[Day 23] Cisco ISE Mastery Training: Guest VLAN & Critical VLAN Configuration
Table of Contents
Introduction
In enterprise networks, wired access security using 802.1X or MAB can occasionally fail due to endpoint configuration issues, missing certificates, or network downtime. When authentication fails, what happens to the user or device? Without proper handling, devices may be completely cut off from the network, leading to user frustration and operational disruption.
Cisco ISE’s Guest VLAN and Critical VLAN features ensure that devices that cannot authenticate still receive limited or fallback access to maintain productivity or facilitate troubleshooting.
- Guest VLAN → For endpoints that fail authentication or do not support 802.1X but should still have restricted internet access.
- Critical VLAN → For scenarios where ISE or RADIUS servers are unreachable, ensuring devices still connect to an emergency VLAN.
Mastering these features ensures business continuity while maintaining security posture.
Problem Statement
Without Guest VLAN or Critical VLAN:
- Devices that cannot authenticate are completely blocked.
- Service disruptions occur during ISE outages.
- Network teams face floods of support tickets.
- No controlled way to give temporary network access for guests or unmanaged devices.
Solution Overview
Cisco ISE integrates with switch features to dynamically assign:
- Guest VLAN when an endpoint fails authentication or is unauthenticated.
- Critical VLAN when the RADIUS server (ISE) is unreachable.
These VLANs are pre-configured on access switches and only allow minimal network resources — e.g., internet access, registration portal, or troubleshooting servers.
Sample Lab Topology
Lab Setup (VMware/EVE-NG):
- Cisco ISE (v3.x) running on VMware ESXi.
- Cisco Catalyst Switch (IOS XE) for wired access.
- Test Endpoints:
- Laptop with 802.1X enabled.
- IoT device without supplicant.
- Guest laptop for testing VLAN assignment.
- DHCP Server in Guest VLAN.
- Gateway/Firewall providing internet access for guest users.
Topology Diagram:
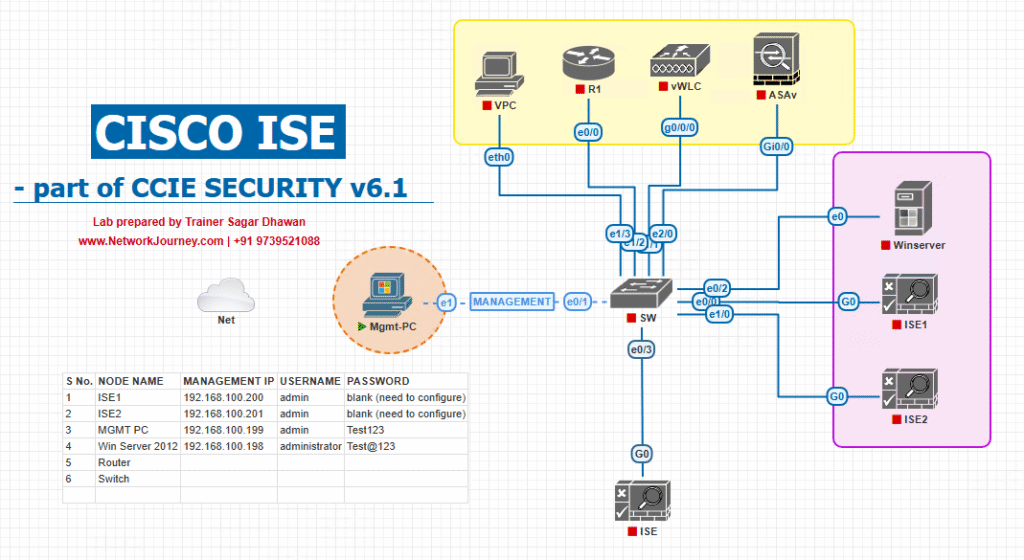
- Port Gi1/0/10 → Test for Guest VLAN.
- Port Gi1/0/11 → Test for Critical VLAN failover.
Step-by-Step GUI & CLI Configuration Guide
Step 1: Create Guest VLAN & Critical VLAN in Switch
Switch(config)# vlan 50 Switch(config-vlan)# name Guest_VLAN Switch(config-vlan)# exit Switch(config)# vlan 99 Switch(config-vlan)# name Critical_VLAN Switch(config-vlan)# exit
Step 2: Configure VLAN Interfaces (for DHCP or Routing)
Switch(config)# interface vlan 50 Switch(config-if)# ip address 192.168.50.1 255.255.255.0 Switch(config-if)# no shutdown Switch(config)# interface vlan 99 Switch(config-if)# ip address 192.168.99.1 255.255.255.0 Switch(config-if)# no shutdown
Step 3: Configure Access Ports for 802.1X + VLAN Fallback
Switch(config)# interface gi1/0/10 Switch(config-if)# switchport mode access Switch(config-if)# authentication port-control auto Switch(config-if)# mab Switch(config-if)# dot1x pae authenticator Switch(config-if)# authentication event fail action authorize vlan 50 Switch(config-if)# authentication event server dead action authorize vlan 99 Switch(config-if)# authentication host-mode single-host Switch(config-if)# spanning-tree portfast Switch(config-if)# exit
Explanation:
authentication event fail action authorize vlan 50→ Assigns Guest VLAN on auth fail.authentication event server dead action authorize vlan 99→ Assigns Critical VLAN if ISE is unreachable.
Step 4: Configure Policy in ISE (GUI)
In Cisco ISE Admin Portal:
- Go to Policy > Policy Sets.
[Screenshot: ISE Policy Sets Page]
- Select the relevant Policy Set or create a new one for Wired Access.
- Under Authentication Policy, define conditions for MAB / 802.1X.
- In Authorization Policy:
- Condition: If user fails authentication → Assign Guest VLAN (Optional, for MAB fallback).
- Condition: If user group = Guest → Assign Guest VLAN.
- Use “Permit Access” with VLAN ID override or return RADIUS attribute
Tunnel-Private-Group-ID=50.
Step 5: Validation – GUI
- Connect endpoint to the port.
- If authentication fails → Check Operations > Live Logs in ISE.
[Screenshot: ISE Live Logs Showing Guest VLAN Assignment]
- Verify VLAN in switch:
Switch# show authentication sessions interface gi1/0/10 detailsYou should seeVLAN: 50for Guest VLAN.
Step 6: Validation – Critical VLAN
- Shut down the ISE NIC or block RADIUS communication.
- Reconnect the endpoint to trigger authentication.
- Verify VLAN assignment:
Switch# show authentication sessions interface gi1/0/11 detailsVLAN should be99.
FAQs
1. Q: What is the exact difference between Guest VLAN and Critical VLAN in Cisco ISE deployments?
A:
- Guest VLAN → Assigned when an endpoint fails authentication (e.g., no supplicant, wrong credentials, unsupported device).
- Critical VLAN → Assigned when the switch cannot reach any configured RADIUS servers (ISE down or unreachable).
Guest VLAN is about authentication result; Critical VLAN is about server reachability.
2. Q: Who decides the VLAN assignment — the switch or ISE?
A:
- Guest VLAN → Can be decided either by the switch (locally) or by ISE (sending VLAN ID in RADIUS attributes).
- Critical VLAN → Always decided by the switch, because it happens when ISE is unreachable.
3. Q: Can I configure both Guest VLAN and Critical VLAN on the same interface?
A:
Yes. The sequence is:
- Try authentication via ISE.
- If authentication fails → Assign Guest VLAN.
- If ISE unreachable → Assign Critical VLAN.
4. Q: What happens if the endpoint is already in Guest VLAN and then ISE becomes unreachable?
A:
If the port reinitializes or MAB/802.1X re-triggers, the switch will detect ISE unreachability and put the device in Critical VLAN instead.
5. Q: Is DHCP mandatory in Guest or Critical VLAN?
A:
Yes, unless your devices have static IPs. Without DHCP, endpoints will join the VLAN but won’t get an IP, rendering the fallback VLAN useless for troubleshooting or internet access.
6. Q: How do I limit access in these VLANs so they don’t become a security hole?
A:
Use ACLs on the switch or firewall to restrict Guest/Critical VLAN traffic to:
- Internet only (Guest VLAN).
- Essential services like DNS/DHCP (Critical VLAN).
Avoid direct access to internal subnets unless absolutely necessary.
7. Q: How do I verify if the switch actually assigned the Guest or Critical VLAN?
A:
Use:
show authentication sessions interface Gi1/0/x details
Look for:
Current Policy VLAN: 50(Guest VLAN)Current Policy VLAN: 99(Critical VLAN)
8. Q: Can I apply different Guest VLANs for different access ports?
A:
Yes. You can:
- Set
authentication event fail action authorize vlan <ID>per interface. - Use ISE policy to send different VLAN IDs based on conditions.
9. Q: What happens in a wireless network — is there a Guest VLAN equivalent?
A:
Wireless networks don’t use the wired Guest/Critical VLAN mechanism. Instead, WLC applies a WebAuth portal or Pre-Auth ACL for guests, and uses SSO fail-open policies for controller/Ise outages.
10. Q: Does Critical VLAN trigger if just one ISE node fails?
A:
No. Critical VLAN triggers only when all configured RADIUS servers in the switch’s list are unreachable. This is why you should always configure multiple ISE PSNs for redundancy.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Guest VLAN and Critical VLAN are safety nets in NAC deployments. Without them, even minor authentication hiccups can cause large outages. Configuring them ensures continuous, controlled access — a must-have for any real-world Cisco ISE deployment.
Upgrade Your Skills – Start Today
Master Cisco ISE & CCIE Security
This guide is just one lesson from the 4-Month Instructor-Led CCIE Security Mastery Program. If you want to go beyond theory and build real-world, job-ready NAC, VPN, and Firewall skills, this course blends deep technical training, hands-on labs, and interview preparation to help you dominate the security engineering job market.
- Secure your seat now → https://course.networkjourney.com/ccie-security/
- Live labs, lifetime recordings, 1-on-1 mentorship, and community access.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 23] Cisco ISE Mastery Training: Guest VLAN & Critical VLAN Configuration](https://networkjourney.com/wp-content/uploads/2025/08/Day-23-Cisco-ISE-Mastery-Training-Guest-VLAN-Critical-VLAN-Configuration.png)
![Mastering Layer 2 Troubleshooting Commands: A Complete Guide with CLI & EVE-NG Labs [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/06/Mastering-Layer-2-Troubleshooting-Commands_networkjourney.png)
![[Day 20] Cisco ISE Mastery Training: Configuring Authorization Profiles](https://networkjourney.com/wp-content/uploads/2025/08/Day-20-Cisco-ISE-Mastery-Training-Configuring-Authorization-Profiles.png)
