[Day 118] Cisco ISE Mastery Training: REST API Advanced — Automating User Onboarding
Table of Contents
Introduction
In the modern enterprise, manual onboarding of users is a bottleneck. Picture this: a new employee joins, HR requests IT to create credentials, IT manually adds them to ISE, assigns groups, emails credentials, and then configures device access. Multiply this by hundreds of employees, contractors, and BYOD endpoints, and you quickly run into delays, errors, and security gaps.
This is exactly where the Cisco ISE REST API becomes a game-changer. REST APIs allow us to automate user lifecycle management — from onboarding, to policy assignment, to revocation. Instead of clicking through GUIs for every new joiner, you can script, integrate with HR systems (Workday, SAP, ServiceNow), or tie into SIEM/SOAR workflows to automatically create, update, and delete users in ISE.
By the end of this session, you’ll not only learn the step-by-step GUI and CLI validation for API configuration, but you’ll also build the muscle memory to:
- Enable and secure ERS APIs on ISE.
- Create users automatically with REST calls (curl, Python, Ansible).
- Bulk-onboard 100+ users without ever touching the GUI.
- Validate API success/failures through CLI logs and GUI checks.
- Troubleshoot common onboarding errors (401, 403, 500, etc).
- Extend onboarding workflows to external systems (HR, ITSM, SOAR).
Think of this as your transition from GUI-operator to API-driven network automation engineer. We’re not just learning what buttons to press, but also how to validate, script, and scale user onboarding at enterprise level.
This is not a surface-level “REST API overview” — it’s a full masterclass deep-dive, with:
- GUI navigation & placeholders
- CLI show/debug validation commands
- Real-world automation scripts (curl + Python)
- Troubleshooting guide with log inspection
- Expert-level use cases (HR integration, SOAR automation, BYOD workflows)
By the end of today’s Article, you’ll have the confidence to automate ISE user onboarding end-to-end and be ready for real-world production deployments.
Problem Statement
- Helpdesk creates users in ISE inconsistently; typos & wrong groups break NAC.
- Contractors & guests need time-bound access; manual expiry tracking fails.
- Device onboarding (MAC, descriptions, custom attributes) is slow; bulk imports are brittle.
- No closed loop: HR/ITSM events don’t drive ISE identity lifecycle; stale accounts linger.
- No evidence pack (logs) to satisfy audits/CAB.
Goal today: Build repeatable, scripted pipelines to:
- Create/modify Internal Users & Endpoints (with identity groups, attributes, expiry).
- JIT Guest User creation (sponsor/self-reg) via API.
- Bulk import at scale.
- Validate in GUI & CLI; collect artifacts; implement safe rollback.
Solution Overview
Control surfaces
- ERS (External RESTful Services) on
https://<ise>:9060/ers/config/*for CRUD on identities, endpoints, groups, guest users, ANC, etc. - pxGrid (optional here) to enrich/verify sessions (resolve IP⇄MAC⇄User) pre/post changes.
Core resources for onboarding
/ers/config/internaluser— Internal Users./ers/config/identitygroup— Identity Groups (Users/Endpoints)./ers/config/endpoint— Endpoints (MAC entries)./ers/config/guestuser— Guest users (sponsored/self-reg)./ers/bulk/*— Bulk import/update.
Security
- Enable ERS at node-level, restrict by ACL/IP allowlist, use TLS, least-privilege ERS admin, and audit.
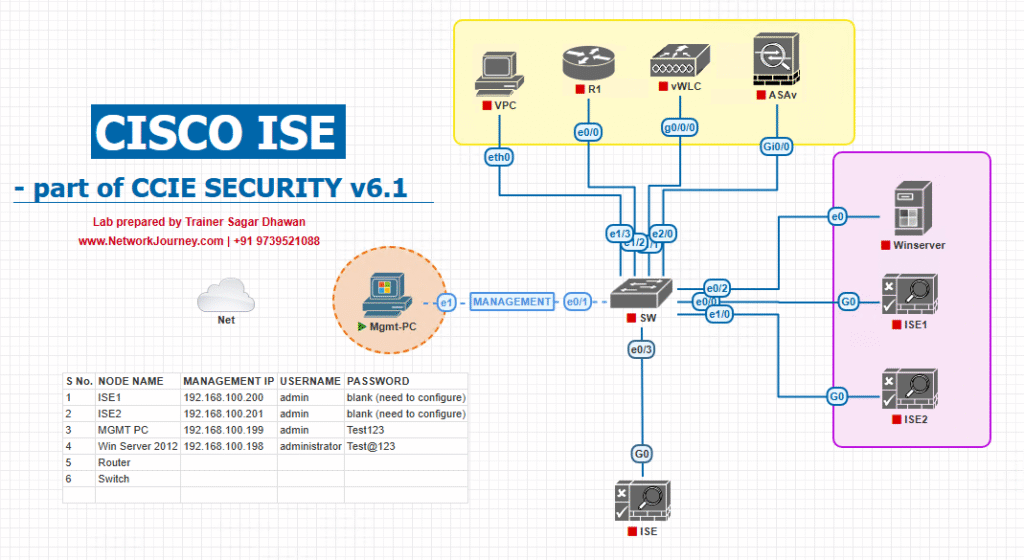
Sample Lab Topology (VMware/EVE-NG)
Nodes
- ISE: 3.x (PAN/MnT/PSN) single-node lab or distributed (PAN+MnT + PSN).
- Switch: Catalyst 9300 (802.1X/MAB, CoA, DACL/SGT).
- WLC (optional) for WLAN onboarding validation.
- Endpoint: Win 11 (wired/wireless).
- Automation Host: Linux/Windows with curl/Postman/Python.
- ITSM/Mock HR: Simple webhook/script to emulate HR events.
Topology diagram:
Step-by-Step GUI Configuration Guide
A. Pre-Checks (Do these once)
- Time/DNS/PKI aligned (ISE, Automation Host, Switch/WLC).
# Automation host date -u; nslookup ise-pan.lab; nslookup c9300.lab openssl s_client -connect ise-pan.lab:9060 -servername ise-pan.lab </dev/null | openssl x509 -noout -subject -dates - ISE app status
ise/admin# show application status ise - Switch supports CoA & DACL
c9300# show run | s radius|aaa|cts c9300# show authentication sessions
B. Enable ERS & Create ERS Admin (GUI)
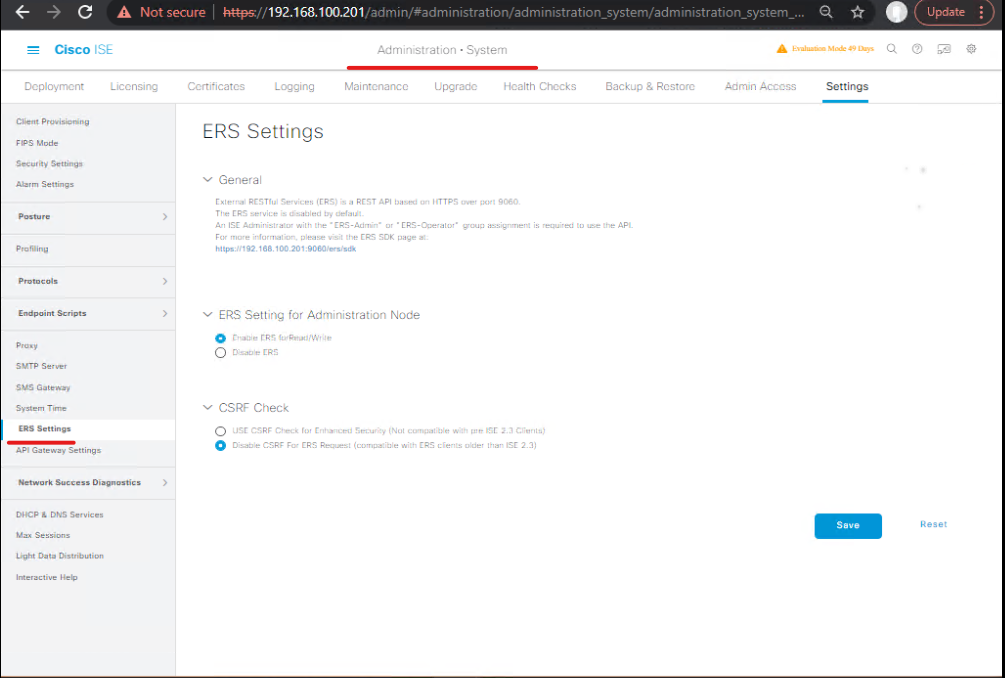
- Enable ERS
- Administration → System → Settings → ERS Settings → Enable ERS for Read/Write
- Save.
- [ISE ERS Settings Enabled]
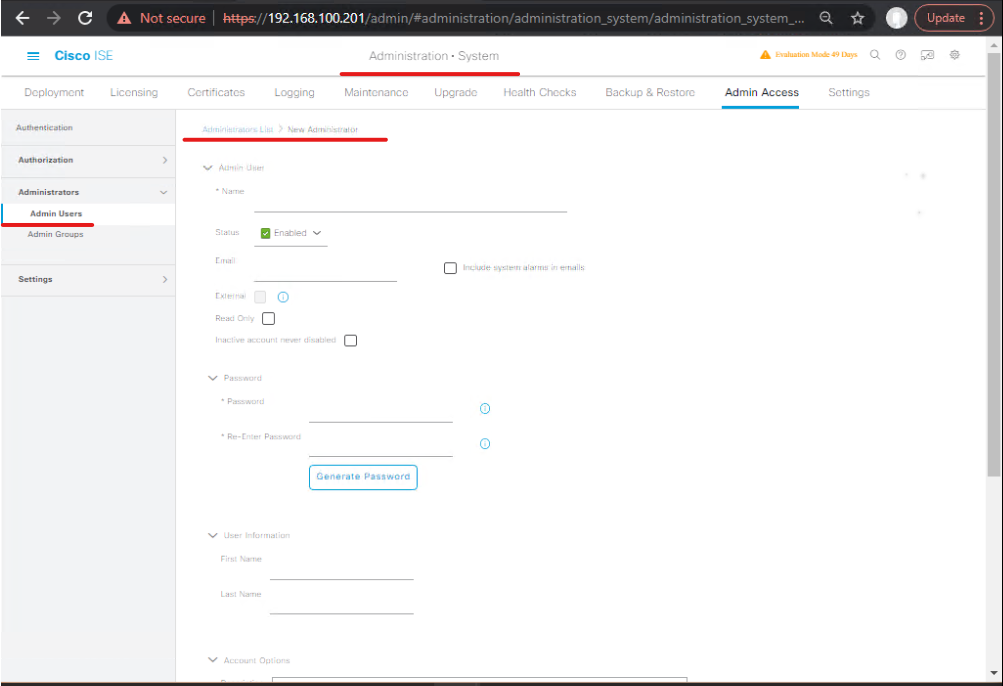
- Create ERS Admin (least privilege)
- Administration → Admin Access → Administrators → Add
- Create user:
ers_onboardwith ERS Admin role (or custom role limited to users/endpoints/guests). - [ISE Admin – ers_onboard role]
- Confirm ERS reachability (Automation Host)
curl -k -u ers_onboard:Str0ng! https://ise-pan.lab:9060/ers/sdk -I # Expect HTTP/1.1 200 OK (or 401 if creds wrong)
C. Create Identity Groups (Users & Endpoints)
Why: Normalize onboarding by assigning the right group at creation time.
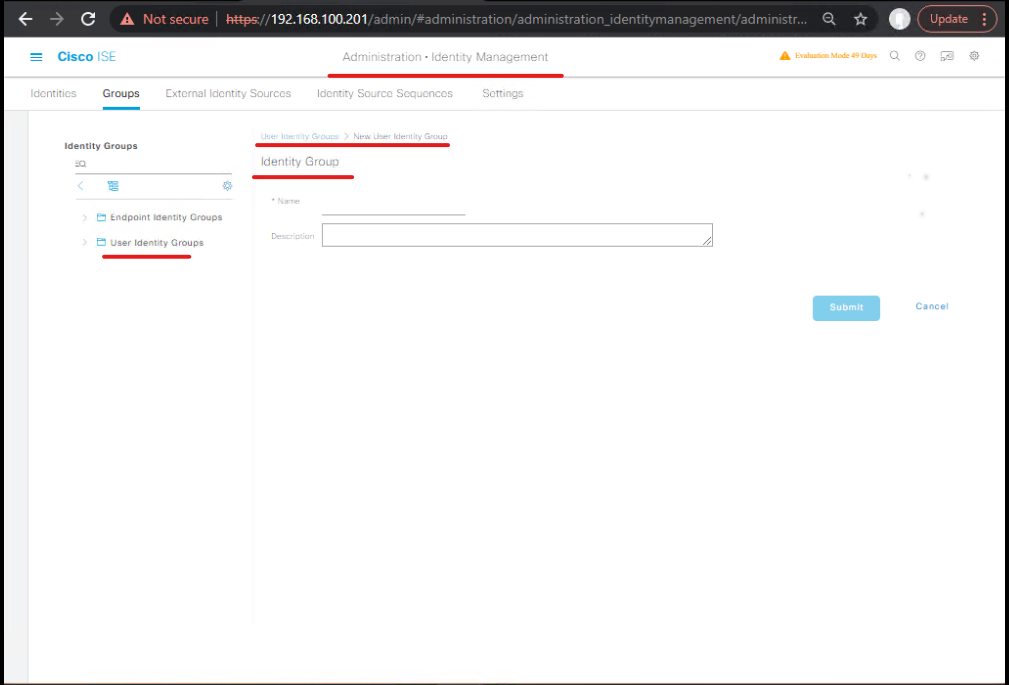
- User Identity Group (GUI)
- Administration → Identity Management → Groups → User Identity Groups → Add
- Name:
HR-Employees - [User Identity Group – HR-Employees]
- Endpoint Identity Group (GUI)
- Administration → Identity Management → Groups → Endpoint Identity Groups → Add
- Name:
CORP-Laptops - [Endpoint Identity Group – CORP-Laptops]
ERS Validation (Automation Host)
# Get group IDs (store for scripts) curl -sk -u ers_onboard:Str0ng! https://ise-pan.lab:9060/ers/config/identitygroup?filter=name.EQ.HR-Employees | jq . curl -sk -u ers_onboard:Str0ng! https://ise-pan.lab:9060/ers/config/identitygroup?filter=name.EQ.CORP-Laptops | jq .
D. Automate Internal User Creation (ERS)
Tip: ERS content types vary by version. If you get 415 Unsupported Media Type, use the ERS media type shown in ISE ERS API Docs page (Developer Portal). Generic JSON often works in 3.x.
1) Create Internal User (API)
curl -sk -u ers_onboard:Str0ng! \
-H "Content-Type: application/json" -H "Accept: application/json" \
-X POST https://ise-pan.lab:9060/ers/config/internaluser \
-d '{
"InternalUser": {
"name": "jdoe",
"password": "TempP@ssw0rd!",
"firstName": "John",
"lastName": "Doe",
"email": "jdoe@corp.lab",
"enabled": true,
"changePassword": true,
"identityGroups": "ID:{{HR_EMPLOYEES_GROUP_ID}}",
"expiryDateEnabled": true,
"expiryDate": "2025-12-31 23:59",
"customAttributes": { "employeeId": "E12345", "dept": "Finance" }
}
}'
- Replace
{{HR_EMPLOYEES_GROUP_ID}}with the ID from the earlier GET. - [ISE → Users → Internal Users – jdoe visible]
2) Validate (GUI + Switch CLI)
- GUI: Users → Internal Users filter
jdoe→ verify attributes/group. - Switch (testing RADIUS auth quickly):
c9300# test aaa group radius ISE username jdoe password TempP@ssw0rd! new # Expect "User was successfully authenticated"
3) Update User (e.g., move group, set description)
# Get user ID
curl -sk -u ers_onboard:Str0ng! https://ise-pan.lab:9060/ers/config/internaluser?filter=name.EQ.jdoe | jq -r '.SearchResult.resources[0].id' > /tmp/jdoe.id
# PUT
curl -sk -u ers_onboard:Str0ng! -H "Content-Type: application/json" \
-X PUT https://ise-pan.lab:9060/ers/config/internaluser/$(cat /tmp/jdoe.id) \
-d '{"InternalUser":{"description":"Promoted to Sr Analyst","identityGroups":"ID:{{HR_EMPLOYEES_GROUP_ID}}"}}'
4) Disable / Delete (Leaver)
# Disable
curl -sk -u ers_onboard:Str0ng! -H "Content-Type: application/json" \
-X PUT https://ise-pan.lab:9060/ers/config/internaluser/$(cat /tmp/jdoe.id) \
-d '{"InternalUser":{"enabled":false}}'
# Delete (with change ticket reference)
curl -sk -u ers_onboard:Str0ng! -X DELETE https://ise-pan.lab:9060/ers/config/internaluser/$(cat /tmp/jdoe.id)
E. Automate Endpoint Creation/Update (ERS)
1) Create Endpoint (assign to Endpoint Group)
curl -sk -u ers_onboard:Str0ng! -H "Content-Type: application/json" \
-X POST https://ise-pan.lab:9060/ers/config/endpoint \
-d '{
"ERSEndPoint": {
"name": "LAPTOP-JDOE",
"mac": "AA:BB:CC:DD:EE:FF",
"description": "Corporate laptop for jdoe",
"staticGroupAssignment": true,
"groupId": "ID:{{CORP_LAPTOPS_GROUP_ID}}",
"customAttributes": { "assetTag":"AT-00912", "owner":"jdoe" }
}
}'
- [Context Visibility → Endpoints – record visible]
2) Validate on switch after endpoint authenticates
c9300# show authentication sessions mac aabb.ccdd.eeff details # Expect: Endpoint Identity Group=CORP-Laptops (if used in policy), dACL/SGT as designed
F. Automate Guest User Creation (ERS)
Prereqs: Guest Portal exists. Note Portal ID.
1) Find Portal ID
curl -sk -u ers_onboard:Str0ng! https://ise-pan.lab:9060/ers/config/portal | jq . # locate the Guest Portal (e.g., "Self-Registered Guest Portal") and copy its id
2) Create Sponsored Guest
curl -sk -u ers_onboard:Str0ng! -H "Content-Type: application/json" \
-X POST https://ise-pan.lab:9060/ers/config/guestuser \
-d '{
"GuestUser": {
"guestInfo": {
"firstName": "Amy",
"lastName": "Visitor",
"emailAddress": "amy@example.com",
"enabled": true,
"password": "GuestP@ss123",
"userName": "amy.visitor",
"validDays": 2
},
"portalId": "{{GUEST_PORTAL_ID}}",
"sponsorUserName": "sponsor1",
"status": "active"
}
}'
- [ Work Centers → Guest Access → Manage Accounts – amy.visitor]
3) Validate login on guest WLAN (WLC)
- WLC:
(Cisco Controller) > show wlan <id> (Cisco Controller) > debug aaa events enable - Client connects → webauth to portal → success.
G. Bulk Imports (ERS Bulk)
1) Prepare CSVs
- Internal Users
internaluser.csv(headers depend on version; typical):name,password,firstName,lastName,email,enabled,identityGroups,expiryDate,customAttributes.employeeId jsmith,TempP@ssw0rd!,John,Smith,jsmith@corp.lab,true,ID:{{HR_EMPLOYEES_GROUP_ID}},2025-12-31 23:59,E12346
2) Import
zip internaluser.zip internaluser.csv curl -sk -u ers_onboard:Str0ng! -H "Content-Type: application/zip" \ --data-binary @internaluser.zip \ https://ise-pan.lab:9060/ers/bulk/internaluser/import
3) Monitor Job
curl -sk -u ers_onboard:Str0ng! https://ise-pan.lab:9060/ers/bulk/status | jq . # Look for jobId; fetch its status/log curl -sk -u ers_onboard:Str0ng! https://ise-pan.lab:9060/ers/bulk/status/<jobId> | jq .
H. Post-Provisioning Policy Hooks (Optional but Recommended)
- Authorization Policy matches Identity Group = HR-Employees → full access.
- Endpoint Group = CORP-Laptops → posture required, DACL permit.
- Guest Users → Guest policy with time-bound access.
I. Audit & Rollback
- Audit:
- ISE: Operations → Reports → Admin Audit (who/what via ERS), Identity Reports.
- Save API responses and job logs.
- Rollback:
- Internal user: set
enabled=falseor DELETE. - Endpoint: DELETE or clear group/attributes.
- Guest: status to
disabledor DELETE.
- Internal user: set
- Keep a Change Ticket ID in
description/customAttributes.changeId.
Expert-Level Use Cases
- HR-Driven JML (Joiner/Mover/Leaver): Workday/SuccessFactors → iPaaS (Boomi/Mulesoft) → ISE ERS: create user, set group, expiry; mover updates groups; leaver disables user and clears endpoints.
- Just-In-Time Contractors: ITSM ticket approved → ISE InternalUser with 30-day expiry and
contractIdattribute; auto disable after expiry; nightly report to security. - VIP Device Fast-Track: Asset tool posts MAC + SGT request → ISE Endpoint in
CORP-Laptops, DACL permit; notify NOC on success. - Bulk New Site Go-Live: Import hundreds of user & device records via ERS bulk; job monitoring exports failure CSV for rerun.
- Guest Event Automation: Event portal creates guest users for attendees with validDays=2; SMS delivery; post-event cleanup API.
- Zero-Trust Staging: New users created with limited SGT; posture/EDR registration flips attribute → policy grants full access.
- IoT Warehouse Onboarding: CMDB feed → ISE Endpoints with OUI classification +
zoneattribute; policy maps SGT per zone. - Self-Service Device Registration: Portal → API adds Endpoint with owner attribute; nightly script revokes stale devices >90 days.
- Emergency Disable: SOC webhook disables InternalUser across ISE in seconds; optional bulk action for incident.
- M&A User Migration: Map source directory to ISE Internal Users with interim groups; phased cutover; API adjusts attributes post-directory consolidation.
Validation Checklists
ISE/ERS Readiness
- ERS enabled (GUI)
- ERS admin created
curl -Ito/ers/sdk= 200.- Firewall/ACL permits Automation Host → 9060/tcp.
Identity Objects
- User Group
HR-Employeespresent. - Endpoint Group
CORP-Laptopspresent. - Policy references these groups.
Onboarding Run
- InternalUser
jdoecreated (GUI) - Endpoint
AA:BB:CC:DD:EE:FFcreated (GUI) - Guest
amy.visitorcreated (GUI) - Switch CLI shows correct dACL/SGT after auth.
- Bulk job status = Success
Audit & Rollback
- Admin Audit log entries exported (PDF/CSV).
- Rollback tested: disable/delete user & endpoint; logs captured.
FAQs – Cisco ISE REST API Advanced (Automating User Onboarding)
FAQ 1. How do I enable REST API access on Cisco ISE?
- GUI Path:
- Navigate to Administration → System → Settings → API Settings
- Enable ERS (External RESTful Services).
- Check Enable ERS for Read/Write.
- Save changes.
- CLI Validation:
ise/admin# show running-config | include ers ers-api: enabled: true write-access: true
FAQ 2. Which user roles are required to use ISE REST APIs for onboarding?
- The account must have ERS Admin or ERS Operator privileges.
- GUI Check: Administration → System → Admin Access → Administrators → Assign Role.
- CLI Check:
ise/admin# show user all | include ers
FAQ 3. How do I generate an API request for onboarding a new user?
- Example (using curl):
curl -k -u admin:Password123 \ -H "Content-Type: application/json" \ -X POST https://ise01.networkjourney.com:9060/ers/config/internaluser \ -d '{ "InternalUser": { "name": "student01", "password": "Test123!", "firstName": "Student", "lastName": "One", "email": "student01@lab.local", "enabled": true } }' - GUI Validation: Navigate to Administration → Identity Management → Identities → Internal Users. Verify that
student01was created.
FAQ 4. Can I bulk-import users with REST API?
- Yes, loop API calls with a script (Python preferred).
- Python Snippet:
import requests, json url = "https://ise01.networkjourney.com:9060/ers/config/internaluser" headers = {"Content-Type": "application/json"} auth = ("admin", "Password123") users = [ {"name": "userA", "password": "Pass@123"}, {"name": "userB", "password": "Pass@123"} ] for u in users: payload = {"InternalUser": {**u, "enabled": True}} r = requests.post(url, headers=headers, auth=auth, data=json.dumps(payload), verify=False) print(r.status_code, r.text) - Validation: Refresh GUI user list or run API GET request.
FAQ 5. How do I validate a REST API call was successful?
- Response Codes:
- 201 → Created successfully
- 200 → Success (for GET/PUT)
- 400 → Bad request (check JSON format)
- 401 → Unauthorized (invalid API user/role)
- CLI Debugging:
ise/admin# show logging application ise-ers.log
FAQ 6. How do I integrate REST API onboarding with Active Directory users?
- REST API cannot create AD users (since AD is external), but you can:
- Use REST API to assign users to ISE groups that map to AD groups.
- Sync policy mapping automatically with AD identity store.
- GUI Validation: Administration → Identity Management → External Identity Sources → Active Directory.
FAQ 7. What security measures should I follow for REST API access?
- Use HTTPS only (ISE runs API on port
9060). - Create dedicated ERS accounts (not superadmin).
- Rotate API passwords with automation (Ansible, Hashicorp Vault).
- CLI Validation:
ise/admin# show application status ise # Ensure "ise-ers" service is running
FAQ 8. How do I use REST API for onboarding BYOD users automatically?
- Process Flow:
- Endpoint registers on Guest/BYOD portal.
- Custom workflow triggers API call to create InternalUser.
- Assign BYOD group dynamically.
- GUI Validation: Check Policy Sets → Authentication Policy → Condition → User Group (BYOD).
FAQ 9. Can I delete or update users using REST API?
- Update User (PUT example):
curl -k -u admin:Password123 \ -H "Content-Type: application/json" \ -X PUT https://ise01.networkjourney.com:9060/ers/config/internaluser/{userId} \ -d '{"InternalUser": {"enabled": false}}' - Delete User:
curl -k -u admin:Password123 \ -X DELETE https://ise01.networkjourney.com:9060/ers/config/internaluser/{userId} - Validation: GUI → Internal Users list.
FAQ 10. What are common troubleshooting issues in REST API onboarding?
- 401 Unauthorized → Wrong user role (must be ERS Admin).
- 403 Forbidden → ERS not enabled in GUI.
- 500 Internal Error → Wrong JSON format or system service error.
- Timeouts → Check firewall blocking port
9060. - Validation: Always cross-check via:
- GUI: Internal Users → User List.
- CLI:
ise/admin# show logging application ise-ers.log tail
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes (Key Takeaways)
- Automate everything: users, endpoints, guests, attributes, expiries.
- Always lookup → decide → act → validate → audit → rollback.
- Standardize groups and attributes first; APIs will then be deterministic and safe.
- Keep evidence packs (CLI outputs, job logs) for compliance.
Upgrade Your Skills — Start Today
For production-ready scripts, Postman collections, and live labs (ERS/pxGrid, identity lifecycle, bulk/guest automation), subscribe to Network Journey on YouTube and join 4-month instructor-led CCIE Security Mastery. Get the ISE Onboarding Automation Pack: ready-to-use ERS scripts, CSV templates, and validation checklists.
Course outline & enrollment: https://course.networkjourney.com/ccie-security/
Fast-Track to Cisco ISE Mastery Pro — Lead Funnel
- You will build: API-driven onboarding (HR/ITSM → ISE), posture+TrustSec enforcement, SIEM-driven ANC, HA/DR runbooks.
- Included: 60+ guided labs, 25+ runbooks, ERS/pxGrid code, Postman/Ansible packs, audit templates.
- Outcome: Slash onboarding time from hours to seconds, with zero-touch and full compliance trails.
Reserve your seat now to receive pre-class lab prep + artifacts.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



![[Day 25] Cisco ISE Mastery Training: Dynamic VLAN Assignment in Wired Networks](https://networkjourney.com/wp-content/uploads/2025/08/Day-25-Cisco-ISE-Mastery-Training-Dynamic-VLAN-Assignment-in-Wired-Networks.png)