[Day 120] Cisco ISE Mastery Training: Bulk Endpoint Management via API (ERS + OpenAPI)
Table of Contents
Introduction
In real networks, endpoints don’t trickle in—they arrive in waves: 300 cameras for a new building, 1,000 scanners for a retail rollout, 2,500 laptops post-merger. Manually clicking through Context Visibility → Endpoints isn’t just slow—it’s operational debt that creates drift between policy intent and reality.
This masterclass turns Cisco ISE into a programmable platform using ERS (External RESTful Services) and OpenAPI so you can create, tag, group, quarantine, and delete thousands of endpoints with repeatable, auditable workflows. You’ll build a lab where:
- You pre-stage new MACs into Endpoint Identity Groups (EIGs),
- Attach SGTs for TrustSec,
- Stamp custom attributes (Location, Owner, CostCenter),
- Quarantine with ANC on demand,
- And validate everything in ISE GUI, Live Logs, and network device CLI.
By the end, you’ll have a reusable CSV-driven + Python/cURL toolkit to run bulk endpoint operations with confidence.
Problem Statement
Operational gaps without automation
- New site cutovers require hundreds/thousands of pre-staged MACs for MAB/IoT. Doing it by hand is error-prone.
- Endpoint Identity Groups & SGTs must be applied consistently for authorization/DACLs/SGACLs. Human clicks drift.
- Rapid containment (ANC) for outbreaks requires batch action—seconds, not hours.
- CMDB/MDM/ServiceNow often becomes a “truth silo.” ISE lags unless you synchronize.
We need: Idempotent, scripted, bulk endpoint CRUD (Create/Read/Update/Delete) + tagging + quarantine, with verifiable outcomes.
Solution Overview
- Enable ERS & OpenAPI on ISE with a least-privileged ERS admin.
- Use ERS resources:
/ers/config/endpoint(create/update/delete/search)/ers/config/endpointgroup(lookup group UUIDs)/ers/config/sgt(lookup SGT UUIDs)/ers/config/ancendpoint/apply|clear(quarantine workflows)
- Drive bulk using:
- A CSV (name, mac, groupName, sgtName, description, location, custom attributes),
- Python requests (or Postman/cURL) with pagination & retries,
- Validation via GUI (Context Visibility, Live Logs), ERS GETs, and network device CLI (
show authentication sessions).
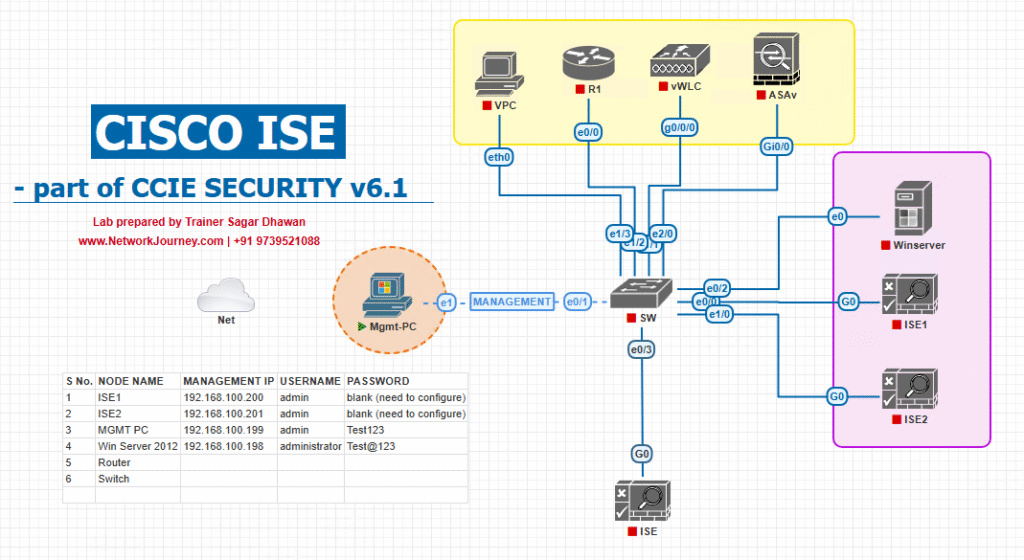
Sample Lab Topology
Platform: VMware/EVE-NG
Nodes
- ISE Policy Administration Node (PAN) + MnT (single-node lab), HTTPS/ERS on
9060/tcp. - Catalyst 9300 Switch (Access) for MAB test, uplink to core.
- WLC + AP (optional) for wireless MAB/EAP validation.
- Automation Workstation (Windows/Linux/Mac): Postman + Python 3.10+.
- Test Endpoints:
- IoT camera (MAB),
- Printer (MAB),
- Laptop (802.1X) to watch ANC behavior.
Logical Flow
- Workstation → ISE ERS API (CRUD, ANC).
- ISE pushes decisions to NADs (switch/WLC) during authZ.
- Switch/WLC enforces DACL/SGT/VLAN; ANC quarantine if applied.
Diagram:
Step-by-Step GUI Configuration Guide (with API & CLI)
A) ISE System Prep
- Enable ERS & OpenAPI
- Navigate: Administration → System → Settings → API Settings
- Check Enable ERS for Read/Write
- (Optional) Enable OpenAPI interactive docs.
- (Optional) Restrict ERS IP allowlist for security.
[ISE API Settings]
- Create ERS-only Admin
- Administration → System → Admin Access → Administrators
- Add user:
ers-adminwith ERS Admin (or custom role with only endpoint/anc/sgt read/write).
[ ISE Admins & Roles]
- Add user:
- Certificates & TLS
- Ensure ISE portal/ERS cert is CA-signed or import ISE CA into your workstation trust store.
[Certificates → System Certificates]
- Create Endpoint Identity Groups (EIG) & SGTs
- Work Centers → Profiler → Endpoint Identity Groups: add
IoT-Cameras,Printers
[ Endpoint Identity Groups]
- Work Centers → TrustSec → Components → Security Group Tags: add
IoT,Printers
[SGT Table]
- Optional: ANC Policies
- Operations → Adaptive Network Control: create policy
QUARANTINE(e.g., DACL QUAR-BLOCK or SGACL deny-all).
[ANC Policy]
B) First Contact: Test ERS with Postman/cURL
Postman Setup
- New Collection → Variable
ise_base=https://<ise-ip>:9060 - Auth: Basic Auth using
ers-admin. - Default headers:
Accept: application/jsonContent-Type: application/json
GET Endpoint Groups (find Group UUID)
GET {{ise_base}}/ers/config/endpointgroup?filter=name.EQ.IoT-Cameras
[Postman GET endpointgroup]
GET SGT (find SGT UUID)
GET {{ise_base}}/ers/config/sgt?filter=name.EQ.IoT
[Postman GET sgt]
Create One Endpoint (camera)
Example JSON payload (use your groupId/sgtId UUIDs):
{
"ERSEndPoint": {
"name": "camera-01",
"mac": "AA:BB:CC:11:22:33",
"description": "Lobby Cam",
"staticGroupAssignment": true,
"groupId": "<UUID-of-IoT-Cameras>",
"securityGroupId": "<UUID-of-SGT-IoT>",
"customAttributes": { "customAttributes": { "Location": "BLR-1F", "Owner": "Facilities" } }
}
}
POST {{ise_base}}/ers/config/endpoint
Expect 201 Created.
[Postman POST endpoint]
Verify in GUI
- Context Visibility → Endpoints: search MAC
AA:BB:CC:11:22:33
[Endpoints Table]
cURL equivalents (Linux/Mac)
curl -k -u ers-admin:'ChangeMe!' \ -H "Accept: application/json" -H "Content-Type: application/json" \ -X GET "https://<ise>:9060/ers/config/endpointgroup?filter=name.EQ.IoT-Cameras" curl -k -u ers-admin:'ChangeMe!' \ -H "Accept: application/json" -H "Content-Type: application/json" \ -d @camera.json \ -X POST "https://<ise>:9060/ers/config/endpoint"
C) Bulk Create/Update from CSV (Provided Script)
Your files (already generated):
- CSV template: ise_endpoints_template.csv
- Python script: ise_bulk_endpoints.py
Edit the script’s header (ISE host/creds/VERIFY_SSL).
ISE_HOST = "https://10.10.10.5:9060" ISE_USER = "ers-admin" ISE_PASS = "ChangeMe!" VERIFY_SSL = False
Open CSV and add rows (one per endpoint). Columns included:
name, mac, groupName, sgtName, description, location, customAttr1Key, customAttr1Value, customAttr2Key, customAttr2Value
Run (example)
python3 ise_bulk_endpoints.py apply-csv --file /path/to/ise_endpoints_template.csv
- The script will for each row:
- Lookup Endpoint Identity Group (by name) → UUID
- Lookup SGT (by name) → UUID
- Create the endpoint if not found, else Update
- Sleep briefly to avoid bursts
Validation
- GUI: Context Visibility → Endpoints, filter by
Location,Owner, or MAC.
[Endpoints with Custom Attributes] - ERS:
GET /ers/config/endpoint?filter=mac.EQ.AA:BB:CC:11:22:33 - Switch CLI (MAB or reauth to test policy):
# On Catalyst Access (sample) show authentication sessions interface Gi1/0/10 details show authentication sessions mac AA:BB:CC:11:22:33 detailsValidate AuthC, AuthZ, DACL/SGT, and Status.
D) Bulk Quarantine / Clear via ANC (Script & API)
Apply ANC to a device
python3 ise_bulk_endpoints.py anc-apply --mac AA:BB:CC:11:22:33 --policy QUARANTINE
- Validate in GUI: Operations → Adaptive Network Control → ANC Endpoints
[ANC Applied]
Clear ANC
python3 ise_bulk_endpoints.py anc-clear --mac AA:BB:CC:11:22:33
CLI Validation
- Force reauth (wired):
conf t interface Gi1/0/10 authentication control-direction in mab dot1x pae authenticator authentication periodic authentication timer reauthenticate 60 end clear authentication sessions interface Gi1/0/10 show authentication sessions interface Gi1/0/10 details - You should see DACL/SGT changes reflecting ANC.
E) Update, Move, or Delete Endpoints (Idempotent)
Update (change group/SGT/attributes)
Just edit CSV row → rerun apply-csv. The script PUT updates the endpoint.
Delete by MAC
python3 ise_bulk_endpoints.py delete --mac AA:BB:CC:11:22:33
- Validate: ERS GET returns 404 or absent; GUI endpoint removed.
Common ERS return codes to expect
- 200/201/204 = success,
- 401 = auth issue,
- 404 = not found,
- 409 = conflict (already exists),
- 415 = media type header mismatch,
- 422 = schema issues.
Expert-Level Use Cases
- Greenfield Site Cutover: Pre-stage 3,000 IoT MACs with Location/Owner attributes; run during maintenance window; validate with bulk GET and spot-check on access ports.
- Contractor Season: Create temporary Endpoint Identity Group + SGT; import contractor MACs with Expiry attributes; nightly job moves expired to Blacklist (or deletes).
- CMDB Sync: Nightly pull from ServiceNow or CMDB; diff against ISE
/endpointlist; add/update where drift detected; tag CostCenter. - MDM/EMM Alignment: From Intune/JAMF inventory, pre-stage corporate devices with SGT=Corporate; BYOD remains dynamic via profiling.
- Rapid Outbreak Containment: SOC feed (SIEM) posts suspicious MACs to an ANC queue; Python Lambda/container applies
QUARANTINEin seconds; clears automatically after remediation. - Mergers & Acquisitions: Mass ingest of legacy devices; map foreign groups to ISE EIG and SGTs; run transform rules in CSV pre-processor.
- Zero-Touch IoT: OUI-based bootstrap—create endpoints by OUI bucket with staticGroupAssignment and restricted DACL; elevate after validation job.
- Compliance Tagging: Weekly job tags endpoints missing posture → SGT NonCompliant; AuthZ maps that SGT to quarantine VLAN/portal.
- Lifecycle Governance:
lastSeen> 90 days? Move to Dormant group and reduce access; purge after 180 days. - High-Velocity Retail: Store opening playbook—site code in custom attribute; bulk run per-store CSV; single verification dashboard for go/no-go.
- SGACL Migration: Phase from DACL to TrustSec—bulk attach SGTs while keeping DACLs; flip SGACL once SXP/propagation validated.
- API-Driven Guest MAC Passthrough: Sponsor portal event posts auto-created guest MACs to a dedicated EIG with temporary access window via API.
- Blue/Green Policy Changes: Duplicate EIG/SGT sets; bulk pivot pilot endpoints to Green for A/B testing; roll back in minutes via API.
- Asset Owner Self-Service: Portal writes to CSV in SharePoint; pipeline validates and pushes to ISE; sends success/failure mail per row.
- Drift Remediation Dashboard: Scheduled job lists endpoints missing expected SGT/EIG vs policy intent; one-button “Remediate” calls ERS.
Validation Quick Checklist (GUI + CLI)
- Context Visibility → Endpoints shows new MACs with correct EIG/SGT and custom attributes.
- Operations → RADIUS → Live Logs shows expected AuthZ policy hits post-reauth.
- ANC tab lists quarantined endpoints when applied.
- Switch:
show authentication sessions mac <mac> detailsshows DACL/SGT/VLAN as intended. - cURL/Script GETs return expected payloads and HTTP 200s.
FAQs – Bulk Endpoint Management via API
1. What are the prerequisites for using Bulk Endpoint Management via Cisco ISE APIs?
- Answer:
You need:- ISE with ERS (External RESTful Services) API enabled.
- Administrator account with ERS Admin role.
- API client software like Postman or Python scripts with Requests module.
- Trusted certificate for HTTPS communication (optional but recommended for production).
- Network connectivity to TCP 443 of ISE nodes.
2. How do I authenticate my API requests in Cisco ISE?
- Answer:
Authentication is done using Basic Authentication with ISE admin credentials.
Headers must include:
Authorization: Basic <Base64(username:password)> Accept: application/json Content-Type: application/json
Always test with a single GET request first:
GET https://<ISE-IP>:9060/ers/config/endpoint
3. What is the recommended way to bulk-add endpoints in ISE?
- Answer:
Use the ERS API POST method with JSON body containing endpoint details. Example:
{
"ERSEndPoint": {
"name": "Finance-Laptop01",
"mac": "AA:BB:CC:DD:EE:FF",
"description": "Finance Department Endpoint",
"groupId": "<Group-UUID>"
}
}
For bulk imports, write a Python script that loops over a CSV file and POSTs each entry to ISE.
4. How can I validate if endpoints were successfully added via API?
- Answer:
Use GET calls or the ISE GUI. Example:
GET https://<ISE-IP>:9060/ers/config/endpoint?filter=mac.EQ.AA:BB:CC:DD:EE:FF
GUI Validation:
- Navigate to Administration > Identity Management > Identities > Endpoints.
- Search for the MAC address and confirm its group assignment and status.
5. Can I bulk-update endpoint attributes such as descriptions, groups, or profiles?
- Answer:
Yes, use PUT method with endpoint ID. Steps:
- GET the endpoint to retrieve its unique ID.
- PUT updated details.
Example:
PUT https://<ISE-IP>:9060/ers/config/endpoint/<id>
{
"ERSEndPoint": {
"id": "<id>",
"mac": "AA:BB:CC:DD:EE:FF",
"description": "Updated Finance Asset",
"groupId": "<New-Group-UUID>"
}
}
6. What’s the fastest way to delete multiple endpoints in bulk?
- Answer:
ISE doesn’t support bulk delete in one call, but you can automate via Python loop:
for mac in mac_list:
id = get_endpoint_id(mac)
requests.delete(f"https://<ISE-IP>:9060/ers/config/endpoint/{id}", headers=headers, verify=False)
GUI Validation: Recheck Endpoint Identity List to ensure entries are gone.
7. How do I find the correct Group ID (UUID) when assigning endpoints via API?
- Answer:
Use:
GET https://<ISE-IP>:9060/ers/config/endpointgroup
It returns all endpoint groups with their UUIDs.
Pro Tip: Keep a local JSON/CSV reference of your Group IDs for scripting efficiency.
8. Can I integrate Cisco ISE Bulk Endpoint Management with external systems like CMDB or Asset DB?
- Answer:
Yes. Many organizations integrate with: - ServiceNow CMDB → Auto-push new assets to ISE.
- Asset inventory systems → Sync endpoints daily.
- MDM platforms (Intune, AirWatch) → Update endpoint attributes (e.g., compliant vs. non-compliant).
This is achieved by building a middleware script that pulls from CMDB and POSTs to ISE via API.
9. What are the rate limits or performance considerations for bulk API calls?
- Answer:
- Cisco ISE API does not enforce hard rate limits, but best practice:
- Throttle requests to 5–10 per second.
- Use batch scripts with error handling & retries.
- Performance bottlenecks come from:
- ISE CPU utilization.
- Database replication in multi-node deployments.
Always test in lab before production import of thousands of endpoints.
10. What troubleshooting steps should I take if API bulk imports fail?
- Answer:
- Check ISE ERS logs (
/var/log/ise/ers.log). - Verify JSON syntax (missing commas, invalid MAC format).
- Ensure endpoint group UUID exists.
- Run ISE GUI test: manually add one endpoint, confirm group exists.
- Use
curlwith-vto debug request headers:
curl -k -u admin:password -H "Content-Type: application/json" -H "Accept: application/json" -X POST -d @endpoint.json https://<ISE-IP>:9060/ers/config/endpoint
- If still failing, enable API debugging logs in ISE > Operations > Logging.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
You now have a repeatable, auditable way to make ISE reflect policy intent at scale: create/update/delete endpoints, attach EIG + SGT, push ANC on demand, and prove results via GUI and CLI. Treat ISE as code—version CSVs/scripts, peer review changes, and pilot before sweeping production.
Fast-Track to Cisco ISE Mastery Pro
Ready to dominate ISE automation end-to-end?
I run a focused 4-month, instructor-led CCIE Security journey (hands-on ISE, TrustSec, pxGrid, automation).
Get the full course outline and reserve your seat here: course.networkjourney.com/ccie-security.
Bonus for early sign-ups: Postman collections, Python playbooks, and graded lab checklists tailored to your environment.
Subscribe to Network Journey on YouTube for weekly ISE deep dives, and apply for the cohort to get 1:1 lab feedback and career-grade projects.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



