[Day 16] Cisco ISE Mastery Training: Understanding 802.1X Authentication Flow
Table of Contents
Introduction
802.1X is the foundation of secure wired and wireless network access control in enterprise networks.
With Cisco ISE, 802.1X authentication ensures that only authorized devices and users can connect to the corporate network — reducing the risk of data breaches and preventing rogue devices from bypassing security.
This training dives into the real authentication flow, so you understand exactly what happens from the moment a device connects to a switch/WLC, all the way to ISE granting (or denying) access.
Problem Statement
In many networks, unmanaged endpoints, compromised user credentials, or misconfigured switches can allow unauthorized access.
Without 802.1X, a switch port or SSID behaves like an “open door” — no validation, no policy enforcement.
Engineers often struggle to troubleshoot failures because they don’t understand each step of the EAP conversation between supplicant, authenticator, and authentication server.
Solution Overview
Cisco ISE acts as the RADIUS Authentication Server in an 802.1X setup.
The 3 main players in the authentication flow are:
- Supplicant: Endpoint device (PC, laptop, phone) requesting access.
- Authenticator: Network device (switch/WLC) controlling access to the network.
- Authentication Server: Cisco ISE validating credentials and applying policies.
802.1X uses EAP (Extensible Authentication Protocol) to securely exchange authentication information, and ISE enforces role-based access once identity is verified.
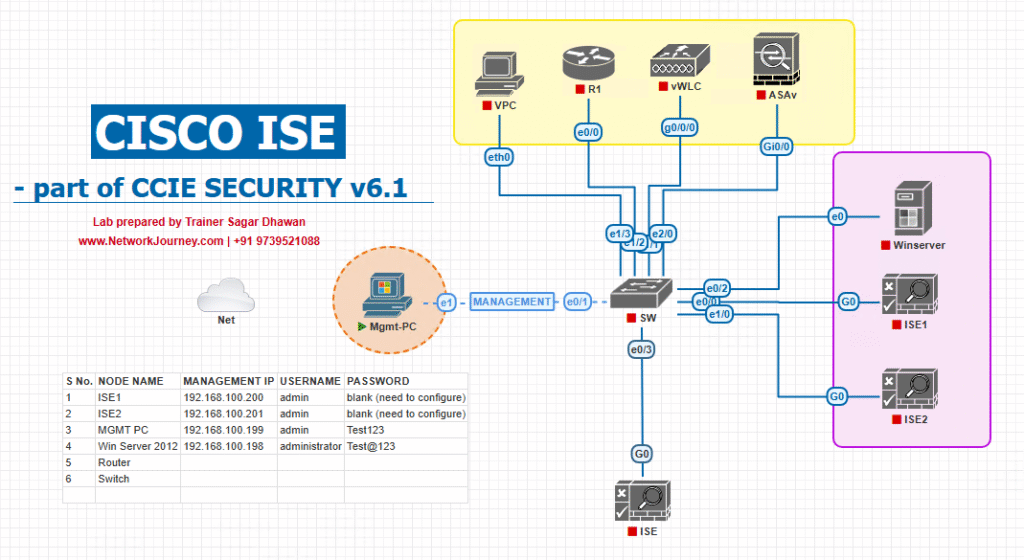
Sample Lab Topology
Lab Environment:
- VMware Workstation / EVE-NG running:
- Cisco ISE 3.x
- CSR1000v or C9300 switch image
- Catalyst 9800 WLC (optional for wireless)
- Windows 10/11 endpoint (with supplicant enabled)
- Optional: Active Directory integration
Topology Layout:
5. Step-by-Step GUI + CLI Configuration Guide
Step 1 – Enable 802.1X on ISE
- Log in to ISE GUI.
- Navigate to Administration > Deployment → Select your ISE node → Enable RADIUS Service.
- [Screenshot: ISE Deployment Node Configuration]
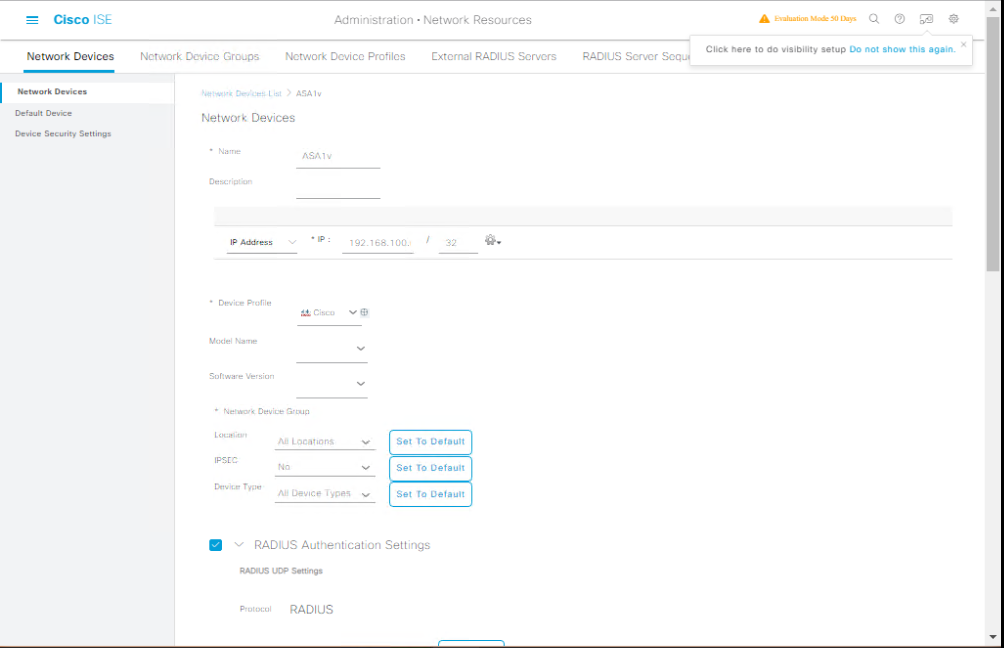
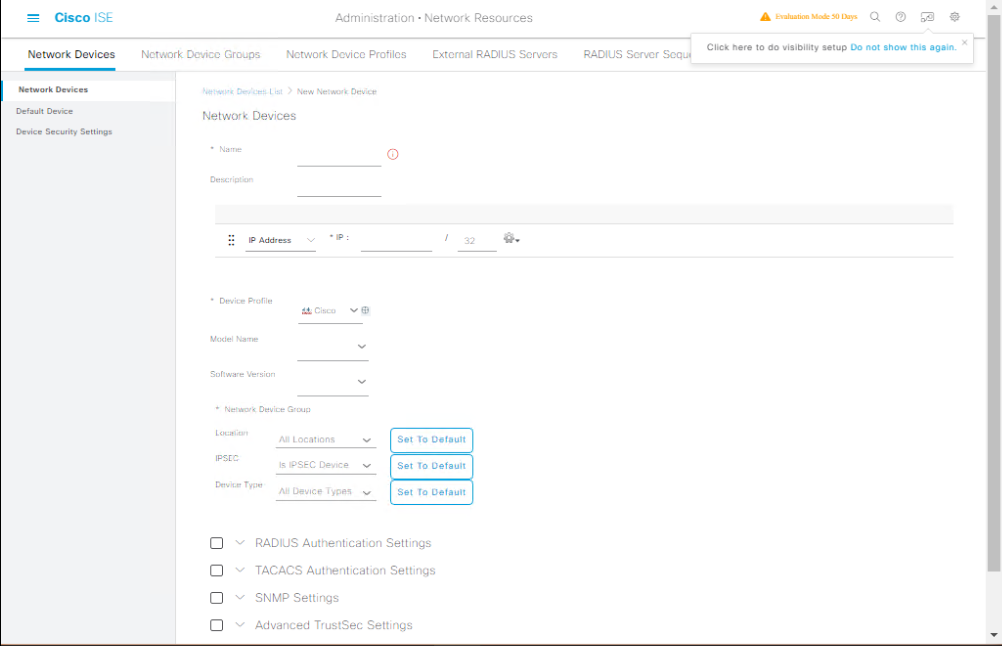
Step 2 – Add the Switch/WLC as a Network Device in ISE
- Administration > Network Resources > Network Devices.
- Click Add → Enter Device Name, IP, and Shared Secret.
- Check RADIUS Authentication Settings.
- [Screenshot: Network Device Add Screen]
Step 3 – Configure the Switch for 802.1X
CLI Commands:
conf t aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius radius-server host <ISE_IP> auth-port 1812 acct-port 1813 key <shared_secret> ! dot1x system-auth-control ! interface Gig1/0/1 switchport mode access switchport access vlan 10 authentication port-control auto mab dot1x pae authenticator spanning-tree portfast end wr mem
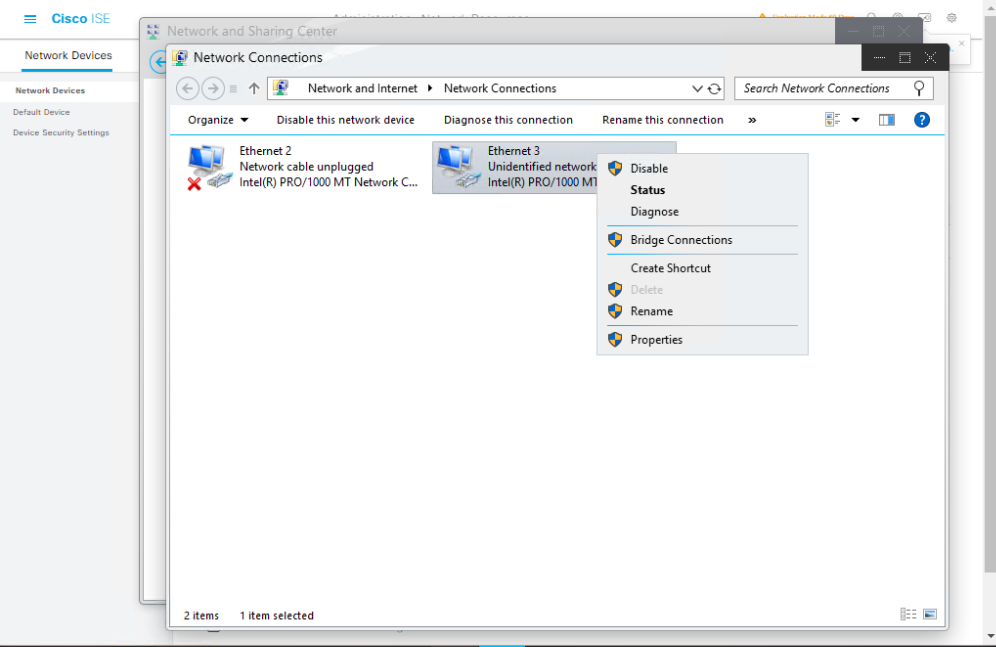
Step 4 – Enable Supplicant on Windows Endpoint
- Go to Control Panel > Network & Sharing > Adapter Settings → Ethernet → Properties → Authentication tab → Enable 802.1X and choose EAP method.
- [Screenshot: Windows Supplicant Config]
Step 5 – Create ISE Policy Set for 802.1X
- Go to Policy > Policy Sets.
- Create a new policy with conditions:
- Protocol = RADIUS
- Authentication method = EAP-PEAP or EAP-TLS
- Add authorization rules based on AD group, device type, etc.
- [Screenshot: ISE Policy Set Screen]
Step 6 – Validate Using CLI
On the switch:
show authentication sessions interface gig1/0/1 details debug dot1x all debug radius authentication
Step 7 – Validate Using GUI
- In ISE: Operations > RADIUS > Live Logs → Look for authentication events.
- Click Details → Verify Authentication Result and Authorization Profile.
- [Screenshot: ISE Live Logs]
FAQs
1. How can I verify if 802.1X authentication succeeded on the switch?
Run:
show authentication sessions interface Gi1/0/1 details
Check Status: Authorized and Method: dot1x. If it says mab instead of dot1x, the endpoint failed EAP and fell back to MAB.
2. Why is my endpoint stuck at “Requesting Identity” during authentication?
This usually means:
- Supplicant is disabled on the endpoint.
- Wrong EAP type selected (e.g., ISE policy expects PEAP, endpoint using TLS).
- Bad cable or port configuration (trunk instead of access mode).
3. Can I run both MAB and 802.1X on the same port?
Yes. Configure:
authentication order mab dot1x authentication priority dot1x mab
This allows non-802.1X devices to connect using MAB fallback without blocking 802.1X-capable devices.
4. How do I test 802.1X without a physical switch?
Use EVE-NG or GNS3 with CSR1000v or C9300v images that support 802.1X commands. Connect them to virtual Windows/Linux endpoints with a supplicant enabled.
5. Why does authentication fail after joining ISE to Active Directory?
Common causes:
- Wrong AD group mapping in ISE authorization policy.
- Identity source sequence not including AD.
- ISE node not time-synced with AD (check NTP).
6. How can I see the actual EAP conversation for troubleshooting?
On the switch:
debug dot1x all debug radius authentication
On ISE: Operations > RADIUS > Live Logs → Select a failed attempt → View Steps tab for EAP stages.
7. What’s the difference between EAP-PEAP and EAP-TLS in ISE?
- EAP-PEAP: Username/password-based authentication; easier to deploy but less secure.
- EAP-TLS: Certificate-based authentication; stronger security but requires PKI infrastructure.
8. What happens if a device doesn’t support 802.1X?
The port will move to MAB authentication if configured. You can assign such devices to a guest VLAN or a restricted VLAN via ISE authorization profiles.
9. Can I force re-authentication for testing policy changes?
Yes.
clear authentication sessions interface Gi1/0/1
This triggers the device to go through the 802.1X process again and hit your updated ISE policies.
10. How do I simulate authentication failure to check fallback policies?
- Enter wrong credentials in the supplicant.
- Disable the supplicant on the endpoint.
- Temporarily unmap the endpoint’s MAC in ISE to force policy rejection.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Understanding the 802.1X authentication flow is essential before deploying ISE in production.
It ensures smooth rollout, faster troubleshooting, and secure access for legitimate users.
Fast-Track to Cisco ISE Mastery Pro
Take your Cisco ISE skills from basic configs to expert-level mastery!
I run a focused 4-month, instructor-led CCIE Security Mastery Program — covering ISE, Firepower, VPNs, and full enterprise NAC deployment.
- Get the complete course outline here: https://course.networkjourney.com/ccie-security/
- Join now and build hands-on lab skills with structured guidance, real lab topologies, and direct Q&A access to the instructor. Limited seats — secure your spot today!
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 16] Cisco ISE Mastery Training: Understanding 802.1X Authentication Flow](https://networkjourney.com/wp-content/uploads/2025/08/Day-16-–-Cisco-ISE-Mastery-Training-Understanding-802.1X-Authentication-Flow.png)

![Mobility Groups & Roaming – Seamless Wireless in Action [CCNP Enterprise]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/07/Mobility-Groups-Roaming-–-Seamless-Wireless-in-Action-CCNP-Enterprise.png)
