[Day 122] Cisco ISE Mastery Training: Integration with Microsoft Intune
Table of Contents
Introduction
In today’s zero-trust enterprise networks, security is no longer about controlling who connects — it’s about ensuring the health and compliance of the device itself before granting access. Cisco Identity Services Engine (ISE) has long been the policy decision point (PDP) for identity-based network access control. But the real power comes when ISE integrates with mobile device management (MDM) or endpoint compliance platforms like Microsoft Intune (part of Microsoft Endpoint Manager).
Why does this matter?
Think about it:
- An employee walks into the office with a corporate laptop that has BitLocker disabled. Should this device access the core network?
- A contractor joins the Wi-Fi with their mobile phone — but the device is jailbroken and running outdated patches. Do we allow it on the corporate VLAN?
- A sales executive connects from home on a personal iPad — Intune confirms it’s compliant, encrypted, and has the latest OS version. Should we fast-track them to full access?
Without real-time compliance integration, NAC alone is blind. A device could authenticate correctly but still pose a major risk if it’s non-compliant or compromised.
This is where Cisco ISE + Intune integration becomes a game-changer:
- ISE leverages Intune’s endpoint compliance posture (encryption, jailbreak/root status, patch levels, antivirus status, OS version, etc.).
- ISE can enforce conditional access policies — e.g., compliant devices get full access, non-compliant ones get quarantined or redirected to remediation.
- Security teams gain end-to-end visibility of identity + device health, across wired, wireless, and VPN.
- Organizations achieve true Zero Trust Network Access (ZTNA) at the network layer, complementing Azure AD Conditional Access in the cloud.
This Article is designed not just to show you how to “click through” the integration, but to make you expert-level fluent in:
- Architecture flows: How ISE queries Intune for compliance decisions (SAML, OAuth tokens, API calls).
- Step-by-step config: From Azure AD app registration → ISE pxGrid/MDM integration → Intune compliance policies.
- Validation: Both GUI (ISE Live Logs, Intune Device Status) and CLI (ISE debug logs, API call testing with curl/Postman).
- Expert Use Cases: Device onboarding automation, BYOD security enforcement, remediation workflows, hybrid cloud security posture checks.
By the end of this Article, you won’t just know how to “integrate” ISE with Intune — you’ll be able to design, implement, validate, and troubleshoot enterprise-grade NAC + MDM integrations confidently.
Problem Statement (real-world)
- Enterprises want network access decisions (allow/quarantine/restrict) to depend on device posture (is the device Intune-managed and compliant?).
- Devices roam (Wi-Fi, wired, VPN) and modern OSes use MAC randomization, so MAC alone is unreliable — you need a GUID certificate binding from Intune.
- Microsoft retired older NAC APIs; integration must use Microsoft Graph / NAC 2.0 (Compliance Retrieval) and modern OAuth flows. Cisco ISE must be patched to versions that support these changes. (Cisco, Microsoft Learn)
Solution Overview (how ISE solves it)
- Azure app registration + OAuth client credentials allow ISE to call Microsoft Graph / Intune Compliance Retrieval to fetch device compliance and registration state. (Cisco)
- ISE uses External MDM integration to periodically poll Intune for device compliance (or retrieve on demand during RADIUS flow). The key data fields ISE can use include Compliance Status, Managed by Intune, MAC, and Registered Status — and when GUID is available ISE will prefer GUID over MAC. (Cisco)
- Use ISE Authorization Policy conditions (MDM dictionary attributes) in your Authorization Rules to grant/deny network access or apply remediation (e.g., Quarantine dACL, redirect to MDM enrollment). (Cisco)
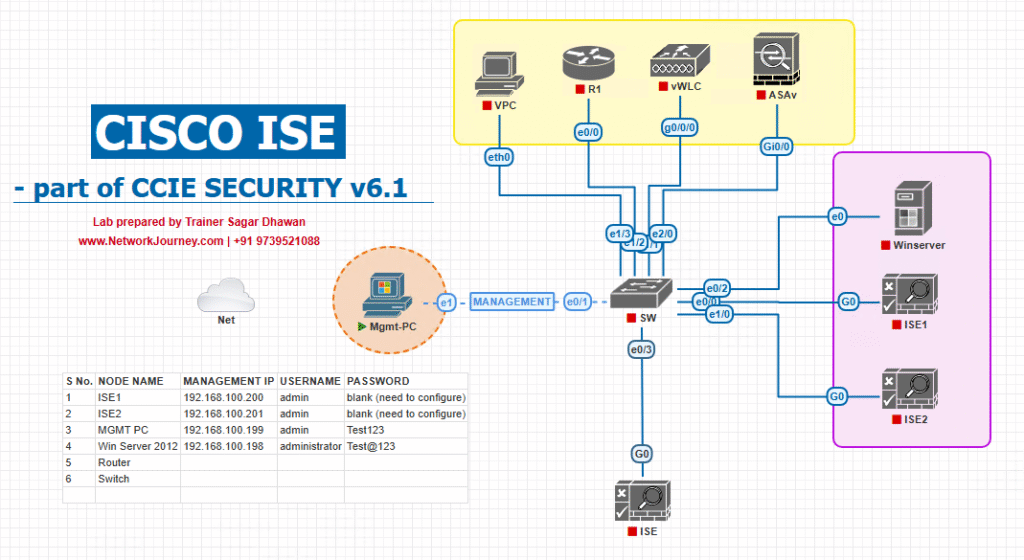
Sample Lab Topology
Lab platform: VMware for ISE (PAN/MnT + PSN), EVE-NG for NADs (Catalyst 9300), Windows Admin VM (Postman/PowerShell), Azure Tenant (Microsoft Endpoint Manager / Intune).
IP plan (example)
- ISE PAN/MnT:
10.10.10.10 - ISE PSN (RADIUS):
10.10.10.11 - Catalyst 9300 (wired access):
10.10.30.30 - WLC 9800-CL (wireless):
10.10.30.40 - Admin PC (Postman/curl):
10.10.40.10 - Azure/Intune: cloud (tenant id) — use real tenant for testing
Endpoint types: corporate laptops (Intune-enrolled), BYOD phones (unenrolled), VPN clients (AnyConnect).
Topology diagram
Step-by-Step GUI Configuration Guide (numbered — include CLI/API validation)
Before you begin: Ensure your Cisco ISE release is one of the supported releases for Microsoft Graph / NAC 2.0 integration. Cisco warns that older releases will not work with Microsoft changes — upgrade ISE to one of the supported releases/patches described in Cisco’s Intune integration guide. (Cisco)
PREP: Verify ISE and gather prerequisites
- Check ISE release/patch level. Required versions (examples from Cisco documentation): ISE 3.1 Patch 8, ISE 3.2 Patch 4 or later (for NAC 2.0 / Graph). If your ISE is older, upgrade before continuing. (Cisco)
CLI on ISE:ise/admin# show version ise/admin# show application status ise - Admin account: Create or use an ISE admin account with privileges to manage certificates and External MDM. (You’ll create an ERS user later for API tests.)
STEP 1 — Prepare certificates & Intune device certificate profile (on Intune side)
Objective: Intune must issue a certificate to devices where the certificate SAN includes the Intune GUID (so ISE can get GUID instead of a randomized MAC). Cisco requires the GUID to be included in the certificate SAN as a URI: ID:Microsoft Endpoint Manager:GUID:{{DeviceId}}. (Cisco)
- In Microsoft Endpoint Manager (Intune), create a SCEP or PKCS certificate profile (or use your PKI) that includes a Subject Alternative Name (SAN) entry:
- Type: URI
- Value:
ID:Microsoft Endpoint Manager:GUID:{{DeviceId}}
(This causes Intune to place device GUID into the client cert SAN). (Cisco)
[Intune – Create SCEP/PKCS Certificate Profile — SAN settings]
- Deploy the certificate profile to test devices (corporate laptops, iOS/Android as needed) and verify a certificate is installed and contains the SAN.
Validation (on device): check cert details and SAN includesID:Microsoft Endpoint Manager:GUID:....
STEP 2 — Register an Azure AD App & configure permissions (on Azure side)
Objective: Create an app in Azure AD that ISE will use (OAuth client credentials) to call Graph / Intune compliance APIs. Follow Cisco’s permission list. (Cisco, Microsoft Learn)
- Portal: Azure Portal → Azure Active Directory → App registrations → New registration.
- Name:
ISE-Intune-Integration-<tenant> - Supported account types: Accounts in this organizational directory only
- Register → Save.
- Name:
- Certificates & secrets: Upload the certificate you exported from ISE (next step) or create a client secret for test labs (certificate is recommended for prod). Cisco requires uploading the ISE certificate fingerprint to the app. (Cisco)
[Azure App Registration – Certificates & Secrets] - API Permissions: Add and then Grant admin consent for:
- Intune:
get_device_compliance(Application) — used for device state/compliance. - Microsoft Graph:
Application.Read.All(Application).
Then click Grant admin consent. (Exact permission names per Cisco doc.) (Cisco)
[Azure App Registration – API permissions]
- Intune:
- Make note of Application (client) ID, Directory (tenant) ID, and the OAuth 2.0 token endpoint (V2) (from Endpoints). You’ll need these for ISE External MDM configuration. (Cisco)
STEP 3 — Export ISE certificate & upload to Azure app (ISE GUI)
Objective: Export the certificate ISE will present to Azure for mutual trust and upload into the Azure app registration.
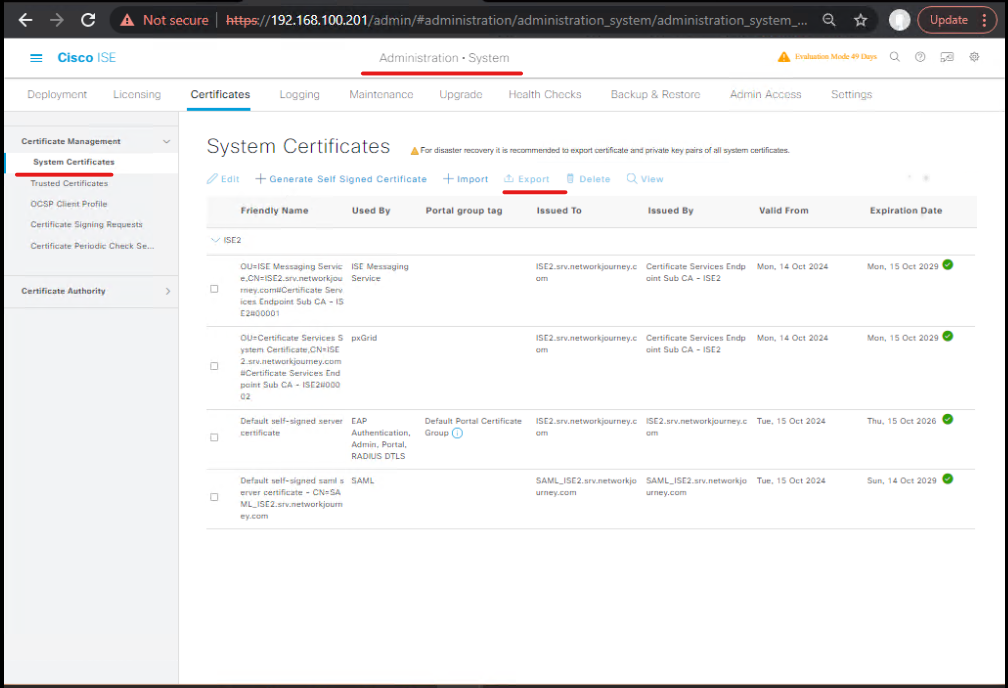
- In ISE GUI: Administration → System → Certificates → System → Certificates. Select the certificate used for admin/HTTPS (or a dedicated certificate), click Export → Certificate Only. Save PEM.
[ISE – Export Certificate] - In Azure AD (app registration): Certificates & secrets → Upload certificate — upload exported PEM. Verify thumbprint matches the certificate fingerprint from ISE (Cisco doc reminds to verify displayName matches CN). (Cisco)
STEP 4 — Add Microsoft root certs to ISE truststore
- Download Microsoft CA root certificates (e.g., Digicert chain per Cisco doc). Administration → System → Certificates → Trusted Certificates → Import. Mark “Trust for authentication within ISE” and “Trust for authentication of Cisco Services” as required. (Cisco)
[ISE – Trusted Certificates import]
Validation: After import, you should be able to show them in the trusted list.
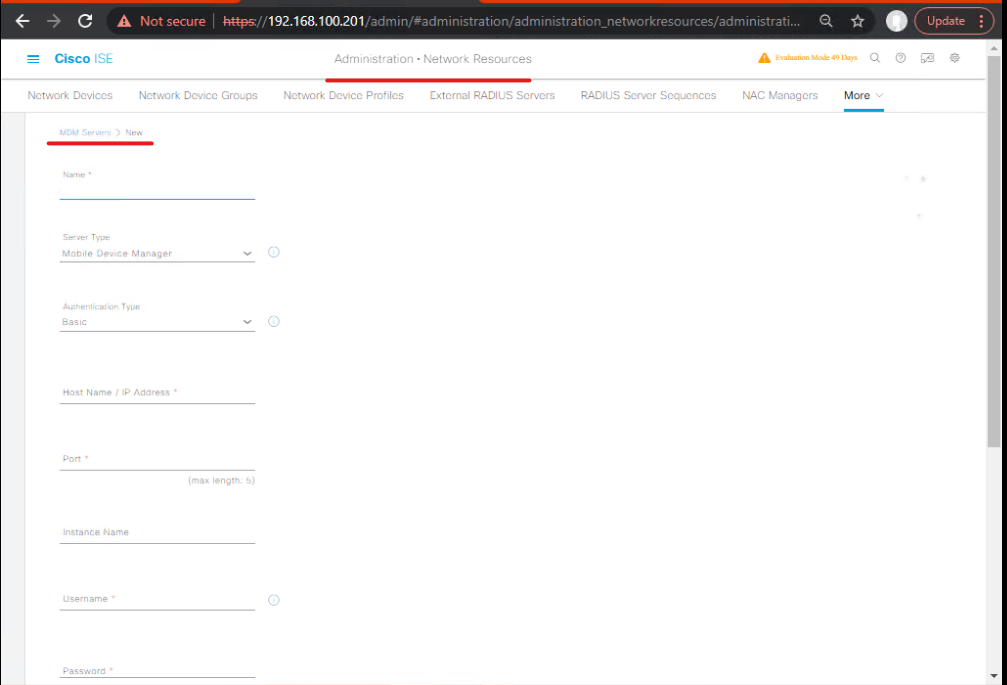
STEP 5 — Create External MDM entry in ISE (ISE GUI)
- ISE GUI:Administration → Network Resources → External MDM → Add.
- Name:
Intune-MDM-<tenant> - Authentication Type:
OAuth – Client Credentials - Auto Discovery URL:
https://graph.microsoft.com(use national cloud endpoint for special Azure clouds). (Cisco) - Client ID:
<Application (client) ID>(from Azure) - Token Issuing URL:
<OAuth 2.0 token endpoint (V2)>(from Azure Endpoints) - Token Audience: For many modern ISE releases set to
https://api.manage.microsoft.com//.default(Cisco doc explains token audience must match ISE release — some releases auto-populate this). IMPORTANT: follow the token audience guidance exactly for your ISE release. (Cisco) - Polling Interval / Compliance Device ReAuth Query: set based on scale (e.g., Polling 5m, ReAuth Query 60s) — these control how ISE polls Intune for compliance and how long ISE waits to re-auth devices. (Cisco)
- Upload the certificate (if client cert is used) or reference the client secret configured earlier.
- Click Test Connection. If successful, set Status = Enabled → Save. (Cisco)
[ISE – Add External MDM Step]
- Name:
Validation (GUI): The new MDM entry appears in Administration → Network Resources → External MDM; Test Connection should return success. (Cisco)
STEP 6 — Configure device certificates (AnyConnect / Wi-Fi / VPN) to carry GUID for VPN scenarios
- For VPN (AnyConnect): Ensure the AnyConnect VPN profile includes the Intune Device Identifier key (Cisco guidance / Intune app config) so AnyConnect logs
ID:Intune:DeviceID:<device id>and ISE picks it up during posture checks. Cisco documents the format and behavior (AnyConnect logs capture DeviceID and ISE uses it). (Cisco, Security CCIE Blog –)
Validation (VPN): On client, view AnyConnect logs for ID:Intune:DeviceID:<id>; On ISE, check endpoint attributes and RADIUS/MDM logs.
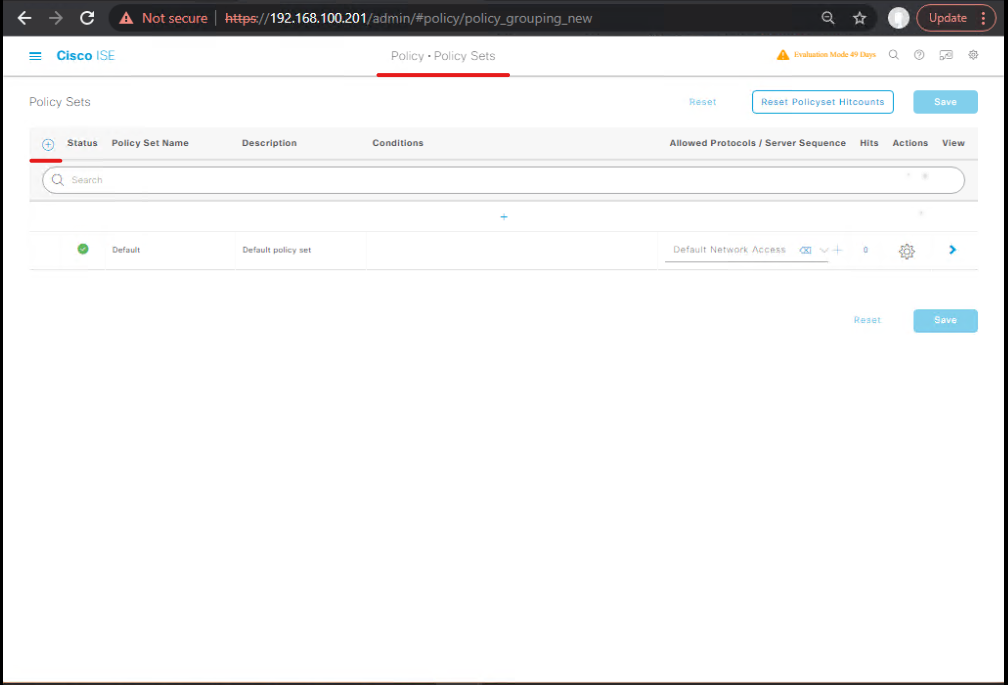
STEP 7 — Create Authorization Policy conditions in ISE using MDM attributes
- ISE GUI: Policy → Policy Sets → (your policy set) → Authorization
- Add Conditions based on MDM dictionary attributes exposed by the External MDM: examples:
- MDM:DeviceCompliantStatus == Compliant → Permit Full Access
- MDM:ManagedByIntune == True AND MDM:DeviceCompliantStatus == NonCompliant → Quarantine (dACL/VLAN/redirect)
- MDM:DeviceRegisteredStatus == False → Remediate (redirect to Intune enrollment portal)
(Attribute names and exact syntax show up in your ISE policy element Conditions list once the MDM server is enabled.) (Cisco)
[Authorization Rule – MDM Conditions]
Validation: Test with a compliant device (should be allowed) and a non-compliant device (should match quarantine rule). Use Operations → RADIUS Live Logs to see matched Authorization rule and attributes returned.
STEP 8 — Validation & CLI/API checks (end-to-end)
A. ISE GUI checks
- Administration → Network Resources → External MDM → ensure status Enabled and last successful poll timestamp. (Cisco)
- Operations → RADIUS → Live Logs → view the authentication event; expand details to see MDM attributes (compliance status, managed flag).
- Context Visibility → Endpoints → open endpoint details → MDM/MDM Attributes tab shows managed/compliant/registered. (Cisco)
B. ISE CLI debug & logs
- To enable debug for MDM-related flows use the Debug Wizard: Operations → Troubleshoot → Debug Wizard → enable
external-mdm/ MDM debug (TRACE if needed). Cisco documents how to enable debug logs in the UI (or CLI). Checkise-psc.logfor MDM entries. (Cisco, Security CCIE Blog –)
Useful CLI snippets
# show ISE status ise/admin# show application status ise # tail relevant ISE logs (PSC / MDM) ise/admin# show logging application ise-psc.log tail 50 # If using debug wizard, collect logs and inspect /var/log/ise/ise-psc.log for MDM messages
C. Azure/API test (optional)
- Using tenant/client credentials you can manually request a token and query the Graph endpoint to confirm
get_device_complianceworks (use Postman or curl). Microsoft docs explain the OAuth v2 token flow and Graph endpoints for compliance. (Microsoft Learn)
Example token request (curl):
TENANT=<tenant-id>
CLIENTID=<app-id>
CLIENTSECRET=<secret> # cert-based flow recommended for prod
curl -X POST -d "client_id=${CLIENTID}&scope=https://graph.microsoft.com/.default&client_secret=${CLIENTSECRET}&grant_type=client_credentials" \
https://login.microsoftonline.com/${TENANT}/oauth2/v2.0/token
Then call Graph/Intune compliance APIs per Microsoft docs. (Microsoft Learn)
STEP 9 — Test cases (practical checks you must run)
Run these tests and capture logs:
- Compliant enroll device (Intune managed + compliant) → Connect via Wi-Fi → Expected: Auth successful, Authorization rule for Compliant matched, Full access. Validation: RADIUS Live Logs shows compliance attribute; Endpoint Context Visibility shows
ManagedByIntune = true,ComplianceStatus = compliant. (Cisco) - Managed but Non-Compliant (e.g., disable antivirus) → Connect → Expected: Quarantine rule matches, dACL applied. Validation: RADIUS Live Logs show MDM attributes; switch shows CoA/ACL applied; ISE shows rule name matched.
- Unmanaged device (not enrolled) → Connect → Expected: Deny or redirect to onboarding portal. Validation: Live Logs and endpoint details show
RegisteredStatus=false. - VPN client with GUID in cert → Connect via AnyConnect → Expected: ISE identifies DeviceID from AnyConnect log and queries Intune by GUID (not MAC), returns compliance. Validation: AnyConnect logs show
ID:Intune:DeviceID:<id>, ISE Live Logs show it used GUID for lookup. (Cisco, Security CCIE Blog –)
Final checklist & quick validation
Quick ISE checks
# ISE version / status ise/admin# show version ise/admin# show application status ise # Tail MDM/PSC logs after Test Connection ise/admin# show logging application ise-psc.log tail 100
Test flows
- Test Connection in Administration → Network Resources → External MDM. (Cisco)
- Authenticate a compliant device → Operations → RADIUS → Live Logs should show MDM attributes. (Cisco)
- Change device compliance in Intune → watch ISE poll and check Live Logs and Context Visibility.
Expert Level Use Cases (turn these into lab projects / production automations)
- Zero-Trust Posture Enforcement
- Intune reports
compliant→ ISE assigns SGT and full access to internal services. Ifnoncompliant→ ISE applies Quarantine dACL via CoA and auto-creates a ServiceNow ticket with device details.
- Intune reports
- VPN GUID-Based Posture
- AnyConnect sends
ID:Intune:DeviceID:<GUID>in client handshake. ISE queries Intune for GUID compliance and allows/blocks VPN tunnel or applies split-tunnel policy based on result. Validate by reading AnyConnect logs and ISE Live Logs.
- AnyConnect sends
- Automated Re-Auth on Compliance Drift
- Intune detects noncompliance → webhook triggers an orchestration function (Azure Function) → call ISE pxGrid/ERS to CoA or change endpoint group → network enforcement updated in seconds.
- Intune detects noncompliance → webhook triggers an orchestration function (Azure Function) → call ISE pxGrid/ERS to CoA or change endpoint group → network enforcement updated in seconds.
- BYOD automated onboarding
- Unmanaged devices get redirected to Intune enrollment portal via Authorization rule; once enrolled and SCEP delivered (with GUID SAN), ISE automatically moves them into
Corpgroup and applies normal policy.
- Unmanaged devices get redirected to Intune enrollment portal via Authorization rule; once enrolled and SCEP delivered (with GUID SAN), ISE automatically moves them into
- MAC randomization resilience
- Use certificate GUID for wired/wireless/VPN so device identity persists across randomized MAC sessions; design ISE policy to prefer GUID for compliance lookups.
- Use certificate GUID for wired/wireless/VPN so device identity persists across randomized MAC sessions; design ISE policy to prefer GUID for compliance lookups.
- Compliance-based SGT Assignment
- Map
Compliant→ SGT 100 (Corp),NonCompliant→ SGT 200 (Quarantine). Push SGT via TrustSec integration or network device ACLs.
- Map
- Audit & Forensic enrichment
- On every compliance change, enrich SIEM logs (Splunk/QRadar) with Intune state via ISE pxGrid or ERS events for threat hunting.
- On every compliance change, enrich SIEM logs (Splunk/QRadar) with Intune state via ISE pxGrid or ERS events for threat hunting.
- Multi-tenant / National cloud support
- Use the correct Graph endpoint for national clouds (modify Auto Discovery URL accordingly) and handle certificate chaining per Cisco recommendations.
- Use the correct Graph endpoint for national clouds (modify Auto Discovery URL accordingly) and handle certificate chaining per Cisco recommendations.
- Intune certificate rotation automation
- Build scheduled job to re-upload new ISE cert into Azure app and toggle MDM entry (disable/enable) to clear cache — scripted with PowerShell / Azure CLI.
- Build scheduled job to re-upload new ISE cert into Azure app and toggle MDM entry (disable/enable) to clear cache — scripted with PowerShell / Azure CLI.
- Managed Device Lifecycle automation
- When Intune retires device (retire action) → automation removes endpoint from
Corpgroup in ISE and moves toDecomissionedgroup; revoke network access.
- When Intune retires device (retire action) → automation removes endpoint from
FAQs
FAQ 1 — Which ISE versions/patches are required for Intune NAC 2.0 / Microsoft Graph?
Answer: Cisco ISE must be upgraded to releases/patches that support Microsoft Graph and NAC 2.0. Cisco’s integration doc lists supported versions (example: ISE 3.1 Patch 8, 3.2 Patch 4, and later for full NAC 2.0 support). Always consult the Cisco Intune integration PDF before deploying. (Cisco)
Validation: ise/admin# show version and compare with Cisco doc.
FAQ 2 — What exact Intune attributes will ISE receive from Microsoft?
Answer: With NAC 2.0 / Compliance Retrieval, ISE can retrieve: Compliance Status, Managed by Intune, MAC Address, and Registered Status. If GUID is provided (via certificate SAN), ISE can use GUID for lookups which is preferred when MACs are randomized. (Cisco)
Validation: Trigger an auth and inspect Operations→RADIUS→Live Logs; look for MDM attribute entries.
FAQ 3 — How does ISE get the Intune GUID from devices?
Answer: You must configure Intune certificate profiles (SCEP/PKCS) to include the device GUID in the certificate SAN as a URI ID:Microsoft Endpoint Manager:GUID:{{DeviceId}}. ISE will then prioritize GUID over MAC when querying Intune. (Cisco)
Validation: On device check certificate SAN; on ISE check endpoint details for DeviceID in endpoint attributes.
FAQ 4 — Do I need to upload Microsoft root certs to ISE?
Answer: Yes — Cisco recommends importing Microsoft PKI root chain into ISE’s trusted certificates so SSL/TLS trust with the Intune endpoints is established. Cisco’s doc shows which certs to download (Digicert etc.) and how to import them into ISE. (Cisco)
Validation: After import, Test Connection from ISE External MDM UI should succeed.
FAQ 5 — What OAuth fields must I enter in ISE’s External MDM page?
Answer: Auto Discovery URL (https://graph.microsoft.com), Client ID (app ID), Token Issuing URL (OAuth v2 token endpoint), and Token Audience (value depends on ISE release; often https://api.manage.microsoft.com//.default). Cisco’s doc lists exact token audience guidance per ISE release. (Cisco)
Validation: Use Test Connection and check for a successful token exchange (ISE logs will indicate token success/failure).
FAQ 6 — What if Test Connection fails — where do I look?
Answer:
- In ISE: enable
external-mdmdebug via Operations → Troubleshoot → Debug Wizard and inspectise-psc.logfor MDM messages. Check that the uploaded certificate thumbprint matches the Azure app entry and that API permissions & admin consent were granted. (Cisco, Security CCIE Blog –) - In Azure: ensure the certificate uploaded to the app matches ISE exported cert, and admin consent exists for the required API permissions. (Cisco)
FAQ 7 — How do I handle MAC randomization on modern OSes?
Answer: Use the GUID approach — ensure Intune certificate profile adds GUID to the cert SAN; configure ISE to use GUID for compliance lookups instead of MAC. This is the modern, resilient pattern. (Cisco)
Validation: Force client to randomize MAC and verify ISE still matches device by GUID during auth.
FAQ 8 — Can I require Intune enrollment for network access?
Answer: Yes. Build authorization rules to require ManagedByIntune == True and DeviceCompliantStatus == Compliant. For devices that fail, create remediation (redirect to MDM enrollment page or Quarantine). (Cisco)
Validation: Attempt with an unmanaged device; it should hit the authorization rule for remediation.
FAQ 9 — Does ISE initiate immediate re-auth when device compliance changes?
Answer: ISE polls Intune on a schedule (Polling Interval) and can be configured to reauth devices (Compliance Device ReAuth Query). For immediate enforcement, you can combine with pxGrid or external triggers to request CoA / reauth for the session. (Cisco)
Validation: Change compliance in Intune and observe ISE poll run / RADIUS reauth events in Live Logs.
FAQ 10 — Where are the MDM debug / trace logs on ISE?
Answer: Enable external-mdm or MDM trace via Debug Wizard and check ise-psc.log for detailed MDM integration logs. The Debug Wizard is in Operations → Troubleshoot → Debug Wizard for ISE 3.x. Use those logs to troubleshoot token exchange, Graph queries and response parsing. (Cisco, Security CCIE Blog –)
Validation: Run a Test Connection in the External MDM UI and then inspect ise-psc.log (tail) for connection/response messages.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes — key takeaways
- Upgrade & plan: Ensure your ISE release/patch supports Microsoft Graph/NAC 2.0 (Cisco lists the required builds). (Cisco)
- GUID is the modern identifier: Add GUID to device cert SAN via Intune certificate profiles; ISE will prefer GUID over MAC. (Cisco)
- OAuth + certs required: App registration + certificate upload + admin consent + token audience alignment are critical. (Cisco)
- Test, then enforce: Use Test Connection, Live Logs, and debug
ise-psc.logbefore you move from logging-only to enforcement. (Cisco, Security CCIE Blog –)
Upgrade Your Skills – Start Today
“For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.”
Fast-Track to Cisco ISE Mastery Pro — I run a focused an intensive 4-month instructor-led program covering TrustSec, pxGrid, ISE APIs, Intune integration, TACACS+, SIEM integration, and troubleshooting bibles.
Course outline & enrollment: https://course.networkjourney.com/ccie-security/.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



