[Day 133] Cisco ISE Mastery Training: MFA Integration (Duo, RSA SecurID)
Table of Contents
Introduction
Multi-factor authentication (MFA) is now table stakes: passwords alone are not sufficient. Cisco ISE sits at the center of network access control — it’s the ideal enforcement point to require a second factor before granting access to sensitive networks or services. Integrating an MFA provider (Duo, RSA SecurID, or others) with ISE lets you apply conditional, step-up, and guest MFA policies consistently across wired/wireless/VPN/TACACS+.
In this Article l will show two real, production-grade patterns:
- Duo + ISE — either via the Duo Authentication Proxy (universally supported) or native ISE → Duo API integration available in newer ISE releases (3.3+ patch1 and later). (Duo Security, Cisco)
- RSA SecurID + ISE — either using native SecurID agent integration (sdconf recursively configured) or via RADIUS to RSA Authentication Manager. (RSA Community)
You’ll walk away able to design MFA flows, build lab infrastructure (ISE + Duo proxy + RSA AM), configure ISE authentication policy to call external MFA, validate end-to-end, and troubleshoot every common failure mode.
Problem Statement
Typical operational problems MFA integration solves:
- Untrusted credentials: single factor (password) fails when credentials are compromised.
- Inconsistent enforcement: different devices and access points require a single central policy to require MFA depending on user role, device posture, or location.
- Guest/contractor access: Sponsor workflows need one-time codes or push verification.
- Admin access protection: CLI/TACACS+ sessions to network devices must require MFA for admin accounts.
Challenges you’ll face while integrating MFA with ISE:
- Matching RADIUS attributes and reply behavior between ISE and MFA proxy.
- Maintaining session continuity (CoA) after step-up or failing gracefully.
- Handling timeout/delivery issues (push/OTP failures).
- Correctly sequencing primary auth (AD) and secondary auth (Duo/RSA).
I solve this by designing deterministic flows and concrete validation steps.
Solution Overview
Two proven integration patterns
- ISE + Duo Authentication Proxy (recommended for broad compatibility):
- ISE proxies authentication requests (RADIUS) to the Duo Authentication Proxy which performs primary authentication against AD (or ISE) and then calls Duo cloud for second factor (push, phone, OTP). Duo returns success/fail to proxy; proxy returns RADIUS success/fail back to ISE. This pattern is vendor-agnostic and commonly used. (Duo Security)
- ISE native Duo API integration (ISE 3.3+ patch 1 and later):
- Newer ISE releases can call Duo natively (API) to request secondary auth without deploying the local proxy in some flows — simpler for VPN/management access. Validate whether your ISE release supports native Duo integration before choosing this path. (Cisco)
- ISE + RSA Authentication Manager:
- Two options: (a) Native SecurID integration (using sdconf.rec and agent) for direct token validation, or (b) RADIUS integration where ISE proxies to RSA as an external RADIUS token server. Choose based on your RSA environment and available sdconf files. (RSA Community)
ISE Policy placement: set up Authentication Policy such that certain rule(s) send authentication to an External Identity Source (RADIUS Token / External RADIUS) when MFA is required; otherwise use internal AD authentication.
Security controls: TLS to MFA APIs, restrict proxy hosts, rate limit attempts, lockout on repeated OTP failures.
Key references: Duo docs & Duo Auth Proxy config, Cisco ISE native Duo doc, RSA Implementation guide. (Duo Security, Cisco, RSA Community)
Sample Lab Topology
Platform: VMware or EVE-NG. Use snapshots and predefined OVA images.
VMs / Devices
- Cisco ISE (PAN + PSN) — ISE psn IP:
10.10.10.11 - Windows AD / LDAP — for primary authentication (
10.10.20.10) - Duo Authentication Proxy VM (Windows/Linux) —
10.10.99.10(or use ISE native if available) - RSA Authentication Manager (if testing RSA) —
10.10.80.10 - Network Access Device (WLC or switch) —
10.10.30.10(simulated in EVE) - Client (Windows laptop) — on guest or corp VLAN for testing
Topology diagram:
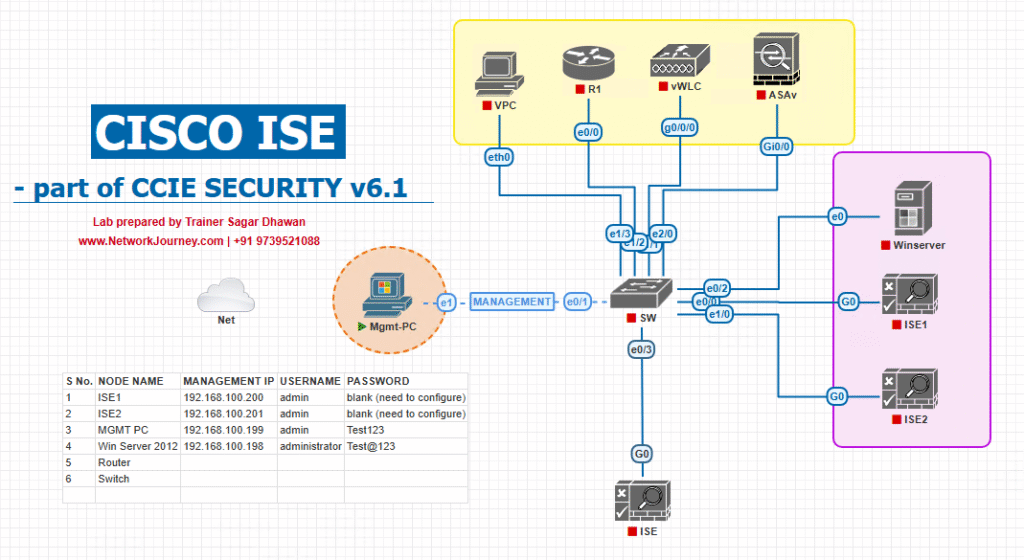
Notes
- Duo proxy must be reachable from ISE PSN (RADIUS traffic).
- For native Duo (ISE 3.3+ patch1) the PSA/PSN must be allowed to call Duo API (HTTPS). (Cisco, Duo Security)
Step-by-Step GUI Configuration Guide
Part A — Duo Integration (Option 1): Duo Authentication Proxy (universal)
Overview: ISE will proxy RADIUS auth to Duo Auth Proxy which will perform primary auth against AD and then contact Duo cloud for 2nd factor.
A.1 — Install Duo Authentication Proxy (lab host)
- Follow Duo docs for platform (Windows or Linux). Key config file is
authproxy.cfg. Official reference: Duo authproxy docs. (Duo Security Knowledge Base)
Sample authproxy.cfg (radius server mode + AD primary):
[general] ; log and pid settings log_level = INFO
[radius_server_auto]
ikey=DIXXXXXXXXXXXXXXXXXX skey=your_secret_key api_host=api-XXXXXXXX.duosecurity.com radius_ip_1=10.10.10.11 ; ISE PSN IP radius_secret_1=ISE_DUO_SECRET port=1812 [radius_server_iframe] ; optional for different flows ; …
Alternative (proxy primary to AD then duo):
[ad_client] host=10.10.20.10 service_account_username=duo_bind_user service_account_password=SecretPass
[radius_server_auto]
ikey=DI…. skey=… api_host=api-xxxx.duosecurity.com radius_secret_1=ISE_DUO_SECRET client=ad_client
Validation: Start the authproxy (systemctl start duoauthproxy or Windows service). Check logs (/var/log/authproxy.log) for “starting” and “listening on port 1812”. (Duo Security)
A.2 — Add Duo as External RADIUS Server in ISE (so ISE can proxy)
- ISE GUI → Administration > System > External RADIUS Servers (or Administration > Identity Management > External Identity Sources > RADIUS Token depending on release). Add new RADIUS server:
- Name:
DuoProxy-RADIUS - IP:
10.10.99.10(Duo proxy) - Shared Secret:
ISE_DUO_SECRET - Auth port:
1812 - [Screenshot: ISE Add External RADIUS Server].
- Name:
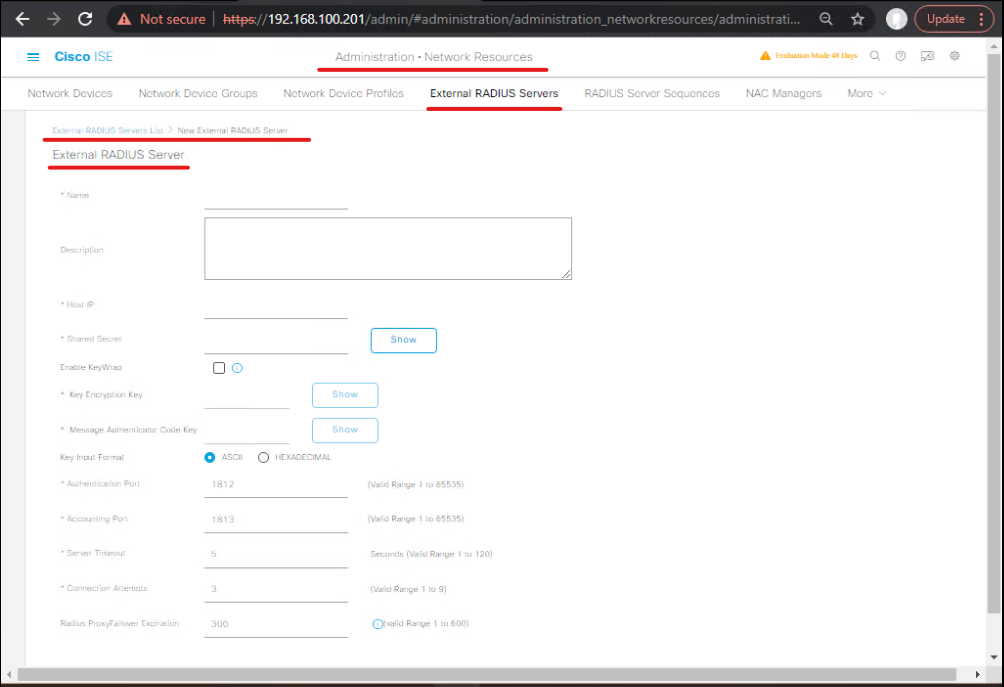
Validation: Use ISE Test External Identity Source or run a sample RADIUS test from ISE to Duo proxy (some versions have test buttons).
A.3 — Configure ISE Authentication Policy to use Duo proxy
- ISE GUI → Policy > Authentication.
- Create rule: when
Network Access: Identity Source=DuoProxy-RADIUSOR use a rule keyed on SSID/VPN/TACACS+ user group to forward to external RADIUS server. Example flow:- If
EAP Method == PEAPandPolicy Condition==Require MFA→ Allowed -> Use External RADIUS (DuoProxy).
- If
- Move rule above default AD rule.
Validation: ISE Live Logs should show Access-Request forwarded to external RADIUS server when rule matches. You can also view the RADIUS packet capture between ISE and Duo proxy.
A.4 — Test end-to-end (user + Duo push)
- Begin authentication on the client (AnyConnect / 802.1X).
- ISE forwards to Duo proxy → Duo proxy authenticates to AD (primary) → Duo cloud sends push to enrolled device.
- User approves push → Duo returns success → Duo proxy replies Access-Accept to ISE → ISE applies Authorization Profile.
Validation checks
- On Duo Proxy: tail logs
/var/log/authproxy.log— check for Access-Request and Duo returned success. - On ISE: Operations > RADIUS > Live Logs → Access-Request from NAD → forwarded to Duo proxy -> Access-Accept; examine attributes.
- Packet capture:
tcpdump -i any host 10.10.99.10 and port 1812to see RADIUS traffic. - Duo Admin Panel: Message / auth history shows push attempt. (Duo Security)
A.5 — Troubleshooting common Duo proxy issues
- Proxy won’t start — check config syntax and
ikey/skey/api_host. - ISE 401/NAK — shared secret mismatch between ISE and Duo proxy.
- Timeouts — ensure firewall allows outbound TCP/HTTPS from proxy to
api-*.duosecurity.com. - User not enrolled — Duo returns “user not found” — enroll user in Duo Admin.
- Logs: Duo proxy logs are the primary source of truth. (Duo Security Knowledge Base)
Part B — Duo Integration (Option 2): Native ISE → Duo API (ISE 3.3+ patch1+)
Only use if your ISE release supports it. Native integration reduces the need for a local authproxy in some admin/VPN flows. See Cisco guide for ISE native Duo MFA.
B.1 — Obtain Duo application keys (Admin portal)
- Create an “Application” in Duo (API type) and collect
integration key (ikey),secret key (skey), andapi hostname.
B.2 — Configure Duo in ISE (GUI)
- ISE GUI → Administration > Identity Management > External Identity Sources > Duo Integration (or similar).
- Enter
ikey,skey, andapi hostname. Save.- [Screenshot: ISE Duo Native Add].
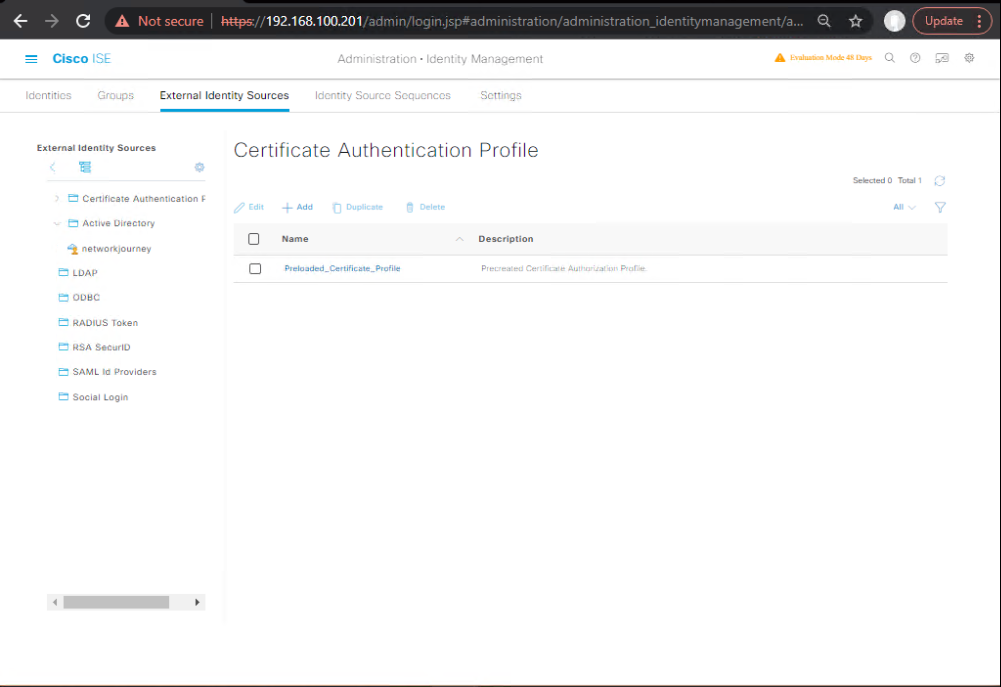
B.3 — Use Duo step in authentication policy
- Create authentication rules that call the Duo integration as a second factor (ISE will call Duo API to push/OTP). Place rules above primary AD-only rules.
Validation: Use ISE Live Logs and Duo Admin logs to confirm push/OTP flows.
Part C — RSA SecurID Integration
RSA supports multiple integration paths; choose Native SecurID (sdconf) for tight integration or RADIUS if you prefer decoupled flows. Official RSA implementation guides and Cisco “RSA Ready” docs provide details. (RSA Community)
C.1 — Native SecurID (recommended if sdconf is available)
High-level steps
- Obtain
sdconf.recfrom RSA Authentication Manager (secure transfer). - On ISE: Administration > Identity Management > External Identity Sources > RSA SecurID → upload
sdconf.rec, configure realm and agent settings. (ISE crypto agent will use sdconf to validate tokens).- [Screenshot: ISE RSA SecurID Add]. (RSA Community)
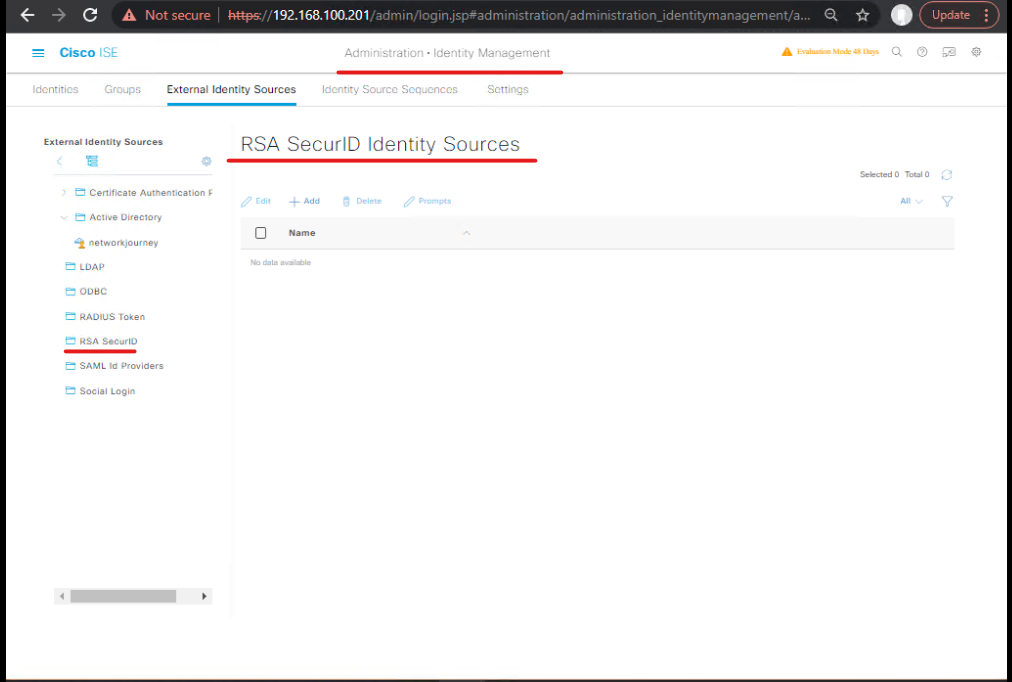
Validation
- Use ISE Live Logs to see RSA challenge/response events (Prompt and token validation).
- Test with known token (hardware/software) to validate passcode acceptance.
C.2 — RADIUS to RSA Authentication Manager (alternate)
Steps
- Configure Authentication Manager to accept RADIUS requests from ISE (register ISE IP as client).
- In ISE, add Authentication Manager as an External RADIUS Token Server (Administration > Identity Management > External Identity Sources > RADIUS Token). (Cisco)
- Configure ISE auth policy to forward to RSA RADIUS when 2FA is required.
Validation
- Test RADIUS exchange (radtest or inner flow) and view RSA logs for token validation.
Troubleshooting & Diagnostics
Common checks (always first)
- Shared secrets: verify in ISE and MFA proxy.
- Network: ensure UDP/TCP ports allowed (RADIUS 1812/1813; Duo API 443).
- Time: NTP drift breaks OTP flows (RSA tokens). Sync ISE, Duo proxy, RSA at NTP servers.
- User enrollment: ensure user/device enrolled in Duo or has an active RSA token. (Duo Security, RSA Community)
ISE side
- Live Logs: Operations → RADIUS → Live Logs — look for Access-Request forwarded to external server, Access-Accept, or Access-Reject. Capture the RADIUS attributes and the
NAS-IP/Called-Stationto validate policies. - Monitoring > System: PSN health and network reachability.
- Debug (lab only): enable RADIUS debug on ISE (use carefully; production can be noisy).
Duo proxy side
- authproxy.log: first stop. See requests from ISE and responses from Duo cloud.
- Verify API connectivity: run
curl -v https://api-<duo>.duosecurity.comfrom proxy to ensure TLS works. - Check AD binds when using proxy with primary auth to AD. (Duo Security Knowledge Base)
RSA side
- AM logs: view Authentication Manager logs for RADIUS or token validation failures.
- sdconf: ensure
sdconf.recup to date and not expired (if your RSA roll/generation changed keys). (RSA Community)
Packet capture tips
- Capture on path between ISE PSN and Duo proxy:
tcpdump -i eth0 host 10.10.99.10 and port 1812 -w duo_ise.pcap - For Duo API: capture TLS sessions (IP / TCP 443) and inspect timing if push delays are reported.
- For RSA RADIUS: capture RADIUS attribute flows to find Error-Cause codes.
Lab Walkthroughs with Validation (2 canonical scenarios)
Walkthrough 1 — AnyConnect VPN MFA (Duo via Auth Proxy)
Goal: Protect remote VPN with AD + Duo push.
Steps
- Configure Duo Auth Proxy with AD client and radius_server_auto (see sample authproxy.cfg). (Duo Security Knowledge Base)
- Add Duo proxy as External RADIUS server in ISE (Administration).
- Configure ISE Authentication policy rule for VPN SSID → forward to Duo external RADIUS.
- Test VPN login: user types AD creds → ISE forwards to Duo proxy → Duo triggers push → user accepts → ISE allows VPN access.
Validation
- Duo proxy logs show AD bind, Duo push, and success.
- ISE Live Logs show Access-Request forwarded, Access-Accept returned, and applied Authorization profile.
- VPN client connected.
Walkthrough 2 — Wired 802.1X step-up for privileged VLAN (RSA SecurID)
Goal: When a user attempts to reach privileged resources, require RSA token (Step-up).
Steps
- Configure RSA AM and get
sdconf.rec. Configure ISE Native SecurID realm OR configure RSA as external RADIUS token server. (RSA Community) - On ISE, create an Authentication Policy that upon detection of sensitive SSID/ACL triggers forwarding to RSA for token validation (EAP inner methods or challenge).
- Test: user authenticates normally but when requesting privileged ACL, ISE issues reauth/step-up requiring token. User enters tokencode → ISE validates with RSA → applies privileged authorization.
Validation
- ISE Live Logs show RSA challenge/response and final Access-Accept.
- RSA logs show tokencode validation.
Expert Level Use Cases
- TACACS+ Admin CLI with Duo Push — Protect device admin sessions: devices authenticate to ISE TACACS+ → ISE proxies to Duo Proxy → duo push to admin phone before TACACS+ shell granted. Validate with TACACS+ debug and Duo logs.
- Conditional MFA — Use ISE policy: require MFA only when device posture is NonCompliant OR user coming from untrusted network. Implement step-up via reauth (CoA) or by proxying during initial RADIUS flow. Validate with posture sample and ISE Live Logs.
- Guest Sponsor OTP (Duo or RSA as SMS/OTP) — For guest flows, call external portal or use ISE portal to create guest then use MFA provider or SMS gateway to send OTP or passcode. Validate guest monitor and verify logging.
- High-Availability Duo Proxy — Deploy multiple Duo proxies and configure ISE external RADIUS servers with both IPs (primary/secondary). Test failover by stopping primary proxy and ensuring authentication continues.
FAQs: MFA Integration with Cisco ISE (Duo, RSA SecurID)
1. Can Cisco ISE directly act as an MFA server, or does it only integrate with third-party MFA providers like Duo/RSA?
Cisco ISE cannot act as an MFA server. Instead, it integrates with third-party MFA providers (Duo, RSA, Okta, Azure MFA, etc.) through RADIUS or SAML. ISE enforces policies while the MFA provider handles secondary authentication.
Validation: In ISE GUI → Administration > External Identity Sources → verify Duo or RSA configured as RADIUS Token Server.
2. What are the key integration methods for MFA in Cisco ISE?
- RADIUS Proxy Method – ISE forwards authentication requests to Duo/RSA.
- Inline RADIUS Challenge (Step-Up Authentication) – ISE sends a challenge to the MFA server.
- SAML Redirection – ISE redirects web authentication to MFA IdP.
Validation: On CLI, useshow logging application ise-psc.logto confirm MFA challenge exchange.
3. How does the user authentication flow work with Duo MFA in ISE?
- User enters primary credentials (AD/LDAP).
- ISE validates credentials.
- ISE sends RADIUS Access-Request to Duo Proxy.
- Duo sends OTP push/approval to the user.
- Upon success, Duo replies RADIUS Access-Accept.
Validation: Wireshark trace → look for Access-Challenge / Access-Accept exchange with Duo.
4. What happens if the MFA server (Duo/RSA) is down—does user authentication fail?
Yes, by default authentication will fail-closed for security.
But you can configure ISE fail-open policies for specific scenarios (guest VLAN, limited access).
Validation: ISE → Policy Sets > Authentication Policy → add fallback rule to “Permit Access” with low priority.
5. How do I configure ISE to forward authentication to RSA SecurID?
- Configure RSA Authentication Manager as a RADIUS Token Server in ISE.
- Add RSA server IP + shared secret.
- Bind it in Authentication Policy.
Validation: In ISE GUI → Test Connection → success message should show “Authentication Server reachable”.
6. Can ISE perform step-up authentication (e.g., normal login + MFA only for privileged access)?
Yes. Step-up can be achieved by Policy Sets where MFA is triggered only if conditions match (e.g., AD group = Admins, resource = critical VLAN).
Validation: Test login as normal user (no MFA) vs. admin user (MFA prompt).
7. Is certificate-based authentication compatible with MFA in ISE?
Yes. Certificate (EAP-TLS) can be used as first factor, then MFA server provides second factor (OTP, push, token).
Validation: In ISE Live Logs → check authentication record → first EAP-TLS success → then RADIUS Access-Challenge from Duo/RSA.
8. What are common troubleshooting steps when MFA is not working in ISE?
- Check ISE Live Logs for RADIUS Access-Reject.
- Verify NTP sync between ISE and MFA servers (OTP failures often due to clock drift).
- Ensure firewall allows RADIUS UDP 1812/1813 between ISE and Duo/RSA.
- Use CLI:
show radius statisticsfor dropped/rejected packets.
9. How do I provide a seamless user experience (no repeated MFA prompts)?
- Enable MFA session caching in Duo or RSA policies.
- Configure ISE Authorization Profiles to allow re-use of session token until expiry.
Validation: User re-authentication within cache period should bypass second MFA.
10. Can MFA integration with ISE work for both wired, wireless, and VPN users?
Yes.
- Wired/Wireless → MFA triggered during 802.1X or WebAuth portal login.
- VPN (AnyConnect) → ASA or FTD forwards authentication to ISE, then ISE enforces MFA with Duo/RSA.
Validation: Test in lab topology → Wired 802.1X (AD + Duo), Wireless Guest Portal (SMS OTP), VPN (RSA Token).
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes (key takeaways)
- Design choice matters: Duo proxy is reliable and flexible; native ISE→Duo API reduces infrastructure but depends on ISE release. Pick the pattern that fits your operational model. (Duo Security Knowledge Base, Cisco)
- Test the whole chain (ISE → proxy → AD → Duo/RSA) — most production issues are network, secret, or enrollment problems.
- Monitor and log: Duo proxy logs, ISE Live Logs, and MFA provider dashboards are your triage tools.
- Security: Use TLS for API calls, NTP sync for tokens, and rotate secrets/ssh keys.
Upgrade Your Skills — Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to Network Journey on YouTube and join my instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro — 4-month instructor-led, lab-heavy course: EVE-NG/VMware labs, weekly live debugging, exam-style scenarios.
Reserve a seat & get the MFA labpack: https://course.networkjourney.com/ccie-security/
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![[Day 41] Cisco ISE Mastery Training: Wireless 802.1X Authentication Overview](https://networkjourney.com/wp-content/uploads/2025/08/Day-41-Cisco-ISE-Mastery-Training-Wireless-802.1X-Authentication-Overview.png)

