[Day 113] Cisco ISE Mastery Training: Integration with Cisco Umbrella
Table of Contents
Introduction
In modern enterprise networks, visibility and control stop at the perimeter if identity and DNS security are not tightly integrated. Cisco Identity Services Engine (ISE) provides context-rich, identity-based access control inside your network, but what happens once the user leaves the enterprise perimeter or connects via unsecured networks? This is where Cisco Umbrella, Cisco’s cloud-native Secure Internet Gateway (SIG), comes into play.
By integrating Cisco ISE with Cisco Umbrella, we extend zero-trust enforcement beyond the LAN/WLAN into the cloud and the internet. Think of it as taking ISE’s policy engine and Umbrella’s DNS-layer security, and merging them into a unified enforcement fabric.
This integration is not just about security alerts or visibility. It allows enterprises to:
- Dynamically map user and device identity (from ISE) with DNS-layer enforcement (via Umbrella).
- Enforce conditional internet access policies (e.g., block risky domains unless posture-verified).
- Enable real-time threat response automation (e.g., quarantine a compromised endpoint by changing its Umbrella policy, triggered by ISE).
- Provide consistent protection for roaming users — whether they’re inside the corporate LAN, on public Wi-Fi, or remote via VPN split-tunneling.
In other words: ISE + Umbrella integration closes the enforcement gap. Without it, security is blind once traffic leaves the enterprise edge. With it, your security posture is continuous, everywhere, identity-driven, and cloud-extended.
This makes Day 113 critical in your Cisco ISE Mastery journey because it demonstrates how cloud-delivered security and NAC policies converge to protect hybrid workforces.
Problem Statement
Security teams need to:
- Enforce DNS/SWG policy on every device (LAN, VPN, off-net).
- Tie Umbrella policy to who/what (user/endpoint posture/identity), not just IPs.
- Avoid brittle PAC/VPN dependency for web controls.
- Prove enforcement & compliance in seconds, not hours.
Solution Overview (What you will configure now)
- Endpoint enforcement (everywhere): Push Cisco Secure Client – Umbrella module via ISE client provisioning using the OrgInfo.json profile from the Umbrella dashboard. Validate local protection in the client UI and Umbrella reports. (Cisco)
- Network-side DNS control (on-prem):
- Option A: ISE authorization with dACL to allow only DNS to Umbrella resolvers/VA and block direct DNS. (docs.sse.cisco.com)
- Option B (Catalyst 9k): Switch-native Umbrella integration (
umbrella in) with org/API credentials; ISE still provides 802.1X/MAB authorization. (Cisco)
- Cloud identity sharing: Connect ISE ↔ pxGrid Cloud ↔ Cisco Secure Access (Umbrella) so Umbrella sees ISE identity/endpoint signals for policy & visibility. (docs.sse.cisco.com)
Sample Lab Topology
Virtualization: VMware ESXi (or EVE-NG for switches/WLC).
Security/NAC: ISE 3.2+ (PAN/PSN on one node for lab).
Access: 1× Catalyst 9300 (16.12+/17.x) as access switch; 1× WLC9800-CL; 1× AP.
Clients:
- Win 11 (corporate image) with Cisco Secure Client 5.x (Umbrella module),
- macOS 14 with Secure Client Umbrella module,
- BYOD phone (optional).
Umbrella/SSE: Umbrella org (SSE portal), 2× Umbrella Virtual Appliances (VAs) on ESXi for on-prem DNS (optional but recommended). (docs.sse.cisco.com)
Diagram (text description):
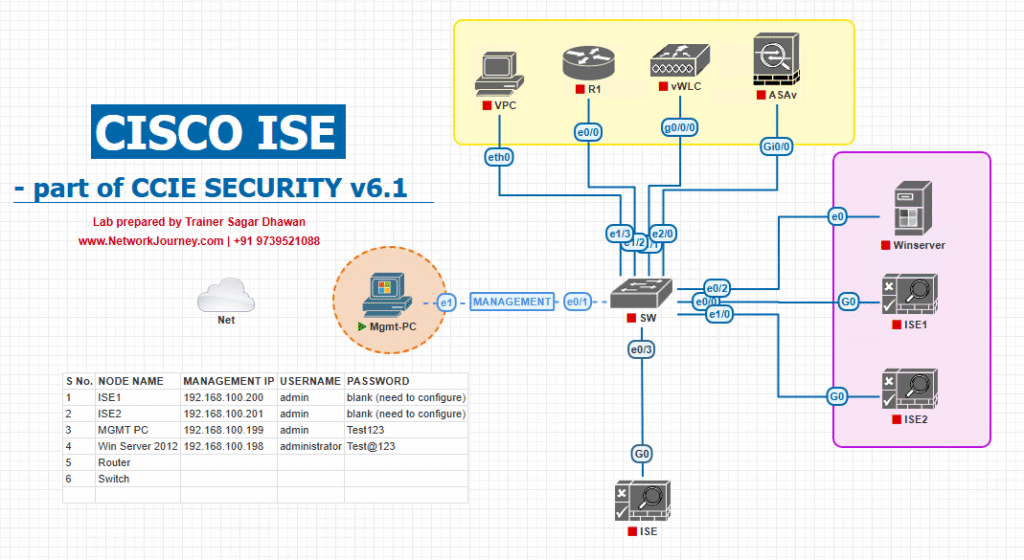
- Users → Access (Cat9k) → Core → Internet.
- ISE PSN inline with RADIUS (802.1X/MAB) from Cat9k/WLC.
- Umbrella:
- Endpoint path: Secure Client Umbrella module intercepts DNS → Umbrella resolvers/SWG.
- On-prem path: Cat9k “umbrella in” and/or ISE dACL forces DNS to VA pair → Umbrella cloud.
- pxGrid Cloud: ISE publishes context → Cisco Secure Access (Umbrella).
[Diagram Placeholder: ISE + Cat9k + VA + SSE/ Umbrella flow]
Step-by-Step GUI & CLI Configuration Guide
A) Umbrella Org Prep & Packages
- In Umbrella/SSE dashboard:
- Go to Identities > Roaming Computers → + → download Umbrella Roaming Security Module Profile (OrgInfo.json). Keep it handy. (Cisco)
- (If using VAs) Deploy two VAs (vCPU/RAM per doc), record IPs, complete registration. (docs.sse.cisco.com)
- Firewall prep (optional but recommended): Allow encrypted DNS to Umbrella (TCP/UDP 443) and classic resolvers 208.67.222.222 / 208.67.220.220 as needed. (docs.sse.cisco.com, Cisco Umbrella Documentation)
Validation
- Umbrella: Activity Search should show queries after clients come online (post-deployment). Initial check-in may take up to ~90–120 minutes for new Roaming Computer entries. (Cisco)
- Network: From a client,
curl https://1.1.1.1/cdn-cgi/trace(to confirm egress) then verify DNS queries appear in Umbrella Reports → Activity Search.
B) ISE: Upload Secure Client + Umbrella Module + OrgInfo.json
What you need:
- Cisco Secure Client 5.x packages (Win/macOS) with Umbrella module.
- The OrgInfo.json you downloaded.
Steps (ISE 3.x GUI):
- Administration > Client Provisioning > Resources → Add → Agent Resources.
- Upload Cisco Secure Client package(s) (Windows
.pkg/.msi, macOS.dmg/pkg). - Upload Umbrella module package(s).
- Upload OrgInfo.json but rename to
OrgInfo.xmlbefore upload (per Cisco guide). Map this as AnyConnect Umbrella profile for client provisioning. (Cisco) - Client Provisioning > Client Provisioning Policy:
- Create policy: If OS = Windows 10/11 (and/or macOS) THEN install Secure Client + Umbrella module + OrgInfo profile.
Validation
- ISE Live Logs: Operations > RADIUS > Live Logs, look for
Client-Provisioningredirection then success.- Endpoint (Windows): Open Cisco Secure Client UI → Umbrella Roaming Security tile should show Protected once registered. (SWG status codes & paths documented).
- File presence (common path; may vary by version):
- Win:
C:\ProgramData\Cisco\Cisco Secure Client\Umbrella\containsOrgInfo.json(or in anumbrella\datafolder as documented).- macOS:
/opt/cisco/anyconnect/umbrella/…(SWG config path in doc; OrgInfo lives under Umbrella data subfolder).
C) ISE Posture (Optional but Powerful): Enforce “Umbrella Installed & Active”
- Work Centers > Posture > Requirements → Add requirement “Umbrella Module Present & Registered”.
- Check file existence for
OrgInfo.jsonin the Umbrella data folder (Win/macOS). - Optionally check process/service is running (e.g., Umbrella agent).
- Check file existence for
- Work Centers > Posture > Policies: create posture rule → Compliant only if Umbrella checks pass; Non-Compliant → remediate or quarantine.
- Policy Sets: add authorization rules: If Posture = Compliant ⇒ full access; If Non-Compliant ⇒ limited access / remediation VLAN.
Validation
- Live Logs posture column (three-dot menu) → Agentless Posture Troubleshooting for details.
- Troubleshoot posture status if mismatched (common causes documented).
D) Network-Side Enforcement with ISE dACL (DNS Steering to Umbrella)
Goal: Force on-prem clients to use Umbrella resolvers (cloud or VA IPs), block all other DNS.
- ISE > Policy Elements > Results > Authorization > Downloadable ACLs (dACLs) → Add
DACL-UMB-DNS-ONLY:remark Allow DNS to Umbrella (encrypted & classic) permit udp any host 208.67.222.222 eq 53 permit udp any host 208.67.220.220 eq 53 permit tcp any host 208.67.222.222 eq 443 permit tcp any host 208.67.220.220 eq 443 ! If using VA pair (recommended), replace/add these: permit udp any host <VA1_IP> eq 53 permit udp any host <VA2_IP> eq 53 ! Allow DHCP/DNS to infra as needed permit udp any any eq 67 permit icmp any any deny ip any any(Adjust to your policy; include DNS-over-TLS/HTTPS if applicable to your Umbrella plan.) (docs.sse.cisco.com) - Authorization Profile
AUTH-UMB-DNS: apply the dACL. - Policy Set rule: “If Wired_802.1X AND Corp-Endpoints THEN
AUTH-UMB-DNS.”
Validation
- Client:
ipconfig /flushdnsthennslookup example.com→ resolver should be Umbrella/VA.- Umbrella Activity Search should show the client’s queries. (Cisco)
E) Catalyst 9k Native Umbrella Integration (Alternative/Complement)
Use when you want switch-enforced DNS redirection & device identity registration directly with Umbrella (still keep ISE for 802.1X authorization).
Cat9k CLI (example):
! Global Umbrella parameter-map with org credentials parameter-map type umbrella global organization-id <ORG_ID> token <REG_TOKEN> api-key <API_KEY> secret <API_SECRET> crypto ca-trustpoint <TRUSTPOINT> ! if using custom CA umbrella device-id C9300-ACC-01 umbrella source-interface Vlan10 ! mgmt/source to Umbrella ! ip name-server 208.67.222.222 ip name-server 208.67.220.220 ! interface GigabitEthernet1/0/10 description User_Port_A umbrella in spanning-tree portfast ! ! (802.1X/MAB/CTS/SGT config omitted for brevity)
Key notes/limitations (from Cisco): SGT/QinQ not supported by switch-Umbrella feature; configure per-interface; see full guide. (Cisco)
Validation (Cat9k):
show umbrella config/show umbrella status/show umbrella statistics(look for registered state & DNS hit counters).- Client
nslookupshows Umbrella path; Umbrella Activity Search populates. (Cisco)
F) ISE ↔ pxGrid Cloud ↔ Cisco Secure Access (Umbrella) Identity Share
Purpose: Let Umbrella consume ISE identity/endpoint context (user, IP, posture state, device attributes) for policy & reporting in Cisco Secure Access.
Steps (ISE GUI & SSE GUI):
- ISE: Administration > pxGrid Services > pxGrid Cloud → Connect.
- Ensure pxGrid services are enabled and ISE trusts a CA suitable for pxGrid Cloud.
- Cisco Secure Access (Umbrella) portal: Integrations > Cisco ISE → Add and follow the connector workflow.
- Back in ISE, approve the pxGrid Cloud connection request if prompted.
- Verify sessions/identities flowing to SSE/Umbrella. (docs.sse.cisco.com)
Validation
- In SSE/Umbrella, check Users/Identities mapped to IPs/hosts.
- In ISE, pxGrid Cloud status shows Connected.
Expert-Level Use Cases
Encrypted DNS standardization: Force DoH/DoT to Umbrella where supported; block opportunistic DoH to public resolvers; posture requires Secure Client Umbrella module enabled. (docs.sse.cisco.com)
Quarantine via DNS: ISE detects high risk posture → assigns dACL that allows only DNS to Umbrella SWG → Umbrella Block-Page carries remediation steps.
SDA + Umbrella: Fabric edge ports authenticated by ISE; DNS steered to VAs inside fabric; SWG user auth from Secure Client; pxGrid Cloud shares identity to Umbrella for correlated reports.
Contractor Kiosk Mode: ISE classifies device as unmanaged → applies DACL-UMB-DNS-ONLY + captive portal to MDM/MDM-less onboarding; Umbrella policy restricts categories and malware.
Branch with SD-WAN: Internet breakout uses Umbrella SIG; on-prem Wi-Fi guest VLAN gets ISE WLC dACL forcing DNS to SIG; Secure Client on corp laptops adds roaming protection off-site.
Just-in-time containment: EDR flags host IOC → feed to ISE (pxGrid/ANC) → ISE pushes restricted dACL; Umbrella denies high-risk destinations; SOC verifies in Umbrella Activity Search.
Adaptive access by role: ISE maps AD groups → pxGrid Cloud → Umbrella applies different DNS/SWG policies by user role/geolocation, visible in unified reporting.
Validation Checklists (GUI + CLI)
Client (Windows/macOS)
- Secure Client UI → Umbrella Roaming Security = Protected. (Cisco)
nslookup whoami.akamai.net→ resolver = Umbrella/VA.- Visit blocked category (per policy) → Umbrella block page.
ISE
- Live Logs show successful auth + applied Authorization Profile (dACL).
- Posture column shows Compliant with your Umbrella checks. (Cisco)
Umbrella/SSE
- Identities → Roaming Computers shows your host(s).
- Reports → Activity Search shows DNS/SWG hits. (Cisco)
- Integrations shows Cisco ISE connector Connected (pxGrid Cloud). (docs.sse.cisco.com)
Catalyst 9k (if used)
show umbrella status show umbrella statistics show umbrella config
Expect Registered/Up state and DNS counters incrementing. (Cisco)
FAQs – Cisco ISE Integration with Cisco Umbrella
FAQ 1: What is the main purpose of integrating Cisco ISE with Cisco Umbrella?
Answer:
The purpose is to extend ISE’s identity-based access control into cloud-delivered DNS-layer security. With integration:
- ISE shares user identity, group, and posture compliance info with Umbrella.
- Umbrella enforces DNS-layer filtering and policy mapping based on that identity.
- Remote or roaming users remain protected even when they are off the corporate LAN/WLAN.
Validation: - In ISE: Navigate to Context Visibility → Endpoints and confirm endpoint group membership.
- In Umbrella Dashboard: Check Activity Search and confirm logs show user identity & policy applied.
FAQ 2: How does ISE actually communicate with Umbrella?
Answer:
Integration is achieved via pxGrid and APIs:
- ISE provides identity context (usernames, AD groups, device posture).
- Umbrella consumes this via ISE-to-Umbrella connector/API for dynamic policy assignment.
- Enforcement happens at the DNS-layer in Umbrella’s resolvers.
Validation: - ISE CLI:
show application status ise→ ensure pxGrid and ERS services are running. - Umbrella Dashboard: Verify ISE is listed as an identity source.
FAQ 3: What licensing is required for this integration?
Answer:
- Cisco ISE: At least Plus (for pxGrid) and possibly Apex (for posture if you want conditional Umbrella enforcement).
- Cisco Umbrella: DNS Essentials is not enough — you need at least Umbrella SIG Advantage (to consume identity info and enforce per-user policies).
Validation: - In ISE: Administration → Licensing to check Plus/Apex license.
- In Umbrella: Admin → Licensing tab.
FAQ 4: How are Umbrella security policies mapped to ISE identities?
Answer:
- You configure Umbrella Security Policies (e.g., block gambling sites, restrict malicious domains).
- ISE endpoint identity groups or AD groups are synced to Umbrella.
- A specific user/device group from ISE can be assigned a corresponding Umbrella policy.
Validation: - ISE GUI: Work Centers → TrustSec → Components → Security Groups.
- Umbrella GUI: Policies → Policy Components → Identities. Confirm groups match.
FAQ 5: How does this help with roaming/off-network users?
Answer:
When a user is remote (home, public Wi-Fi, coffee shop):
- AnyConnect Roaming Security Module or Umbrella roaming client forces DNS queries to Umbrella resolvers.
- ISE identity is still tagged to the device → Umbrella applies same corporate DNS policies as on-prem.
Validation: - CLI on remote endpoint:
nslookup badsite.com→ should return Umbrella block page IP. - Umbrella logs show request tied to user identity from ISE.
FAQ 6: Can I trigger automated threat response between ISE and Umbrella?
Answer:
Yes, using Adaptive Network Control (ANC) + pxGrid:
- If Umbrella flags a device as compromised, it can trigger ISE to quarantine that endpoint.
- Conversely, if ISE detects non-compliance (posture failure), Umbrella can enforce stricter DNS policies.
Validation: - In ISE: Operations → Adaptive Network Control → ANC Policies.
- In Umbrella: Threat response logs show “action: blocked/quarantined.”
FAQ 7: How do I validate the integration is working end-to-end?
Answer:
- Connect a test endpoint to the network (wired/wireless).
- Authenticate via ISE (dot1x/MAB).
- Confirm in ISE logs that identity is tagged.
- From endpoint, browse to blocked category (e.g., gambling).
- Umbrella should redirect to block page.
CLI Validation:
- On endpoint:
nslookup example.com→ verify resolver is Umbrella IP (208.67.x.x). - ISE CLI:
show logging application ise-psc.log→ confirm pxGrid event forwarded.
FAQ 8: What common issues do students/engineers face during this integration?
Answer:
- pxGrid service not enabled in ISE → Umbrella cannot consume identity.
- Incorrect license tier → policies not applied per identity.
- DNS not forced to Umbrella (split-tunnel VPN bypass).
- Endpoint client missing (no roaming client → identity lost off-network).
Quick Fix:
- ISE: enable pxGrid (Administration → pxGrid Services).
- Endpoint: install Umbrella Roaming Module.
- ASA/FTD: configure tunnel all DNS traffic to Umbrella.
FAQ 9: How does integration scale in large enterprises?
Answer:
- pxGrid supports multi-node deployments → Umbrella connects to ISE cluster.
- Umbrella cloud scales globally, so DNS requests are always resolved at nearest data center.
- Policies remain synchronized across all remote offices/users.
Validation: - ISE GUI: System → Deployment → confirm pxGrid is enabled on multiple nodes.
- Umbrella Dashboard: check Activity Search across global users.
FAQ 10: Can I see identity-based reporting in Umbrella after integration?
Answer:
Yes — instead of just showing IP-based queries, Umbrella reports now show:
- Usernames (from ISE/AD).
- Device Groups (from ISE profiling).
- Policy names applied.
Validation: - Umbrella GUI → Reports → Activity Search → filter by username.
- Confirm the identity matches with ISE endpoint report.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- Push the Umbrella module via ISE to standardize enforcement everywhere.
- Use VA pair + ISE dACL or Cat9k umbrella to guarantee on-prem DNS path.
- Wire pxGrid Cloud so Umbrella sees ISE identities and posture.
- Prove it every time: Live Logs, Activity Search,
nslookup, and device CLI.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro:
I run a focused runs a 4-month instructor-led program (CCIE Security-aligned). The course blends ISE, Umbrella/SSE, SDA, FTD/FMC, ASA/RA-VPN, pxGrid automation, posture, and large-scale design, with hands-on labs, graded drills, and design reviews—a complete funnel from fundamentals to expert design/operations.
Reserve your seat & download the detailed outline here: course.networkjourney.com/ccie-security/
Production-ready runbooks, upgrade/migration templates, and war-room troubleshooting patterns you can apply Day-1.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088


![[Day 121] Cisco ISE Mastery Training: Automated Guest User Creation via API](https://networkjourney.com/wp-content/uploads/2025/08/Day-121-Cisco-ISE-Mastery-Training-Automated-Guest-User-Creation-via-API.png)
