[Day 112] Cisco ISE Mastery Training: FMC Automation via pxGrid
Table of Contents
Introduction
Welcome to Day 112 of the Cisco ISE Mastery Training, where we step into one of the most advanced integrations in the modern Zero-Trust ecosystem — FMC (Firepower Management Center) Automation via pxGrid.
In today’s cyber battlefield, time is your greatest enemy. A malware-infected endpoint or a compromised remote user session can laterally move across your fabric in minutes, sometimes seconds. Security teams often lose precious time chasing alerts across disjointed systems: ISE for identity, FMC for threat prevention, AMP/NGIPS for malware defense. What we need is orchestration, automation, and enforcement at machine speed — and that’s where pxGrid (Platform Exchange Grid) steps in.
With pxGrid, Cisco ISE becomes the nervous system of the enterprise network, feeding contextual identity, posture, and group tag information directly into FMC. FMC, in turn, can automate rapid containment actions — like quarantining endpoints, triggering threat-based ACLs, or pushing security intelligence policies to Firepower Threat Defense (FTD) devices — without waiting for manual admin intervention.
This isn’t just about integration. This is about transforming NAC into a dynamic SOC enforcer, where Cisco ISE + pxGrid + FMC form a closed loop of detection, context, and enforcement. By the end of this session, you won’t just learn how to configure this integration — you’ll understand how to validate it step-by-step in both GUI and CLI, simulate real-world attacks in your lab, and confirm that automated containment is happening at speed and scale.
Problem Statement
- Manual lag between ISE detection and firewall action → long dwell time.
- Siloed tools: ISE knows identity/posture; FMC enforces packets — but no automated bridge.
- Inconsistent triage: Analysts copy IPs into ad-hoc block lists; errors & misses happen.
- Audit gaps: No repeatable, timestamped evidence trail from detection → enforcement.
Target Outcome: Near-real-time, deterministic containment where ISE events auto-translate into FMC policy/object updates, with end-to-end validation and an evidence pack.
Solution Overview
- pxGrid Client (Python / Go / Node) subscribes to ISE topics:
com.cisco.ise.session(user/IP/SGT)com.cisco.ise.identity.endpoint(profiling)com.cisco.ise.posture(compliant/non-compliant)com.cisco.ise.config.ancpolicy&anc.endpoint(quarantine)
- On event, automation calls FMC REST API to:
- Add IP into Network Group
ISE_QUARANTINE_IPS. - (Option) Append to Security Intelligence Network list.
- (Option) Toggle a block rule or override policy.
- Deploy to targeted FTD(s).
- Add IP into Network Group
- Evidence captured at each hop: ISE Live Logs, pxGrid client log, FMC API responses, deployment job IDs, FTD event hits.
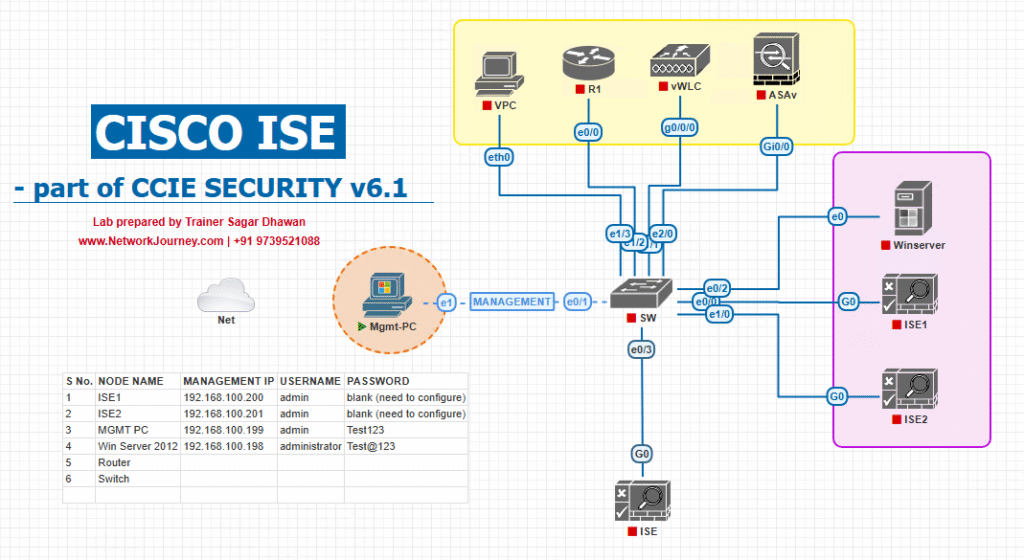
Sample Lab Topology (VMware/EVE-NG)
Nodes
- ISE cluster: PAN/MnT + PSN1/PSN2 (VMware)
- FMC (VM or physical), FTDv-01 and FTDv-02 (EVE-NG/VMware)
- AD/DNS/NTP/PKI (Windows Server)
- Automation VM (Ubuntu): pxGrid client + FMC API scripts
- Test clients: Windows 11 (AnyConnect), Ubuntu host
Topology Diagram:
Assumptions
- DNS/NTP aligned; mutual CA trust between ISE ↔ pxGrid client, and FMC ↔ client.
- FMC manages FTDv-01/FTDv-02; ACP has a top rule referencing group ISE_QUARANTINE_IPS.
Step-by-Step GUI Configuration Guide
PRECHECKS — Hard Gate (must pass)
Checklist
- DNS A/PTR for
ise-pan.lab,fmc.lab,automation.lab - NTP sources identical on ISE/FMC/FTD/Automation VM
- PKI: ISE pxGrid certs & CA chain, FMC HTTPS cert trusted by client
- ISE pxGrid enabled; ERS optional
- FMC admin with API rights; domain UUID known
CLI (Automation VM)
nslookup ise-pan.lab && nslookup fmc.lab curl -k https://fmc.lab/api/fmc_platform/v1/info -I openssl s_client -connect ise-pan.lab:8910 -showcerts </dev/null 2>/dev/null | openssl x509 -noout -subject -issuer
STEP 1 — ISE: Enable pxGrid & Approve pxGrid Client
- Enable pxGrid
- ISE GUI:
Administration → System → Settings → pxGrid Services→ Enable & Start.
- ISE GUI:
- Certificates
- ISE GUI:
Administration → System → Certificates → System Certificates→ ensure cert with proper SAN/FQDN for pxGrid. - Export ISE Trusted Certificates chain for your client trust store.
- ISE GUI:
- pxGrid Client Registration (automation VM as client)
- ISE GUI:
Work Centers → pxGrid Services → All Clients→ set Auto-Approve (lab) or keep Manual (prod).
- ISE GUI:
Validation (ISE CLI)
show application status ise show logging application pxgrid.log tail 100
Expect pxGrid up; no trust errors.
STEP 2 — FMC: Prepare API & Policy Placeholders
- Create Network Group Objects
- FMC GUI:
Objects → Object Management → Network → Network Groups → Add - Name:
ISE_QUARANTINE_IPS(start empty) - Name:
ISE_MONITORED_IPS(optional)
- FMC GUI:
- Access Control Policy rule (identity-agnostic, IP-based block for speed)
- FMC GUI:
Policies → Access Control → <Your ACP> → Add Rule- Name:
ISE_QUARANTINE_BLOCK - Source Networks:
ISE_QUARANTINE_IPS - Action: Block (or “Trust → next rule deny” if you prefer)
- Logging: Log at beginning + end
- Name:
- Move rule to top (above general allows).
- FMC GUI:
- (Optional) Security Intelligence (SI) Network block
Policies → Access Control → Security Intelligence→ add Network ListISE_SI_BLOCK_FEED(you can update this list via API too).
- Deploy to FTDs
- FMC GUI:
Deploy → Deploy Now→ select FTDv-01/02.
- FMC GUI:
Validation (FMC API, get Domain UUID & objects)
# Get token curl -k -u admin:Pass https://fmc.lab/api/fmc_platform/v1/auth/generatetoken -i # Save X-auth-access-token from headers into $TOK # Get domain UUID curl -k -H "X-auth-access-token: $TOK" https://fmc.lab/api/fmc_platform/v1/info/domain # List network groups curl -k -H "X-auth-access-token: $TOK" \ "https://fmc.lab/api/fmc_config/v1/domain/<DOMAIN_UUID>/object/networkgroups?expanded=true"
STEP 3 — Automation VM: Build pxGrid Client (subscribe to ISE events)
Goal: Subscribe to Session & ANC/Posture topics and log events with user/IP/host posture.
Python (structure)
# pxgrid_client.py (excerpt) # Requires: requests, websocket-client, certs in ./certs/ PXGRID_HOST = "ise-pan.lab" NODE_NAME = "pxgrid-fmc-automation" CLIENT_CERT = "./certs/client.crt" CLIENT_KEY = "./certs/client.key" CA_CERT = "./certs/ise-ca.crt" TOPICS = [ "com.cisco.ise.session", "com.cisco.ise.posture", "com.cisco.ise.config.ancendpoint" ] # 1) Register client & get services (accessSecret, nodeName) via pxGrid REST # 2) Use returned WebSocket URL for each topic; present certs; receive JSON events # 3) Parse IP, username, posture/compliance, ancStatus # 4) Call FMC API function (see Step 4) to add/remove IP in ISE_QUARANTINE_IPS
Run & Validate
python3 pxgrid_client.py # Expect: Connected to pxGrid, subscribed to topics... # Incoming event logs printed to console/file with timestamp.
STEP 4 — Automation VM: Build FMC API functions (add/remove IP; deploy)
Create/Update Host Object, add to Group, Deploy
# Create a Host object (idempotent by name)
curl -k -H "X-auth-access-token: $TOK" -H "Content-Type: application/json" \
-X POST "https://fmc.lab/api/fmc_config/v1/domain/<DOMAIN_UUID>/object/hosts" \
-d '{"name":"ISEQ_10.10.10.25","value":"10.10.10.25","type":"Host"}'
# Get Network Group details for ISE_QUARANTINE_IPS (to obtain id and current members)
curl -k -H "X-auth-access-token: $TOK" \
"https://fmc.lab/api/fmc_config/v1/domain/<DOMAIN_UUID>/object/networkgroups?name=ISE_QUARANTINE_IPS"
# Update Network Group: append host object reference
curl -k -H "X-auth-access-token: $TOK" -H "Content-Type: application/json" \
-X PUT "https://fmc.lab/api/fmc_config/v1/domain/<DOMAIN_UUID>/object/networkgroups/<GROUP_ID>" \
-d '{"id":"<GROUP_ID>","name":"ISE_QUARANTINE_IPS","literals":[],"objects":[
{"type":"Host","id":"<HOST_ID>"}]}'
# Trigger Deployment to specific devices (v6.7+ API path sample; adjust to your version)
curl -k -H "X-auth-access-token: $TOK" -H "Content-Type: application/json" \
-X POST "https://fmc.lab/api/fmc_config/v1/domain/<DOMAIN_UUID>/deployment/deployments" \
-d '{"type":"DeploymentRequest","forceDeploy":true,"ignoreWarning":true,
"version":"1.0","name":"ISE_AutoDeploy",
"devices":[{"id":"<FTD_DEVICE_ID>"}]}'
STEP 5 — ISE: Create ANC Policy (Quarantine) & Test Triggers
- ISE ANC Policy
- ISE GUI:
Operations → Active Sessions → ANC(orPolicy → Policy Elements → Results → ANC) - Create Policy:
QUARANTINE
- ISE GUI:
- Test ANC Apply
- ISE GUI:
Operations → Active Sessions→ select the endpoint → Apply ANC Policy =QUARANTINE. - pxGrid Client should receive
ancendpointevent with endpoint IP/MAC.
- ISE GUI:
Validation (Automation Log)
- See event consumed → IP added to
ISE_QUARANTINE_IPSvia FMC API → deployment triggered.
STEP 6 — FMC: Confirm Object Update, Rule Hit & Deployment
- Objects
- FMC GUI:
Objects → Network Groups → ISE_QUARANTINE_IPScontains new host(s).
- FMC GUI:
- Deployment Jobs
- FMC GUI:
System → Monitoring → Deployments→ job Success.
- FMC GUI:
- Policy Hit
- FMC GUI:
Analysis → Connections → Events— filter by quarantined IP → expect Blocked by ruleISE_QUARANTINE_BLOCK.
- FMC GUI:
FTD CLI (diagnostic)
system support diagnostic-cli show access-control-config | i ISEQ show conn | include 10.10.10.25 exit
Capture outputs for evidence.
STEP 7 — Auto-Unquarantine (Revert Flow)
- When ISE clears ANC or endpoint becomes Compliant, your pxGrid client should:
- Remove IP from
ISE_QUARANTINE_IPSgroup (FMC API), - Trigger Deploy,
- Log recovery event.
- Remove IP from
Validation
- FMC object shows IP removed; new deploy job; endpoint traffic shifts from Blocked to Allowed (per baseline rules).
STEP 8 — Hardening & Reliability
Checklist
- pxGrid client mutual TLS, key permissions
0600. - Retry with exponential backoff on FMC 429/5xx.
- Idempotency: don’t duplicate host names; prefer
ISEQ_<IP>. - Rate-limit deployments; batch updates within a short window (e.g., 30–60s).
- Health probes: cron job to GET
networkgroups& verify membership <> rules hit. - Logging: timestamped JSON logs + evidence CSV.
STEP 9 — Evidence Pack Template
Files to collect (per test):
ise_live_log_<ts>.png,anc_apply_<ts>.pngpxgrid_console_<ts>.txtfmc_api_create_host_<ts>.json,fmc_api_update_group_<ts>.jsonfmc_deploy_job_<ts>.jsonfmc_events_<ts>.csvftd_diag_<ts>.txt
CSV Format
Case,Start,End,User,IP,Trigger,Action,FMCJobID,FTDDevice,Result,Notes
Expert-Level Use Cases
- Malware IOC autoblocker: pxGrid client also ingests SIEM IOC feed → adds matching IPs to
ISE_SI_BLOCK_FEEDin FMC; logs job ID & reason code. - Adaptive posture ring-fence: When posture flips to Non-Compliant, move IP to
ISE_QUARANTINE_IPS; when Compliant, auto-remove + deploy; all changes annotated with user/host. - Conditional privilege access: ISE marks admins with
SGT=Privileged; automation inserts a time-boxed “Allow Admin → Jump-Host” rule; cron job auto-reverts. - Lateral movement throttle: On multiple auth failures (ISE), automation raises a rate-limit rule or IPS policy override for that source until cleared.
- BYOD suppression window: Profiling detects IoT/BYOD; automation assigns Restricted-IoT object; ACP allows only specific destinations/ports; posture compliance expands access.
- Geo/IP surge block: ISE/Threat intel surge triggers SI country block overlay (if licensed) or dynamic object with offending ranges; expire after N minutes.
- Tenant-aware enforcement: Multi-domain FMC: map ISE NDGs → FMC domains; pxGrid client dispatches updates to the right domain/device fleet automatically.
- SOAR closed-loop: SOAR confirms containment in FMC, then calls ISE ANC Clear via ERS; pxGrid event confirms; script removes IP from quarantine group and redeploys.
- Maintenance freeze guard: During change freeze, script flips to SI list mode only (no ACP structure changes) — still enabling containment without full deployments.
- Deception trigger: Honeypot hit → pxGrid client tags source in ISE (ERS) as
Suspect→ FMC receives event → auto-block & open case in ITSM with evidence bundle.
FAQs: FMC Automation via pxGrid
1. What exactly is pxGrid and why is it critical for FMC integration?
- Answer: pxGrid (Platform Exchange Grid) is Cisco’s open, publish-subscribe based information exchange framework. ISE publishes contextual identity/session info (username, IP, MAC, SGT, posture, device type) and FMC subscribes to this data for dynamic security enforcement.
- Without pxGrid, FMC cannot dynamically map security intelligence with who/what/where in your network, making automated containment impossible.
2. What licenses are required on ISE and FMC for pxGrid integration?
- ISE: You need the Plus license (or higher, like Apex) for pxGrid functionality.
- FMC: Requires Control + Threat licenses (for FMC-FTD policy control) and Integration module for pxGrid.
- Validation Tip: In ISE → Administration > Licensing, confirm “pxGrid Services” is enabled. In FMC → System > Integration, check that Cisco ISE Integration appears.
3. How do I validate pxGrid connectivity between ISE and FMC?
- GUI Validation:
- On ISE → Administration > pxGrid Services > Clients, you should see FMC listed as a pxGrid client.
- On FMC → Integration > Identity Sources > ISE, status should show Connected.
- CLI Validation:
- On ISE:
show logging application pxgrid→ look for FMC session join events. - On FMC CLI (FTD):
show identity status→ confirms FMC is consuming pxGrid context.
- On ISE:
4. What kind of contextual data does ISE actually send to FMC via pxGrid?
- Username, IP, MAC address, VLAN, Endpoint Posture (compliant/non-compliant), Device Type, Security Group Tags (SGTs).
- Example: If a user logs in via AnyConnect, FMC can now enforce rules like “Deny non-compliant HR endpoints from accessing Finance servers.”
5. How do I configure FMC to use pxGrid session data in policies?
- In FMC → Policies > Access Control > Identity Rules.
- Create a rule matching SGT/username/device type from pxGrid feed.
- Validation: Test traffic from an endpoint → FMC dashboard → Analysis > Users should resolve identity info.
6. What happens if pxGrid connection breaks between ISE and FMC?
- FMC will stop receiving live identity updates. Existing sessions may persist but new logins won’t map identities.
- Troubleshooting:
- Check pxGrid services on ISE:
application stop pxgrid && application start pxgrid. - Restart integration on FMC: Integration > Identity Sources > Cisco ISE > Test Connection.
- Check pxGrid services on ISE:
7. How can I simulate and test automated endpoint quarantine?
- From ISE → Context Visibility > Endpoints > Actions > Change Authorization (CoA) → select “Quarantine”.
- FMC will consume pxGrid update and enforce access restrictions (via ACP or Dynamic ACLs).
- Validation CLI: On FTD CLI →
show conn→ verify dropped connections for quarantined endpoint.
8. What are common pxGrid troubleshooting commands?
- ISE CLI:
show application status ise(check pxGrid status).show logging application pxgrid(look for FMC client errors).
- FMC CLI (FTD):
system support firewall-engine-debug(check policy hits).show identity(ensure pxGrid identity mappings are being used).
9. Can FMC use pxGrid SGT information directly in firewall rules?
- Yes — FMC supports SGT-based firewall policies when integrated with ISE.
- Example: Allow SGT: HR_Users → Finance_DB, Deny SGT: Guest → Internal_Servers.
- Validation: In FMC policy hit counts → confirm rule with SGT match is triggered.
10. What’s the difference between pxGrid and pxGrid2 in ISE 3.x?
- pxGrid (legacy): SOAP-based, limited scalability.
- pxGrid2: REST/JSON-based, faster, more scalable, supports modern API integrations (like Cisco Threat Response).
- Pro Tip: Always enable pxGrid2 in ISE 3.x labs to future-proof integrations.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes (Ops-ready Takeaways)
- Build the event bridge once; reuse for posture, profiling, malware and SIEM detections.
- Pre-stage ACP rules & objects so automation only mutates group membership.
- Treat this as production software: MTLS, retries, logging, metrics, and roll-back logic.
- Keep an evidence pack routine — it wins audits and speeds RCA.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to Network Journey on YouTube and join my instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro
I run a focused 4-month instructor-led CCIE Security program (ISE, pxGrid, TrustSec/SGT, FMC/FTD, SDA, HA/DR, Advanced Automation).
Course outline & enrollment: https://course.networkjourney.com/ccie-security/
Book your slot, get the automation code pack, lab topologies, and weekly live troubleshooting drills.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088


![[Day 41] Cisco ISE Mastery Training: Wireless 802.1X Authentication Overview](https://networkjourney.com/wp-content/uploads/2025/08/Day-41-Cisco-ISE-Mastery-Training-Wireless-802.1X-Authentication-Overview.png)
