[Day 12] Cisco ISE Mastery Training: TACACS+ Overview & Use Cases
Table of Contents
Introduction
TACACS+ (Terminal Access Controller Access Control System Plus) is the go-to protocol for device administration control in enterprise networks. Unlike RADIUS, which is primarily for network access (wired/wireless), TACACS+ is designed for controlling administrative access to routers, switches, firewalls, and other network gear.
In Cisco ISE, TACACS+ centralizes the authentication, authorization, and accounting of network device administrators. This is critical in multi-admin environments where tracking every login, command execution, and privilege level change is necessary for compliance, auditing, and security.
With TACACS+ in ISE, you can:
- Grant different privilege levels to different users.
- Log every administrative action.
- Enforce multi-factor authentication for device logins.
- Ensure unauthorized users cannot access device CLI.
Problem Statement
In large networks:
- Admin credentials are often shared among engineers — a huge security risk.
- Local device accounts make it difficult to revoke access when someone leaves.
- Tracking who ran what command is nearly impossible without centralized logging.
Without TACACS+, you’re left with scattered admin accounts, weak accountability, and no granular command control — a compliance nightmare.
Solution Overview
Cisco ISE with the Device Administration Service (TACACS+) solves this by:
- Acting as a central TACACS+ server for all network devices.
- Authenticating admins via corporate Active Directory or internal ISE database.
- Authorizing commands based on roles, privilege levels, or policy sets.
- Storing detailed accounting logs for every admin action.
Sample Lab Topology
Lab Components:
- ISE 3.x running in VMware/EVE-NG.
- Catalyst Switch (access & core role).
- Cisco WLC for wireless device admin demo.
- Two endpoints (Admin PCs) with SSH client.
- Active Directory Server (optional for external auth).
Diagram Description:
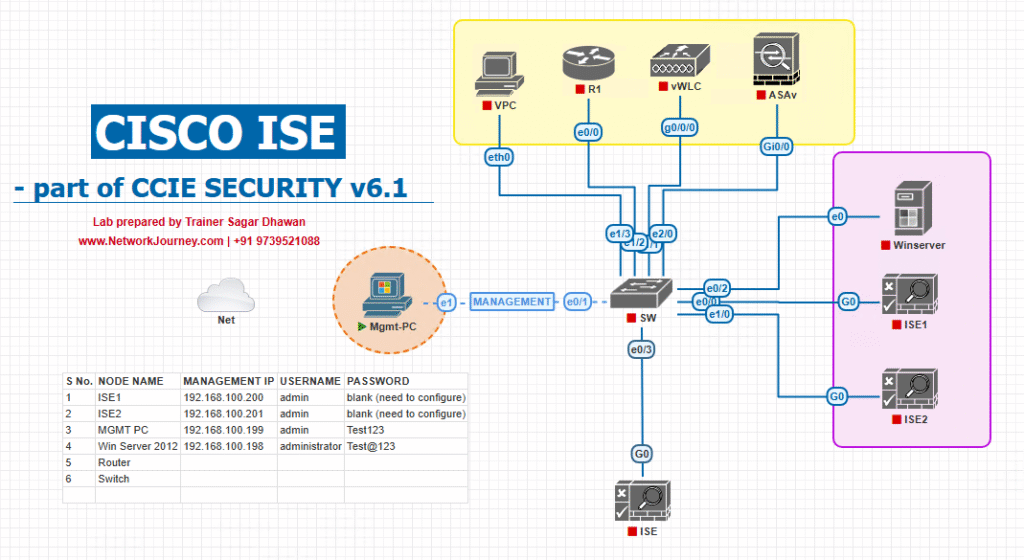
- Admin PCs connect via SSH to Switch/WLC.
- Switch/WLC sends TACACS+ requests to ISE.
- ISE verifies credentials, applies admin role policies, and logs activities.
Step-by-Step GUI Configuration Guide
Step 1 – Enable TACACS+ on ISE
- Log in to ISE GUI.
- Go to Administration → System → Deployment.
- Select your ISE node.
- Under TACACS+ Service, enable the checkbox.
- Save & restart application services if prompted.
- [Screenshot: ISE Deployment TACACS+ Service Enabled]
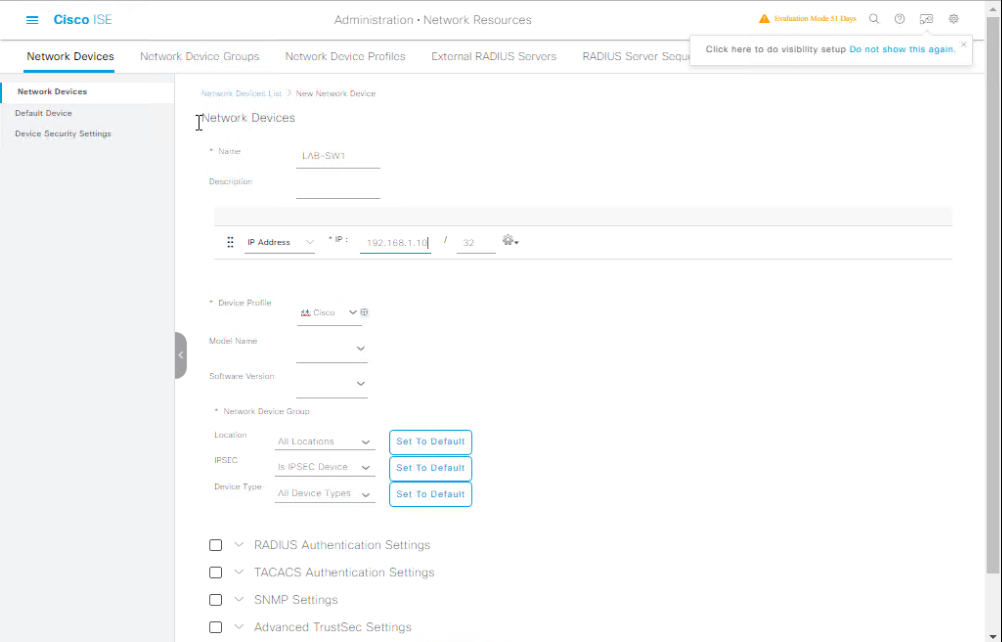
Step 2 – Add Network Device for TACACS+
- Go to Administration → Network Resources → Network Devices.
- Click Add.
- Name:
LAB-SW1 - IP Address:
192.168.1.10(switch mgmt IP) - Enable TACACS+ Authentication Settings.
- Set a shared secret (must match switch config).
- Save.
- [Screenshot: Network Device TACACS+ Config]
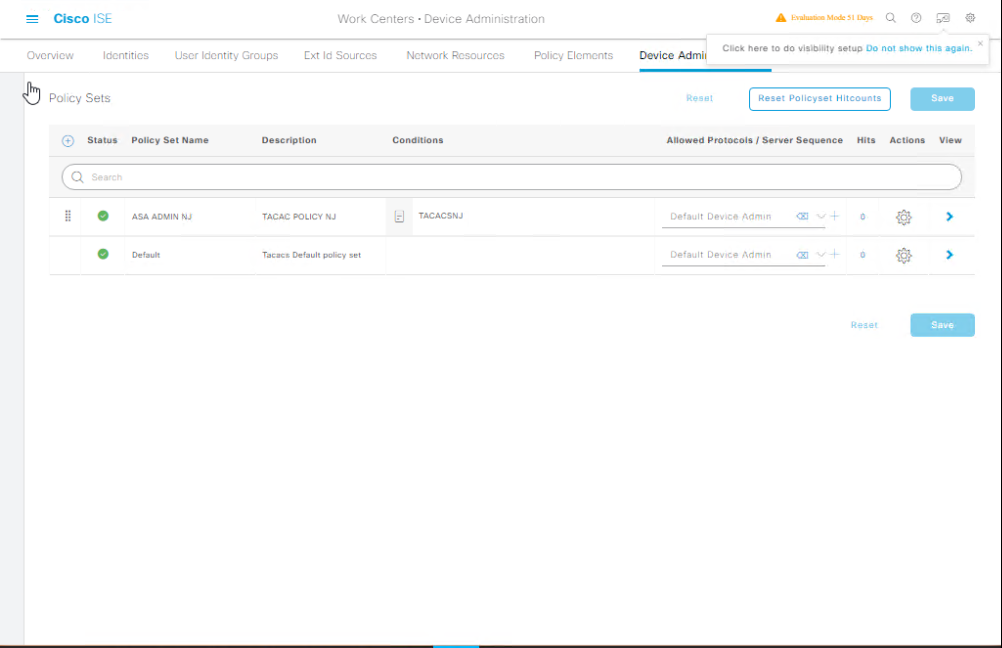
Step 3 – Create Device Admin Policy Set
- Go to Work Centers → Device Administration → Policy Sets.
- Create a new Policy Set named
Switch_Admin_Access. - Conditions:
Device: Device Type = Switch
- Authentication Policy: Use Internal Users or AD join point.
- Authorization Policy: Map users to Privilege Levels (e.g., 15 for full access, 1 for read-only).
- [Screenshot: TACACS+ Policy Set Screen]
Step 4 – Create Command Sets (Optional Granular Control)
- Go to Work Centers → Device Administration → Policy Elements → Command Sets.
- Create
Full_Access(Permit All Commands). - Create
Read_Only(Permitshowcommands, denyconfigurecommands).- [Screenshot: TACACS+ Command Set Creation]
Step 5 – Switch CLI Configuration
! Enable AAA aaa new-model ! Define TACACS+ servers tacacs server ISE1 address ipv4 192.168.1.50 key cisco123 ! Enable device admin via TACACS+ aaa authentication login default group tacacs+ local aaa authorization exec default group tacacs+ local aaa accounting commands 15 default start-stop group tacacs+ ! Optional: Fallback to local if ISE is down aaa authentication login default group tacacs+ local ! Enable privilege level support aaa authorization commands 15 default group tacacs+ local
Step 6 – Validation
- SSH from Admin PC to switch:
ssh admin@192.168.1.10
- Authenticate with ISE user credentials.
- Check ISE Live Logs → TACACS+ Authentication for login records.
- Run a few commands (e.g.,
show run) and confirm they appear in TACACS+ Accounting logs.
FAQs – Cisco ISE TACACS+
- What’s the primary difference between TACACS+ and RADIUS in ISE?
- TACACS+ is used for device administration (managing switches, routers, firewalls, etc.) and separates authentication, authorization, and accounting functions.
- RADIUS is used for network access control (wired, wireless, VPN). In ISE, you can run both on the same node.
- Which TCP/UDP ports does TACACS+ use, and do I need to open them in the firewall?
- TACACS+ uses TCP port 49 by default. TCP ensures reliable delivery of authentication requests and accounting logs. You must allow TCP/49 between the network devices and the ISE node.
- Can I integrate TACACS+ with Active Directory for authentication?
- Yes. In ISE, you can join the node to AD and map TACACS+ policies to AD groups (e.g.,
NetAdmin_FullorNetOps_ReadOnly). This eliminates the need to create separate local ISE accounts.
- Yes. In ISE, you can join the node to AD and map TACACS+ policies to AD groups (e.g.,
- How do I restrict an engineer to read-only access on network devices?
- Use TACACS+ Command Sets in ISE.
- Create a Command Set that allows only
showcommands. - Deny
configure,reload, and other privileged commands. - Apply it in the Authorization Policy for that user/group.
- Create a Command Set that allows only
- Use TACACS+ Command Sets in ISE.
- What happens if ISE is unavailable — will I be locked out of devices?
- Not if you configure a local fallback on your network devices:
aaa authentication login default group tacacs+ localThis ensures that local accounts can still log in if TACACS+ is unreachable.
- Not if you configure a local fallback on your network devices:
- Can TACACS+ log every command an admin runs?
- Yes. TACACS+ Accounting in ISE can log:
- Start/stop times of device sessions
- Commands executed, along with timestamps
- Privilege level changes
- Yes. TACACS+ Accounting in ISE can log:
- Do I need a special license in ISE for TACACS+?
- Yes. The Device Administration license is required to use TACACS+ in ISE. Without it, TACACS+ configuration and policies are not available.
- Can I have different TACACS+ policies for switches, firewalls, and wireless controllers?
- Absolutely. In ISE Policy Sets, use Device Type or Location conditions to apply unique policies and command sets for each device category.
- How can I test TACACS+ connectivity from the device to ISE?
- On the network device (e.g., Cisco switch):
test aaa group tacacs+ admin password legacyOr from ISE CLI:ise/admin# ping <device_ip> ise/admin# show loggingCheck Live Logs → TACACS+ in ISE GUI for the test request.
- On the network device (e.g., Cisco switch):
- Can I run TACACS+ and RADIUS simultaneously on the same ISE node?
- Yes. ISE can handle both services concurrently, using separate policy sets for TACACS+ (Device Admin) and RADIUS (Network Access). This is common in real-world deployments.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
By enabling TACACS+ on Cisco ISE, you gain granular control over network device administration, ensure accountability, and meet compliance requirements. This is a must-have for organizations aiming for strong operational security.
Fast-Track to Cisco ISE Mastery Pro
Ready to take your Cisco ISE skills to the next level?
I run a focused an intensive 4-month CCIE Security Instructor-Led Training — covering ISE, Firewalls, VPN, SD-WAN, and advanced security architectures.
- This is not just theory — it’s live labs, real enterprise scenarios, and direct mentorship.
- Seats are limited. Secure your spot today at: course.networkjourney.com/ccie-security
- Learn. Lab. Master. Become the network security expert companies hire.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088


![[Day 23] Cisco ISE Mastery Training: Guest VLAN & Critical VLAN Configuration](https://networkjourney.com/wp-content/uploads/2025/08/Day-23-Cisco-ISE-Mastery-Training-Guest-VLAN-Critical-VLAN-Configuration.png)
