[Day 110] Cisco ISE Mastery Training: AnyConnect Posture Enforcement for Remote Users
Table of Contents
Introduction
In today’s world, remote work is no longer an exception—it’s the new normal. With users connecting from home offices, co-working spaces, airports, and even unsecured public Wi-Fi, the enterprise security perimeter has dissolved. Traditional VPN connectivity ensures encryption, but it does not guarantee that the endpoint itself is secure, compliant, or trusted. An infected laptop or a non-compliant device tunneling into your corporate network can be just as dangerous as leaving your datacenter door unlocked.
This is where Cisco ISE Posture Enforcement with AnyConnect becomes mission-critical. ISE doesn’t just authenticate users—it validates the health, compliance, and security posture of the connecting endpoint in real time. By integrating with Cisco AnyConnect (or Cisco Secure Client), organizations can enforce policies such as:
- Ensuring up-to-date antivirus/antimalware is running.
- Validating OS patches and updates.
- Verifying firewall, encryption, and registry settings.
- Restricting non-compliant endpoints to a remediation VLAN until fixed.
Think of it like a virtual security guard at the network door: not only checking who you are, but also if you’re healthy enough to enter. This provides a Zero Trust Remote Access Framework where identity and posture together decide access privileges.
In our Article today, we’ll go step-by-step, both GUI + CLI validation, to build and test AnyConnect Posture Enforcement with ISE—from installing the Posture Agent to validating remediation flows, posture profiles, and policy sets.
By the end of this masterclass, you will have the confidence to design, deploy, and troubleshoot Cisco ISE Posture for Remote VPN users at scale, just like in real-world enterprise networks.
Problem Statement
Remote access risk is twofold: users may be compromised and devices may be unhealthy. Without posture enforcement:
- Compromised or unpatched endpoints get full access → lateral movement and data leakage.
- Security teams cannot enforce corporate baseline on remote devices.
- Manual remediation is slow and error prone.
You need an automated way to validate device health during VPN onboarding, enforce policy in real time, and remediate where possible. That’s exactly what AnyConnect posture + ISE delivers — when architected, configured, and validated correctly.
Solution Overview
Components & flow (high level):
- User/Device attempts VPN (AnyConnect connects to ASA).
- ASA forwards RADIUS auth to ISE (PSN).
- ISE evaluates authentication policies; if posture is required it triggers the Posture workflow.
- AnyConnect posture module (client) is downloaded/activated; it runs checks and reports findings to ISE.
- ISE returns Authorization Profile based on posture (Full-Access, Quarantine, Remediation).
- ASA applies the returned attributes (group-policy, downloadable ACL, or SGT).
- ISE can issue CoA to change session state post-connect (e.g., after remediation).
This lab covers all steps: posture policy authoring, AnyConnect profile/ASA config, ISE policy set rules, test cases (compliant, non-compliant, remediation), and post-connect CoA validation.
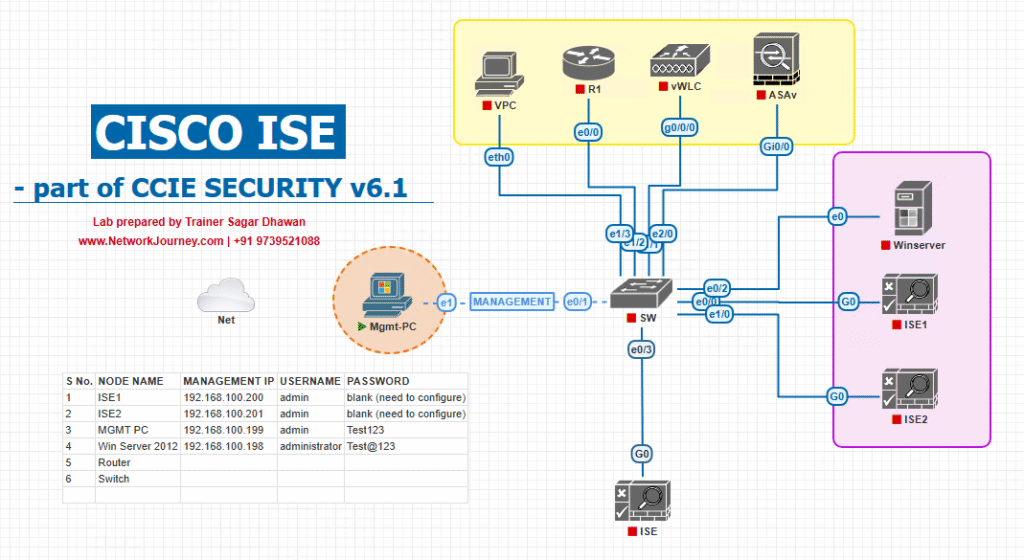
Sample Lab Topology (VMware / EVE-NG + devices)
Virtual/Physical elements
- Cisco ISE cluster (PAN, MnT, 1–2 PSNs) — VMware
- Cisco ASA (ASAv) running AnyConnect — EVE-NG or physical
- AnyConnect client (Windows 10/11 VM) — posture agent installed via ASA / manual
- Active Directory + PKI (ADCS) — VMware
- NTP, DNS services
- Optional: SIEM for log aggregation
Topology diagram:
Lab notes
- Use an ASA reachable by client and ISE; ensure DNS resolves ISE PAN/PSN and ASA.
- Use a short NTP drift window (fine time sync essential for certificates).
- Decide whether ASA will host posture agent download (webvpn) or distribute via enterprise channels.
Step-by-Step GUI Configuration Guide
PREP: mandatory prechecks (run first)
- Verify NTP + DNS across all components.
- CLI (jump host / ISE / ASA):
# Jump host or ISE shell nslookup ise-pan.corp ping -c3 ise-pan.corp ntpstat # or `chronyc tracking` - Expected: DNS resolves; NTP synchronized.
- CLI (jump host / ISE / ASA):
- Confirm versions & resources:
- ISE version supports posture (ISE 2.4+ / 2.6 / 3.x).
- ASA firmware supports AnyConnect posture and RADIUS CoA (e.g., ASA 9.8+).
- [ISE Version] [ASA show version]
STEP 1 — Prepare ISE: enable Posture service and create Posture Policy elements
- Enable Posture Service (ISE GUI)
- Path:
Work Centers → Posture→Posture Services→ ensure service is enabled and healthy. - If a standalone posture node is needed, register and set role.
- [ISE Posture Service Enabled]
- Path:
- Create Posture Elements (Conditions/Checks)
Work Centers → Posture → Posture Condition -> Add- Add checks: Antivirus present & up to date, OS patch level, Firewall enabled, Registry/key exists, File presence/hash. For Windows, select the built-in checks (AV, Firewall, MS updates).
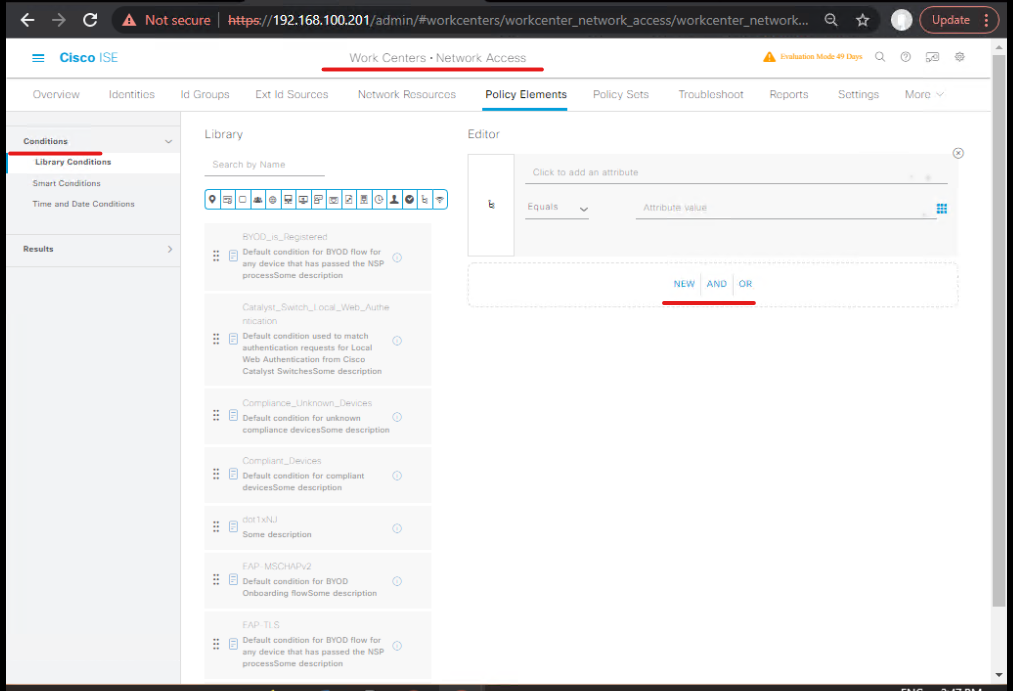
- Group these into a Posture Condition named
Corp-Baseline. - [Create Posture Condition — Corp-Baseline]
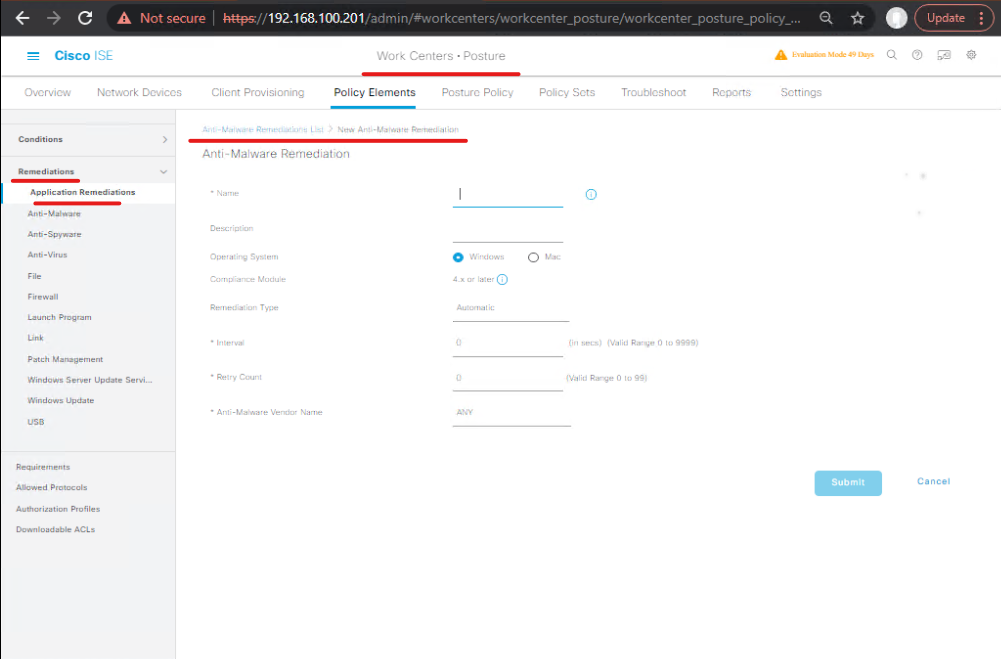
- Create Posture Remediation Actions
Work Centers → Posture → Remediation → Add- Create actions such as
Prompt user to install AV, display remediation portal URL, or trigger downloadable installers. For automated remediation (e.g., run script), prepare remediation packages/outbound resources. - [Remediation Action config]
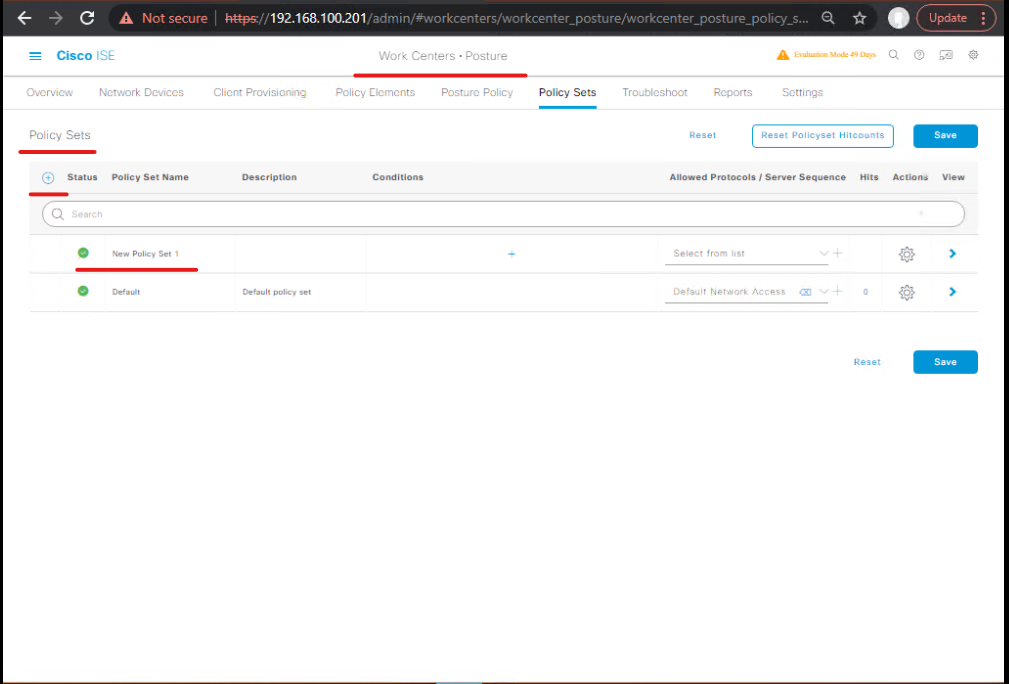
- Create Posture Policy (tie conditions & remediation)
Work Centers → Posture → Policy Sets → Add→ LinkCorp-Baselinecondition toFull-Accesssuccess path and attachRemediationactions to failure path.- [Posture Policy mapping Success/Failure]
VALIDATION (ISE GUI):
Work Centers → Posture → Policydisplays policy with assigned checks.Work Centers → Posture → Reportsshould allow you to run posture simulation tests.- CLI service check (ISE):
show application status ise show logging application ise-psc.log tail 50 - Expected: Posture service running; no posture-service errors in logs.
STEP 2 — Create Authorization Profiles for VPN outcomes
- Create Authorization Profile: Full-Access
- UI:
Policy → Policy Elements → Results → Authorization → Add - Name:
AC-FullAccess - RADIUS AV-pairs: set
Cisco-AVPairto instruct ASA group-policy or setFilter-Idto a named ACL (ACL_VPN_EMPLOYEES). - (Optional) assign SGT or downloadable ACL attributes if environment supports.
- [Create Authorization Profile AC-FullAccess]
- UI:
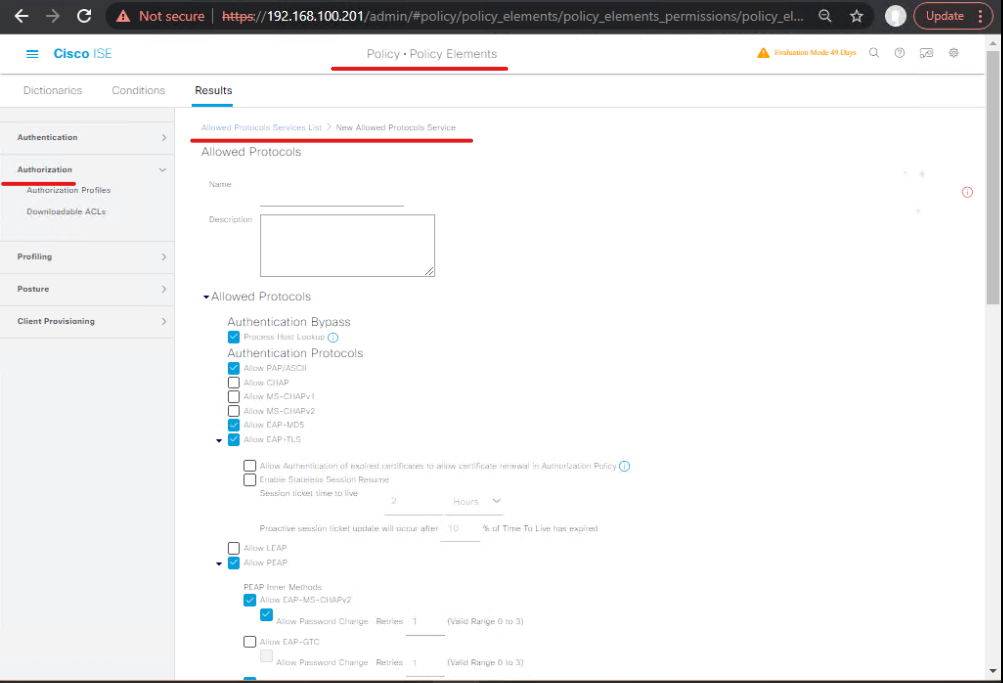
- Create Authorization Profile: Quarantine
- Name:
AC-Quarantine - Attributes:
Filter-Id = ACL_QUARANTINEorCisco-AVPairmapping toGPolicy_Quarantine. - [AC-Quarantine]
- Name:
- Create Authorization Profile: Remediation Pending (if you want limited network to download patches).
- Attributes: ACL limiting to remediation servers only.
- [AC-Remediation]
VALIDATION (ISE GUI & CLI):
- Ensure profiles appear:
Policy → Policy Elements → Authorization. - CLI:
show running-config ise | include Authorization(or review via GUI export). - Confirm attributes are correct in UI (AVPairs/Filter-Id).
STEP 3 — Add Network Device (ASA) and RADIUS secret in ISE
- ISE GUI:
Administration → Network Resources → Network Devices → Add- Name:
ASA-AnyConnect - IP(s): ASA internal interface or management IP (or add ASA group).
- Shared secret:
MyRadKey(must match ASA). EnableRADIUS Authenticationcheckbox. - Assign Network Device Group (e.g.,
VPN Devices). - [Add ASA to ISE]
- Name:
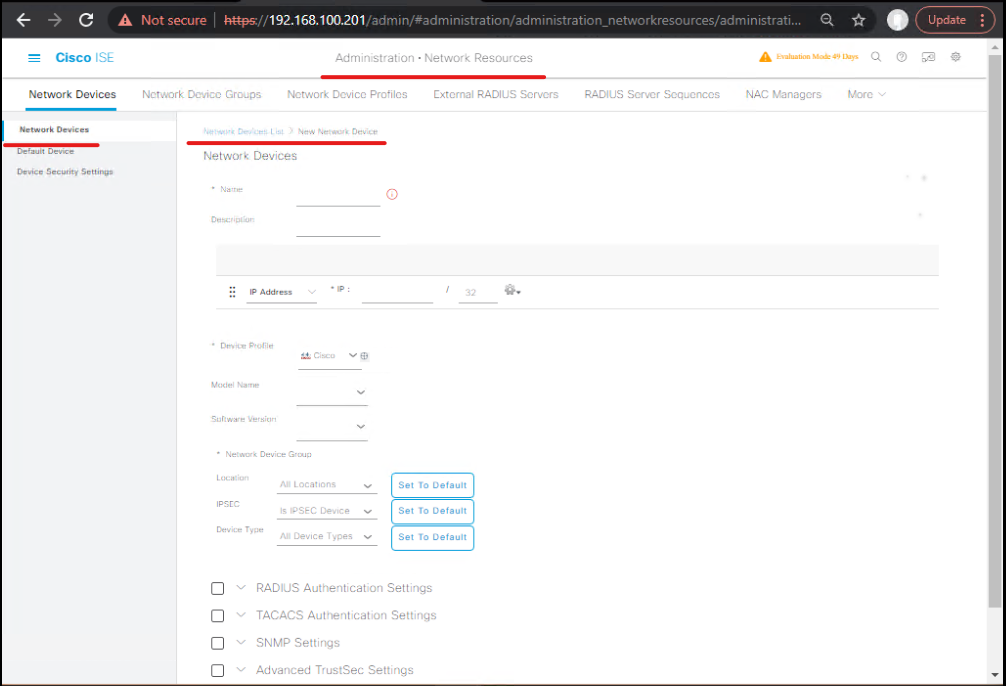
- Validation (ISE GUI): Verify device appears in list and that the Reachability test (if available) succeeds.
ASA CLI to check connectivity:
# show current AAA server status (later after ASA config) show aaa-server ISE-RADIUS
STEP 4 — Configure ASA for AnyConnect + Posture + RADIUS
Two parts: AnyConnect (VPN) basics + posture enablement.
- Upload AnyConnect packages to ASA (if hosting posture agent via ASA webvpn) — use ASDM or CLI.
- ASDM / CLI: upload
anyconnect-win-x.x.x-k9.pkgand posture module if hosting.
- ASDM / CLI: upload
- Configure RADIUS server group on ASA (CLI):
aaa-server ISE-RADIUS protocol radius aaa-server ISE-RADIUS host 10.10.10.15 key MyRadKey timeout 10
- Configure Tunnel-Group and Group-Policy (example):
group-policy GPolicy_Employees internal group-policy GPolicy_Employees attributes split-tunnel-policy tunnelspecified split-tunnel-network-list value SPLIT_TUNNEL_LIST tunnel-group AnyConnect-VPN general-attributes address-pool VPN_POOL default-group-policy GPolicy_Employees tunnel-group AnyConnect-VPN webvpn-attributes authentication-server-group ISE-RADIUS
- Posture / AnyConnect settings on ASA
- If ASA hosts posture: configure webvpn posture to allow download URLs and enable posture chaining. (If using ISE-hosted posture download, ensure ASA allows redirect). This step is typically done in ASDM under AnyConnect > AnyConnect Client Profiles or Configuration > Remote Access VPN.
- Ensure ASA allows posture traffic to/from ISE / remediation servers (ACLs).
VALIDATION (ASA CLI):
show aaa-server ISE-RADIUS show running-config tunnel-group AnyConnect-VPN show webvpn
- Expected: AAA server listed and reachable (after network is configured), default group-policy present.
STEP 5 — Wire ISE Posture into the Policy Set (Authentication & Authorization)
- ISE GUI: Policy → Policy Sets → Create or edit the VPN policy set (e.g.,
ASA-AnyConnect-Policy).- Condition: Network Device =
ASA-AnyConnect(or NDG). - Authentication: EAP (if using certificate or AD), or PEAP for username/password.
- Authorization: Add rules:
- If
Posture = Compliant→ Authorization Profile =AC-FullAccess. - If
Posture = NonCompliant&Remediation possible→ Authorization Profile =AC-Remediation. - Else →
AC-Quarantine.
- If
- [Policy Set Authorization rules]
- Condition: Network Device =
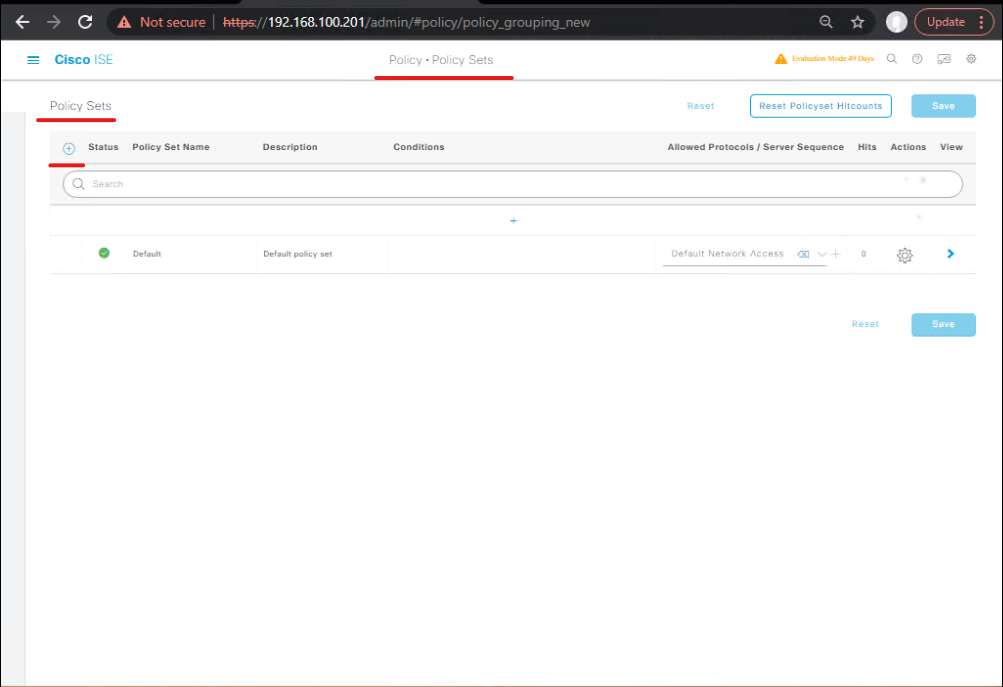
- Validation (ISE Live Logs)
- After a test connect, visit
Operations → RADIUS → Live Logsand observe Access-Request / Access-Accept and the authorization profile applied. The live log shows whether posture was invoked and the result.
- After a test connect, visit
ISE CLI (service status):
show application status ise show logging application ise-psc.log tail 100
STEP 6 — Client Workflow Tests (Compliant vs Non-Compliant)
Prepare three test scenarios: COMPLIANT, NON-COMPLIANT (remediable), NON-COMPLIANT (unremediable).
Test A — Compliant device (expected: full VPN access)
- Ensure Windows client has corporate posture (AV enabled, firewall on, latest patches).
- Connect AnyConnect to ASA. Authenticate.
- Validation:
- ISE Live Logs: Access-Accept, Authorization Profile
AC-FullAccess. [ISE Live Log – FullAccess] - ASA CLI:
show vpn-sessiondb anyconnect detail show vpn-sessiondb detail username <user>Confirm group-policy or ACL applied. [CLI output saved]
- ISE Live Logs: Access-Accept, Authorization Profile
- Network test: Ping internal server(s) defined in split-tunnel or access policy — success.
Test B — Non-Compliant, Remediation Possible (expected: limited access, remediation UI)
- On client, disable AV or cause a registry noncompliance condition.
- Connect AnyConnect; posture triggers; ISE returns
AC-Remediation. - AnyConnect displays remediation portal or instructions (via posture module).
- Actions: Apply remediation (install AV patch) or click remediation link.
- After remediation, ISE may reauthorize (CoA) or user reauthenticates.
- Validation:
- ISE Live Logs: show Posture result = NonCompliant then Remediation Succeeded; second authorization =
AC-FullAccess. [ISE Live Logs – Remediation] - ASA CLI: show session change / new group-policy.
- ISE Live Logs: show Posture result = NonCompliant then Remediation Succeeded; second authorization =
Test C — Non-Compliant, Unremediable (expected: Quarantine)
- Make device fail a non-remediable check (e.g., banned OS).
- Connect; ISE returns
AC-Quarantine. - Client limited to remediation servers or blocked per quarantine ACL.
- Validation:
- ISE Live Logs show Quarantine; ASA applied
ACL_QUARANTINE. show ip access-lists | include ACL_QUARANTINEon ASA to see hits.
- ISE Live Logs show Quarantine; ASA applied
STEP 7 — CoA / Change of Authorization (post-connect)
- From ISE GUI:
Operations → Live Sessions→ locate session →Change Authorization→ chooseAC-QuarantineorAC-FullAccess.- [ISE Change Authorization UI]
- Validation (ASA CLI):
show vpn-sessiondb anyconnect detail username <user> # Check if group-policy/acl updated show log | include CoA
- Expected: ASA receives CoA and applies new group-policy / ACL; client capabilities change without reconnect.
STEP 8 — Accounting / Logging / Evidence capture
Collect these artifacts for each test:
- ISE Live Log (Auth request, posture status, authorization profile).
- ASA
show vpn-sessiondb anyconnect detailoutputs saved. - ASA
show aaa-server ISE-RADIUSoutput. - AnyConnect client (posture prompts, remediation screen).
- Time-stamped CSV test matrix (see Evidence template below).
Evidence Pack Template (CSV columns)TestCase,StartTS,EndTS,ClientHostname,User,ISE_Log_File,ASA_Session_File,Client_Screenshot,Result,Notes
Acceptance Criteria (must be PASS)
- Compliant device receives
AC-FullAccessand can reach internal resources. - Non-compliant remediable device receives
AC-Remediation, can download fixes, then promoted to FullAccess. - Non-compliant unremediable device is quarantined (limited network ACL applied).
- CoA changes take effect within policy SLA (documented).
Expert-Level Use Cases (practical SRE / SOC patterns)
- Automated containment: SIEM detects lateral movement → trigger API to ISE to quarantine the user session via CoA on ASA.
- Continuous posture telemetry: Stream posture results to SIEM via pxGrid for trend analysis and compliance reporting.
- Just-in-Time access: Grant temporary elevated access post-remediation for specific business tasks with automatic expiry.
- Patch gating: Only allow access to patch servers until remediation completes (remediate then CoA to full access).
- EDR integration: If EDR flags a threat, push to ISE to revoke VPN access or move to quarantine SGT.
- Zero-Trust remote access: Combine posture + certificate + AD groups to implement least-privilege remote access.
- Automated agent distribution: Use SCCM/Intune to push posture agent, with ISE verifying installation before granting access.
- Multitenant posture orchestration: For MSSPs, create tenant-specific posture profiles and remediation portals per customer.
- Cloud posture for SaaS: Posture check before allowing access to sensitive SaaS applications via split-tunnel policy + group-policy enforcement.
- DR posture mode: In outages, switch posture to “monitor-only” mode and capture posture stats for later compliance audits.
FAQs – Cisco ISE AnyConnect Posture Enforcement for Remote Users
1. What’s the difference between AnyConnect Posture and NAC Agent?
- Answer: Cisco has deprecated the NAC Agent; AnyConnect (now Secure Client) Posture Module is the standard. It supports more OS types, integrates seamlessly with ISE, and allows more granular posture checks (AV, firewall, disk encryption, etc.).
- Validation: In ISE Work Centers → Posture → Client Provisioning, confirm “AnyConnect Posture Agent” package is uploaded.
- CLI Check (ASA):
show vpn-sessiondb detail anyconnect→ Look for Posture Status: Compliant/Non-Compliant.
2. Do I need separate AnyConnect licenses for Posture?
- Answer: Yes. You need AnyConnect Plus or Apex licenses depending on feature set. For Posture Enforcement with ISE, Apex is required.
- Validation: On ASA or FTD:
show activation-keyEnsure “AnyConnect Apex” is enabled.
3. How does ISE determine if a device is compliant?
- Answer: Through Posture Policies (Work Centers → Posture → Policy Sets). Each rule checks for conditions like antivirus, OS patch level, registry keys, or firewall status. If all required conditions match, the device is marked Compliant. Otherwise, it goes into Non-Compliant and can be redirected.
- Validation: On ISE Live Logs, filter by Posture Status.
4. What happens if a device is non-compliant?
- Answer: ISE can apply:
- Remediation VLAN/ACL (for updates).
- Web redirection to remediation portal.
- Limited access until compliance is met.
- Validation: On ASA, use:
show vpn-sessiondb anyconnect filter name <username>Look for applied Dynamic ACL or VLAN tag.
5. How are Posture Policies pushed to endpoints?
- Answer: Through Client Provisioning Policies. When a user first connects, ISE provisions the AnyConnect Posture module and compliance rules. The agent enforces them locally and reports status to ISE.
- Validation (GUI):
- ISE → Client Provisioning → Verify AnyConnect package & compliance modules uploaded.
- Check endpoint’s log:
C:\ProgramData\Cisco\Cisco AnyConnect Secure Mobility Client\ISEPosture.log.
6. How do I troubleshoot if posture checks are failing?
- Answer:
- Check AnyConnect posture logs on endpoint.
- Validate ASA is redirecting to ISE with correct redirect ACL.
- Check ISE Live Logs → Look for Failure Reason.
- CLI Validation (ASA):
show running-config webvpnEnsureanyconnect module postureis enabled.
7. Can Posture be used for split-tunnel VPNs?
- Answer: Yes, but ensure the ISE posture redirect traffic is excluded from split-tunnel. Otherwise, the agent may fail to communicate with ISE.
- Validation: Check ASA split-tunnel ACL includes ISE PSN IP.
8. How long does posture re-check (reauth) take?
- Answer: Default is 1 hour, configurable in ISE under Posture Settings → Compliance Module. You can set shorter or longer re-check timers depending on security requirements.
- CLI Validation:
show vpn-sessiondb anyconnectLook for “Posture Token Lifetime.”
9. Can I integrate 3rd-party antivirus/firewall checks with ISE posture?
- Answer: Yes. ISE uses OPS (Opportunistic Posture Service) and the Posture Compliance Module which has built-in vendor checks for major AV vendors (McAfee, Symantec, Windows Defender, etc.).
- Validation: ISE → Posture Policies → Conditions → AV checks.
10. What’s the difference between ISE posture and Secure Endpoint (AMP) posture checks?
- Answer:
- ISE Posture: Checks compliance before granting full network access. Reactive and policy-driven.
- Secure Endpoint (AMP/EDR): Provides continuous endpoint monitoring, malware detection, and behavioral analysis. Proactive and threat-driven.
- Best practice: Use both together for layered Zero Trust endpoint security.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes (Key takeaways)
- Posture is a process — design checks that map to real security posture, not vanity metrics.
- Test policies in phases: monitoring → alerting only → remediation → enforcement.
- Collect evidence (ISE Live Logs + ASA session data + client logs) for audits.
- CoA is powerful; use it for dynamic post-connect policy updates after remediation.
- Operationalize posture: run regular posture drills, automate remediation packaging, and integrate posture events into SOC workflows.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro
I run a focused 4 months of hands-on instructor-led CCIE Security training covering ISE, posture, SDA, pxGrid integrations, HA/DR, TrustSec, and more.
Course & enrollment: https://course.networkjourney.com/ccie-security/
Book a discovery call, request the AnyConnect Posture Runbook Pack (templates, CLI snippets, evidence CSV), and reserve your cohort seat.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



