[Day 129] – Cisco ISE Mastery Training: Mixed Vendor Environments (HP/Aruba, Juniper)
Table of Contents
Introduction
Mixed-vendor networks are the reality: Cisco campus switches, Aruba aggregation, Juniper edge, and multi-vendor controllers often coexist. Cisco ISE is commonly used as the central RADIUS/Policy engine — but different vendors implement RADIUS dynamic features (CoA/Disconnect/VSA) and 802.1X behavior with vendor-specific quirks.
This masterclass teaches you how to design, configure, validate and troubleshoot Cisco ISE working reliably across Aruba (AOS-CX / ArubaOS) and Juniper (EX / SRX / MX) so that authentication, authorization and dynamic actions (CoA, VLAN/dACL changes, port-bounce, disconnects, and vendor VSAs) work predictably — and so you can confidently teach students to do the same.
Problem Statement (what we solve)
Real world problems in mixed vendor ISE deployments:
- CoA/Disconnect inconsistencies across vendors (different ports, attribute support).
- Vendor VSAs (Aruba vs Juniper vs Cisco) require different RADIUS attributes or formatting.
- HA/cluster VRRP or controller clustering can obscure NAD IP used for CoA (PSN must target right IP).
- Network device profiles in ISE may not match vendor defaults, resulting in failed dynamic authorizations.
- Troubleshooting is noisy: RADIUS logs show CoA sent but NAD returns NAK or ignores reauth (missing attribute).
Goal: give you the exact steps and validation checks to make these work, and the diagnostic playbook to fix failures fast.
Solution Overview (how ISE addresses the problem)
Cisco ISE centralizes authentication/authorization while treating each NAD (network access device) as a network device entry with a shared secret, vendor profile, and CoA settings. To make mixed-vendor environments work you must:
- Add each NAD to ISE with the correct vendor Network Device Profile (or import one).
- Configure NAD to accept RFC-3576 dynamic RADIUS (CoA/Disconnect) and ensure both sides use same CoA UDP port and shared secret. Juniper defaults to port 3799 and uses Juniper VSAs for dynamic filtering; Aruba supports RFC-3576 and exposes RFC-3576 server configuration in AOS-CX / ArubaOS. (Juniper Networks, HPE Aruba Networking)
- Map ISE Authorization Profiles to vendor expectations (VLAN names vs numeric IDs, dACLs, or vendor VSA formats such as Juniper-Switching-Filter). (Juniper Networks)
- Test and validate using ISE Live Logs, NAD CLI debug (radius/dynamic-auth), and packet captures for CoA UDP traffic. Also consult vendor integration docs (Cisco has a guide for 3rd party Aruba integration). (Cisco)
Sample Lab Topology
Platform: VMware or EVE-NG (use ISE OVA, Junos vMX/EX image, Aruba AOS-CX image or ArubaOS/Controller image if available).
Components & IPs (example)
- ISE PAN:
10.10.10.10 - ISE PSN:
10.10.10.11(use real PSN IP for CoA) - Aruba AOS-CX switch:
10.10.30.20 - Aruba Mobility Controller (optional):
10.10.30.21 - Juniper EX switch:
10.10.30.30 - Test client (wired):
172.16.110.100 - Lab automation host (for curl/pcap):
10.10.99.50
Simple topology:
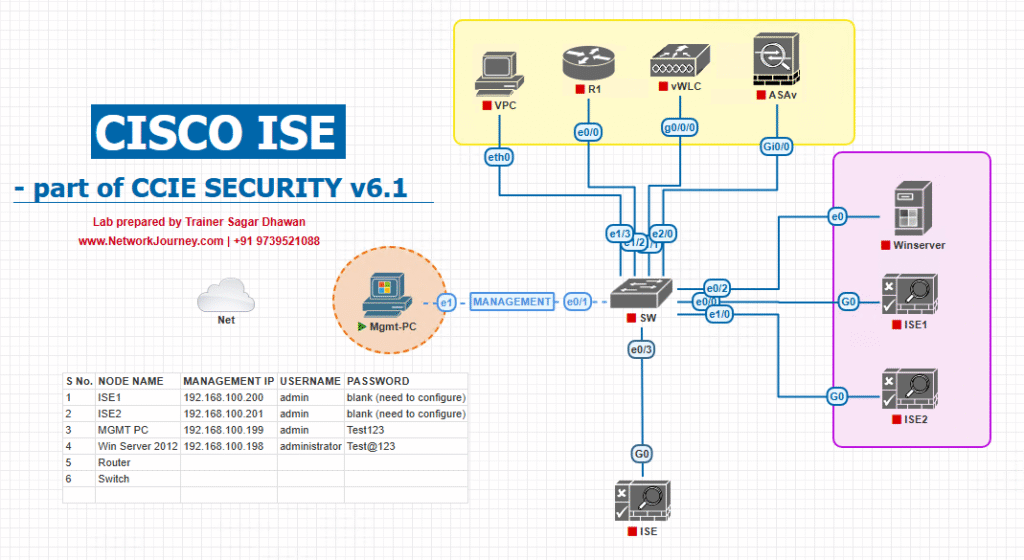
Key design notes:
- Ensure ISE PSN IP is reachable from NAD for CoA (use PSN real IP, not a VIP). (community.f5.com)
- If NADs are HA clusters (Aruba cluster / Juniper Virtual Chassis), ensure RFC-3576 server config uses cluster VRRP/IP options recommended by vendor docs. (Airheads Community)
Step-by-Step GUI & CLI Configuration Guide (copy-pasteable)
We’ll configure the main items: (A) ISE Network Device entries and profiles; (B) Juniper EX; (C) Aruba AOS-CX; (D) ISE policy & authz mapping; (E) Testing & validation.
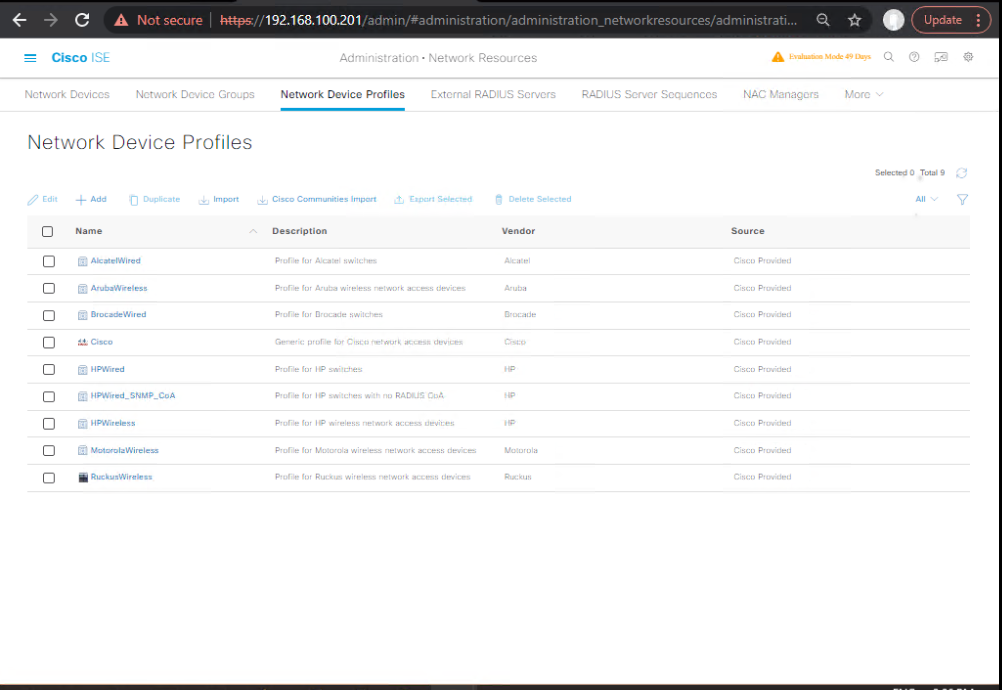
A — ISE: Add network devices & vendor profiles (GUI)
- ISE GUI → Administration > Network Resources > Network Device Profiles → ensure vendor profiles exist. If Juniper or Aruba profiles are missing, import or create one. (ISE provides templates; you can edit). [Screenshot: ISE Network Device Profiles]
- ISE GUI → Administration > Network Resources > Network Devices > Add → for each device:
- Name:
Aruba-AOSCX-6300 - IP Address:
10.10.30.20 - Device Type / Product: set vendor (Aruba / Juniper) or choose matching profile
- RADIUS Shared Secret:
ISE_SECRET - Enable Dynamic Authorization / CoA checkbox (if present in your ISE version). [Screenshot: Add Network Device]
- Name:
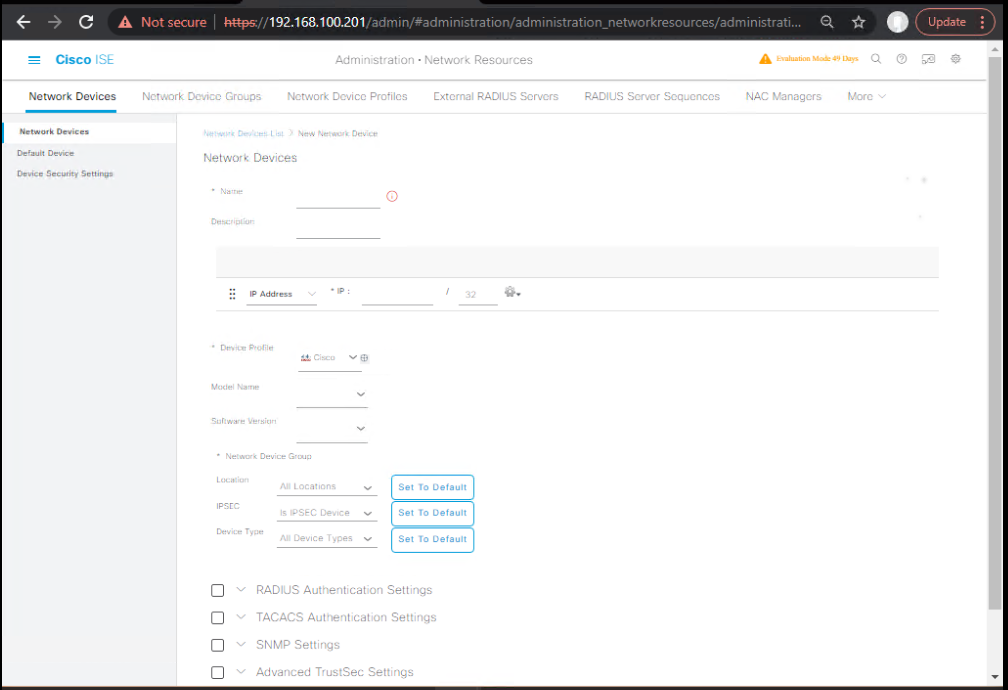
- Save. Validate on ISE: Operations > Network Devices → should show your device and reachability if you run a test (ping/ SNMP test depends on ISE version).
Tip: For clustered NADs, add the device using the actual IP that will receive CoA (Juniper default port 3799 uses specific server IPs). Use real PSN IP in device entry for CoA routing. (community.f5.com)
B — Juniper EX example: enable CoA / dynamic requests (Junos)
Goal: Configure EX to accept CoA on UDP 3799 and point to ISE RADIUS servers.
Example config (candidate):
configure set access profile AAA-RADIUS radius authentication-server 10.10.10.11 set access profile AAA-RADIUS radius accounting-server 10.10.10.11 # Configure dynamic request support (CoA default port 3799) set access profile AAA-RADIUS radius dynamic-requests # Optionally set the port (default 3799) set access profile AAA-RADIUS radius dynamic-request-port 3799 commit
Validate on Junos:
show configuration access show system services radius show aaa server # (or the Junos equiv) show authentication sessions
Notes & vendor specifics:
- Junos monitors UDP 3799 by default; you must use same port across all configured servers or use default. Junos supports vendor VSAs such as Juniper-Switching-Filter to deliver firewall filters dynamically from RADIUS. (Juniper Networks)
C — Aruba AOS-CX example: RFC-3576 server + radius group
Goal: Configure Aruba to accept RFC-3576 dynamic requests and enable RADIUS server group used for dot1x/MAB.
Sample AOS-CX commands (example):
configure terminal # Add RADIUS auth server radius server ISE address 10.10.10.11 key ISE_SECRET port 1812 # Add RFC-3576 (dynamic-auth) server entry aaa rfc-3576-server ISE-RFC3576 host 10.10.10.11 key ISE_SECRET port 3799 # Bind RFC3576 server to AAA profile aaa authentication port-access <profile-name> radius-server-group ISE aaa authorization port-access <profile-name> radius-server-group ISE exit write memory
Validate on AOS-CX:
show radius statistics show aaa rfc-3576-server show authentication sessions interface <if>
Notes:
- Aruba AOS-CX has specific
aaa rfc-3576-servercommands for CoA support — use the RFC 3576 server construct and attach it to AAA profiles. Aruba docs explain details and mention VRRP/cluster requirements for dynamic auth. (HPE Aruba Networking)
D — Example ArubaOS (Mobility Controller) RFC-3576 (if using Aruba controllers)
Aruba controller GUI: Configuration → Authentication → RFC3576 → add ISE IP, shared secret and port. Ensure the RFC3576 server is linked to your authentication profile so CoA flows to the controller cluster. Community checklists note cluster VRRP/VLAN must be configured when using controllers. (Airheads Community)
E — ISE: Create Authorization Profiles mapped to vendor expectations
- Authorization Profiles (ISE GUI → Policy > Policy Elements > Results > Authorization Profiles)
Aruba_Full_Access→ Access Type =ACCESS_ACCEPT, set VLAN Name/ID or DACL (vendor expects VLAN name or ID depending on device). [Screenshot: Authorization Profile Aruba]Juniper_Quarantine→ Access TypeACCESS_ACCEPT, set Filter-ID (if using Juniper) or apply Juniper-Switching-Filter via VSA mapping. [Screenshot: Authorization Profile Juniper]
- Policy Set → create rules that select the correct authz profile when NAS-IP or NAD type matches Aruba/Juniper device entry.
Important mapping note:
- Juniper EX often expects VLAN NAMES mapped to local VLANs or uses Juniper VSAs for switching filters — ISE must send expected attribute formats. Consult Juniper docs for Juniper-Switching-Filter examples when pushing layer-2 firewall filters. (Juniper Networks)
F — Testing & Validation (GUI + CLI + packet capture)
1) Authentication test (client connects)
- On client: connect 802.1X or MAB.
- On ISE: Operations > RADIUS > Live Logs → find Access-Request and Access-Accept with Authorization profile. [Screenshot: ISE Live Logs]
2) CoA test (trigger from ISE)
- On the ISE Live Log entry for the session: Use Take Action → Reauthenticate / Disconnect / Port Bounce.
- Watch NAD CLI while action occurs.
Juniper CLI checks:
show authentication sessions interface <if> details show radius statistics show system services radius # or dynamic request show commands
Aruba CLI checks:
show authentication sessions interface <if> show radius statistics show aaa rfc-3576-server
3) Packet capture (critical validation)
- Capture on NAD or network tap between ISE and NAD:
sudo tcpdump -i eth0 udp and (port 3799 or port 1700) -w coa.pcap - In Wireshark: see RADIUS CoA-Request (Code for CoA), CoA-Ack or CoA-NAK. If NAK present, investigate error code. Refer to RFC 3576. (IETF Datatracker)
Troubleshooting & Diagnostics (vendor-specific)
Use this checklist in order — fast path to root cause.
1 — CoA packet not reaching NAD
- Check firewall/NAT: CoA is unsolicited server→NAD; NAT often breaks it. Ensure direct route and UDP port allowed (3799 or configured port).
- Check NAD listening port: Juniper default is 3799; Aruba may use configured port via
aaa rfc-3576-server. Ensure both sides match. (Juniper Networks, HPE Aruba Networking)
2 — Shared secret mismatch
- Verify secret in ISE Network Device entry matches
radius server/aaa rfc-3576-serverentries on NAD. A mismatch yields NAK or ignores.
3 — ISE shows “CoA Sent” but NAD NAKs or ignores
- Run a packet capture at NAD — look for NAK reason (Invalid Request / Missing Attribute).
- Common vendor issue: Aruba sometimes requires specific attributes for Reauth CoA (only port bounce/disconnect may work unless attributes configured). Community threads report Aruba reauth requires attribute formatting. If reauth fails, try Disconnect or Port Bounce and inspect logs. (Airheads Community)
4 — Vendor VSA formatting problems (Juniper)
- For Juniper filter delivery, ensure RADIUS server sends Juniper-Switching-Filter VSA encoded correctly and RADIUS dictionary includes Juniper VSAs. Junos doc shows format examples (e.g.,
match destination-ip ... action allow). (Juniper Networks)
5 — NAD cluster/HA issues (Aruba controllers)
- If using cluster, ensure RFC3576 configured with cluster VRRP IP or correct cluster address and follow vendor checklist (VRRP, L2 connected etc.). Aruba community checklist covers common pitfalls. (Airheads Community)
6 — ISE PSN vs VIP confusion
- Use PSN real IP for CoA — CoA must target PSN directly. If you attempt CoA to a load-balanced VIP it can fail — use PSN IP and ensure NAD resolves correctly. (community.f5.com)
Lab Walkthroughs with Validation (2 scenarios)
Lab A — Juniper EX wired guest → upgrade to employee (CoA Reauth)
Pre-req: Juniper configured with access profile pointing to ISE (10.10.10.11) and dynamic requests enabled.
Steps
- Connect client (MAB) → ISE assigns
Guest_VLAN. Validate:show authentication sessions interface Gi0/0/10 details(shows Guest role). - In ISE, approve guest or change authorization rule to
Employee_VLAN. From Live Logs select session → Take Action → Reauthenticate. - On Juniper: you should see Received CoA-Request and subsequent reauth:
show authentication sessions mac <mac>now showsEmployee_VLAN. - Validate ISE Live Logs show reauth success. Also capture CoA UDP packets to verify CoA-Request and CoA-Ack. (Juniper Networks)
Lab B — Aruba AOS-CX wireless via Mobility Controller — disconnect test
Pre-req: Aruba controller configured with RFC3576 server pointing to ISE, APs forwarding to controller.
Steps
- Connect wireless client to Guest SSID; confirm redirect.
- In ISE, trigger Disconnect on the session.
- On Aruba controller, verify client disappeared from controller client table and session terminated. Use
show client mac <mac>(controller CLI or GUI). - Packet capture: verify CoA-Request with Disconnect and CoA-Ack. If NAK, inspect controller logs and verify RFC3576 server config & secrets. (Airheads Community)
Expert Level Use Cases (step-by-step mapping + validation)
Use Case 1 — Campus with mixed Juniper/Aruba access, single ISE policy
Goal: One ISE, seamless policy across vendors.
Steps:
- Add all NADs to ISE with correct vendor profile and secret.
- Use ISE Policy Sets keyed by
NAS-IPorNetwork Devicegroups so authorization maps to vendor-specific profiles (e.g.,Juniper_DeviceGroup→ send Juniper VSAs;Aruba_DeviceGroup→ send Aruba expected attributes). - Validate: test auth and CoA per vendor. Use packet capture for each vendor to confirm attribute format. (Juniper Networks, HPE Aruba Networking)
Use Case 2 — Cross-vendor CoA orchestration on incident
Goal: SOC triggers containment: ISE sends disconnect to Aruba AP and Juniper switch for same MAC.
Steps:
- SOC automation calls ISE Monitoring/CoA API to disconnect session (or call ISE to send CoA to both NADs).
- ISE sends CoA → NADs disconnect. Validate both NADs show session removal in CLI and ISE Live Logs show CoA Sent + NAD Ack.
Validation: Packet captures at both NADs show CoA-Request; ISE logs show success.
Use Case 3 — Vendor migration (Aruba→Juniper) with staged coexistence
Goal: Gradual migration while keeping ISE policies intact.
Steps:
- Ensure both vendors are added in ISE with correct profiles.
- Create policy rules that match by
Network Device Groupso that when traffic moves to new vendor, auth behavior remains consistent. - Test per-port/vlan after cutover and verify CoA/Disconnect behave identically.
FAQs – Cisco ISE in Mixed Vendor Environments (HP/Aruba, Juniper)
Q1. How does Cisco ISE communicate with HP/Aruba and Juniper switches when they are not Cisco?
Answer:
- Communication still happens over RADIUS (authentication, authorization, accounting).
- Key difference → vendor-specific attributes (VSAs) must match NAD behavior.
- Cisco AV-Pairs may not be supported → instead use Aruba/Juniper-specific VSAs (e.g.,
Aruba-User-Role,Juniper-Local-User-Role).
Validation: - On ISE → Policy Sets > Authorization Profile → add VSA.
- On NAD CLI:
show radius-server statistics show access-sessionEnsure access role mapping is applied.
Q2. What RADIUS attributes do Aruba switches/WLCs expect from ISE for role assignment?
Answer:
- Aruba expects attributes like:
Aruba-User-Role(string: maps to pre-defined role on switch/WLC).Aruba-Priv-Admin-Userfor admin access.
Validation:
- On ISE → create Authorization Profile with
Aruba-User-Role = employee. - On Aruba NAD:
show user-tableConfirm user role.
Q3. How do Juniper EX switches handle ISE authorization compared to Cisco switches?
Answer:
- Juniper supports RADIUS CoA and dACLs, but naming differs.
- Instead of Cisco dACLs, Juniper expects Firewall Filters mapped via RADIUS attribute
Juniper-Local-User-Role.
Validation: - On ISE → create custom attribute
Juniper-Local-User-Role = Staff. - On Juniper CLI:
show dot1x interface ge-0/0/5 show log radiusdConfirm role assignment.
Q4. How do we test CoA (Change of Authorization) in Aruba/Juniper devices integrated with ISE?
Answer:
- Ensure NAD supports RFC 5176 (CoA).
- ISE sends CoA → NAD must disconnect/re-auth endpoint.
Validation: - On ISE Live Logs → click endpoint →
Reauthenticate. - On NAD:
show radius-server statistics→ Look for CoA counters increment.
Q5. Can dACLs from ISE be pushed to Aruba and Juniper devices?
Answer:
- Aruba → Yes, but implemented as
Aruba-User-RoleACLs pre-configured on controller/switch. ISE only sends role name. - Juniper → Supports filter-based enforcement, requires predefined firewall filters.
Validation: - Aruba CLI:
show rights <role-name> - Juniper CLI:
show configuration firewall
Q6. How do we configure ISE NAD profiles for Aruba and Juniper?
Answer:
- ISE GUI Path: Administration > Network Resources > Network Devices > Add.
- Define NAD IP, RADIUS shared secret, SNMP settings.
- Apply correct Device Profile (Aruba, Juniper).
Validation: - Confirm in ISE RADIUS Live Logs that request is tagged with correct profile.
Q7. What are the most common authentication methods used in mixed-vendor NAC with ISE?
Answer:
- 802.1X with EAP-TLS or PEAP (primary choice).
- MAB (MAC Authentication Bypass) for headless devices.
- Both Aruba and Juniper support these as long as RADIUS is configured correctly.
Validation: - On ISE → Live Logs → check
Authentication Method. - On NAD:
show dot1x statistics
Q8. How do we debug onboarding failures on Aruba switches integrated with ISE?
Answer:
- Aruba CLI debug commands:
debug aaa radius all debug dot1x all show authentication sessions - ISE → check Live Logs → expand failure reason (e.g., “Invalid VSA” or “Role not found”).
Q9. How can we enforce different access policies for Cisco vs Aruba vs Juniper in the same ISE deployment?
Answer:
- Use Device Type/Device Profile conditions in Policy Sets.
- Example:
- If NAD = Aruba → send Aruba role.
- If NAD = Juniper → send Juniper firewall filter.
- If NAD = Cisco → send Cisco dACL.
Validation:
- On ISE → Policy Sets → view matched condition column.
- On NAD CLI → check applied ACL/role.
Q10. Does posture assessment work with Aruba and Juniper devices?
Answer:
- Yes, if device supports redirect ACL/URL.
- Aruba controllers/switches → support captive portal redirect.
- Juniper EX → limited, but can integrate with firewall for posture redirection.
Validation: - On ISE → Reports → Posture Compliance.
- On client → ensure redirect page loads → remediation applied.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes (key takeaways)
- Mixed vendor ISE deployments are common but require vendor-specific attention: CoA port, shared secrets, vendor VSAs and NAD cluster settings are the usual friction points. (Juniper Networks, HPE Aruba Networking)
- Always validate with three lenses: ISE Live Logs (server side), NAD CLI debug/logs (client side), and packet captures (network wire). That triple view resolves ~90% of issues quickly.
- For production, use lab-tested mappings (Authorization Profile → vendor format) and automate tests to prevent regressions during firmware upgrades or policy changes.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to Network Journey on YouTube and join my instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro — 4-month instructor-led program (hands-on EVE-NG/VMware labs, weekly live troubleshooting, CCIE-style scenarios).
Reserve a seat / get the BYOD + CoA lab pack: https://course.networkjourney.com/ccie-security/
Reserve my seat + get free Mixed-Vendor CoA lab pack. Collect: name, email, org, lab platform (VMware/EVE).
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![QoS Fundamentals for Network Engineers: Boost Performance, Reduce Latency [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/QoS-Fundamentals-for-Network-Engineers_Boost-Performance_Reduce-Latency_networkjourney.png)

![AAA Authentication with TACACS+ and RADIUS – Step-by-Step Cisco Guide [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-AAA-TACACS-RADIUS.jpg)