[Day 115] Cisco ISE Mastery Training: Stealthwatch Threat‑Based Quarantine
Table of Contents
Introduction
You’re the lead security engineer in a large financial enterprise. It’s Monday morning, and suddenly Stealthwatch starts flagging anomalous traffic from a user’s laptop in your corporate LAN. At first glance, nothing seems wrong — the user is just logged in and working. But Stealthwatch’s Encrypted Traffic Analytics (ETA) engine detects unusual beaconing patterns to an external IP. No packet payloads are visible (because the traffic is encrypted), but the metadata patterns scream Command-and-Control.
Now here’s the challenge:
- You can’t afford to take down the entire VLAN just because one host looks suspicious.
- You can’t wait for manual triage, because attackers move fast — every minute counts.
- And you must ensure the user device is contained, but without breaking core business functions.
This is exactly where the integration of Cisco Stealthwatch with Cisco ISE delivers its magic.
- Stealthwatch detects the compromise using flow telemetry, machine learning, and behavioral baselines.
- Stealthwatch publishes the threat event to Cisco ISE over pxGrid.
- ISE dynamically enforces a quarantine policy — maybe by moving the endpoint into a restricted VLAN, applying a downloadable ACL, or tagging it with a Security Group Tag (SGT) that blocks external communications.
- The user is effectively isolated in real time, while SOC teams investigate further.
This transforms your network into an adaptive security fabric:
- Every endpoint is continuously monitored.
- Every anomaly has teeth — instant enforcement.
- Every incident response workflow is shortened from hours to seconds.
And this is not theory — this is a production-grade Zero Trust capability that enterprises deploy globally.
In this masterclass Article, you and I will walk step by step through:
- How to integrate Stealthwatch and ISE over pxGrid.
- How to configure threat-response policies in ISE to quarantine automatically.
- How to validate using GUI and CLI that the endpoint is detected, tagged, and blocked in real time.
By the end, you won’t just know the buttons to click. You’ll understand why this integration is mission-critical, how to tune it for your environment, and how to prove it works under a live attack scenario.
This is where your Cisco ISE deployment graduates from just authentication to proactive threat containment — the difference between watching a fire burn and instantly putting it out.
Problem Statement
Real networks face two linked operational failures:
- Detection without enforcement: SOC sees a suspicious internal flow, but containment requires manual ticketing, device lookups, and CLI changes — slow and error-prone.
- Identity-blind containment: Firewalls or NDR tools block IPs only; they lack per-session identity and cannot selectively apply least-privilege while preserving business connectivity.
Result: dwell time increases and attackers move laterally. The Stealthwatch → ISE integration solves this by giving detections identity context and an accessible enforcement engine at the access layer (switch/WLC/VPN). (Cisco)
Solution Overview
How it works (high level):
- Stealthwatch/SNA detects anomalous behavior (east-west scanning, beaconing, odd flows).
- SNA publishes a quarantine recommendation via pxGrid (or its Central Management) to ISE Threat-Centric NAC (TC-NAC).
- ISE maps the detection to the active session (user, MAC, IP, switch port).
- ISE applies an ANC action (Authorization Profile with dACL, VLAN swap, SGT) and issues a RADIUS CoA to the network device.
- Network device applies changes; traffic is contained immediately.
- Evidence (ISE Live Logs, Stealthwatch event, switch auth session) is collected for SOC and audit. (Cisco)
Key enabling tech: pxGrid for context/events and ISE Adaptive Network Control (ANC) for quarantine actions (CoA/DACL/SGT). (Cisco)
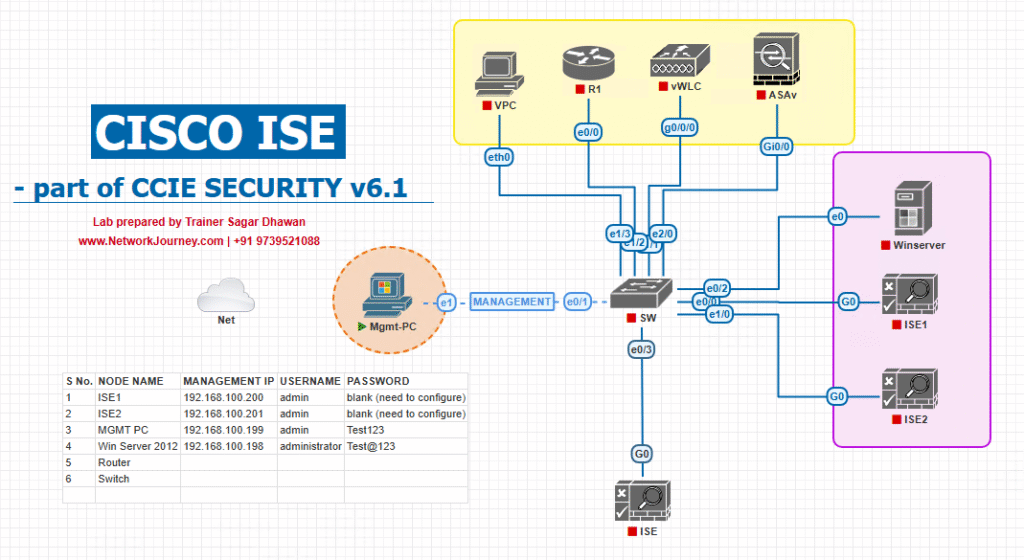
Sample Lab Topology (VMware / EVE-NG friendly)
Elements (recommended minimum):
- ISE cluster: PAN + 1 PSN (lab: PAN = PSN okay) — ISE 3.2/3.3+.
- Stealthwatch / Secure Network Analytics (SNA) Manager & Central Management (VMs) — SNA 7.x.
- Access switch: Catalyst 9300 (IOS-XE 16/17) or equivalent (supports RADIUS CoA / dynamic-author).
- WLC (C9800-CL) if testing WLAN CoA.
- VPN headend (ASA/FTD) for remote session CoA (optional).
- Endpoint VMs: Windows 10/11 test host (agentless flow tests are possible), Linux attacker VM (scanning), optional AnyConnect client.
- AD/DNS/NTP VMs and optional SIEM.
Topology diagram:
Lab notes
- pxGrid requires valid certificates and aligned NTP. Stealthwatch Central Management normally generates CSR and uses PKI to create pxGrid client certificate for ISE integration — follow SNA guide. (Cisco)
Step-by-Step GUI Configuration Guide
PRECHECK — Mandatory (do this before touching configs)
- DNS resolves (ISE, SNA, switch).
- NTP synchronized across ISE, SNA, switches.
- ISE reachable from SNA and vice-versa on management network.
- Admin accounts with rights on ISE & SNA; console access to Catalyst/WLC/ASA.
CLI quick test (on jump host):
# Replace hostnames/IPs with lab addresses nslookup ise.lab.local nslookup sna.cm.lab ping -c3 ise.lab.local ntpstat # or chronyc tracking
Expected: name resolves, ping succeeds, ntpstat shows synced.
STEP 1 — Prepare Certificates & pxGrid on SNA (Central Management)
Why: SNA/Stealthwatch must present a certificate to ISE pxGrid; typical flow: generate CSR from SNA Central Management, sign with your CA (or use ISE internal CA), import into SNA.
- Login to SNA Central Management (Central Manager / CM).
- Go Global Settings → Central Management → pxGrid (or Integrations → ISE).
- Generate CSR for pxGrid client certificate (follow SNA doc). Export CSR.
- Sign CSR with your CA (or use ISE internal CA exported chain) — create client certificate.
- Import the signed certificate back into SNA Central Management.
Validation (SNA GUI): pxGrid page shows a Client Certificate installed and status “Ready / CSR imported”.
See: SNA ISE configuration guide for CSR steps.
STEP 2 — Enable pxGrid & Accept SNA client in ISE (GUI)
- ISE GUI: Administration → System → Settings → pxGrid Services → Ensure pxGrid is Enabled and Started.
- ISE GUI: Work Centers → pxGrid Services → All Clients → you should see a registration request from SNA (or manually add SNA client if needed). Approve the client and trust the certificate. Option: set auto-approve for lab.
Validation (ISE CLI & GUI):
# On ISE (SSH) show application status ise show logging application pxgrid.log tail 50
Expected: pxGrid service RUNNING; logs show SNA client registration events. (Cisco)
STEP 3 — Configure the SNA → ISE integration in SNA (GUI)
- In SNA Central Management integration page: add ISE node(s) details (FQDN/IP of ISE pxGrid node), upload the ISE trust chain if required. Use the client cert created earlier.
- Configure the pxGrid topics to publish (session, security events, quarantine recommendations, endpoint details). Typical topic names are
com.cisco.ise.sessionandcom.cisco.ise.anc.*. - Save and verify SNA shows pxGrid connection Established and lists ISE as subscriber.
Validation (SNA GUI): Connection shows Connected, last heartbeat recent.
Validation (ISE GUI): Under pxGrid Clients, SNA shows Online and available services.
Cite: SNA + ISE integration steps & requirements. (Cisco)
STEP 4 — Configure ISE Threat-Centric NAC & ANC (GUI)
- Enable TC-NAC/ANC (if not already): Administration → System → Settings → Threat-Centric NAC → Enable. (Only enable on a single node for TC-NAC services.)
- Create ANC Action / Authorization Profile:
- Policy → Policy Elements → Results → Authorization → Add → AUTH-STEALTHWATCH-QUARANTINE.
- Include a Downloadable ACL (dACL) that allows only remediation servers / DNS to ISE / management and denies everything else, OR assign Quarantine VLAN or SGT.
- Save the dACL under Policy Elements → Results → Authorization → Downloadable ACLs.
- Create ANC Policy: Work Centers → Adaptive Network Control → Policies → Add.
- Name:
ANC-Quarantine-Stealthwatch - Action: Apply the
AUTH-STEALTHWATCH-QUARANTINEprofile.
- Name:
Validation (ISE GUI & CLI):
- In GUI: The new Authorization Profile and ANC policy must appear in lists.
- CLI:
show logging application ise-psc.log tail 50
Expected: No errors; policy listed. (Cisco)
STEP 5 — Ensure Network Devices Accept CoA & DACLs (Switch/WLC/ASA config & validation)
Configure your NAD (Network Access Device) to accept dynamic RADIUS CoA from ISE.
Catalyst 9300 (example)
Configuration (CLI):
conf t aaa new-model radius server ISE1 address ipv4 10.10.10.11 auth-port 1812 acct-port 1813 key ISEsecret aaa group server radius ISE-GRP server name ISE1 ip radius source-interface Vlan10 aaa server radius dynamic-author client 10.10.10.11 server-key ISEsecret # enable 802.1X/MAB on ports as needed interface Gi1/0/10 switchport mode access authentication port-control auto mab dot1x pae authenticator end wr mem
Validation (Switch CLI):
show aaa servers show authentication sessions interface Gi1/0/10 details show aaa-server ISE-GRP
Expect: RADIUS servers visible, dynamic-author client configured, authentication session present for test endpoint.
WLC/ASA notes: Configure equivalent dynamic-author/CoA clients; use aaa server radius dynamic-author on WLC/ASA. Ensure UDP ports for CoA allowed (usually 1700). (Cisco)
STEP 6 — Map Stealthwatch Event → ISE Endpoint & Apply Quarantine (Lab test)
- Simulate or trigger a Stealthwatch detection — e.g., run a benign scan (internal port scan) or replay a test signature so SNA flags anomalous behavior. (In labs, SNA has “test event” tools.)
- SNA now publishes a quarantine recommendation via pxGrid to ISE (or uses SNA UI Take Action → ISE). In ISE: Operations → Threat-Centric NAC → Compromised Endpoints you should see the detected host.
- Apply ANC through ISE: select endpoint → Actions → Apply ANC → choose
ANC-Quarantine-Stealthwatch. Confirm.
Validation (ISE Live Logs & Switch CLI):
- ISE Live Logs: Operations → RADIUS → Live Logs — look for Change-Authorization (CoA) record with status Success for that session.
- Switch CLI:
show authentication sessions interface Gi1/0/10 details show running-config interface Gi1/0/10 | include access-session show ip access-lists | include QUARANTINE-DACL
Expected: session now shows applied ACL/VLAN/SGT; quarantine DACL shows hit counter increment.
- Endpoint behavior verification: From the quarantined endpoint, attempt to access internal resources that should now be blocked. Use
ping,curl, ortraceroute. The attempts should fail per the quarantine policy. Collect packet capture (optional) at switch or core.
[CLI on endpoint:]
ping 10.1.1.10 # internal server curl http://finance.internal
Expected: blocked or timeouts.
STEP 7 — Automate Quarantine (ERS or Orchestration)
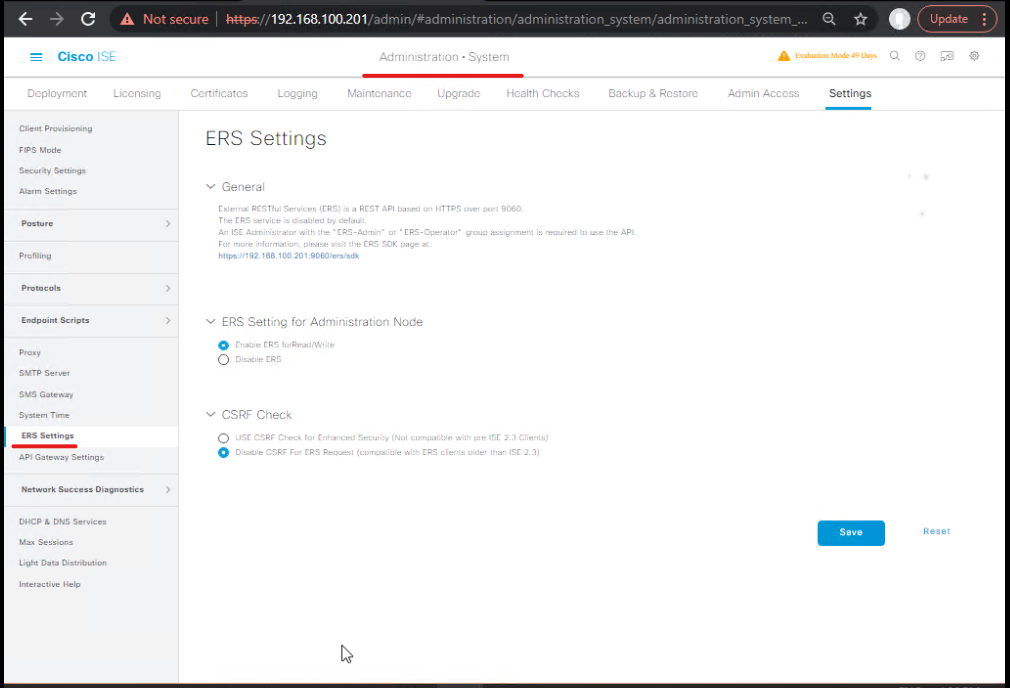
- Enable ERS & create ERS admin: Administration → System → Settings → ERS → enable. Create an ERS user with appropriate role.
- API test: Use curl / Postman to call ERS ANC apply endpoint (example simplified payload — adapt to your ISE version):
# Example (replace hostnames/creds)
TOK=$(curl -k -u ersadmin:Password https://ise.lab:9060/ers/sdk/auth/login 2>/dev/null)
curl -k -u ersadmin:Password -H "Content-Type: application/json" \
-X POST https://ise.lab:9060/ers/config/ancendpoint/apply \
-d '{"OperationAdditionalData":{"additionalData":[{"name":"macAddress","value":"AA:BB:CC:DD:EE:FF"},{"name":"policyName","value":"ANC-Quarantine-Stealthwatch"}]}}'
Expected: 202 Accepted (or appropriate JSON job id). Save the job id for evidence.
- Orchestration: Wire this call from Stealthwatch or SOAR (SecureX/Phantom) when SNA emits High severity alarms.
Validation: Check ERS job status, ISE Live Logs, and switch show authentication sessions to confirm CoA actions applied. (Cisco)
STEP 8 — Clear / Release Quarantine & Evidence Collection
- Release via ISE GUI: Work Centers → Adaptive Network Control → Compromised Endpoints → select endpoint → Clear ANC.
- Release via API:
POST …/ers/config/ancendpoint/clearpayload similar to apply. - Evidence pack (must collect for each test):
- Stealthwatch event export
- ISE Live Logs (Access-Request/CoA) + saved raw log.
- Switch
show authentication sessionspre/post CoA outputs saved as.txt. - Endpoint connectivity test logs (ping/curl outputs).
- ERS API request/response JSON.
Acceptance criteria: Quarantined host loses access per DACL/VLAN and is restored after clear. All logs show consistent timestamps.
Expert-Level Use Cases (deployable patterns)
- Auto Quarantine on Lateral Movement: SNA detects abnormal L2/L3 lateral flows → auto ERS apply ANC → DACL isolates host.
- Rogue DNS Quarantine: SNA detects rogue DNS servers being used → quarantine host and force DNS to corporate resolvers. (Cisco Community)
- Segmentation Enforcement Validation: Use ISE + SNA to confirm microsegmentation rules are working by intentionally generating cross-segment flows.
- SOC Closed-Loop: SIEM triggers Stealthwatch to mark host suspicious → automation invokes ISE ERS to quarantine and opens SOC ticket with artifacts.
- Red Team Rapid Response Drill: Simulate compromise → time containment metrics (pxGrid→ISE→CoA) and produce SLA report.
- IoT Infection Containment: SNA detects IoT C2 traffic → ISE quarantines MAB-authenticated device without impacting other IoT flows.
- Quarantine Failover Plan: Maintain separate DACL and VLAN strategies per site — choose DACL for global, VLAN for local full isolation.
- Forensic Preservation Mode: Quarantine that permits only SIEM and forensic upload endpoints to allow evidence collection.
- Multi-tenant MSP Model: Map SNA events per tenant → ISE enforces tenant-specific quarantine policies with evidence export for customers.
- Timesliced Containment: Apply quarantine for a configurable window (e.g., 20 min) then re-evaluate automatically via automation workflow.
FAQs – Cisco ISE & Stealthwatch Threat-Based Quarantine
FAQ 1. How does Stealthwatch actually communicate threat events to Cisco ISE?
Answer:
- Stealthwatch uses pxGrid 2.0 to publish context (security events, threat severity, host details).
- Cisco ISE subscribes as a pxGrid client, listening for events.
- Once a threat event matches your enforcement policy, ISE applies Adaptive Network Control (ANC) to quarantine the endpoint.
Validation:
- GUI: In ISE → Operations → Adaptive Network Control → Policy List, verify your quarantine policies exist.
- CLI (ISE):
show logging application pxgrid-server.logLook for “subscription accepted from Stealthwatch”.
FAQ 2. What happens to an endpoint when it is quarantined by ISE?
Answer:
- The endpoint is dynamically assigned:
- dACL → blocks traffic except to remediation servers.
- SGT → can restrict based on TrustSec policy.
- VLAN change → move to a quarantine VLAN.
- Choice depends on your enforcement design.
Validation:
- GUI: ISE → Operations → Radius → Live Logs → look for “Posture/ANC Quarantine applied”.
- CLI (Switch/WLC):
show authentication sessions interface Gi1/0/10→ should display dACL/SGT/VLAN quarantine.
FAQ 3. Can I customize which Stealthwatch threats trigger quarantine?
Answer:
- Yes. In ISE you configure ANC Policies to react only to specific categories (e.g., Botnet beaconing, Data Exfiltration).
- Avoid “quarantine everything” — use severity or event type filters.
Validation:
- GUI: ISE → Policy → ANC Policy → check match conditions.
- Test with Stealthwatch event injection tool or simulate suspicious traffic.
FAQ 4. What if Stealthwatch falsely classifies traffic and triggers quarantine?
Answer:
- False positives happen. Use:
- ANC Rollback to release endpoint.
- Exception lists in Stealthwatch for trusted hosts.
- Best practice: Start with monitor-only, then move to auto-quarantine after tuning.
Validation:
- GUI: ISE → Operations → Adaptive Network Control → Active Sessions → manually clear ANC.
- CLI:
ise/admin# clear access-session interface Gi1/0/10
FAQ 5. Does this work for both wired and wireless clients?
Answer:
- Yes. Any 802.1X/MAB authenticated client can be quarantined if connected through a device that supports dACL/VLAN assignment/SGT enforcement.
- Wireless: WLC must be TrustSec/dACL capable.
- Wired: Catalyst/IOS-XE switches support it natively.
Validation:
- CLI (WLC):
show client detail <MAC>→ Check “Quarantine ACL” applied.
FAQ 6. Can I integrate Stealthwatch with ISE in an EVE-NG/VMware Lab?
Answer:
- Yes. Use the Stealthwatch Management Console (SMC) VM + Flow Collector VM.
- Generate NetFlow from CSR1000v or Catalyst switch images.
- pxGrid must be enabled on ISE (Admin → pxGrid Services).
Validation:
- GUI: ISE → Administration → pxGrid Services → Clients → check Stealthwatch registered.
- CLI (ISE):
show application status ise | include pxGrid
FAQ 7. What’s the difference between Manual Quarantine vs Automated Quarantine?
Answer:
- Manual: SOC analyst triggers quarantine from ISE GUI/CLI based on Stealthwatch alert.
- Automated: Stealthwatch alert → pxGrid → ISE → automatic ANC action.
- Automated saves response time but needs strong tuning to avoid false positives.
Validation:
- GUI: Try both. Manually apply ANC on endpoint in ISE.
- CLI:
ise/admin# anccli apply <MAC> Quarantine ise/admin# anccli clear <MAC>
FAQ 8. How do I validate that the quarantined endpoint cannot reach the internet but still reaches remediation servers?
Answer:
- Design dACL with:
- Deny all IP traffic by default.
- Permit DNS/HTTP(S) only to patch/remediation servers.
- Test by browsing: External site should fail, remediation server should succeed.
Validation:
- CLI (Switch):
show ip access-lists <dACL> show authentication sessions interface Gi1/0/10 details - Endpoint test:
ping google.com(blocked) vsping remediation-server(allowed).
FAQ 9. How do I see which endpoints are currently quarantined?
Answer:
- GUI: ISE → Operations → Adaptive Network Control → Active Sessions.
- CLI:
ise/admin# anccli list
FAQ 10. What logs should I check if quarantine does not trigger?
Answer:
- Stealthwatch side: Check SMC → Alarms → ensure pxGrid export enabled.
- ISE side:
- pxGrid logs (
pxgrid-server.log,pxgrid-client.log). - Radius Live Logs (see if ANC pushed).
- Device logs (switch/WLC).
- pxGrid logs (
Validation CLI:
- ISE:
show logging application pxgrid-server.log - Switch:
show authentication sessions debug radius
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes — Key takeaways
- pxGrid bridges detection to enforcement. Stealthwatch finds the suspicious flow; ISE enforces per-session containment. (Cisco)
- Start with cautious enforcement (dACL) then automate for high-confidence detections.
- Test, measure, collect evidence for every scenario — containment timing and rollback are the operational metrics SOC will ask for.
- Certificates & NTP are the usual fail points — automate certificate renewals and monitor pxGrid health.
Upgrade Your Skills – Start Today
For deeper, hands-on Cisco ISE Mastery Training (full labs, automation scripts, and weekly troubleshooting clinics) subscribe to my Network Journey YouTube channel.
Consider the Fast-Track to Cisco ISE Mastery Pro: a 4-month instructor-led CCIE-Security-level program.
Course outline and enrollment: https://course.networkjourney.com/ccie-security/. Sign up for the discovery call and get the “Stealthwatch → ISE Quarantine” runbook pack as a lead magnet.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



