[Day 121] Cisco ISE Mastery Training: Automated Guest User Creation via API
Table of Contents
Introduction
Imagine you’re managing the network for a global enterprise campus or hospitality chain. Every single day, you’re bombarded with requests: “We have 200 guests for today’s event… Please create accounts for them.” If you’ve ever sat in the Cisco ISE GUI and painfully clicked through the Sponsor Portal to create one guest at a time, you know how tedious, error-prone, and operationally unsustainable this becomes.
Now scale this to thousands of users per week, each requiring:
- Unique credentials
- Defined validity period (hours, days, weeks)
- Consistent sponsor attribution for audit
- Email or SMS notifications
- Immediate visibility in RADIUS Live Logs for authentication
Cisco Identity Services Engine (ISE) provides a powerful answer: the ERS (External RESTful Services) API. With it, guest creation stops being a manual chore and becomes a fully automated, programmable process. Instead of depending on human sponsors logging into portals, you tie ISE directly into your business systems — hotel PMS, event registration platforms, service desk portals, or even IoT onboarding tools.
This is more than just “automation for convenience.” It enforces security consistency, creates audit trails, removes manual bottlenecks, and empowers engineers to build self-service guest systems. When integrated properly, your network becomes as dynamic as your business needs — instantly creating, revoking, or extending guest access with no human delay.
In today’s Article, You will:
- Build a working lab (VMware/EVE-NG) with WLC, switches, ISE, and endpoints.
- Configure ISE GUI (enable ERS, set sponsor portal, guest types, policies).
- Execute API calls (curl + Python) to create, validate, update, and delete guest accounts.
- Verify results in both ISE GUI and CLI/RADIUS logs.
- Scale up: learn expert-level use cases like bulk event onboarding, PMS integration, kiosks, and IoT onboarding.
- Validate and troubleshoot every step with a checklist (GUI + CLI + API GET calls).
By the end of this Article, you will be able to fully automate guest provisioning, validate every detail, and integrate ISE with real-world business systems — the exact skills that separate an ISE operator from an ISE architect/automation expert.
Problem Statement
Real world pain points automation solves:
- Sponsor overload during large events → long queues, manual errors, inconsistent time windows.
- Poor audit trail and inconsistent naming/password policy when manual.
- No programmatic way to integrate guest provisioning with Event Management, ServiceNow, or Hotel PMS.
- Scalability: manual creation doesn’t scale to hundreds/thousands of guests daily.
- Delays caused by certificate/portal mismatch or sponsor portal mis-configuration.
Automation via ISE APIs solves these and enforces central policies, expiration, and logging. (Cisco)
Solution Overview
How Cisco ISE addresses it
- ERS / Open API: ISE exposes Guest APIs (create/search/update/delete) — typically through ERS endpoints (
/ers/config/guestuser) or the newer Open APIs. ERS APIs can use port 9060 (or standard HTTPS depending on version/config) and require ERS to be enabled on the PAN and an ERS-Admin/Operator account. (Cisco DevNet) - Sponsor Portal binding: Programmatic guest creation must specify and use a sponsored portalId (the portal the sponsor is allowed to use). ISE will only accept guest creation requests tied to a recognized portal/sponsor combination. (Cisco)
- Policy enforcement & audit: Guests created via API still follow configured Guest Types, Authorization Profiles and can be logged in ISE Monitoring & RADIUS Live Logs. This ensures the same security posture as GUI-created guests. (Cisco)
Sample Lab Topology
Topology summary (VM lab on VMware Workstation / ESXi or EVE-NG)
- ISE PAN (VM) — ISE Primary Admin Node, 8–16GB RAM, 4 vCPU, 200GB disk, mgmt IP
10.10.1.10 - ISE PSN (optional) — Policy Service Node (same or separate VM for realism)
10.10.1.11 - WLC (virtual or physical) — Cisco WLC (for captive portal flows)
10.10.1.20 - Access Switch (virtual/NX-OSv or real Catalyst) — L2/L3 switch for VLANs
10.10.1.5 - Guest laptop — connects to SSID
GUEST_WIFI(DHCP in VLAN 100) - Sponsor workstation — Admin workstation (has Postman / curl / Python)
10.10.1.100 - Optional: Event system / webhook (VM) — posts CSV or calls API to create guests
10.10.1.200
IP addressing (example)
- Mgmt network:
10.10.1.0/24 - Guest VLAN (100):
192.168.100.0/24 - RADIUS shared secret configured between WLC and ISE.
Diagram:
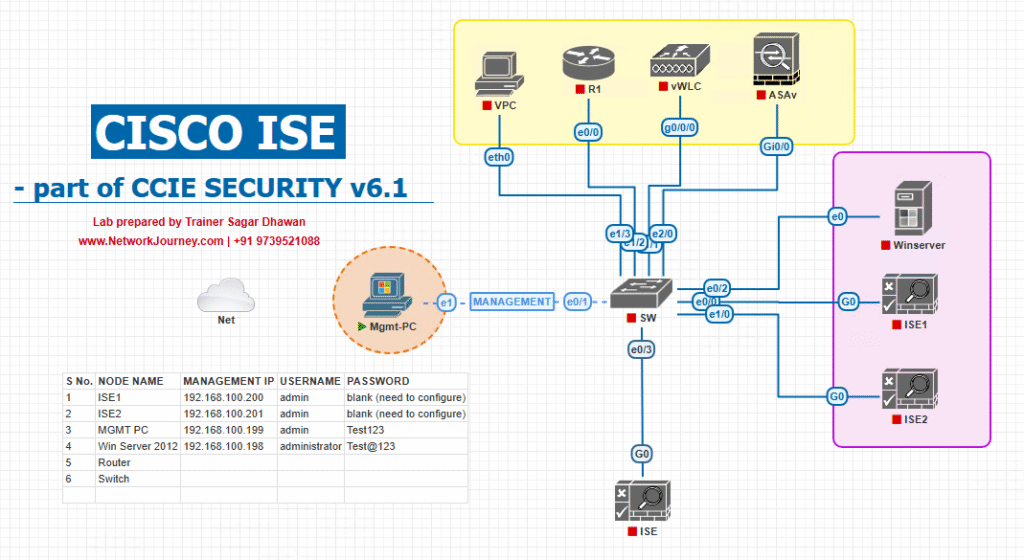
Notes: Use EVE-NG where you want multi-device realism (virtual switches & WLC images). VMware is simpler for single ISE VM + test client VMs. (Lab provisioning details are provided in class resources.)
Step-by-Step GUI Configuration Guide
Precheck (must do BEFORE API calls)
- DNS / NTP / Certificates: Ensure PAN hostname resolves, ISE time is correct, and trusted certs (preferred) are installed on PAN. If using self-signed certs for lab, accept them on client.
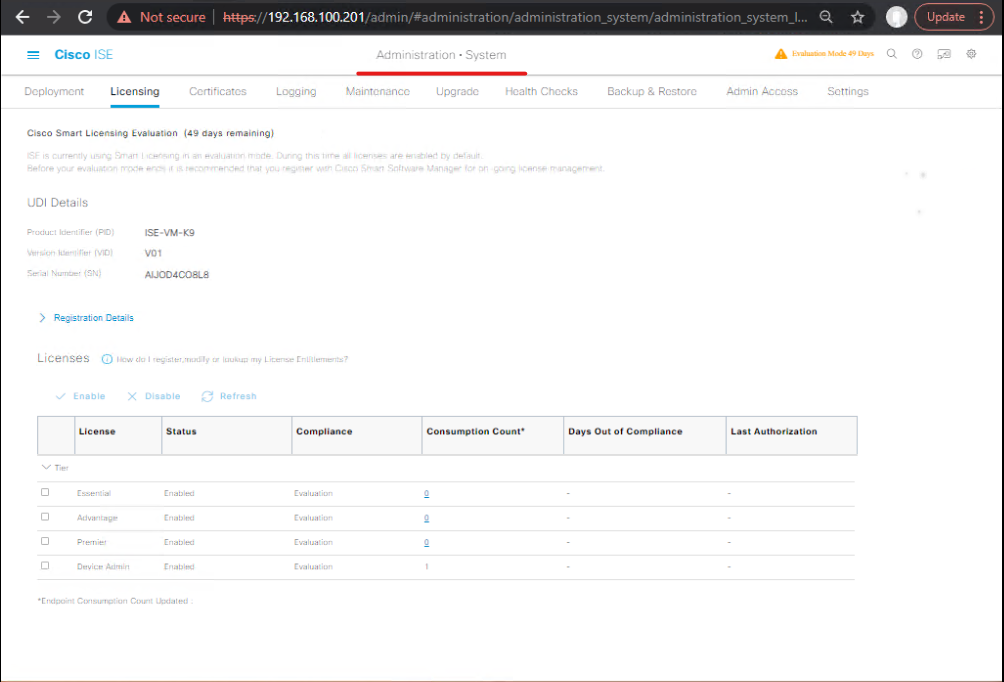
[ISE Dashboard > System time / Certificates] - Licensing & Personas: Verify ISE license and that PAN has appropriate Guest services enabled.
[ Administration > Sytem > Licensing]
A. Enable ERS (API access on PAN)
- GUI path: Administration → System → Settings → API Settings (or Administration > Settings > API Settings depending on version).
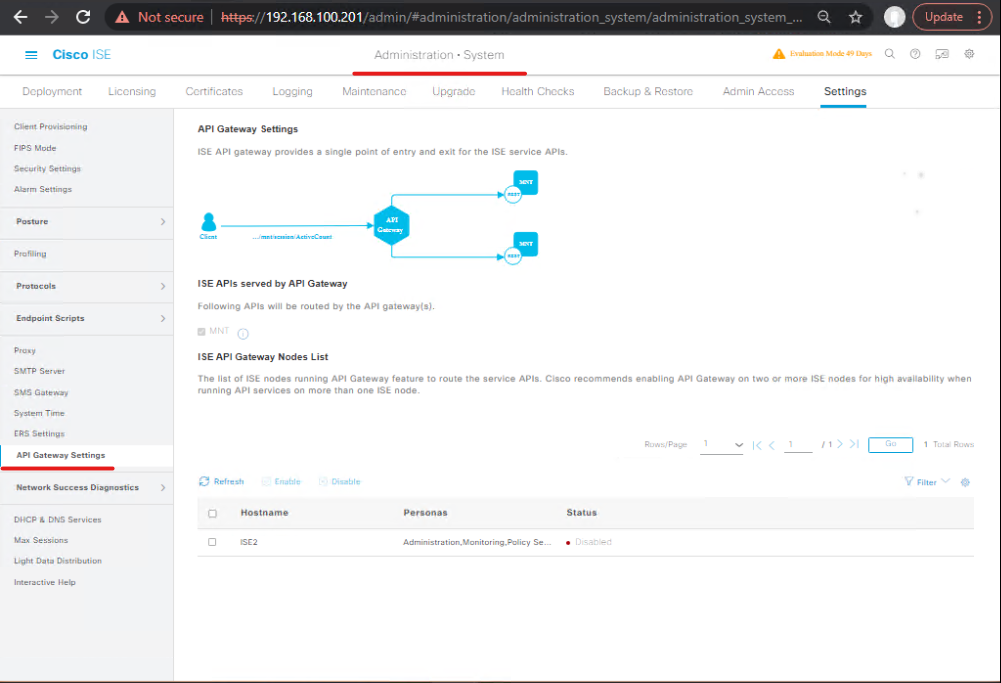
- Toggle ERS (Read/Write) → Save. This opens the ERS API on the PAN (port 9060 / or via API gateway depending on release). (Cisco DevNet, Cisco)
[Administration > Settings > API Settings — highlight ERS (Read/Write)] - (Optional) If using Open API features, enable Open API (Read/Write) as well.
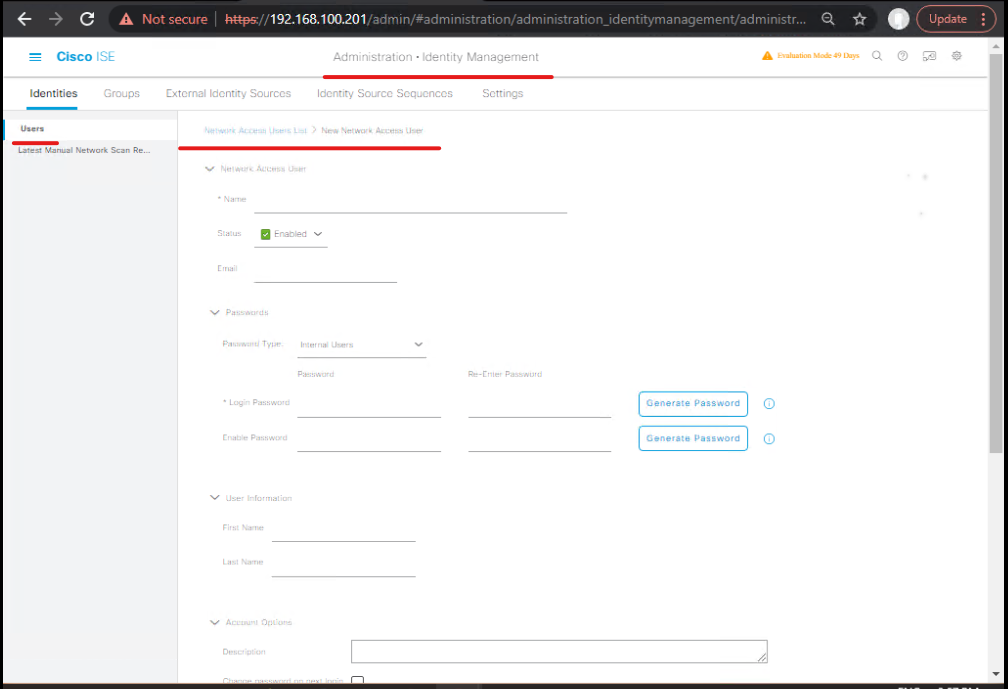
B. Create ERS Admin / Sponsor account (user must be in ERS group)
- GUI path: Administration → Identity Management → Identities → Users → +Add. Fill:
username=apisponsorpassword=StrongPass1email=apisponsor@example.com. Assign to the ERS Admin or ERS Operator group as required (ERS-Admin for create/delete). (GitHub, Cisco Community)
[Administration > Identity Management > Users > Add User] - Save — test by logging in to ISE GUI (optional).
C. Create Guest Sponsor Portal and Guest Type / Authorizations
- GUI path: Work Centers → Guest Access → Portals and Components. Create or edit a Sponsor Portal (give it a name). Note the portal’s ID (you will fetch portalId via API or locate in the GUI component).
[ Work Centers > Guest Access > Portals and Components > Sponsor Portal config]
- Create Guest Type and Guest Access Info (Default validity, location, notifications) if needed. [
- Create appropriate Authorization Profile in Policy > Policy Elements > Results > Authorization > Authorization Profiles and a Policy Set rule to match Guest users to that profile.
D. Confirm Sponsor Portal ID (via API)
Why: API create requests require
portalIdof the sponsor portal.
curl (GET portal list)
curl -s -k -u apisponsor:StrongPass1 \ -H "Accept: application/json" \ https://10.10.1.10:9060/ers/config/sponsorportal
Response contains portal objects with id and name. Copy the portal id. (You can also GET a specific sponsor portal by name; use the devnet docs for syntax.) (Cisco, Cisco DevNet)
E. Create Guest User — API (POST)
Minimal JSON body (fields required by your guest portal / type may differ):
{
"GuestUser": {
"guestType": "Contractor (default)",
"reasonForVisit": "Business meeting",
"portalId": "ce91b520-bb67-11e6-b562-005056873bd0",
"guestInfo": {
"userName": "chris1",
"firstName": "Chris",
"lastName": "Columbus",
"password": "Password1!",
"emailAddress": "chris@cisco.com",
"enabled": true,
"notificationLanguage": "English"
},
"guestAccessInfo": {
"validDays": "90",
"fromDate": "10/07/2025",
"toDate": "01/04/2026",
"location": "San Jose"
}
}
}
curl example:
curl -k -u apisponsor:StrongPass1 \ -H "Content-Type: application/json" -H "Accept: application/json" \ -d @guest.json \ https://10.10.1.10:9060/ers/config/guestuser
Expected: HTTP 201 Created and Location header containing the new guest ID. The DevNet sample Python script demonstrates this exact flow. (Cisco DevNet)
Python requests snippet (lab/proof-of-concept):
import requests, json
requests.packages.urllib3.disable_warnings()
url = "https://10.10.1.10:9060/ers/config/guestuser"
auth = ('apisponsor','StrongPass1')
payload = {...} # JSON above
r = requests.post(url, json=payload, auth=auth, verify=False, headers={'Accept':'application/json'})
print(r.status_code, r.headers.get('Location'))
Warning: verify=False is for lab only; in production always use trusted certs & validate TLS. (Cisco DevNet)
F. Validate Guest Creation (GUI & CLI)
GUI validation
- GUI: Work Centers → Guest Access → Guest Users → Search by username/email. You should see the created user and expiry details.
[Work Centers > Guest Access > Guest Users]
- GUI: Operations → RADIUS Live Logs — attempt portal login with guest credentials and verify authentication pass/fail and applied authorization profile. [Operations > RADIUS Live Logs]
CLI / API validation (command-line)
- GET by ID (from
Locationheader):
curl -k -u apisponsor:StrongPass1 -H "Accept: application/json" \ https://10.10.1.10:9060/ers/config/guestuser/<guest-id>
- Search (by username):
curl -k -u apisponsor:StrongPass1 -H "Accept: application/json" \ "https://10.10.1.10:9060/ers/config/guestuser?filter=userName.EQ.chris1"
Check enabled, guestAccessInfo and portalId fields. (Cisco DevNet)
G. Cleanup (Delete guest)
curl -k -u apisponsor:StrongPass1 -X DELETE \ https://10.10.1.10:9060/ers/config/guestuser/<guest-id>
Or use the GUI: Work Centers > Guest Access > Guest Users > Delete.
Expert Level Use Cases
Use Case A — Bulk Event Provisioning (CSV → ISE)
Goal: Create 500 guest accounts for a conference and send credentials via email.
Steps:
- Prepare CSV:
username,firstName,lastName,email,validDays,fromDate,toDate,reason. - Script: Python script reads CSV, builds JSON payload for each row (use sponsor portalId), POST
/ers/config/guestuser. Add exponential backoff and chunking (50 users per minute). Sample skeleton:
import csv, requests, time
def create_guest(row):
payload = {...} # map CSV to JSON
r = requests.post(url, json=payload, auth=auth, verify=True)
if r.status_code == 201:
guest_id = r.headers['Location'].split('/')[-1]
return guest_id
# loop CSV rows
- Validation: After each batch, call GET
/ers/config/guestuser?filter=userName.STARTSWITH.<prefix>and compare counts. Verify a sample login and monitor Operations > RADIUS Live Logs for successful authentication.
Pitfalls: throttle to avoid API gateway limits; ensure SMTP notifications are enabled & tested. (Cisco DevNet)
Use Case B — Hotel PMS Integration (automate guest creation at check-in)
Steps:
- On check-in event, PMS sends API call to middleware with guest details.
- Middleware calls ISE API with portalId matching hotel sponsor portal.
- Middleware returns credentials to PMS which prints them on keycards or emails to the guest.
- Validation: PMS shows
guest_idreturned from Location header; ISE GUI Search for email; attempt portal login; check RADIUS logs.
Hardening: rotate middleware API credentials, only accept signed webhooks from PMS, log all operations.
Use Case C — Self-Service Kiosk + Sponsor Approval Flow
- Self-service kiosk registers guest details to middleware (without immediate creation).
- Sponsor gets a push notification; sponsor clicks approve → middleware POSTs to ISE to create guest with sponsor credentials.
- Validation: sponsor portal audit logs and Guest Users list show sponsor name and time. Use API to fetch sponsor action logs if needed.
Use Case D — Temporary IoT device onboarding (MAC bound guest)
- Include
macAddressfield (if guest portal supports MAC). Create Guest user with MAC to bind to endpoint identity group & limited VLAN via Authorization Profile. - Validation: check Endpoint table in ISE or RADIUS Live Logs for successful MAB authentication. (Note: for IoT often better to use endpoint MAB & posture checks). (ise-support.com)
Recommended Troubleshooting Checklist
- ERS enabled? (Admin > System/Settings > API Settings) (Cisco DevNet)
- Using correct port (9060 vs 443)? (Cisco)
- API account has ERS role? (ERS-Admin/Operator) (Cisco Community)
- Correct
portalIdused? (GET sponsorportal) (Cisco) - Check RADIUS Live Logs for portal authentication and applied auth profile. (Cisco)
FAQs — Automated Guest User Creation via API (Cisco ISE)
1. Q: Why do I need a portalId to create a guest user via API? Where do I find it?
A:
- ISE binds every guest account to a sponsor portal. This ensures policy enforcement and audit attribution.
- Without the correct
portalId, your API request may return201 Createdbut the guest won’t show up in the GUI. - How to find it:
- GUI: Work Centers → Guest Access → Portals and Components → Sponsor Portal.
- API:
curl -k -u apisponsor:StrongPass1 -H "Accept: application/json" \ https://10.10.1.10:9060/ers/config/sponsorportal - Copy the
idfield (UUID).
- Validation: Create a guest using that
portalId, then confirm in GUI under Guest Access → Guest Users.
2. Q: I get HTTP 401 Unauthorized when creating a guest user. Why?
A:
- Common causes:
- ERS not enabled on PAN → Check Administration → System → Settings → API Settings. Enable ERS (Read/Write).
- Using wrong credentials → The API user must be in ERS-Admin group. Normal ISE admin users won’t work.
- Wrong port → Use
https://ISE-PAN:9060/ers/...(unless API Gateway is configured).
- Validation:
- Check ISE logs: Operations → Reports → Admin Audit Logs.
- Retry with
curl -vto see if the handshake failed or if credentials are bad.
3. Q: I get HTTP 201 Created, but I don’t see the guest in GUI. What’s wrong?
A:
- Most often: you used the wrong or missing portalId.
- Another cause: Guest created under a different sponsor portal than you’re checking in the GUI.
- Validation:
- API GET the
Locationheader returned in201 Created. Example:curl -k -u apisponsor:StrongPass1 -H "Accept: application/json" \ https://10.10.1.10:9060/ers/config/guestuser/<guest-id> - Confirm
portalIdandguestTypefields.
- API GET the
4. Q: Can I bulk-create 500 guests for an event using the API?
A:
- Yes, automation is ideal for this.
- Method 1: Loop through a CSV file and POST each row as a JSON payload.
- Method 2: Use a script with retry/backoff to avoid overloading ISE.
- Validation:
- After batch run, GET with a filter:
curl -k -u apisponsor:StrongPass1 -H "Accept: application/json" \ "https://10.10.1.10:9060/ers/config/guestuser?filter=userName.STARTSWITH.event" - Compare count with CSV rows.
- GUI: Guest Access → Guest Users → filter by prefix.
- After batch run, GET with a filter:
5. Q: Can I control guest account expiration via API?
A:
- Yes, using
guestAccessInfoblock. Example:"guestAccessInfo": { "validDays": "3", "fromDate": "24/08/2025", "toDate": "27/08/2025", "location": "HQ-Lobby" } - Validation:
- GUI: Check guest expiry in Guest Users.
- API: GET guest object and confirm
validDays/toDate.
6. Q: How do I update or disable an existing guest user?
A:
- Update (PUT): Modify fields like expiry or enabled status. Example:
curl -k -u apisponsor:StrongPass1 \ -X PUT -H "Content-Type: application/json" \ -d @update.json \ https://10.10.1.10:9060/ers/config/guestuser/<guest-id> - Disable (PATCH/PUT): Set
"enabled": false. - Validation:
- GUI: Guest user should show as Disabled.
- Try login → should fail; confirm in RADIUS Live Logs.
7. Q: My guest login at captive portal fails even though user exists. Why?
A:
- Causes:
- Guest tied to wrong portal.
- Wrong Authorization Profile in policy set.
- Password complexity mismatch.
- Validation:
- GUI: Operations → RADIUS Live Logs → Check reason (invalid creds vs denied by policy).
- CLI/WLC logs: Confirm redirection URL matches the portal configured.
8. Q: What’s the difference between creating guests via GUI, Sponsor Portal, and API?
A:
- GUI (Admin Portal): For administrators; one-off tasks.
- Sponsor Portal: Delegated guest creation (by HR, receptionist). Enforces sponsor attribution.
- API: Machine-to-machine; used for integration and bulk automation.
- Validation: All three write to the same Guest DB; verify consistency by searching guest in GUI after API creation.
9. Q: How do I secure API calls in production?
A:
- Do not use
verify=Falsein Python (only for lab). Install a trusted PKI cert on ISE. - Restrict ERS account with minimal privileges.
- Rotate API credentials every 90 days.
- Place API calls inside middleware with audit logging.
- Validation:
- Run API call with
verify=Trueand confirm no SSL errors. - Test expired credentials are rejected with 401.
- Run API call with
10. Q: How do I delete expired guest accounts automatically?
A:
- Method 1: ISE auto-purges based on Guest Type policy (e.g., auto-delete after expiry).
- Method 2: External script queries expired guests and DELETEs them. Example:
curl -k -u apisponsor:StrongPass1 -X DELETE \ https://10.10.1.10:9060/ers/config/guestuser/<guest-id> - Validation:
- GUI: Guest no longer visible.
- API GET returns
404 Not Found.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes — Key takeaways
- Always enable ERS on PAN and use an appropriate ERS role (Admin vs Operator). (Cisco DevNet)
- Guest creation via API requires portalId and a sponsor context — API calls must match a sponsor portal that ISE recognizes. (Cisco)
- Use postman / curl / Python for POC; upgrade to hardened middleware (rotate creds, TLS, logging) before production. (Cisco DevNet)
- Validate with both GUI (Guest Users / RADIUS Live Logs) and API (GET guestuser) — both views are necessary for troubleshooting. (Cisco)
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to the Network Journey YouTube channel and join the instructor-led classes. I run a focused an intensive 4-month instructor-led CCIE/ISE track (course outline here). Enroll for live mentoring, lab access, and the full workbook used in this masterclass. (Network Journey)
Fast-Track to Cisco ISE Mastery Pro
- I Offer a downloadable “ISE Guest Automation POC Kit” (sample Python scripts + lab topology VM images).
- offer: 4-month instructor-led course (full CCIE Security / ISE mastery) — link to course page for checkout. (Network Journey)
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 121] Cisco ISE Mastery Training: Automated Guest User Creation via API](https://networkjourney.com/wp-content/uploads/2025/08/Day-121-Cisco-ISE-Mastery-Training-Automated-Guest-User-Creation-via-API.png)

![VPN 0 and VPN 512 in Cisco SD-WAN: Backbone & Management Explained[CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/nj-blog-post-vpn0-vpn512.jpg)
![Ticket#6 - DHCP Not Working on Access Layer – Troubleshoot Snooping and Relay [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-Ticket-6.jpg)