall rules allow return CoA packets.
STEP 8 — Accounting & Logging Validation (ISE MnT, ASA syslog)
- On ISE (GUI):
Operations → Reports → RADIUS Accountingexport to PDF/CSV. - ASA syslog: Ensure ASA syslog to syslog server or ISE MnT (if used) for correlation:
show logging show logging | include RADIUS
- Cross-validate: match ASA session start/stop logs with ISE accounting records (NAS-Session-ID or username + timestamp).
STEP 9 — Failure Modes & Rollback
- If VPN stops accepting auth: check ASA
show aaa-serverfor reachability, ISEshow application status ise, and network reachability (ping/traceroute). - Rollback: Revert ASA tunnel-group authentication-server-group to local or previous RADIUS server and disable ISE policy changes.
Commands:
# ASA no aaa-server ISE-RADIUS # Or reassign default authentication tunnel-group AnyConnect-VPN general-attributes authentication-server-group LOCAL
STEP 10 — Evidence Pack & Acceptance Criteria (deliverable)
For every test collect:
- ISE Live Log showing Access-Request / Access-Accept and returned attributes.
- ASA
show vpn-sessiondb anyconnect detailoutput file. - ASA
show aaa-server ISE-RADIUSoutput. - Client VPN success .
- Timestamped CSV test matrix with Pass/Fail + notes.
Acceptance criteria
- Successful authentication and correct group-policy / ACL assigned for at least 3 test users (employee, contractor, non-compliant).
- CoA successfully moves one session to Quarantine.
- Accounting logs show Start/Stop on MnT.
Expert-Level Use Cases (practical patterns)
- Adaptive Remote Access — ISE posture + machine cert + AD group → dynamic split-tunnel & SGT assignment. CoA quarantines non-compliant hosts.
- Contractor Access with Just-in-Time Provisioning — ISE guest workflows create temporary AD accounts + dynamic group-policy for ASA; session expires automatically.
- Incident Containment Playbook — SIEM detects suspicious VPN behavior → triggers ISE pxGrid/REST → ISE pushes CoA to ASA to quarantine user and notify SOC.
- Add-on Multi-Factor for VPN — ISE integrates with TACACS or third-party MFA via RADIUS proxy; policy set enforces 2FA for high-risk groups.
- High-Availability VPN Fabric — LB VIPs in front of PSNs, ASA clusters using multiple AAA server entries for scale & resiliency.
- DACL-Based Lateral Restriction — ISE returns Filter-Id referencing per-tenant DACLs to enforce microsegmentation for VPN sessions.
- Cert-Only VPN Profiles for Privileged Users — EAP-TLS only for admin groups; group-policy restricts privilege elevation.
- Cross-Domain SSO — ISE integrates with IdP and ASA webvpn for SSO-based VPN onboarding combined with dynamic ISE authZ.
- Automated Evidence & Auditing — After each user session, ISE MnT exports accounting to SIEM and compliance reports auto-generated for audit.
- Cloud-Burst PSNs for Peak Load — Spin cloud PSNs, add to ASA AAA list, and use DNS or LB to balance RADIUS during high-load periods.
FAQs – Cisco ISE Integration with ASA VPN
FAQ 1. What authentication methods can ISE provide for ASA VPN users?
Answer:
ISE can integrate with ASA using:
- RADIUS (most common) → ASA sends authentication requests to ISE.
- TACACS+ → Not typically for VPN auth, mainly for device admin.
- EAP methods → Such as EAP-TLS (cert-based), PEAP-MSCHAPv2 (username/password).
CLI Validation (ASA):
show running-config aaa-server
ISE GUI Check:
- Administration > Identity Management > External Identity Sources > Active Directory (if AD is backend).
- Verify ASA shows up under Administration > Network Resources > Network Devices.
FAQ 2. How do I configure ASA to use ISE as the RADIUS server?
Answer:
On ASA:
aaa-server ISE-RADIUS protocol radius aaa-server ISE-RADIUS host <ISE-IP> key <shared-secret> authentication-port 1812 accounting-port 1813
Then bind the AAA server to VPN tunnel-group:
tunnel-group <VPN-PROFILE> general-attributes authentication-server-group ISE-RADIUS
ISE GUI Check:
[Administration > Network Resources > Network Devices > Add Device]
- Add ASA with same shared secret.
FAQ 3. How can I enforce posture assessment for AnyConnect VPN users?
Answer:
- On ASA, enable posture module in AnyConnect.
- On ISE, create a Posture Policy under:
- Work Centers > Posture > Policy Sets.
- Users failing posture → placed in quarantine VLAN/ACL.
CLI Validation (ASA):
show vpn-sessiondb anyconnect
ISE Logs:
- Operations > RADIUS > Live Logs → Check posture result.
FAQ 4. How does ISE differentiate between different VPN groups/tunnel-profiles?
Answer:
ASA passes the Tunnel-Group Name as a RADIUS attribute to ISE.
In ISE policy sets, you can match this attribute (e.g., RADIUS:NAS-Tunnel-Group-Name).
CLI Validation:
debug radius authentication
Look for the Tunnel-Group attribute sent.
FAQ 5. Can I assign dynamic ACLs (dACLs) or Security Group Tags (SGTs) to VPN users?
Answer:
Yes .
- In ISE, create an Authorization Profile with a downloadable ACL.
- Assign it in the policy set based on group membership.
- For SDA-enabled environments, assign SGTs instead.
ISE GUI Check:
[Policy > Policy Elements > Results > Authorization > Downloadable ACLs].
FAQ 6. What’s the difference between using LDAP/AD directly on ASA vs. via ISE?
Answer:
- Direct ASA ↔ AD → Basic username/password auth only.
- ASA ↔ ISE ↔ AD → Enables advanced context: posture, dACLs, SGTs, profiling, multi-factor.
Always prefer ISE integration for scalable and policy-driven VPN access.
FAQ 7. How can I troubleshoot authentication failures between ASA and ISE?
Answer:
- ASA Side:
debug radius authentication debug aaa authentication show vpn-sessiondb detail - ISE Side:
- Operations > RADIUS > Live Logs → Check failure reason (e.g., bad secret, AD lookup failed).
FAQ 8. How do I validate that ISE is returning the right authorization profile?
Answer:
- In ISE Live Logs, check the AuthZ Profile applied.
- On ASA CLI:
show vpn-sessiondb anyconnect filter name <username>Look forAssigned ACLor SGT.
FAQ 9. Can I enforce MFA (multi-factor authentication) with ISE + ASA?
Answer:
Yes .
ISE can integrate with RSA, Duo, or Azure MFA via RADIUS proxy or SAML.
- ASA still uses ISE as the RADIUS server.
- ISE forwards secondary auth request to MFA provider.
GUI Check in ISE:
Administration > Identity Management > External Identity Sources > RADIUS Token Servers.
FAQ 10. What licenses are required for ASA–ISE VPN integration?
Answer:
- ISE Base → Required for RADIUS AAA.
- ISE Plus (or Advantage) → Required for posture assessment.
- ISE Apex (or Premier) → Required for VPN posture/mobility and BYOD workflows.
- ASA AnyConnect Apex Licenses → Required for posture and advanced VPN features.
CLI Validation (ASA):
show activation-key
GUI Validation (ISE):
Administration > System > Licensing.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes (Key takeaways)
- ISE centralizes VPN authz: map AD groups to Authorization Profiles that return ASA-readable attributes (group-policy / filter-id).
- Validate end-to-end: client connect → ASA → RADIUS → ISE authz → ASA applies group-policy → user access. Capture Live Logs + ASA sessiondb.
- CoA is essential for remediation and dynamic policy change — test it thoroughly.
- Posture adds security but increases complexity — automate test cases for compliance/non-compliance flows.
- Backup evidence: always produce an evidence pack after each change window for audits.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro
I run a focused 4 months instructor-led CCIE Security track (covers ISE, TrustSec, SDA, pxGrid, multi-DC HA/DR, VPN integrations, TAC-grade troubleshooting).
Course & enrollment: https://course.networkjourney.com/ccie-security/
Book a discovery call, get the ASA-ISE VPN Runbook Pack (templates, CLI scripts, evidence CSV), and reserve your seat.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



