[Day 139] Cisco ISE Mastery Training: Firewall Dynamic ACLs
Table of Contents
Introduction
Firewall Dynamic ACLs (often called downloadable ACLs or dACLs) let Cisco ISE return per-session, per-user, or per-device access rules to enforcement points (firewalls, routers, switches, VPN gateways) at the moment the session is authorized. Instead of static, coarse ACLs tied to VLANs or host-based rules, dynamic ACLs enable least-privilege, contextual access — e.g., “finance_user on compliant laptop gets ACL that allows only finance-app servers on 443; non-compliant BYOD gets quarantine ACL.” That’s powerful for Zero Trust: identity + posture + context → ephemeral firewall policy.
Why this matters in ISE training: You must know how to author dACLs in ISE, map them to Authorization Profiles, expose them in RADIUS replies, and confirm enforcement on vendor gear — and how to troubleshoot when something goes wrong.
Problem Statement
Real-world pain points:
- Static ACLs cause rule sprawl and over-privilege.
- Many enforcement points (VPNs, firewalls, switches) require different ACL formats.
- Teams struggle to map user identity and device posture to firewall policy in real time.
- Emergency containment (quarantine) is manual and slow.
This topic shows how to automate enforcement: ISE evaluates identity/posture and dynamically issues ACLs to enforcement points so access is always minimal and auditable.
Solution Overview
High level flow:
- User/device authenticates to a Network Access Device (NAD) — switch, WLC, VPN, firewall.
- ISE authenticates the user (AD/LDAP, certificates) and evaluates posture/profiling.
- Authorization policy chooses an Authorization Profile which contains a dACL (or references a named ACL or Filter-ID, or assigns a downloadable ACL payload).
- ISE returns the ACL via RADIUS attributes in the Access-Accept (and issues CoA if needed to change an existing session).
- Enforcement device parses the RADIUS reply and applies the ACL to the session (inbound/outbound as configured).
Important enforcement variants:
- dACL payload pushed (ISE provides full ACL lines that the device can accept).
- Filter-ID / ACL name (ISE returns a
Filter-IDand the device maps that to a local ACL). - Vendor AV-pair (Vendor-Specific Attribute carrying the ACL).
- SGT / TrustSec (ISE returns SGT and firewall enforces SGT policies — alternate enforcement mechanism).
We’ll implement the dACL pattern and show vendor-specific validation/CLI.
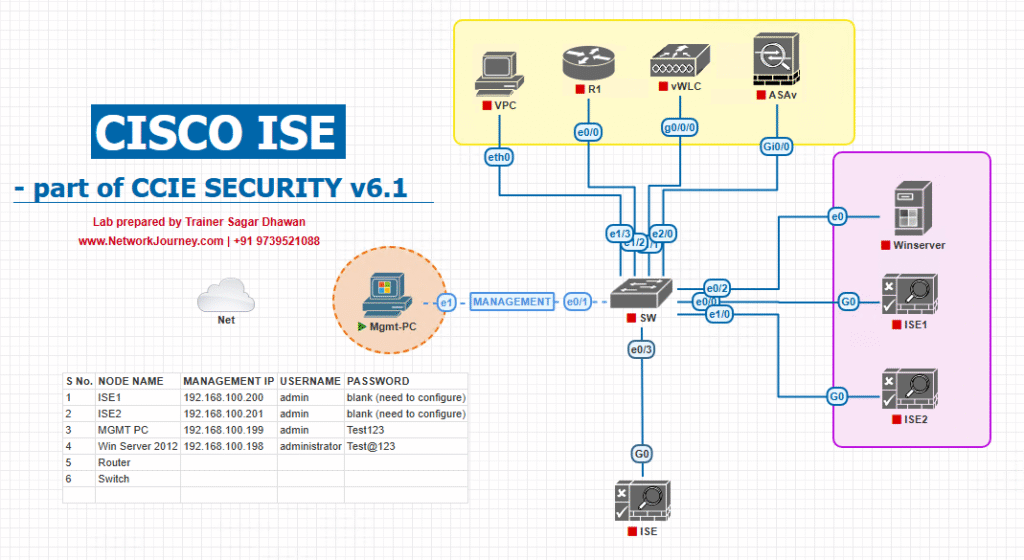
Sample Lab Topology
Platform: VMware or EVE-NG.
Components
- ISE (PAN + PSN) — 10.10.10.11
- Active Directory (LDAP) — 10.10.20.10
- Firewall (Cisco ASA / FTD / NGFW) — 10.10.40.10 (example enforcement point)
- Switch (access switch) — 10.10.30.10 — optional for 802.1X/MAB flows
- VPN Gateway (AnyConnect / ASA) — 10.10.50.10 — optional for remote dACL examples
- Client A (Finance laptop) — 172.16.110.101
- Client B (Guest / BYOD) — 172.16.110.150
- Lab host (packet capture, REST test tools) — 10.10.99.50
Topology Diagram:
Notes
- Use a test VLAN for safe experiments.
- Snapshot before live experiments.
- If you don’t have a physical firewall that supports dACLs, you can emulate behavior by using an IOS XE switch that supports dynamic ACLs or test via VPN gateway.
Step-by-Step GUI Configuration Guide (ISE + Enforcement examples)
Below we show a reproducible lab sequence:
- A. Create a downloadable ACL in ISE (dACL).
- B. Create Authorization Profile that contains the dACL.
- C. Map Authorization rule to return the dACL for a test user.
- D. Configure firewall as a RADIUS client to accept downloadable ACLs.
- E. Test and validate with CLI, Live Logs and packet captures.
A — Create a downloadable ACL in ISE (GUI)
- Login to ISE (PAN).
- Policy > Policy Elements > Results > Authorization > Authorization Profiles → Add.
- Name:
AP_dACL_FINANCE - Access Type:
ACCESS_ACCEPT - Under the Downloadable ACL (dACL) section (or Advanced > Downloadable ACL depending on ISE version) paste the ACL body — use ISE GUI editor.
- Example dACL (Cisco ASA / general ACL syntax sample):
- Name:
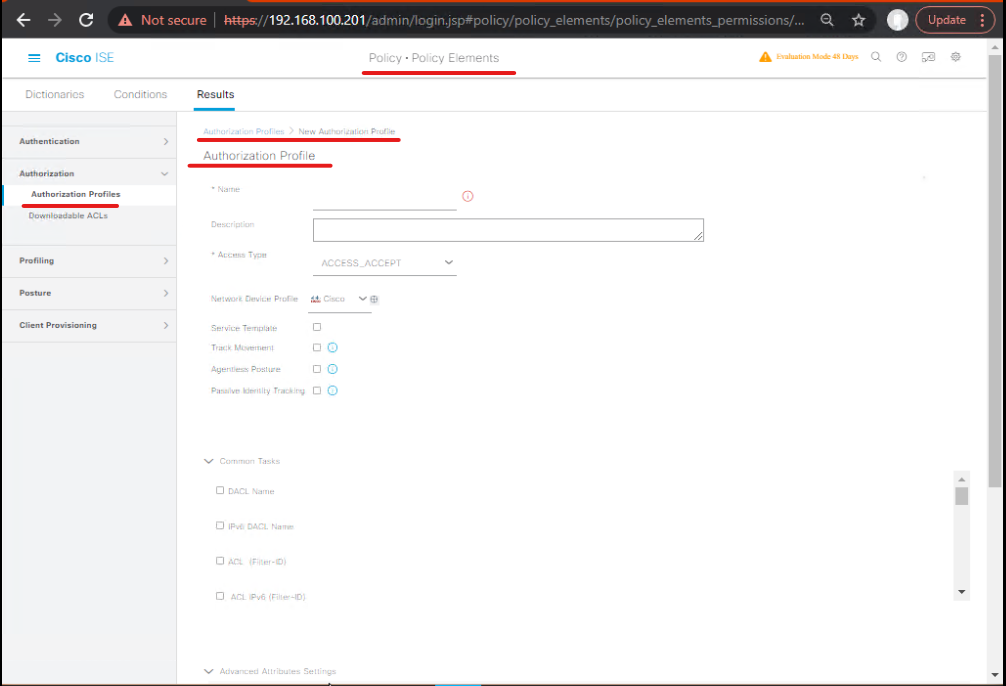
access-list ISE_FINANCE_DACL extended permit tcp any host 10.10.200.50 eq 443 access-list ISE_FINANCE_DACL extended deny ip any any
- Alternatively, many ISE GUIs allow you to enter as lines; choose direction (inbound/outbound) if supported.
- Set any additional attributes (VLAN, SGT) as needed.
- [Screenshot: ISE Authorization Profile Add — Downloadable ACL section]
- Save Authorization Profile.
Notes
- dACL syntax must match the enforcement platform support (ASA vs IOS vs FTD). ISE can store ACL payload; the enforcement device must accept and parse it. If your device doesn’t support payloads, use
Filter-IDmapping or vendor AV-pair mapping (covered later).
B — Create Authorization Profile mapping (GUI)
- Policy > Policy Elements > Results > Authorization → Add Profile
AP_FINANCE_DEFAULT(or reuse above) that referencesAP_dACL_FINANCE. If your version separates dACL and profile, link them here.- Also set
VLANorDownloadable ACLfields as appropriate. - [Screenshot: Authorization Profile referencing dACL]
- Also set
- Save.
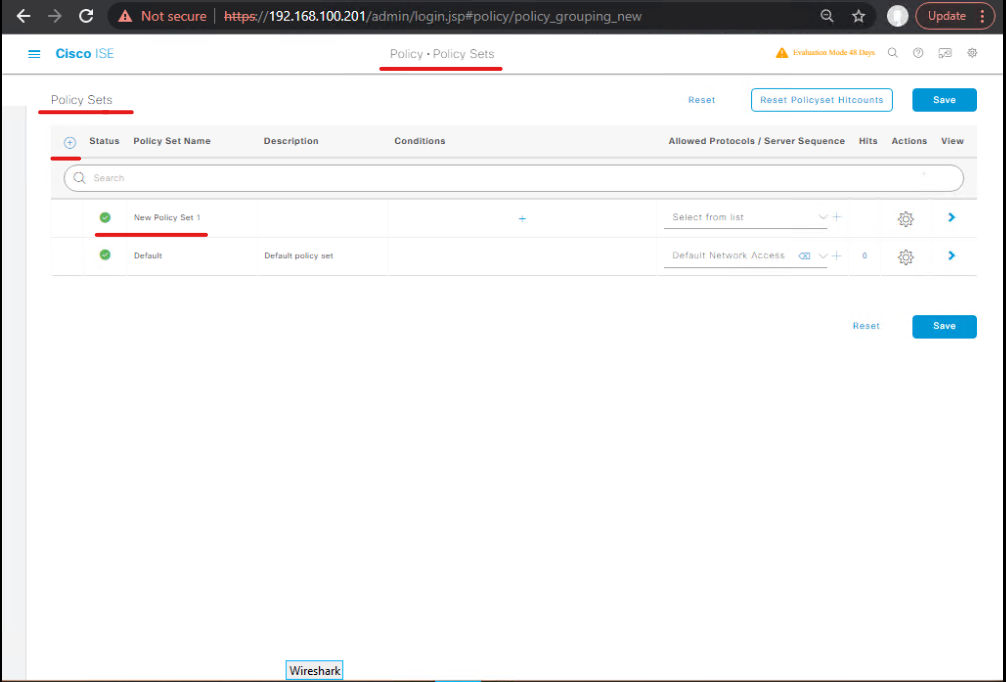
C — Create Authorization Rule in a Policy Set (GUI)
- Policy > Policy Sets → choose the appropriate Policy Set (e.g., Default or a VPN policy set). Click Authorization.
- Add top rule:
- Condition:
Identity Group == AD Group 'Finance'ORNetwork Access:Identity == finance_user - Result: Use Authorization Profile =
AP_dACL_FINANCE. - Place it above broader rules (order matters!).
- [Screenshot: Policy Set → Authorization rule -> AP_dACL_FINANCE]
- Condition:
- Save and Publish (if needed).
Validation in ISE GUI: Use the Policy Tester (if available) to input user & context and confirm the matched Authorization Profile.
D — Add Firewall as Network Device in ISE (GUI)
- Administration → Network Resources → Network Devices → Add.
- Name:
FW-ASA-LAB - IP Address:
10.10.40.10 - Device Profile: choose
ASA/Adaptive Security ApplianceorGeneric Firewalldepending on vendor. - Shared Secret:
ISE_FIREWALL_SECRET(placeholder) - Enable: RADIUS Authentication, RADIUS Accounting, and Dynamic Authorization (CoA) (tick boxes).
- [Screenshot: ISE Admin > Network Devices > Add device]
- Name:
- Save.
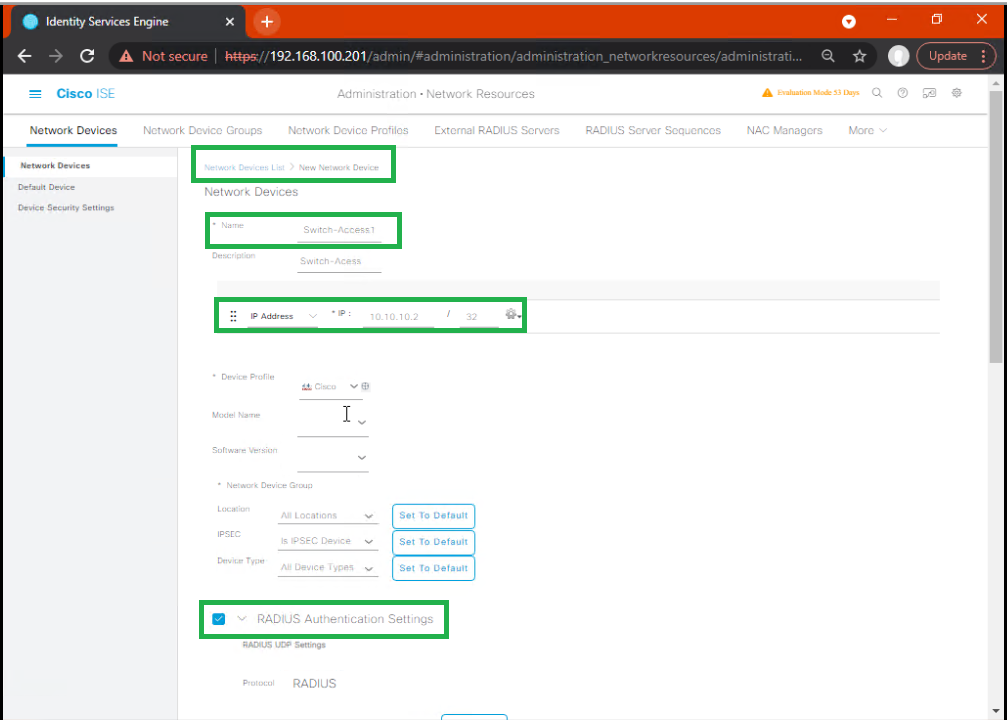
Validation: Use the Test Connection button (if available) or ensure firewall can reach ISE on 1812/1813 from firewall.
E — Configure Firewall to accept dynamic ACLs (Vendor examples & key CLI checks)
NOTE: firewall CLI varies across vendors and versions. Below are representative examples and validation commands. In production follow vendor docs.
Example 1 — Cisco ASA (representative configuration)
- Configure RADIUS server connection to ISE:
! Define RADIUS server group aaa-server ISE_Radius protocol radius aaa-server ISE_Radius (inside) host 10.10.10.11 key ISE_FIREWALL_SECRET
- Configure AAA authentication for VPN or user authentication to use ISE (this varies by use case). For downloadable ACLs on ASA, ensure the ASA supports RADIUS downloadable ACLs (typically by
cisco-avpairorFilter-Idconventions); many ASA versions supportdaclvia RADIUS attributes. - Show commands for debugging / validation:
show running-config aaa-server show aaa-server RADIUS ISE_Radius show access-list # shows ACLs applied locally show vpn-sessiondb detail # for AnyConnect sessions show logging | include RADIUS
How ASA consumes dACL
- ASA may accept a
Filter-IDor vendor AV-pair that maps to a local ACL name or may accept an ACL payload. Check ASA version support. If using Filter-ID: you can create a local ACL named as the Filter-ID and the ASA will apply it by name.
Example 2 — Cisco Firepower/FTD (representative)
- FTD/Firepower typically integrates with ISE via pxGrid/REST or accepts RADIUS attributes for VPN. For FTD, you may map Filter-IDs to access control policies or use API to push ACLs. Validation on FTD:
> show managers > show access-control connections > show running-config | include radius
Example 3 — IOS XE / Nexus switch (representative)
- Many modern switches support downloadable ACLs (dACL) via RADIUS. They accept downloadable ACL name (Filter-ID) and map to local ACLs. Example show commands:
show radius servers show authentication sessions interface Gi1/0/10 details show access-lists
F — Test the flow (end-to-end)
- From Client A (finance_user) perform authentication (802.1X, captive portal, VPN login or MAB).
- ISE evaluates policy and returns Access-Accept with Authorization Profile that includes a dACL.
- Firewall receives RADIUS reply and applies ACL to the client session.
- Client attempts to access
10.10.200.50:443(finance app) — allowed. Client attempts to access other hosts — denied by dynamic ACL.
Validation checklist
- ISE Live Logs: Operations → RADIUS → Live Logs — find the Access-Request/Access-Accept pair; confirm Authorization Profile name and dACL attribute. [Screenshot: ISE Live Logs showing AP_dACL_FINANCE applied]
- Packet capture on ISE↔Firewall: tcpdump
udp port 1812— open Access-Accept and look for RADIUS attributes that contain ACL (vendor attribute, Filter-ID, or dACL lines). Save pcap for class. - Firewall CLI:
show access-listandshow logging— verify dynamic ACL installed and traffic matches/gets permitted/denied accordingly. - Client tests:
curl https://10.10.200.50succeeds;curl http://10.10.200.10fails.
Troubleshooting & Diagnostics
1 — Confirm ISE policy selected the dACL
- ISE Live Logs: find the session and open details. Look for
Authorization Profile = AP_dACL_FINANCEand any related RADIUS attributes exported. If the AP was not selected, fix policy order or conditions.
Quick checks
Policy > Policy Sets > Authorization→ ensure rule order correct.Policy Elements > Authorization→ confirm dACL content saved.
2 — Capture RADIUS traffic: is ISE sending the dACL?
From the firewall or lab host, capture traffic between firewall ↔ ISE:
sudo tcpdump -i eth0 host 10.10.10.11 and udp port 1812 -w radius_ise_fw.pcap
Open in Wireshark. Inspect Access-Accept:
- Look for Filter-Id attribute (standard) OR Vendor-Specific Attribute (VSA) that contains ACL payload.
- If attribute missing — ISE did not send the dACL (policy/config issue). If attribute present — device parsing issue.
3 — Firewall parsing & mapping issues
- If Access-Accept includes Filter-Id or VSA but firewall doesn’t apply ACL: verify firewall supports that attribute format and that there is a local ACL with same name (Filter-Id mapping) OR that firewall supports receiving raw ACL payload (dACL). Check vendor docs for exact RADIUS vendor attribute expected.
Firewall checks
show running-config | include radiusshow access-lists(confirm ACL name created/used)show loggingfor dynamic ACL events / RADIUS parse errors
4 — CoA / Dynamic Reauthorization issues
If you changed policy mid-session and expect firewall to change ACL via CoA:
- Verify Dynamic Authorization (CoA) is enabled on the network device entry in ISE and that the firewall accepts CoA (RFC-3576).
- Capture CoA traffic (usually TCP/3799) between ISE and firewall:
tcpdump -i eth0 host 10.10.10.11 and tcp port 3799 -w coa.pcap
- On firewall, look for CoA messages and error causes.
5 — Common failure modes & fixes
- No dACL in Access-Accept → policy misconfig or ISE version/feature mismatch. Check AP contains dACL and publish/save.
- Device doesn’t accept ACL payload → vendor mismatch; switch to
Filter-Idmapping or use vendor AV-pair. - Authentication works but rules not applied → device restricted (no support for dynamic ACLs) or RADIUS attribute naming mismatch. Use
Filter-IDfallback. - CoA NAK → check RFC-3576 enablement, shared secrets and port connectivity. Inspect Error-Cause attribute in CoA-NAK.
Lab Walkthroughs with Validation
Lab Walkthrough 1 — dACL applied for VPN user (AnyConnect) — Finance access
Scenario: Remote finance user authenticates via AnyConnect; ISE returns a dACL that allows only finance servers.
Steps
- Configure ISE Authorization Profile
AP_dACL_FINANCEwith ACL lines permitting finance app and denying other traffic. - Add Authorization Rule: AD group Finance → AP_dACL_FINANCE.
- Configure ASA/AnyConnect to use ISE as RADIUS auth server.
- Connect AnyConnect from ClientA → authenticate.
- Validate:
- ISE Live Logs show AP_dACL_FINANCE selected.
- Capture RADIUS on ASA → Access-Accept contains Filter-ID or VSA with ACL.
- ASA
show vpn-sessiondb detail anyconnectshows applied group-policy/ACL. - Client can reach finance app (tcp 443) and is blocked from other servers.
Artifacts to collect for class: ISE Live Logs screenshot, pcap of RADIUS Access-Accept, ASA show vpn-sessiondb output, client curl results.
Lab Walkthrough 2 — Quarantine a workstation via dynamic ACL (SOC automation)
Scenario: SOC flags a workstation as compromised; orchestrator calls ISE to change the endpoint’s Authorization Profile to a quarantine dACL.
Steps
- Create
AP_QUARANTINEdACL that permits only remediation servers (NAC, AV update) and blocks everything else. - SOC automation calls ISE ERS API or pxGrid to set endpoint to a group or change Authorization to
AP_QUARANTINE(show ERS sample cURL later). - ISE issues CoA to firewall/switch to change ACL for the session.
- Validate:
- ISE Live Logs show change in Authorization and CoA sent.
- Firewall logs show ACL change; traffic blocked except remediation hosts.
- Attempt to access blocked services fails.
Minimal ERS cURL example (lab; replace with farm credentials):
curl -k -u ersadmin:ERSPASS \
-H "Content-Type: application/json" \
-X PUT https://10.10.10.11:9060/ers/config/endpoint/<endpoint_id> \
-d '{"@status":"Quarantined","customAttributes": {"authProfile":"AP_QUARANTINE"}}'
(Exact ERS payloads differ by ISE version — this is conceptual. Use ISE ERS docs for precise syntax.)
Expert Level Use Cases
- Per-user, per-session VPN dACL — return dACL with ephemeral ACLs for each user (user-based app ACLs). Validate with session logs and per-user pcap samples.
- Time-boxed admin access — during maintenance window grant admin an ACL allowing management ports for defined time then revoke via CoA. Validate timers and CoA.
- IoT containment — when IoT device fails posture, set quarantine dACL blocking all but telemetry endpoints. Validate with pcap and ISE Live Logs.
- Patch window temporary access — change endpoint to dACL that allows patch server IPs only and then revert after patching. Validate access windows and automation logs.
FAQs
Q1 — What’s the difference between a dACL and Filter-ID? Which should I use?
A:
- dACL (downloadable ACL): ISE returns ACL payload (ACL lines). The NAD must accept and install the payload. Good when devices support it.
- Filter-ID: ISE returns a token (
Filter-Id) naming an ACL; the NAD matches it to a preconfigured local ACL. Use Filter-ID when device doesn’t accept raw payloads.
Validation: Capture Access-Accept and see whether attributeFilter-Idor a VSA with ACL payload is present.
Q2 — Do all firewalls support downloadable ACLs?
A: No — support varies by vendor and version. If not supported, use Filter-ID mapping or vendor-specific AV-pairs, or enforce via central firewall using IP→SGT + SXP (TrustSec) mapping.
Validation: Consult vendor docs; in lab, capture Access-Accept and observe firewall behavior.
Q3 — How does ISE send the dACL (which RADIUS attribute)?
A: ISE uses RADIUS attributes — commonly Filter-Id (standard) or vendor-specific attributes (VSAs) carrying ACL payloads. The exact VSA format depends on vendor. Inspect Access-Accept in capture to see what’s sent.
Validation: tcpdump the Access-Accept and inspect attributes in Wireshark.
Q4 — How do I test a dACL in a lab safely?
A: Start with a test VLAN and test firewall or a dedicated lab firewall virtual. Use non-production IPs, avoid port-shutdown CoA actions, and always snapshot devices. Validate using pcap, Live Logs and client connectivity tests.
Q5 — What should I do if Access-Accept contains the ACL but the firewall doesn’t apply it?
A: Check (1) vendor support and exact attribute format, (2) firewall parse logs for RADIUS errors, (3) whether local ACL name exists (for Filter-ID workflows), (4) if the payload syntax matches the firewall OS.
Validation: firewall logs + show access-lists + packet capture.
Q6 — Can ISE push per-user ACLs for thousands of users? Performance concerns?
A: Yes — but beware scale. dACLs per session increase CPU/memory on enforcement devices and RADIUS traffic volume. Test scale in lab and consider using Filter-ID or SGT-based policies for high scale.
Validation: Load test in lab, monitor firewall CPU, memory and RADIUS throughput.
Q7 — How do CoA and reauthorization affect dACLs?
A: ISE sends CoA to update an existing session when Authorization changes (e.g., posture changes). CoA must be enabled on the NAD and require RFC-3576 support. Inspect CoA traffic and ISE logs when reauthorizing.
Validation: tcpdump for TCP/3799 and Live Logs showing CoA request/responses.
Q8 — How should I securely manage dACLs and avoid injection or malformed ACLs?
A: Sanitize ACL content, limit who can create Authorization Profiles, use role-based admin access in ISE, and test ACLs in lab. Audit changes and use change control for dACL modifications.
Validation: Review ISE admin audit logs and Authorization Profile change history.
Q9 — Can dynamic ACLs be used for cloud ZTNA brokers?
A: Yes — you can return Filter-IDs or custom attributes that ZTNA brokers or CASBs consume (via SAML claims or pxGrid) to apply session policies at application layer. Implementation depends on the broker.
Validation: Confirm broker receives attributes and enforces mapped policy.
Q10 — What are the best practices for fallback if dACLs fail?
A: Provide safe default authorization (e.g., limited guest VLAN or controlled network), avoid full open-fail behavior, use monitoring/notify on dACL failure, and automate rollbacks. Test failover thoroughly.
Validation: Create a test scenario where dACL provisioning fails and confirm fallback policy applied.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes (key takeaways)
- Dynamic ACLs let identity & posture drive real-time firewall policy. They’re vital for Zero Trust enforcement.
- Know your vendor: syntax, attribute formats, and CoA support differ. Always test in a lab.
- Monitor & audit: Log dACL issuance, CoA events, and enforcement success to close the control loop.
- Scale & safety: use Filter-ID or SGT-based approaches where per-session ACL payloads create device stress or management overhead.
Upgrade Your Skills — Start Today
For a full, hands-on Cisco ISE mastery path, subscribe to Network Journey on YouTube and join my instructor-led Fast-Track to Cisco ISE Mastery Pro — a 4-month live lab program covering ISE, TrustSec, dACLs, pxGrid automation and CCIE-grade scenarios.
Reserve your seat & claim the dACL lab pack: https://course.networkjourney.com/ccie-security/
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



![[Day 42] Cisco ISE Mastery Training: Integrating Cisco WLC for Wireless Access Control](https://networkjourney.com/wp-content/uploads/2025/08/Day-42-Cisco-ISE-Mastery-Training-Integrating-Cisco-WLC-for-Wireless-Access-Control.png)