[Day 19] Cisco ISE Mastery Training: Creating Authentication Policies for Wired Access
Table of Contents
Introduction
In any enterprise network, securing wired access is just as important as wireless. Cisco ISE enables centralized control over which devices and users can access the network, enforcing identity-based authentication before granting connectivity.
Today, we’ll deep dive into creating authentication policies for wired access, focusing on real-world lab practice, GUI & CLI validation, and step-by-step learning that you can replicate in your own ISE lab.
By the end of this, you’ll not only know how to configure ISE for wired authentication but also how to validate it from both switch CLI and ISE’s live logs.
Problem Statement
Most enterprise networks face these wired access security challenges:
- Unauthorized devices plugging into open Ethernet ports.
- Lack of identity awareness — the network can’t distinguish between an employee laptop, an IP phone, or a rogue device.
- No centralized policy enforcement — security policies vary by location or switch.
- Compliance failures — regulations like ISO 27001, PCI DSS, or HIPAA require device/user authentication.
Without proper authentication policies, a malicious insider or an unauthorized guest can gain unrestricted access to sensitive resources.
Solution Overview
Cisco ISE solves this problem through Authentication Policies, which define:
- WHO can connect (user/device identity).
- HOW they authenticate (802.1X, MAB, WebAuth).
- WHAT credentials are checked against (AD, Internal ISE DB, Certificate).
For wired access:
- Switch ports act as 802.1X authenticators.
- ISE acts as the authentication server (RADIUS).
- Endpoints (supplicants) present credentials before getting network access.
This approach ensures identity-based network access and aligns with Zero Trust principles.
Sample Lab Topology
Lab Environment:
- Virtualization: EVE-NG or VMware Workstation.
- Cisco ISE: v3.x deployed as a VM.
- Switch: Cisco Catalyst 9300/3750/2960 image in EVE-NG or physical lab.
- Endpoints: Windows 10/11 VM with 802.1X supplicant enabled.
- Active Directory: Windows Server 2019 (optional for external identity source).
Topology Description:
- ISE connected to the management VLAN.
- Switch connected to ISE (RADIUS configured).
- Endpoint connected to access port on switch.
- Optional AD server connected to ISE for user authentication.
Diagram (Description):
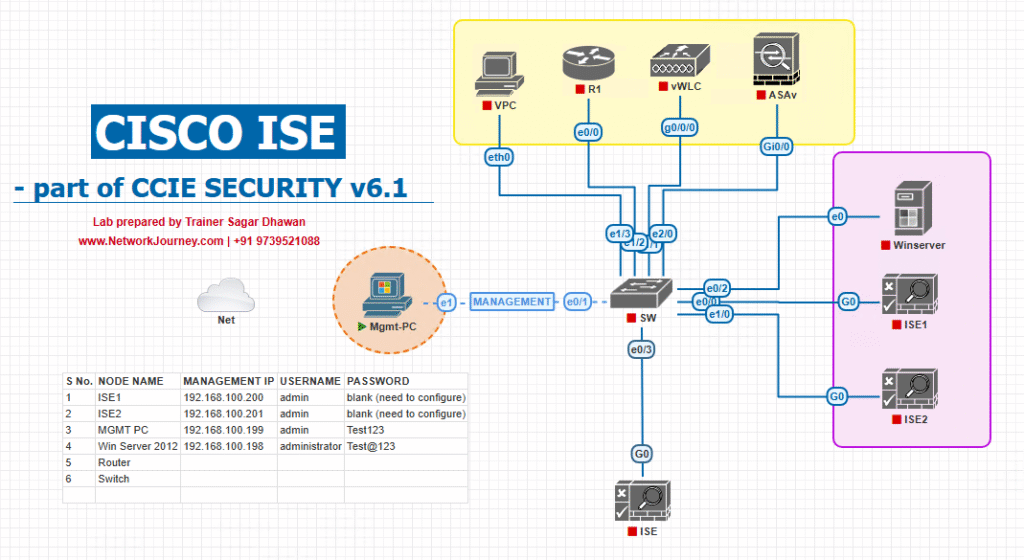
Step-by-Step GUI Configuration Guide
Step 1: Add Switch as Network Device in ISE
- Log in to Cisco ISE Admin GUI.
- Navigate to Administration > Network Resources > Network Devices.
- Click Add.
- Enter:
- Name:
SW1 - IP:
192.168.10.2
- Name:
- Under Authentication Settings, check RADIUS Authentication Settings and set the Shared Secret (must match switch).
- Save.
- [Screenshot: Add Network Device Screen]
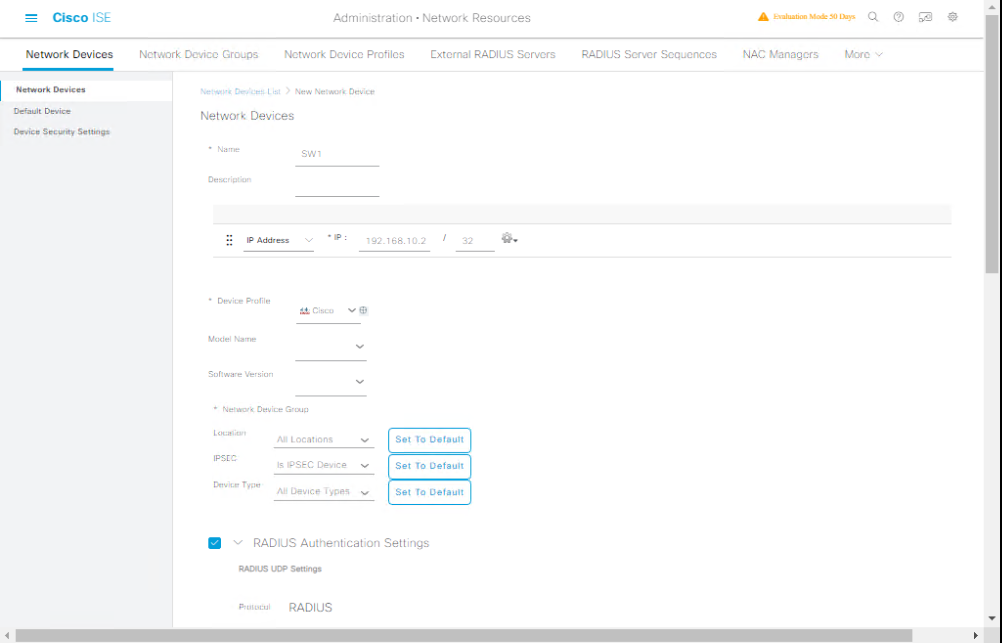
Step 2: Configure Authentication Policy in ISE
- Navigate to Policy > Policy Sets.
- Create a new Policy Set named “Wired Access”.
- In the Authentication Policy:
- Rule 1: Condition = Wired_802.1X, Identity Source = Active Directory.
- Rule 2: Condition = Wired_MAB, Identity Source = Internal Endpoints.
- Default = Deny Access.
- [Screenshot: ISE Authentication Policy Screen]
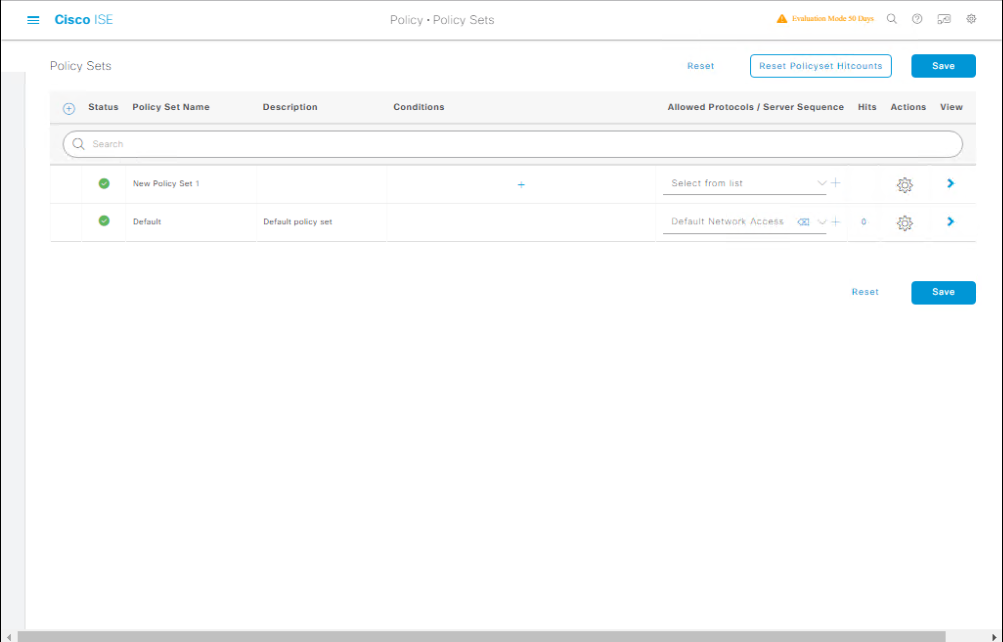
Step 3: Configure Switch for 802.1X + MAB
On switch CLI:
! Enable AAA conf t aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius ! RADIUS configuration radius-server host 192.168.10.10 auth-port 1812 acct-port 1813 key Cisco123 ! Enable 802.1X globally dot1x system-auth-control ! Interface-level configuration interface GigabitEthernet0/1 switchport mode access authentication port-control auto mab dot1x pae authenticator spanning-tree portfast
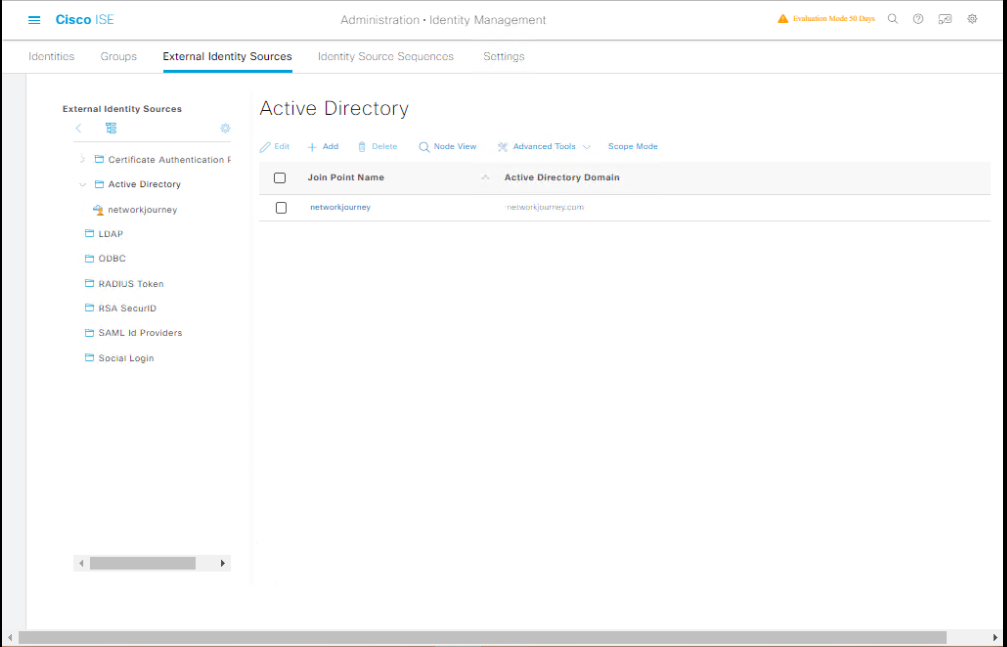
Step 4: Bind Policy to AD (Optional)
- Navigate to Administration > Identity Management > External Identity Sources > Active Directory.
- Join the ISE node to AD.
- [Screenshot: ISE AD Join Screen]
Step 5: Test & Validate
On Endpoint:
- Ensure 802.1X supplicant is enabled (Windows:
Control Panel > Network > Ethernet > Authenticationtab).
On Switch CLI:
show authentication sessions interface gi0/1 details
Expected:
Status: Authorized Method: dot1x Domain: DATA Username: user1@domain.com
In ISE GUI:
- Navigate to Operations > RADIUS > Live Logs.
- Check the latest authentication attempt with “Access-Accept” status.
- [Screenshot: ISE Live Logs Success]
FAQs – Wired Authentication Policies in Cisco ISE
1. Q: What’s the difference between wired 802.1X and wireless 802.1X in ISE?
A: Both use the same EAP authentication methods and ISE policies, but in wired 802.1X, the switch acts as the authenticator instead of a wireless controller. Wired setups usually involve more port-level configurations and deal with endpoints like PCs, IP phones, and printers.
2. Q: Do I need certificates for wired 802.1X authentication?
A: Not strictly. You can use PEAP/MSCHAPv2 with username/password, but EAP-TLS (certificate-based) is more secure and preferred in production because it removes password-based attacks.
3. Q: Can I run both 802.1X and MAB on the same port?
A: Yes. This is called multi-auth or 802.1X with MAB fallback. 802.1X is tried first, and if the device doesn’t respond, MAB is used as a backup (often for printers, phones, IoT devices).
4. Q: What happens if Cisco ISE is unavailable during authentication?
A: You can configure Critical Auth VLAN (a fail-open VLAN) or enable “low-impact mode” to keep essential connectivity. Without it, endpoints may lose access entirely when ISE is down.
5. Q: How can I differentiate between an IP phone and a laptop on the same port?
A: Use ISE’s profiling feature to identify device types automatically, or match MAC OUI patterns in your policy. You can also use voice VLAN + data VLAN separation on the switch.
6. Q: How do I verify if wired authentication is working from the switch side?
A: Run:
show authentication sessions interface Gi0/1 details
This will show the username, authentication method (dot1x or mab), and authorization status.
7. Q: Why does my Windows endpoint not prompt for login when connected?
A: The Windows 802.1X supplicant might not be enabled. Go to Control Panel > Network and Sharing Center > Ethernet > Properties > Authentication tab and enable IEEE 802.1X.
8. Q: Can I assign VLANs dynamically via ISE for wired devices?
A: Yes. ISE can send RADIUS attributes to the switch specifying VLAN IDs or ACLs per user/device. This enables role-based network segmentation.
9. Q: What are common reasons wired 802.1X authentication fails?
A:
- Incorrect RADIUS shared secret between switch and ISE.
- Supplicant disabled or misconfigured on endpoint.
- Mismatched authentication methods between client and ISE policy.
- AD connectivity issues (if using external identity store).
10. Q: How fast is wired authentication compared to wireless?
A: Wired authentication is usually faster (2–4 seconds) because there’s no RF negotiation. However, MAB fallback can take longer (up to 8–10 seconds) as the switch waits for the 802.1X timeout before trying MAC-based authentication.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Wired authentication policies in Cisco ISE are the backbone of network access control in enterprise environments. By combining 802.1X, MAB fallback, and centralized authentication via ISE, you ensure every device is identified and authorized before getting network access.
The steps we covered are production-ready and validated with both CLI and GUI checks.
Upgrade Your Skills – Start Today
Master Cisco ISE and CCIE Security in 4-Month Instructor-Led Training!
Get hands-on, lab-driven mastery with real-world network security scenarios.
- Next Batch: Seats filling fast!
- Course Outline & Registration: https://course.networkjourney.com/ccie-security/
- Bonus: Lifetime lab access + personal mentorship for your certification & job success.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![[Day 32] Cisco ISE Mastery Training: Configuring Cisco AnyConnect NAM for Wired Auth](https://networkjourney.com/wp-content/uploads/2025/08/Day-32-–-Cisco-ISE-Mastery-Training-Configuring-Cisco-AnyConnect-NAM-for-Wired-Auth.png)
