[Day 114] Cisco ISE Mastery Training: AMP for Endpoints Threat Mitigation
Table of Contents
Introduction
Welcome to Day 114 of the Cisco ISE Mastery Training Series, where we take a hard, uncompromising look at one of the most critical integrations in modern enterprise security:
Cisco ISE + Cisco AMP (Secure Endpoint) for advanced threat mitigation.
Why does this matter? Because identity without threat context is incomplete. Cisco ISE excels at telling us who is connecting, what device they’re using, and where they’re connecting from. But what happens if that device—despite being authenticated—gets infected with ransomware, a rootkit, or malware that bypassed perimeter defenses? Authentication alone is no longer enough.
This is where Cisco Advanced Malware Protection (AMP) for Endpoints changes the game. AMP goes deep into the endpoint’s behavior—file trajectory, exploit detection, retrospective alerts—and continuously evaluates whether a device is trustworthy. By integrating AMP telemetry directly into Cisco ISE through pxGrid, we elevate NAC from binary access decisions to adaptive, threat-aware enforcement.
Think of this integration as a real-time security feedback loop:
- AMP identifies compromised or high-risk endpoints.
- AMP shares this intelligence with ISE via pxGrid.
- ISE instantly re-evaluates the endpoint session and enforces new policies—quarantine VLANs, restricted ACLs, or outright blocking.
- Security analysts gain visibility and control across the entire fabric, without manual intervention.
In today’s enterprise, where zero-day attacks, advanced persistent threats (APTs), and remote work endpoints blur traditional perimeters, this level of adaptive, dynamic enforcement is not optional—it is mandatory.
This Article isn’t just about turning on an integration. It’s about mastering the operational flow, validating telemetry in both GUI and CLI, and simulating attack scenarios so you understand not just the “how” but the “why” behind every configuration step. By the end, you’ll be able to:
- Configure and validate AMP–ISE integration end-to-end.
- Build adaptive policy sets that respond dynamically to AMP verdicts.
- Use CLI + GUI validation to prove enforcement in real time.
- Simulate threat events to test automated response workflows.
This is not theory. This is battlefield NAC, where endpoints may be authenticated but cannot be trusted unless continuously verified. And with AMP + ISE, you gain the weapons and visibility to enforce real zero-trust security at scale.
Problem Statement
- Security teams detect real malware on managed laptops, but network access remains open until someone manually hunts the switchport/VLAN.
- Containment playbooks are slow and error-prone across wired, wireless, and VPN.
- SOC needs deterministic controls (DACL/SGT/VLAN) applied in-session using RADIUS CoA—with audit trails.
- Endpoint tools can signal compromise, but network enforcement must happen where the attacker moves: the access layer and WLAN controllers.
Solution Overview
- ISE Threat-Centric NAC (TC-NAC) subscribes to Secure Endpoint (AMP) Cloud events (malware detections, file trajectory, etc.). ISE processes those events and exposes a Compromised Endpoints workflow to quarantine with ANC. Vulnerability events support auto-CoA; threat events from AMP are typically actioned via manual ANC or external automation (ERS/Orchestration).
- Adaptive Network Control (ANC) applies enforcement (quarantine DACL, VLAN, SGT) in-session via RADIUS CoA to switches/WLCs. (Cisco)
- ERS/ANC API enables automatic quarantine from SecureX/Orchestration or custom scripts calling
…/ers/config/ancendpoint/apply. (Cisco DevNet, Cisco Live, Postman)
Sample Lab Topology
Platform: VMware ESXi or EVE-NG
ISE: 2 nodes (Primary Admin/Monitoring + PSN), ISE 3.2+ with TC-NAC enabled on the Primary Admin (only one node can run TC-NAC services). ISE Premier license required for TC-NAC.
Secure Endpoint: Cloud Console (US/EU region), Windows 10/11 test host with Secure Endpoint Connector installed.
Switch: Catalyst 9300 (IOS-XE 17.x) as Access Layer.
WLC: C9800-CL (optional WLAN testing).
AD/DNS/NTP: Two services VMs.
AnyConnect (optional): for VPN/Posture cross-validation.
Topology Diagram:
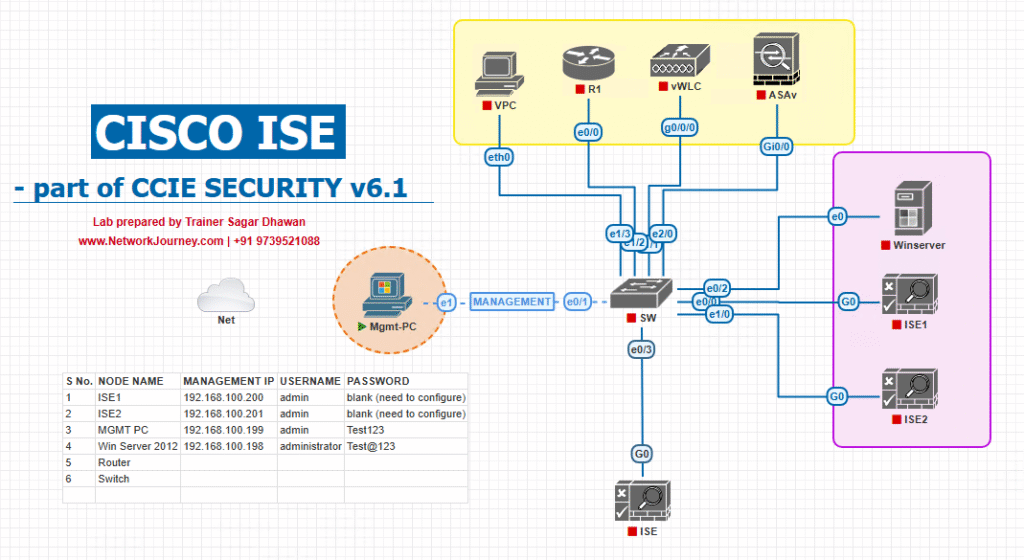
- User VLAN ↔ C9300 (dot1x/MAB, CoA enabled) ↔ Core/Router ↔ ISE PSN (RADIUS)
- ISE PAN/MNT (admin + TC-NAC) ↔ Internet ↔ Secure Endpoint Cloud
- Endpoint (Win11 + Secure Endpoint) → C9300 → PSN (RADIUS) → Authorized
- On detection, AMP Cloud → ISE TC-NAC → ANC Quarantine → CoA to C9300 → Quarantine DACL applied.
Step-by-Step GUI Configuration Guide (+ CLI)
A) Prerequisites & Health Checks
- ISE 3.2+ up and licensed (Premier for TC-NAC). (Admin > Licensing)
- Time sync (NTP), DNS forward/reverse for ISE/PSNs.
- PSN reachable from switches/WLC; firewalls allow RADIUS 1812/1813 and CoA (1700/UDP). (Cisco)
- Endpoint has Secure Endpoint agent, shows in Secure Endpoint console as “Protected”.
B) Enable TC-NAC Services on ISE
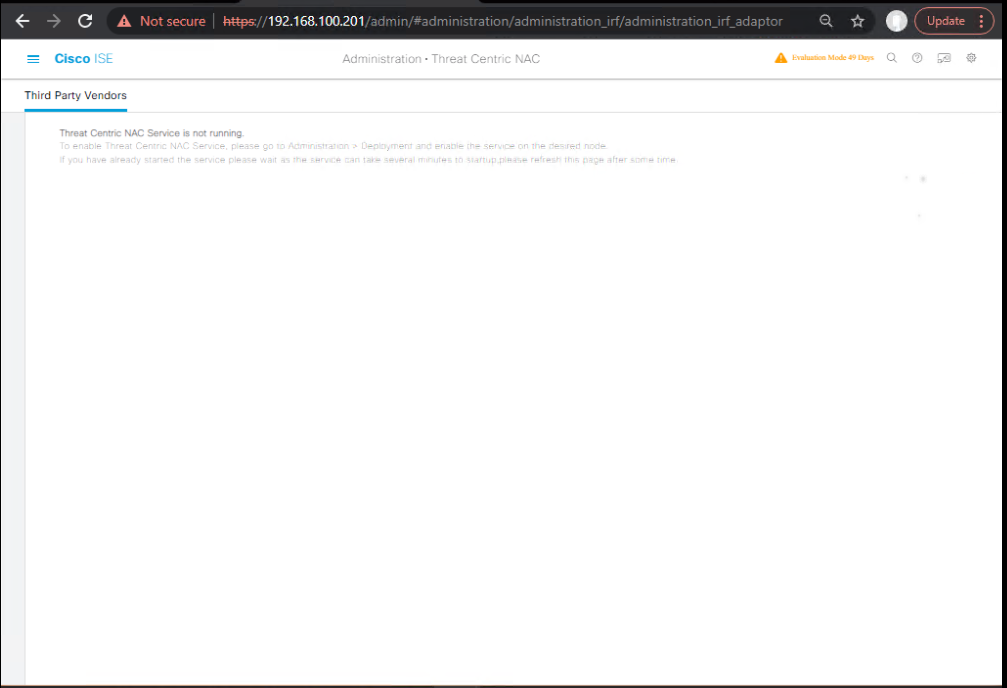
- GUI:Administration > System > Settings > Threat-Centric NAC → Enable TC-NAC (enable on the Primary Admin).
- Note: TC-NAC is a single-node service; enable only on one node.
- Note: TC-NAC is a single-node service; enable only on one node.
- Validate services:
- GUI: Operations > Threat Centric NAC > Live Logs should load (empty initially).CLI (ISE PAN):
application status ise show logging application ise-psc.log tail
- GUI: Operations > Threat Centric NAC > Live Logs should load (empty initially).CLI (ISE PAN):
C) Create the AMP (Secure Endpoint) Adapter in ISE
- GUI:Administration > Threat Centric NAC > Third-Party Vendors → Add → AMP: Threat.
- Choose the Secure Endpoint Cloud Region (US/EU).
- Click Login to Secure Endpoint (FireAMP) cloud and Authorize streaming.
- Select Event Types to subscribe (e.g., Malware Detections, Threat Detected, Threat Quarantined, Connector State).
- (Optional) Configure Proxy if required.
(ISE connects to Secure Endpoint cloud via OAuth/REST + AMQP event streaming.)
- Validate Adapter Health:
- GUI: In the AMP vendor instance, check Connection Status: Connected, Last Event Received timestamp.
- GUI: Operations > Threat Centric NAC > Live Logs → generate a benign test (e.g., EICAR) on the endpoint to see Threat events appear.
Important behavior: ISE does not auto-CoA on AMP threat events by default; you will manually action containment from Compromised Endpoints OR automate via ERS/Orchestration. (Automatic CoA is natively tied to “Vulnerability” adapters; AMP Threat is typically manual/automated externally.)
D) Prepare Network Devices for CoA/ANC (CLI)
Catalyst 9300 (IOS-XE 17.x) — baseline CoA & 802.1X/MAB:
conf t aaa new-model ! RADIUS servers radius server ISE1 address ipv4 10.10.10.11 auth-port 1812 acct-port 1813 key <ISE-SECRET> radius server ISE2 address ipv4 10.10.10.12 auth-port 1812 acct-port 1813 key <ISE-SECRET> aaa group server radius ISE-GRP server name ISE1 server name ISE2 ip radius source-interface Vlan10 ! CoA Dynamic Authorization aaa server radius dynamic-author client 10.10.10.11 server-key <ISE-SECRET> client 10.10.10.12 server-key <ISE-SECRET> auth-type any ! (Optional hardening) attribute event-timestamp drop-packet ! 802.1X/MAB on an access port (example) interface GigabitEthernet1/0/10 switchport mode access access-session host-mode multi-auth authentication port-control auto mab dot1x pae authenticator dot1x timeout tx-period 10 dot1x max-req 3 ! CoA bounce compliance authentication periodic authentication timer reauthenticate server spanning-tree portfast end wr mem
- Validate CoA readiness:
show aaa servers(look for Dynamic authorization clients),show authentication sessions interface gi1/0/10 details(look for Server Policies and Session Identifier).
(RADIUS CoA feature reference). (Cisco)
C9800-CL WLC (optional) — CoA:
conf t radius server ISE1 address ipv4 10.10.10.11 auth-port 1812 acct-port 1813 key <ISE-SECRET> aaa group server radius ISE-GRP server name ISE1 ip radius source-interface GigabitEthernet1 aaa server radius dynamic-author client 10.10.10.11 server-key <ISE-SECRET> auth-type any end
- Validate:
show wireless stats radius,show aaa servers. (Generic CoA config guidance.) (Cisco)
E) Create ANC Quarantine Controls (GUI)
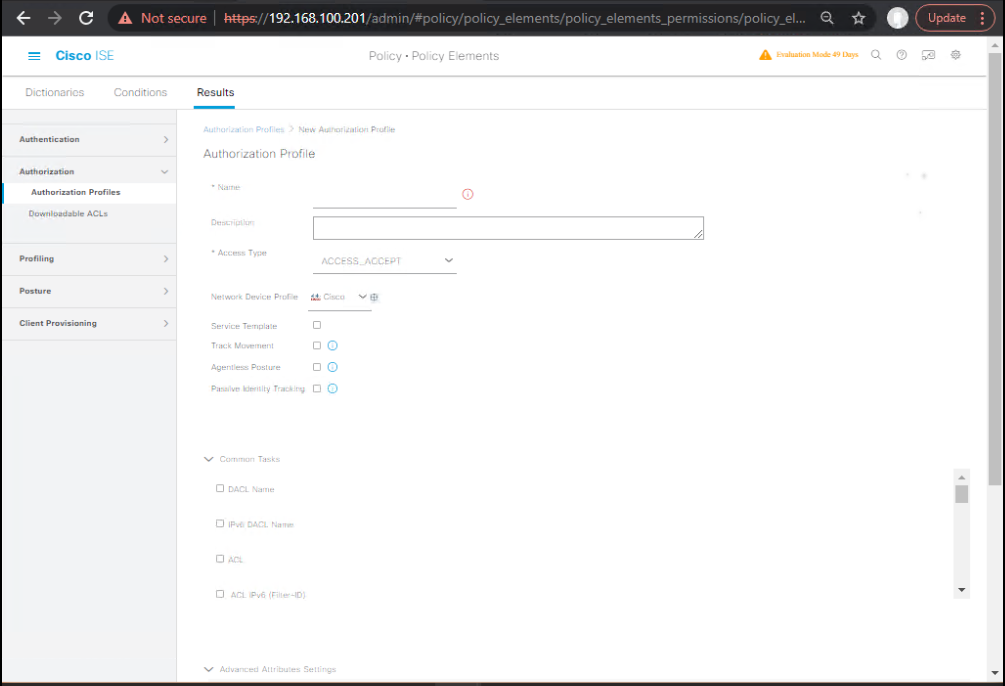
- Authorization Profile (Quarantine DACL or VLAN):
Work Centers > Policy Elements > Results > Authorization > Authorization Profiles → Add- Name: AUTH-QUARANTINE-DACL
- Access Type: ACCESS_ACCEPT
- DACL:
QUARANTINE-DACL(pre-create under Policy Elements > Results > Authorization > Downloadable ACLs with minimal Internet/IT helpdesk reach) - (Alternative) VLAN: 999 Quarantine
- ANC Policy:
Work Centers > Adaptive Network Control > Policies → Add- Name: ANC-QUARANTINE-AMP
- Action: Quarantine (choose Apply Authorization Profile →
AUTH-QUARANTINE-DACL)
- Validate ANC ready:
Work Centers > Adaptive Network Control > Endpoints (empty now).
F) Containment from TC-NAC (Manual)
- Trigger a test detection (e.g., EICAR) on the lab host.
- GUI (ISE): Operations > Threat Centric NAC > Compromised Endpoints → locate endpoint (by hostname/MAC) → Take Action > Apply ANC → select ANC-QUARANTINE-AMP.
- Observe CoA:
- Switch CLI:
show authentication sessions interface gi1/0/10 details ! look for Status = Authorized, Method = 802.1X/MAB ! after ANC/CoA: check "ACS ACL: xACSACLx-<DACL>" or VLAN change debug radius debug aaa coa - ISE GUI: Operations > RADIUS Live Logs → CoA Success against the session.
(TC-NAC threat events feed the Compromised Endpoints workflow; vulnerability adapters can auto-CoA—AMP threat path is usually manual or automated via API.)
- Switch CLI:
G) Automation Path (Optional but Recommended)
Goal: When Secure Endpoint flags High severity, automatically apply ANC via ISE ERS API.
1) Enable ERS on ISE & create ERS User
- GUI: Administration > System > Settings > ERS Settings → Enable ERS.
- GUI: Administration > Admin Access > Administrators > Admin Users → create ERS Admin (role: ERS Admin). (Cisco DevNet)
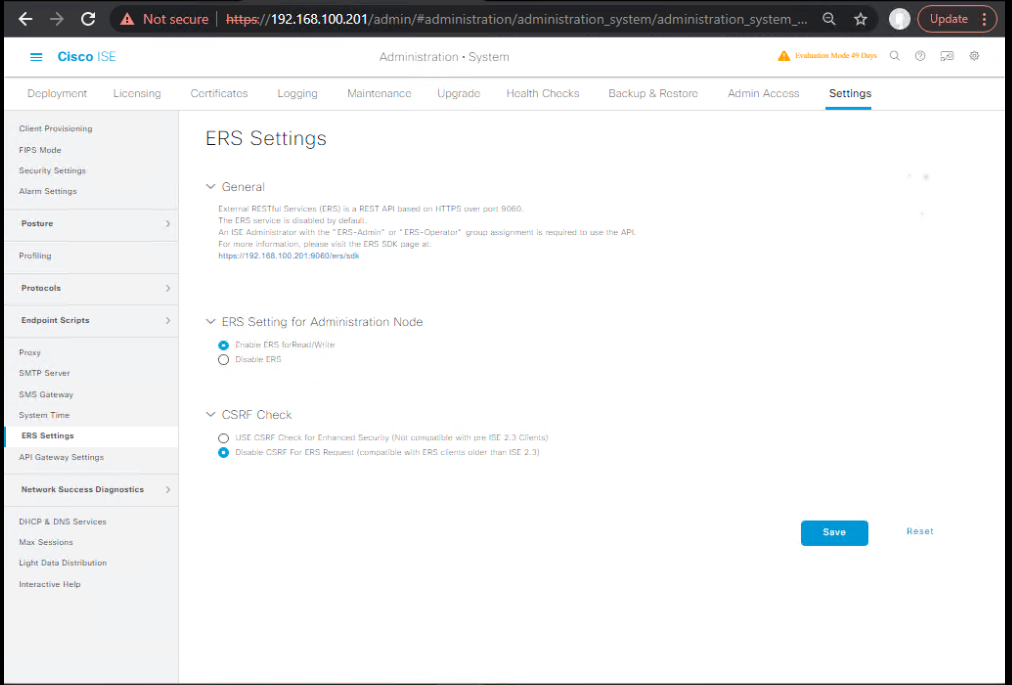
2) Test ERS ANC API (curl/postman)
- GET policies:
GET https://<ise>:9060/ers/config/ancpolicy - APPLY policy:
POST https://<ise>:9060/ers/config/ancendpoint/applycurl -k -u ersadmin:password \ -H "Content-Type: application/json" \ -d '{"OperationAdditionalData":{"additionalData":[{"name":"macAddress","value":"AA:BB:CC:DD:EE:FF"},{"name":"policyName","value":"ANC-QUARANTINE-AMP"}]}}' \ https://<ise>:9060/ers/config/ancendpoint/apply(Endpoint and payload pattern per Cisco Live hands-on & ERS docs.) (Cisco Live, Cisco DevNet)
3) Wire into Orchestration (example paths):
- SecureX Orchestration: Trigger on Secure Endpoint incident created (severity≥High) → extract MAC/IP → ERS Apply ANC task.
- pxGrid Cloud & OpenAPI: Alternate integration path to query ISE, then ERS call to apply ANC. (Cisco DevNet)
Validation: Repeat the malware trigger; verify automatic ANC/CoA without manual ISE action. Check ISE Live Logs, Switch debug aaa coa, and SecureX workflow runs.
H) Roll-Back / Release
- GUI: Work Centers > Adaptive Network Control > Endpoints → select endpoint → Clear ANC.
- CLI (switch): session will receive CoA;
show auth sessionsshould revert to normal DACL/VLAN. - API:
POST …/ers/config/ancendpoint/clearwith MAC in payload (similar structure). (Cisco DevNet)
Expert-Level Use Cases
- Auto-Quarantine on High-Severity Malware: Secure Endpoint → SecureX Flow → ISE ERS
ancendpoint/apply→ Switch CoA → Quarantine DACL. (Cisco Live) - Tiered Responses by Confidence: First detection = DACL (web only), multiple detections = VLAN 999, EDR clean →
ancendpoint/clear. - Executive Device Protection: High-value endpoints mapped to stricter ANC (no DNS except SOC, no SMB).
- Branch Isolation via SD-WAN: ANC ties into SD-WAN policy to black-hole inter-branch flows when a branch host is compromised.
- WLAN Containment with Session Preservation: Use DACL instead of VLAN to avoid DHCP/roam breaks on 9800.
- Threat-Hunting Feedback Loop: SOC closes Secure Endpoint incident → playbook clears ANC automatically (ERS clear API). (Cisco DevNet)
- IoT/Printer Infections: MAB-authenticated devices get SGT = IoT; on threat, ANC swaps to SGT = Quarantine + DACL.
- Compliance Gates: If Secure Endpoint connector not reporting, ANC applies “Limited Access” until posture restored.
- SOAR Integration: FortiSOAR/Palo XSOAR trigger ISE ERS ANC using incident fields mapped to MAC/IP.
- Red Team Drills: EICAR/Caldera sim → verify SOC playbook timers, CoA latency, Live Logs correlation.
Validation Checklists
Event Ingestion
- TC-NAC enabled & AMP adapter Connected.
- AMP test event appears in TC-NAC Live Logs.
Network Enforcement
- Switch/WLC dynamic-author configured;
debug aaa coashows CoA hits. (Cisco) - Authorization Profile (DACL or VLAN) created and downloadable to NAD.
- ANC Policy exists and binds that profile.
Containment (Manual)
- Endpoint visible under Compromised Endpoints; Apply ANC works.
- RADIUS Live Logs: CoA SUCCESS; Switch shows ACS ACL applied.
Containment (Automation)
- ERS enabled; ERS Admin created. (Cisco DevNet)
POST …/ancendpoint/applyreturns 202 Accepted. (Cisco Live)- Orchestration runbook triggers on Secure Endpoint incident and applies ANC.
FAQs – Cisco ISE + AMP for Endpoints Threat Mitigation
Q1. What licenses are required for Cisco ISE and AMP integration?
Answer:
- Cisco ISE: Requires Plus or Apex licenses (for pxGrid and Threat-Centric NAC features).
- AMP for Endpoints: Requires a valid Cisco Secure Endpoint license with Threat Intelligence & Cloud connectivity enabled.
- Both systems must support pxGrid 2.0 for integration.
Validation:
- ISE GUI → Administration > Licensing → check “Plus/Apex” active.
- AMP GUI → Accounts > Licenses → verify active subscription.
- CLI (ISE):
show licenseLook for “pxGrid” enabled.
Q2. How does AMP communicate risk information to Cisco ISE?
Answer:
AMP → shares endpoint disposition & risk scores → via Cisco Threat Response (CTR) → delivered through pxGrid 2.0 → consumed by ISE → mapped into Session Directory & Adaptive Policies.
Validation:
- ISE GUI → Context Visibility > Endpoints → check AMP attributes.
- CLI (ISE):
show logging application pxgrid.logLook for AMP event subscriptions.
Q3. What AMP attributes can ISE consume for enforcement?
Answer:
- Disposition: Clean, Malicious, Suspicious.
- Risk Score: Numerical threat score.
- Threat Verdict: Malware Family (e.g., Trojan, Ransomware).
- File Trajectory Events.
Validation:
- ISE GUI → Live Sessions → AMP attributes should appear in endpoint session details.
Q4. What enforcement actions can ISE take when AMP flags a compromised endpoint?
Answer:
- Change of Authorization (CoA) to move endpoint to:
- Quarantine VLAN.
- Downloadable ACL (dACL) restricting internet access.
- Session termination (hard block).
- Trigger Adaptive Network Control (ANC) to isolate device.
Validation:
- ISE GUI → Policy > Results > Authorization Profiles.
- Switch CLI:
show auth session <MAC|IP>Verify applied VLAN/dACL.
Q5. Does AMP integration work for both wired and wireless endpoints?
Answer:
Yes. Any session authenticated through ISE (wired, wireless, VPN) can be dynamically reclassified based on AMP telemetry.
- Wired → via CoA (switch port).
- Wireless → via WLC CoA.
- VPN → via ASA/FTD session enforcement.
Validation:
- Check Operations > Live Sessions in ISE for endpoint session type.
- WLC CLI:
show client detail <MAC>
Q6. How fast does ISE react to AMP threat verdicts?
Answer:
- Event delivery latency: ~5–15 seconds (depending on pxGrid performance).
- CoA enforcement: ~1–3 seconds after ISE receives verdict.
Validation:
- Inject a malware test file (EICAR).
- AMP → verdict updates.
- Check ISE Live Logs → CoA trigger.
- Switch CLI → confirm session change.
Q7. Can AMP retrospective alerts also trigger ISE policy changes?
Answer:
Yes. Retrospective alerts (where AMP reclassifies a file as malicious after initial execution) still flow into ISE. ISE then dynamically re-enforces the session (quarantine, block, etc.).
Validation:
- AMP Console → Events > Retrospective Alerts.
- ISE Live Logs → verify CoA issued.
Q8. What happens if pxGrid between AMP and ISE goes down?
Answer:
- ISE will not receive live AMP telemetry.
- Existing sessions remain unaffected.
- Enforcement continues based on last known posture.
Validation:
- ISE CLI:
show application status iseLook forpxgridstate. - Logs: pxgrid.log shows subscription drop.
Q9. How do I troubleshoot if AMP risk scores are not visible in ISE?
Answer:
- Check pxGrid connectivity.
- Ensure AMP has ISE registered as pxGrid client.
- Verify ISE consumes pxGrid data from AMP.
- Check time sync (NTP mismatch breaks trust).
Validation:
- ISE GUI → Administration > pxGrid Services → confirm “Registered Clients”.
- AMP Console → check for “ISE pxGrid Subscription”.
Q10. What is the best practice for policy design with AMP + ISE?
Answer:
- Use Policy Sets in ISE:
- Clean devices → full access.
- Suspicious devices → limited ACL/VLAN.
- Malicious devices → quarantine/deny.
- Always combine Identity + Posture + Threat Context.
- Don’t rely on a single attribute—use multiple conditions (e.g., AMP risk + device compliance).
Validation:
- ISE GUI → Policy > Authorization Policy → verify conditions.
- Test multiple endpoints with varying AMP dispositions.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- You connected Secure Endpoint → ISE TC-NAC and proved quarantine in seconds via ANC/CoA.
- You learned both manual containment (SOC analyst click) and automation (ERS API/SecureX).
- This is your golden path for endpoint-driven, network-enforced rapid response—repeatable, auditable, and scalable.
Upgrade Your Skills – Start Today
For deeper Cisco ISE mastery (live labs, advanced blueprints, interview prep):
Subscribe to “Network Journey” on YouTube and join instructor-led classes
Fast-Track to Cisco ISE Mastery Pro
I run a focused 4-month program: hands-on ISE (access control, TC-NAC, pxGrid, TrustSec/SGT, SDA, VPN/Posture), automation (ERS/pxGrid APIs, Ansible, Python), HA/DR, and real-world design clinics. Course outline & enrollment:
Network Journey — CCIE Security (lead-gen landing: course.networkjourney.com/ccie-security).
Reserve your seat → Get syllabus → Book a trainer call → Secure lab access.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![[Day 14] Cisco ISE Mastery Training: Setting Up a Test Switch for Authentication](https://networkjourney.com/wp-content/uploads/2025/08/Day-14-Cisco-ISE-Mastery-Training-Setting-Up-a-Test-Switch-for-Authentication.png)

![[Day 121] Cisco ISE Mastery Training: Automated Guest User Creation via API](https://networkjourney.com/wp-content/uploads/2025/08/Day-121-Cisco-ISE-Mastery-Training-Automated-Guest-User-Creation-via-API.png)