[Day 143] Cisco ISE Mastery Training: Advanced Posture Multi‑Condition Compliance
Table of Contents
Introduction
In modern enterprise networks, simply authenticating a device is no longer enough. Users bring multiple devices, mobile OSes enforce randomization, and threats like unpatched vulnerabilities or non-compliant applications are everywhere.
Advanced Posture Multi‑Condition Compliance in Cisco ISE addresses these realities. By evaluating multiple conditions simultaneously—OS version, patch level, antivirus status, disk encryption, running processes, and more—ISE can make granular access decisions in real time.
This Article demonstrates how to build complex posture policies using multiple conditions, integrate them with network devices, and enforce dynamic remediation via CoA. Students will learn to:
- Combine multiple posture conditions in a single policy.
- Validate device compliance using GUI, CLI, and logs.
- Troubleshoot failures in real time.
- Map advanced posture use cases to real-world enforcement scenarios.
This Article is a step-by-step masterclass for engineers who want production-ready NAC enforcement beyond simple endpoint checks.
Problem Statement
Enterprises face multiple challenges in posture compliance:
- Devices may be partially compliant (e.g., patched OS but outdated AV).
- Single-condition posture policies fail to provide risk-aware access.
- BYOD and corporate devices require different enforcement levels.
- Manual remediation is inefficient; automated enforcement (CoA) is required.
Without multi-condition compliance, enterprises risk:
- Unauthorized access from non-compliant endpoints.
- User productivity loss due to overly restrictive single-condition rules.
- Inconsistent security enforcement across wired, wireless, and VPN access.
Solution Overview
Cisco ISE’s Posture Service addresses these challenges by:
- Collecting endpoint attributes: via Cisco AnyConnect, Cisco NAC Agent, or built-in posture agents.
- Evaluating multiple conditions: ISE can simultaneously check OS patch level, antivirus, firewall status, disk encryption, presence of required apps, and custom conditions.
- Applying granular authorization: based on multiple condition evaluations (AND/OR logic).
- Triggering dynamic remediation: using CoA to quarantine, redirect, or allow full access based on compliance.
- Reporting and visibility: Operations → Posture → Posture Reports, showing device-level compliance.
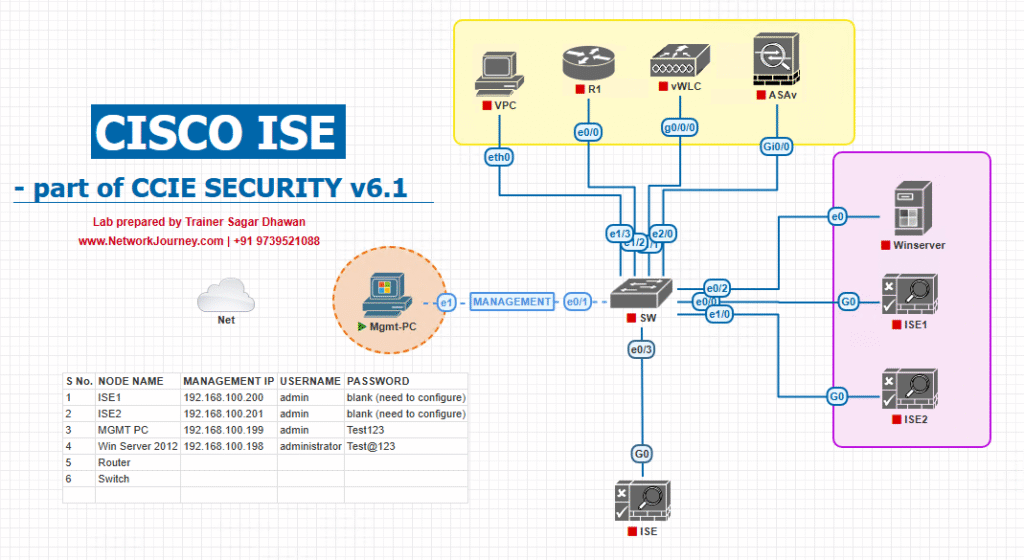
Sample Lab Topology
Lab Components:
- ISE Node (PAN/PSN) – 3.1+ version, single-node lab instance.
- Endpoints – Windows 10, macOS, Android (for posture testing).
- Switch – Catalyst 9300 (802.1X + CoA).
- WLC – Cisco 9800 (Wi-Fi 802.1X + CoA).
- VMware/EVE‑NG – simulates lab network for testing, DHCP, DNS, and AD domain.
- AD + PKI – Microsoft AD + CA for certificates.
Lab Topology:
Step‑by‑Step GUI Configuration Guide
Step 1: Enable Posture Service in ISE
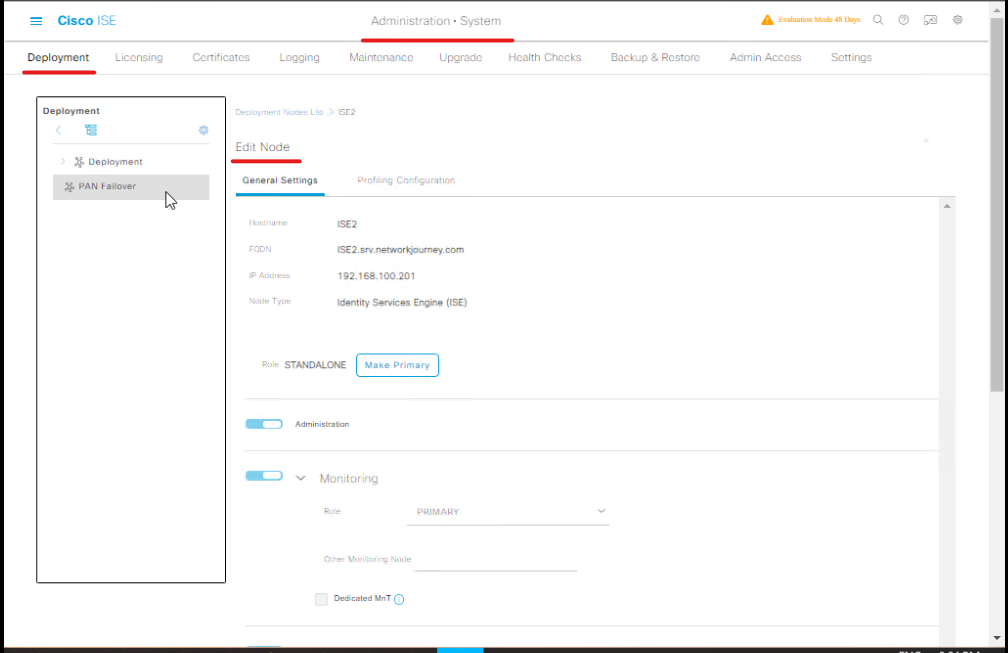
- Log in to ISE Admin GUI → Administration → System → Deployment.
- Select the ISE node (PAN/PSN).
- Click Edit Node → Services → Enable Posture Service.
- Save changes and ensure service is running.
- [Screenshot: ISE Posture Service Enabled]
Validation:
- Navigate Operations → Posture → Endpoints → verify node is listed.
Step 2: Configure Endpoint Profiles
- Administration → Network Resources → Endpoints → Endpoint Profiles → Add
- Define profile for your endpoint type (Windows, macOS, Android).
- Enable Posture Agent support and select AnyConnect/NAC Agent.
- [Screenshot: Endpoint Profile Configuration]
Validation:
- Connect a test endpoint → check Live Logs → Endpoint Detected.
Step 3: Create Individual Posture Conditions
Step 3a: Antivirus Check
- GUI: Policy → Policy Elements → Results → Posture → Conditions → Add
- Name:
AV_Compliant - Type: Endpoint Security → Attribute: Antivirus Status
- Operator: Equals → Value: Running & Up-to-Date
- [Screenshot: Posture Condition – Antivirus]
Step 3b: Firewall Check
- Add new posture condition → Name:
Firewall_Enabled - Type: Endpoint Security → Firewall Status → Equals → Enabled
- [Screenshot: Posture Condition – Firewall]
Step 3c: OS Patch Level
- Add condition → Name:
OS_Patched - Type: OS → OS Version → Greater than or equal → 10.0.19042
- [Screenshot: Posture Condition – OS Patch]
Step 3d: Required Application Installed
- Add condition → Name:
App_Check - Type: Application → Installed Applications → Equals → Zoom OR Slack
- Use logical operator: OR (between apps)
- [Screenshot: Posture Condition – Application]
Validation:
- Navigate Operations → Posture → Posture Reports → simulate endpoint → ensure conditions evaluated individually.
Step 4: Combine Conditions in Multi-Condition Posture Policy
- GUI: Policy → Policy Sets → Posture Policy → Add New
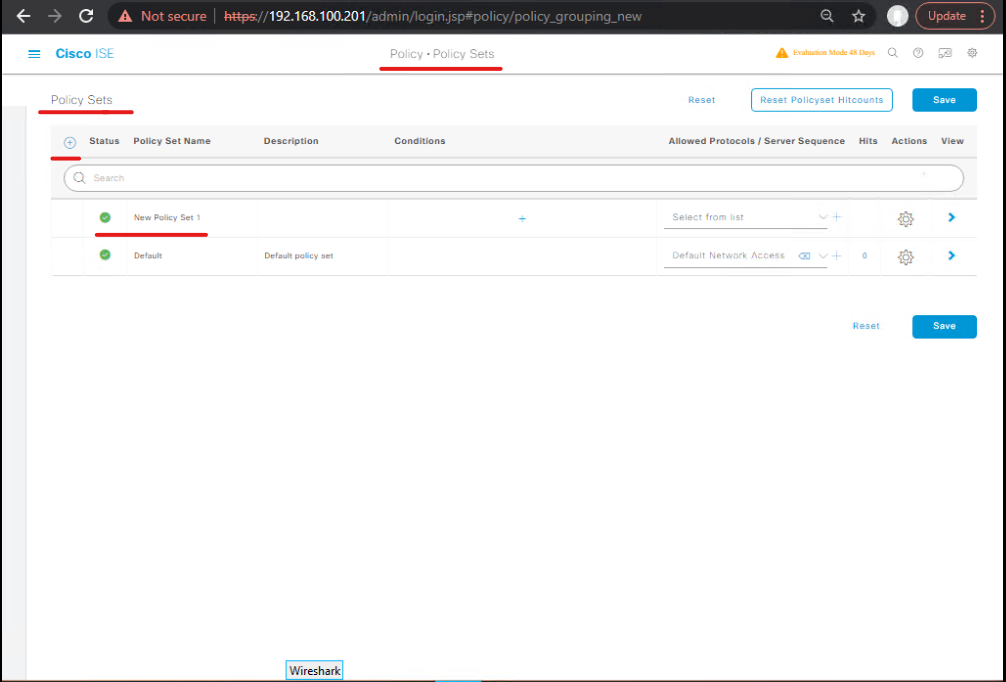
- Name:
Advanced_MultiCondition_Policy - Logic:
IF (AV_Compliant = True) AND (Firewall_Enabled = True) AND (OS_Patched = True) AND (App_Check = True) THEN Full_Access_Profile ELSE Quarantine_Profile
- Save policy.
- [Screenshot: Multi-Condition Posture Policy Set]
Validation:
- Use ISE Live Logs → connect endpoint → check Posture Result Details → all conditions evaluated.
Step 5: Configure Authorization Profiles
Step 5a: Full Access
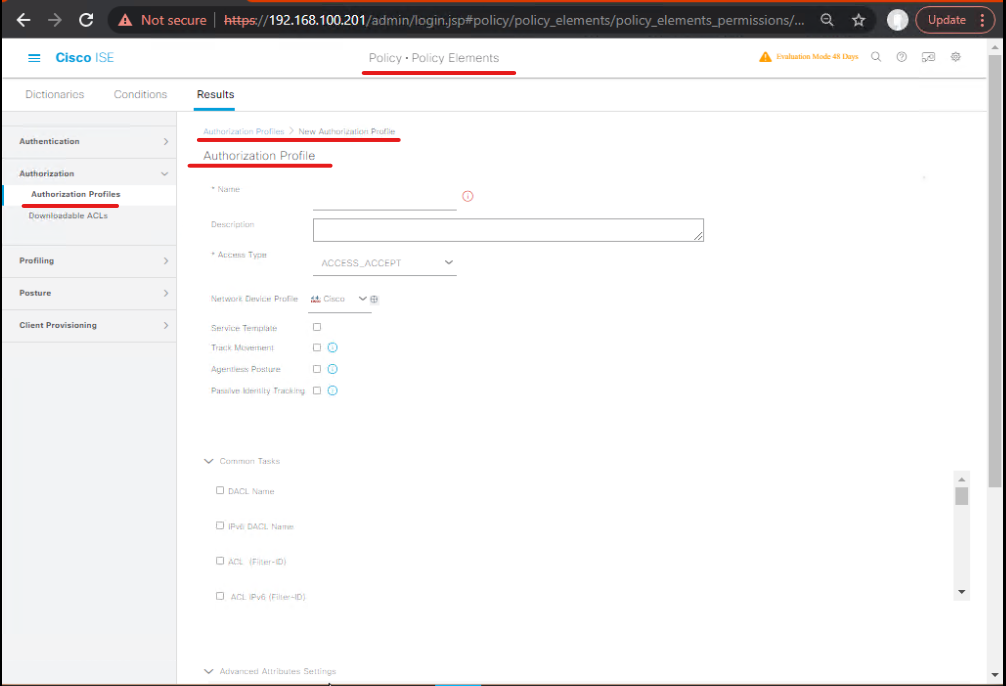
- GUI: Policy → Policy Elements → Results → Authorization → Authorization Profiles → Add
- Name:
Full_Access_Profile - Permit access → VLAN 20 or SGT 20
- Enable CoA
- [Screenshot: Full Access Authorization Profile]
Step 5b: Quarantine / Limited Access
- Add new Authorization Profile → Name:
Quarantine_Profile - Deny or apply restricted VLAN (e.g., VLAN 99)
- Enable CoA for dynamic remediation
- [Screenshot: Quarantine Authorization Profile]
Validation:
- Connect test endpoint → ISE Live Logs → verify correct profile assigned.
Step 6: Configure NAD (Switch/WLC) for 802.1X + CoA
Step 6a: Switch (CLI Example)
aaa new-model radius server ISE address ipv4 10.10.10.10 auth-port 1812 acct-port 1813 key VerySecret123 ! dot1x system-auth-control interface Gi1/0/10 switchport mode access authentication port-control auto dot1x pae authenticator mab
Validation:
show authentication sessions interface Gi1/0/10 detail→ should showAuthorizedorQuarantine.
Step 6b: WLC GUI
- GUI: Controller → Security → AAA → RADIUS → New
- Add ISE IP, Auth/Acct port, shared key
- WLAN → Security → Layer 2 → WPA2 802.1X → assign RADIUS server
- Enable CoA for dynamic posture remediation
- [Screenshot: WLC RADIUS + CoA]
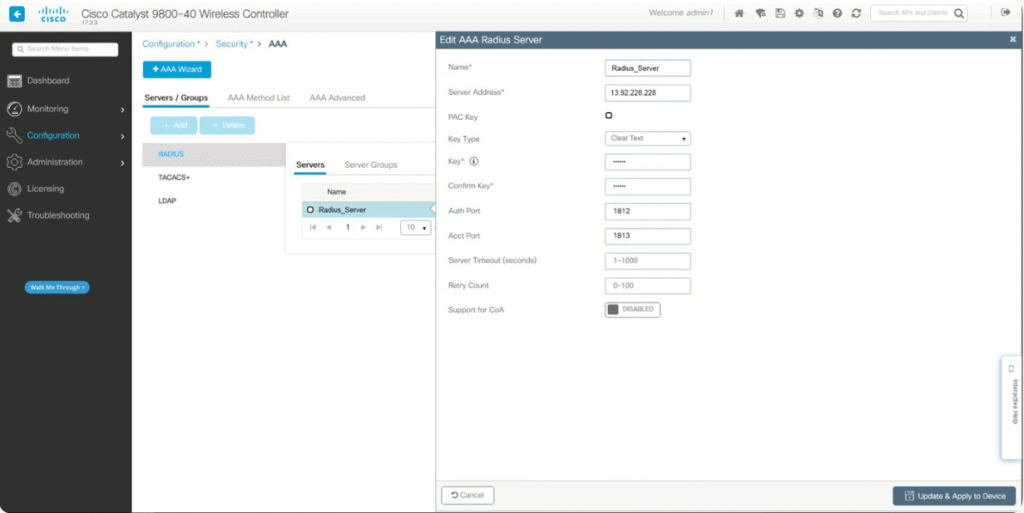
Validation:
- Connect a wireless endpoint → ISE Live Logs → Posture evaluation triggered.
Step 7: Endpoint Agent Configuration
- Install Cisco AnyConnect / NAC Agent
- Enable Posture Module
- Connect to network (wired/wireless) → authentication triggered
- Endpoint evaluates posture conditions and sends result to ISE
- [Screenshot: AnyConnect Posture Module]
Validation:
- Endpoint receives Full Access or Quarantine VLAN
- ISE Live Logs → endpoint compliance detailed
Step 8: Validate Multi-Condition Enforcement
- Scenario 1: All conditions pass → Full Access
- Scenario 2: One condition fails → Quarantine Profile applied
- Scenario 3: Condition resolved while connected → CoA triggers dynamic remediation
GUI Validation:
- ISE → Operations → Live Logs → check compliance, profile assigned
- Reports → Posture → Device Compliance
CLI Validation:
- Switch →
show authentication sessions interface GiX/X detail - WLC →
show client summary+debug aaa radius - Endpoint logs → AnyConnect → Posture evaluation
Troubleshooting & Diagnostics
1. Troubleshooting Tools in ISE
- Live Logs: Operations → Live Logs → filter by Posture, Endpoint, or Authentication.
- Reports: Operations → Reports → Posture → Device Compliance → Historical compliance tracking.
- Endpoint Details: Operations → Endpoints → select endpoint → check Posture Results, Compliance History, Posture Conditions.
- Debug CLI:
debug ise postureservice debug radius show logging application ise postureservice - AnyConnect / NAC Agent Logs: On endpoints, check the posture module logs for errors like missing conditions, agent not installed, or network reachability issues.
2. Common Issues & Diagnostics
| Issue | Symptom | GUI Check | CLI Check | Resolution |
|---|---|---|---|---|
| Endpoint always Non-Compliant | Endpoint fails compliance | Live Logs → Posture Result = Non-Compliant | show authentication sessions interface GiX/X detail → check profile assigned | Verify posture agent installed, conditions mapped correctly |
| CoA not triggering | Quarantined endpoint not moved to Full Access | Live Logs → Posture Evaluation shows compliant | debug radius on switch/WLC, check UDP 1700/3799 open | Enable CoA on NAD, verify firewall/ACL |
| Missing App condition | Policy fails for endpoints with installed apps | Live Logs → Condition evaluation fails | Endpoint logs → Check AnyConnect logs | Check condition syntax, use OR/AND properly |
| AV/Firewall status incorrect | Endpoint passes incorrect state | Live Logs → Attribute mismatch | Endpoint logs → NAC Agent | Update agent, check endpoint OS reporting |
Lab Walkthroughs with Validation
Scenario 1: Fully Compliant Endpoint
- Endpoint meets all posture conditions: AV running, firewall enabled, OS patched, required apps installed.
- Connect endpoint → ISE Live Logs → Posture Result = Compliant
- Switch CLI →
show authentication sessions interface Gi1/0/10 detail→ Authorization Profile = Full Access - Endpoint gets network access → VLAN / SGT 20
Validation Checklist:
- ISE Live Logs → All conditions = True
- Endpoint logs → Posture Module → Compliant
- Switch/WLC → Authenticated, CoA = triggered (if needed)
Scenario 2: Partially Compliant Endpoint
- Endpoint missing required app or AV outdated.
- Connect → ISE evaluates multi-condition policy → Posture Result = Non-Compliant
- Switch CLI → Authorization Profile = Quarantine (restricted VLAN)
- Endpoint shows compliance failure message (AnyConnect / NAC Agent)
Validation Checklist:
- Live Logs → see which condition failed
- Reports → Posture → Device Compliance → verify historical state
- Endpoint → Agent logs → shows failing condition
Scenario 3: Dynamic Remediation with CoA
- Endpoint initially Non-Compliant → quarantined
- Endpoint fixes issue (installs app, updates AV)
- ISE detects compliance change → sends CoA to NAD
- Switch/WLC applies Full Access → Endpoint now granted network access
Validation Checklist:
- Live Logs → Compliance changed to Compliant
- Switch CLI →
show authentication sessions interface GiX/X detail→ Authorization Profile updated - Endpoint logs → Posture Module shows successful remediation
Expert Level Use Cases (Step-by-Step Mapping + Validation)
Use Case 1: BYOD Enforcement
- Goal: Employee-owned devices limited if OS not patched or missing required apps.
- Step-by-Step Mapping:
- Define Endpoint Profile = Employee-Owned BYOD
- Create multi-condition posture policy: OS patch AND required apps
- Assign Authorization Profile = Quarantine if non-compliant
- Validate endpoint → Live Logs → Profile assigned, correct VLAN applied
- CLI Validation:
show authentication sessions interface Gi1/0/XX detail→ confirms correct profile
Use Case 2: Corporate Device Full Access
- Goal: Corporate laptops receive Full Access if fully compliant.
- Step-by-Step Mapping:
- Endpoint Profile = Corporate Device
- Multi-condition policy: AV running, firewall enabled, OS patched, apps installed
- Authorization Profile = Full Access
- Test endpoint → Connect via WLAN → Full Access granted
- GUI Validation: Live Logs → Compliant → Full Access Profile
- CLI Validation: Switch/WLC → session shows VLAN/SGT assignment
Use Case 3: Multi-App Enforcement for Finance VLAN
- Goal: Finance users require multiple apps installed for network access.
- Step-by-Step Mapping:
- Posture Condition: App1 AND App2 installed
- Multi-condition policy includes AV + Firewall + App Check
- Authorization Profile = Finance VLAN (VLAN 50)
- Test endpoint → If missing App2 → quarantined → User notified via AnyConnect
- Validation:
- Live Logs → Condition failed = App2 missing
- Endpoint → AnyConnect → notification displayed
- Fix app → CoA triggers → VLAN 50 applied dynamically
Use Case 4: Dynamic CoA-Based Remediation
- Goal: Automatically move endpoints from Quarantine → Full Access after compliance fixes.
- Step-by-Step Mapping:
- Endpoint initially fails multi-condition policy
- ISE detects fix (e.g., AV update) → triggers CoA
- Switch/WLC receives CoA → updates Authorization Profile
- Endpoint granted Full Access without disconnecting
- Validation:
- Switch CLI →
show authentication sessions interface GiX/X detail→ Authorization Profile updated - ISE Live Logs → Compliance updated → Full Access applied
- Endpoint logs → Posture Module confirms remediation
- Switch CLI →
Use Case 5: Custom Posture Module
- Goal: Evaluate custom scripts/processes (e.g., check if a specific service is running).
- Step-by-Step Mapping:
- Create Custom Posture Module (CPM) in ISE
- Script returns True/False for condition
- Include CPM in multi-condition posture policy
- Test endpoint → Live Logs show CPM condition evaluated
- Validation:
- ISE Live Logs → CPM result = True/False
- Authorization Profile applied based on policy logic
- Endpoint → AnyConnect → compliance state updated
FAQs — Advanced Posture Multi-Condition Compliance
1. Q: Why do endpoints sometimes show Non-Compliant even though AV, firewall, and OS patch are correct?
A:
- Check Posture Agent installation (AnyConnect/NAC Agent).
- Verify individual condition mappings in the posture policy (AND/OR logic).
- Use ISE Live Logs → Posture Result Details to see which condition failed.
2. Q: How does ISE evaluate multiple conditions in a posture policy?
A:
- ISE evaluates each condition independently.
- Logical operators (AND / OR) determine the overall compliance result.
- Non-compliance in an AND chain → endpoint fails; OR chain passes if any condition is True.
3. Q: What is the recommended way to test multi-condition posture policies before production?
A:
- Create lab endpoints with different compliance scenarios.
- Connect endpoints → check Live Logs → Posture Evaluation.
- Validate VLAN/SGT assignment and CoA enforcement.
4. Q: Why isn’t CoA triggering when an endpoint fixes a compliance issue?
A:
- Ensure CoA is enabled in the Authorization Profile.
- Confirm NAD supports CoA (UDP 1700/3799 open).
- Check ISE Live Logs for CoA sent events and NAD log for CoA received.
5. Q: Can I create posture policies that differentiate BYOD vs corporate devices?
A:
- Yes, use Endpoint Profiles or Ownership attributes.
- Assign different multi-condition policies and Authorization Profiles for each type.
6. Q: How can I verify that each individual posture condition is evaluated?
A:
- Use ISE Live Logs → Posture Result Details → each condition is listed with True/False.
- For endpoint-side validation, check AnyConnect/NAC Agent logs → reports which condition passed/failed.
7. Q: Can I add custom scripts or checks to posture evaluation?
A:
- Yes, use Custom Posture Modules (CPM).
- Scripts can check running processes, registry values, or custom files.
- Add CPM to a multi-condition policy and validate in Live Logs.
8. Q: How do I handle endpoints that do not have the posture agent installed?
A:
- ISE marks them Non-Compliant.
- Apply fallback rules in posture policy → quarantine VLAN or restricted access.
- Educate users to install required posture agent or use onboarding portal.
9. Q: Is it possible to enforce different policies for multiple applications (e.g., Zoom AND Slack)?
A:
- Yes, create a multi-condition policy with each application as a separate condition.
- Use AND/OR logic to control compliance evaluation.
- Validation: ISE Live Logs → shows each application check → overall compliance result.
10. Q: How can I troubleshoot endpoints that fluctuate between compliant and non-compliant?
A:
- Check agent connectivity and polling frequency.
- Validate network latency or packet loss between endpoint and ISE.
- Review Live Logs → Posture Evaluation → Time-stamped events.
- Ensure NADs properly handle CoA and authorization updates.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- Multi-condition compliance is critical for risk-aware NAC.
- Always validate each condition separately before combining.
- Use CoA + dACLs for dynamic enforcement.
- Endpoint agents, NAD configuration, and ISE policy logic are all critical — missing any component causes policy failures.
- This lab provides production-grade mastery for real-world deployment.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro — 4-month live training. Full labs, expert guidance, CCIE Security track. Course outline: https://course.networkjourney.com/ccie-security/
- Hands-on labs
- Real-world posture enforcement scenarios
- CoA & dynamic remediation training
- BYOD + corporate multi-condition compliance
“Reserve Your Seat – Download Free Lab Workbook”
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



