[Day 117] Cisco ISE Mastery Training: Automated Incident Response via SIEM
Table of Contents
Introduction
When seconds matter, your SOC can’t wait for humans to swivel-chair between alerts, switches, and identity stores. Automated incident response connects your SIEM detections to Cisco ISE enforcement so the moment Splunk/QRadar/ArcSight confirms a threat, ISE isolates the endpoint (ANC/DACL/SGT), revokes access (CoA), or moves the device to a remediation VLAN—with full, audit-grade evidence.
In this Article you will implement:
- SIEM → ISE action pipelines (ERS & pxGrid),
- Quarantine playbooks (ANC + DACL + CoA),
- Rollback (clear ANC) & safety guardrails,
- End-to-end GUI + CLI validations (ISE, switches/WLC, SIEM).
Problem Statement
Typical gaps you’ll close today:
- Alerts fire in SIEM but nothing changes on the network (manual triage delay).
- NAC teams lack a repeatable, auditable way to quarantine from SOC tools.
- Quarantine actions break users because rollbacks aren’t built.
- Field extraction and identity enrichment are inconsistent, so playbooks can’t target the right endpoint (MAC/IP/username/port).
Goal: Deterministic, tested pipelines from SIEM detection → ISE enforcement (ANC/CoA/SGT/DACL) → validation → rollback, with CLI evidence.
Solution Overview
Control plane:
- ISE ERS API for actions: Apply/Clear ANC, trigger CoA, manage Endpoint attributes.
- pxGrid for live session lookup (map IP → MAC → username, NAD, port, SGT, posture).
Enforcement options:
- ANC policy → Authorization Profile with Quarantine DACL or SGT (TrustSec).
- CoA to force reauth & apply new policy.
- SGT rewrite to push scalable, fabric-wide segmentation (SDA/TrustSec).
- WebAuth redirect to remediation portal (optional).
Automation hooks (per SIEM):
- Splunk: Alert Action (Python/Webhook) calling ISE ERS; optional pxGrid enrichment lookup.
- QRadar: Rule → Custom Action / Webhook / Script on App Host → ISE ERS.
- ArcSight ESM: Rule → Command Action (runs script on connector/manager) → ISE ERS.
Sample Lab Topology
Platform: VMware/EVE-NG
- ISE: PAN+MnT+PSN (3.x/2.7+).
- SIEM: Splunk Enterprise (or QRadar CE / ArcSight ESM dev).
- Switch: Catalyst 9300 (IOS-XE) for 802.1X/MAB + DACL/SGT.
- WLC (optional) for WLAN tests.
- Endpoint(s): Windows 11 client (AnyConnect optional).
- SOAR (optional): Splunk SOAR / QRadar SOAR.
Topology diagram:
Step-by-Step GUI Configuration Guide
PRECHECKS (Run before integration)
- NTP/DNS aligned across ISE, SIEM, switches.
# Jump host nslookup ise.pan.lab nslookup splunk.lab date -u - PKI ready (CA trust on ISE & SIEM if using TLS and for ERS cert validation).
- Network reachability (ISE → SIEM & SIEM → ISE 9060/ers, 8910/pxgrid).
# From SIEM host curl -k https://ise.pan.lab:9060/ers/sdk --head # From ISE (if shell permitted) or jump host nc -vz splunk.lab 6514
A) ISE — Build Enforcement Objects (ANC, DACL/SGT, CoA)
- Create Quarantine DACL
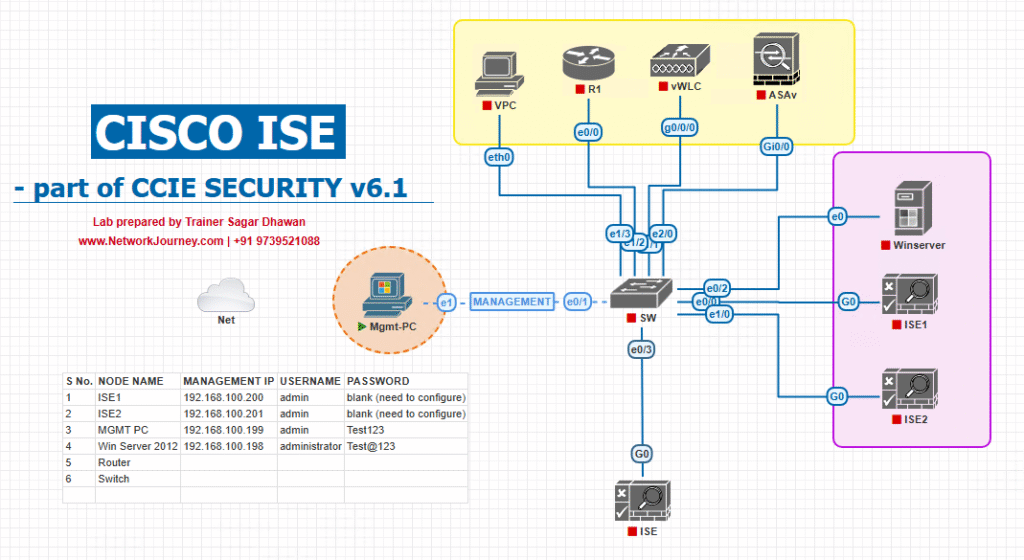
- ISE GUI → Policy > Policy Elements > Results > Authorization > Downloadable ACLs > Add
- Name:
DACL-QUARANTINE - ACL Content:
deny ip any any permit tcp any host 10.10.10.50 eq 443 # remediation portal permit udp any any eq 53 # DNS
- Name:
- Save.
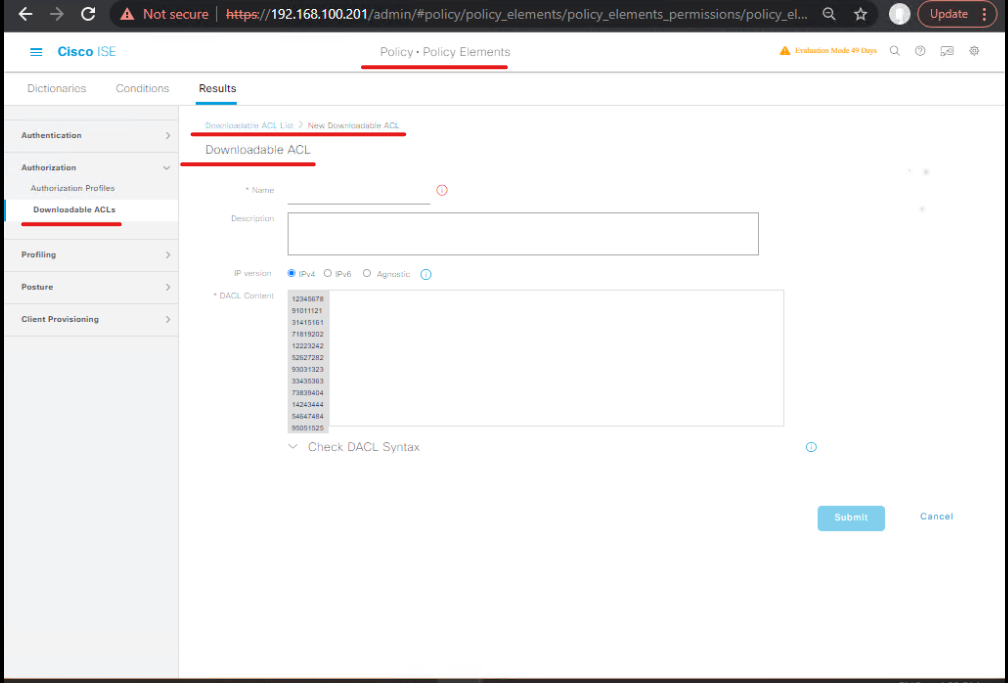
- (Option) Create Quarantine SGT
- Work Centers > TrustSec > Components > Security Groups > Add
- Name:
SGT-QUARANTINE(e.g., tag ID 50)
- Name:
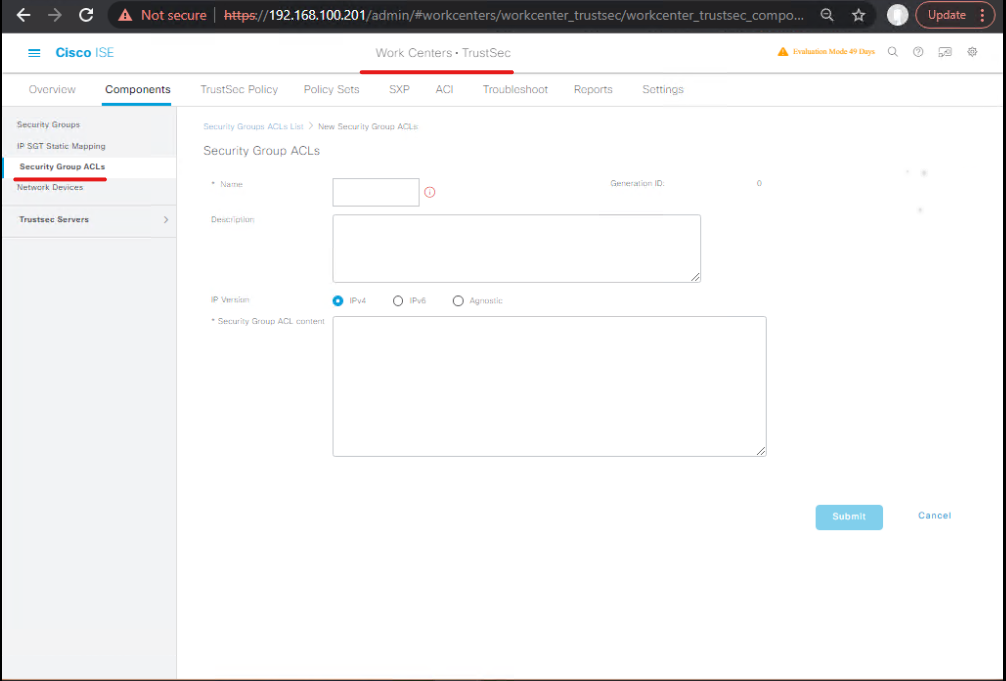
- Authorization Profile for Quarantine
- Policy > Policy Elements > Results > Authorization > Authorization Profiles > Add
- Name:
AUTH-QUARANTINE-DACL - Common Tasks: Check Downloadable ACL → select
DACL-QUARANTINE - CoA Type: Reauthenticate (or Port Bounce as needed)
- Name:
- Save.
- Define ANC Policies
- ISE 2.x: Operations > Adaptive Network Control
- ISE 3.x: Context Visibility > Endpoints > ANC or Policy > Policy Elements > Results > ANC Policy(paths vary; use search for “ANC”)
- ANC Policy Name:
ANC-APPLY-QUARANTINE→ Action = Quarantine → AssignAUTH-QUARANTINE-DACL(or map to SGT). - ANC Policy Name:
ANC-CLEAR→ Action = Clear ANC.
- ANC Policy Name:
Validation (Live Test)
- Connect a test endpoint → normal access.
- ISE Live Logs: Operations > RADIUS > Live Logs shows Access-Accept.
- Switch CLI (C9300):
show authentication sessions interface Gi1/0/10 details # Expect: Status Authorized; DACL none (pre-quarantine)
B) ISE — Enable ERS & pxGrid (for API actions & enrichment)
- Enable ERS
- Administration > System > Settings > ERS Settings > Enable ERS
- Create ERS admin: Administration > Admin Access > Administrators > Add (select ERS permissions).
- Enable pxGrid (for IP→MAC→User lookups)
- Administration > System > Settings > pxGrid Services > Enable
- (Optional) Approve SIEM pxGrid client after first connect.
Validation (API Reachability)
# From SIEM host curl -k -u ers_user:ers_pwd https://ise.pan.lab:9060/ers/config/ancendpoint -I # Expect HTTP/1.1 200 OK (or 401 if creds wrong)
C) Splunk — Build Alert → ISE Action (Webhook/Python)
Goal: When a detection fires (e.g., “High-fidelity malware on host 10.10.10.55”), Splunk calls ISE ERS to quarantine the MAC, then triggers CoA.
- Create Saved Search / Correlation Rule
- Splunk Web → Search & Reporting → craft detection SPL; example:
index=edr sourcetype=malware severity=high | stats latest(host_ip) as src_ip, values(user) as user, values(hostname) as host by signature - Save as Alert: Trigger = Once per Result.
- Create Custom Alert Action (Webhook or Script)
Option A – Webhook (simple):
- Configure Webhook URL to a small middleware on Splunk HF that runs a Python script (recommended for auth & certs).
Option B – Python Alert Action:
- Deploy an Alert Action app that runs a Python script
ise_quarantine.py. - Script (template):
#!/usr/bin/env python3 import requests, json, sys, os ISE = os.environ.get("ISE_HOST","https://ise.pan.lab:9060") ERS_USER = os.environ.get("ERS_USER","ers_user") ERS_PASS = os.environ.get("ERS_PASS","ers_pwd") src_ip = sys.argv[1] # passed from alert # 1) Resolve IP -> MAC via pxGrid or SIEM lookup table (assume provided): mac = lookup_mac_from_ip(src_ip) # implement via pxGrid or Splunk KVstore # 2) Apply ANC (Quarantine) body = {"OperationAdditionalData":{"additionalData":[ {"name":"macAddress","value":mac}, {"name":"policyName","value":"ANC-APPLY-QUARANTINE"}]}} r = requests.post(f"{ISE}/ers/config/ancendpoint/apply", auth=(ERS_USER,ERS_PASS), headers={"Content-Type":"application/json"}, data=json.dumps(body), verify=False) print("ANC apply:", r.status_code, r.text) - Pass token(s)/creds via Splunk secure storage or environment variables.
- (Optional) pxGrid Enrichment
- Before ANC, resolve MAC for the IP:
- Use a pxGrid client (cert-auth) to query Session Directory topic and return MAC, username, NAD, port.
- Cache mapping in Splunk KV Store for quick lookup.
- Create Rollback Alert Action
- A paired alert (or same action with param) to Clear ANC:
curl -k -u ers_user:ers_pwd -H "Content-Type: application/json" \ -X POST https://ise.pan.lab:9060/ers/config/ancendpoint/clear \ -d '{"OperationAdditionalData":{"additionalData":[{"name":"macAddress","value":"AA:BB:CC:DD:EE:FF"}]}}'
Validation (End-to-End)
- Fire test alert manually (Splunk → Trigger Alert).
- ISE GUI: Context Visibility > Endpoints > [endpoint] > ANC Status = Quarantined.
- Switch CLI:
show authentication sessions interface Gi1/0/10 details # Expect: DACL= DACL-QUARANTINE (or SGT=SGT-QUARANTINE), Method=dot1x/mac, Status=Authorized show access-lists | include DACL-QUARANTINE - Client validation: Browsing blocked except remediation allowed; reauth occurred (link flap or CoA seen in logs).
D) QRadar — Rule → Custom Action → ISE
- Correlation Rule
- QRadar Offenses/Rules → Create rule: When events where and identity present.
- Custom Action
- Add Webhook / Script action on App Host that calls ISE ERS Apply ANC with MAC/IP (use pxGrid lookup as needed).
- Rollback Action
- Second custom action to Clear ANC.
Validation
- Fire test offense → Action logs show HTTP 200/202 to ISE.
- ISE endpoint shows ANC applied; switch shows DACL/SGT enforced.
E) ArcSight ESM — Rule → Command Action → ISE
- Rule
- Condition matches high-confidence event; aggregation provides
sourceAddressordeviceCustomString1=MAC.
- Command Action
- Runs a local script (on connector/manager) that performs the same ERS POST apply/clear.
Validation
- ESM Rule fires → Command action logs successful exit code; ISE shows ANC.
F) Safety Guardrails & RBAC
- Two-person approval (optional): use SIEM notable → SOAR playbook with approval step → ISE action.
- Allowlist: refuse quarantine for critical assets (domain controllers, core infra).
- Max hold time: auto-rollback after X minutes if incident closed as false positive.
- RBAC: ERS user limited to ANC/Session read; no full admin rights.
G) Evidence Pack (export these)
- Splunk/QRadar/ArcSight alert firing]
- ISE ANC policy page]
- ISE Endpoint page – ANC=Quarantined]
- Switch CLI output (pre- and post-quarantine):
show authentication sessions interface Gi1/0/10 details show cts role-based sgt-map all | include <MAC or IP> # if SGT used - ISE ERS API response (HTTP 202 + jobId).
- Rollback evidence: ANC cleared; client restored.
Expert-Level Use Cases
- IOC-Driven Quarantine: EDR “High” + DNS tunneling anomaly → SIEM alert → ISE ANC + DACL + CoA → ticket + Slack notification → auto-rollback if EDR clears.
- Ransomware Blast-Radius Control: Lateral movement detector fires → SIEM tags subnet → ISE bulk-ANC on matching MACs via ERS; TrustSec matrix denies east-west.
- Privileged Abuse Throttle: Impossible travel + PAM anomaly → move user to restricted SGT with just-enough access; SOAR requests approval, then auto-rollback after 60 min.
- BYOD Non-Compliant Posture: Splunk receives posture non-compliant + EDR off → ISE assigns remediation portal DACL; CoA to force captive flow.
- Branch Wide Containment: QRadar offense on branch NAT IP → pxGrid resolves per-host sessions on that PSN → mass ANC only for active infected MACs.
- Wireless Rogue AP Client Herding: WLC rogue event → ArcSight rule → ISE applies VLAN redirect to cleanup SSID for affected MACs.
- Data Exfil Spike: DLP alert for userX → ISE reauth userX sessions to SGT-MONITOR; NetFlow & decryption policies intensify inspection.
- Critical Asset Ring-Fence: IDS alert near Tier-0 → ISE raises SGT QUAR-EDGE for untrusted endpoints; fabric matrix blocks Tier-0 adjacency.
- Guest Abuse Auto-Expire: SIEM sees DoS from Guest VLAN → ISE ERS revokes sponsor account + clears active sessions.
- OT/IoT Anomaly: NBAR/Stealthwatch reports protocol drift → ISE maps MAC OUI to IoT-SGT with deny-write DACL; CoA on affected ports.
FAQs: Automated Incident Response via SIEM & Cisco ISE
Q1. How does Cisco ISE receive incident data from SIEM platforms like Splunk, QRadar, or ArcSight?
Answer:
- Cisco ISE integrates with SIEM via Syslog feeds, APIs, or pxGrid.
- SIEM platforms analyze logs from multiple sources (firewalls, endpoints, servers) and push enriched alerts to ISE for policy enforcement.
- Validation:
- CLI:
show logging application ise-psc.log(for pxGrid session updates). - GUI: Navigate to Operations → Radius → Live Logs to see incidents mapped to endpoint sessions.
- CLI:
Q2. What types of incidents can be automatically acted upon by ISE through SIEM integration?
Answer:
- Malware Infections (from AMP, EDR, Firepower logs).
- Data Exfiltration Attempts (from DLP integration).
- Brute Force / Authentication Attacks (from Splunk security rules).
- Command & Control Communication Detection (from Stealthwatch or QRadar).
- ISE then triggers context-based quarantine (VLAN change, dACL, SGT assignment).
Q3. How do I configure ISE to take automated action (quarantine/block) when SIEM detects an incident?
Answer:
- In ISE Admin GUI, go to Work Centers → TrustSec → Adaptive Network Control (ANC).
- Create ANC Policies (e.g., “Quarantine”, “Monitor”, “Block”).
- On SIEM side (Splunk/QRadar): configure pxGrid/REST API call to apply ANC policy.
- Example API Call:
curl -k -u pxgrid-client:pxgridpass \ -X POST https://<ISE-IP>:8910/ers/config/ancendpoint/apply \ -H "Content-Type: application/json" \ -d '{"OperationAdditionalData":[{"name":"macAddress","value":"AA:BB:CC:DD:EE:FF"},{"name":"policyName","value":"Quarantine"}]}'
- Example API Call:
- Validate in ISE → Operations → ANC → Policy Hits.
Q4. How do I test if ANC Quarantine works properly after SIEM triggers?
Answer:
- Use a test endpoint MAC address.
- Push ANC policy from SIEM manually via API.
- In ISE GUI → Context Visibility → Endpoints, check that endpoint’s ANC Status = Quarantine.
- On switch CLI:
show authentication sessions interface Gig1/0/2 show access-session mac AA:BB:CC:DD:EE:FF details→ Should show Quarantine SGT/dACL applied.
Q5. Can ISE differentiate between false positives vs confirmed threats when receiving events from SIEM?
Answer:
- Yes, SIEM rules should define confidence levels (High, Medium, Low).
- Best practice:
- High confidence → Auto-quarantine.
- Medium confidence → Restricted access (SGT-based segmentation).
- Low confidence → Alert only, no enforcement.
- This prevents unnecessary endpoint disruptions.
Q6. What happens if pxGrid or API communication between SIEM and ISE fails?
Answer:
- Incidents will not reach ISE, meaning no quarantine action occurs.
- Troubleshooting:
- ISE CLI:
show application status ise | include pxgrid show logging application ise-psc.log - SIEM logs: Check API call failures (HTTP 401, 403, timeout).
- ISE CLI:
- Mitigation: Always configure syslog-based fallback for redundancy.
Q7. How can I audit or confirm that an endpoint was quarantined due to a SIEM-triggered incident?
Answer:
- ISE GUI: Operations → Reports → Endpoint → ANC Report.
- ISE Live Logs: Filter for endpoint MAC/Username.
- Switch CLI validation:
show access-session mac <endpoint-mac>→ Will show applied ANC or dACL policy. - Splunk/QRadar dashboards should also show ISE enforcement confirmation logs.
Q8. Is it possible to automatically release an endpoint from quarantine once it is clean?
Answer:
- Yes, automation works both ways.
- Workflow:
- AMP/EDR detects malware removed → updates SIEM.
- SIEM calls ISE API →
clear-ancendpointpolicy. - Endpoint reverts to normal network access.
- Validation:
- ISE GUI → Endpoint no longer shows ANC applied.
- CLI:
show access-session interface g1/0/2should show original SGT/VLAN.
Q9. How scalable is automated incident response with ISE + SIEM?
Answer:
- Cisco ISE can handle 100,000+ endpoints with pxGrid scaling across distributed deployments.
- SIEM (e.g., Splunk Enterprise Security, QRadar) can ingest millions of EPS (Events per Second).
- Best Practice:
- Deploy ISE PSN nodes close to network devices.
- Use pxGrid Pub/Sub for high-volume event forwarding.
Q10. What are common misconfigurations engineers face during ISE-SIEM integration for automation?
Answer:
- Incorrect pxGrid certificate trust → API calls fail with SSL errors.
- Missing ANC policy mapping in ISE → SIEM push ignored.
- Improper endpoint ID (e.g., IP vs MAC) used in API request → No enforcement applied.
- ISE not enabled for pxGrid services → SIEM cannot subscribe to sessions.
- Switch not configured for CoA → Quarantine dACL never applied.
- CLI Fix:
aaa authorization network default group radius radius-server attribute 8 include-in-access-req ip device tracking
- CLI Fix:
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes (Key takeaways)
- Automate detection → enforce with ISE (ANC/DACL/SGT + CoA).
- Enrich alerts using pxGrid/ERS to target precisely the right session.
- Prove every step with CLI, and pair every action with a rollback.
- Harden with guardrails, RBAC, allowlists, and rate-limits.
Upgrade Your Skills – Start Today
For hands-on labs, production-grade playbooks, and ready-to-use Splunk/QRadar/ArcSight connectors, subscribe to Network Journey on YouTube and enroll in 4-month instructor-led CCIE Security Mastery.
Get the Automated ISE Response Pack (ANC/DACL objects, Splunk Alert Action app, QRadar Webhook script, ArcSight command scripts, pxGrid session resolver).
Course & outline: https://course.networkjourney.com/ccie-security/ — join to get mentored, lab access, and lead-ready templates.
Fast-Track to Cisco ISE Mastery Pro
- Who it’s for: SOC/NOC engineers, NAC architects, SecOps leads.
- What you’ll build: End-to-end ISE automations (pxGrid, ERS, TrustSec/SGT, SOAR playbooks), HA & DR, large-scale policy sets, fabric segmentation, zero-trust enforcement.
- Deliverables: 25+ runbooks, 60+ labs, Splunk/QRadar/ArcSight integrations, posture & threat-based quarantine, rollback patterns.
- Outcome: Production-ready automated SOC→NAC controls with measurable MTTR reduction.
Enroll now to reserve a seat and receive pre-class lab prep + interview-ready project briefs.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



