[Day 24] Cisco ISE Mastery Training: Implementing Downloadable ACLs (DACLs)
Table of Contents
Introduction – The Power of Downloadable ACLs in Cisco ISE
In modern enterprise networks, security is no longer about simply deciding who gets access — it’s also about controlling what they can do after they get access. This is where Downloadable ACLs (DACLs) in Cisco Identity Services Engine (ISE) step in as a game-changer.
Unlike traditional ACLs, which are manually configured and maintained on every network device (switches, wireless controllers, routers), DACLs allow you to centrally define, store, and dynamically push policy-based ACLs directly from Cisco ISE to the access device at the moment of user or device authentication.
Think of it like this:
- Traditional ACLs = Hardcoded traffic rules on each network device (prone to config drift, hard to scale).
- DACLs = Smart, on-demand rules delivered in real time from a central brain (ISE), based on the user’s identity, posture, and compliance state.
From a network engineer’s perspective, DACLs bring:
- Centralized control – Write the ACL once in ISE and use it anywhere.
- Dynamic enforcement – Apply security based on real-time authentication/authorization results.
- Scalability – No more repetitive CLI configs across hundreds of switches.
- Flexibility – Tailor ACLs per user group, endpoint type, or compliance status.
From a security operations perspective, DACLs are a critical part of Zero Trust Network Access (ZTNA), where every session is evaluated, authorized, and limited to the exact resources needed — nothing more.
In Cisco ISE deployments, DACLs are commonly used for:
- Restricting access for guest users to the internet only.
- Allowing only specific application ports for contractors or vendors.
- Quarantining non-compliant endpoints until they meet security requirements.
- Enforcing micro-segmentation without complex VLAN sprawl.
For learners preparing for CCNP Security, CCIE Security, or real-world NAC deployments, mastering DACLs is non-negotiable — they’re a vital bridge between authentication (who you are) and authorization (what you can do).
Today’s session will go step-by-step, covering:
- Lab topology (how to set up a DACL test environment in VMware/EVE-NG)
- GUI configuration in ISE and network devices
- CLI verification commands to confirm DACLs are working
- Best practices and troubleshooting tips
Problem Statement
In large enterprise networks:
- ACLs are often manually configured per switch or controller.
- Policy changes require touching every device, risking configuration drift.
- Guest, contractor, or BYOD access often requires specific limited permissions — but managing static ACLs becomes a nightmare.
Result?
- Inconsistent policy enforcement
- Slow response to security changes
- Operational overhead for network teams
Solution Overview – How Cisco ISE Solves This with DACLs
Cisco ISE acts as a central policy server. When a user/device authenticates, ISE:
- Matches them to a policy condition (e.g., “Contractor Group”).
- Pushes a Downloadable ACL to the access switch/WLC via RADIUS CoA (Change of Authorization).
- The switch applies the ACL in real time without requiring pre-config on the device.
Advantages:
- Write Once, Use Anywhere – Define the ACL in ISE, not on each device.
- Dynamic & Context-Aware – Based on user identity, device type, posture status, etc.
- Easier Auditing – Policies are centrally visible in ISE.
Sample Lab Topology
Lab Tools: VMware Workstation / EVE-NG
Devices:
- Cisco ISE 3.x (VM)
- Catalyst 9300 Switch (or IOU in EVE-NG)
- Windows 10 Endpoint (wired 802.1X)
- AD Server (for user auth)
- Optional WLC + Wireless Client
Topology Diagram:
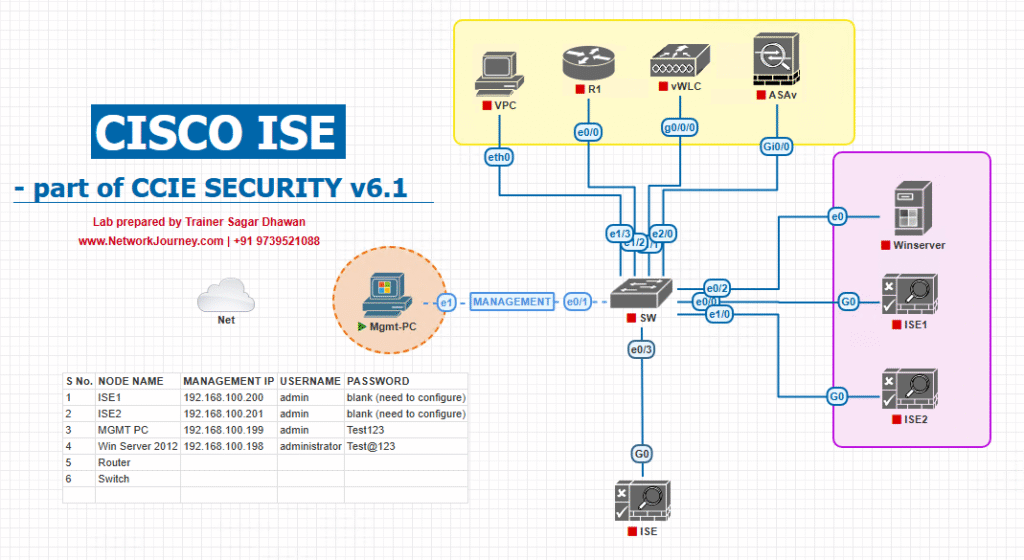
DACL flow:
- User connects to the network.
- Switch authenticates via 802.1X or MAB.
- ISE matches user policy and pushes DACL via RADIUS.
- Switch enforces DACL dynamically.
Step-by-Step GUI & CLI Configuration Guide
Step 1 – Create DACL in Cisco ISE
- Log in to Cisco ISE Admin Portal.
- Go to: Policy → Policy Elements → Results → Authorization → Downloadable ACLs.
- Click Add.
- Name:
DACL_Contractor - ACL Content:
permit tcp any host 10.1.1.100 eq 443 permit tcp any host 10.1.1.100 eq 80 deny ip any any - Save.
[Screenshot: ISE DACL Creation Page]
Step 2 – Create Authorization Policy in ISE
- Go to: Policy → Authorization.
- Add new rule:
- Condition: User Group = Contractor (from AD).
- Result: PermitAccess + Apply DACL: DACL_Contractor.
- Save & Publish.
[Screenshot: ISE Policy Set Screen]
Step 3 – Configure Switch for DACL Support (CLI)
On the Catalyst switch:
conf t aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius radius-server host 10.1.1.20 auth-port 1812 acct-port 1813 key cisco123 ip device tracking dot1x system-auth-control interface Gig1/0/10 switchport mode access authentication port-control auto mab dot1x pae authenticator spanning-tree portfast
Step 4 – Validation (CLI)
After user authentication:
show authentication sessions interface gi1/0/10 details
You should see:
URL Redirect ACL: N/A DACL: DACL_Contractor (downloaded)
Step 5 – Validation (GUI in ISE)
- Go to Operations → RADIUS → Live Logs.
- Select the user session → Details → Authorization Result should show applied DACL.
At this stage, your DACL is active and enforcing policies dynamically.
FAQs
1. What is a Downloadable ACL (DACL) in Cisco ISE?
A DACL is an ACL stored and managed centrally in Cisco ISE instead of on the network device (like a switch or WLC). When a user or device authenticates, ISE dynamically pushes the ACL to the NAD (Network Access Device) over RADIUS CoA, so access rules are applied instantly without manually configuring them on each switch or WLC.
2. How is a DACL different from a static ACL on a switch?
- Static ACL: Manually created on each device; changes require device-by-device updates.
- DACL: Created once in ISE; pushed automatically during authentication; instantly updates across the network without touching NAD configurations.
3. Which network devices support DACLs?
Most Cisco switches (Catalyst 2960, 3650, 3850, 9000 series), Cisco Wireless LAN Controllers (AireOS, Catalyst 9800), and ASA/FTD support DACLs. You must confirm the device runs an IOS version that supports ISE integration and DACL download via RADIUS.
4. How does ISE deliver a DACL to a switch or WLC?
When a session matches an authorization policy in ISE that includes a DACL, ISE sends a RADIUS Access-Accept message with a Cisco VSA (Vendor Specific Attribute) containing the ACL name and content. The NAD applies it instantly.
5. Can DACLs be used with both Wired and Wireless clients?
Yes. DACLs work for wired 802.1X/MAB sessions on switches and for wireless 802.1X/MAB sessions on WLCs. The configuration process in ISE is the same, but NAD-specific compatibility must be checked.
6. What happens if the NAD cannot apply the DACL?
If the NAD does not support DACLs or the ACL syntax is incompatible with its IOS/WLC code, the session may default to the Critical VLAN, deny access, or allow limited access depending on your fallback configuration.
7. Can I combine DACLs with VLAN assignments in the same authorization policy?
Yes. You can push both a VLAN and a DACL in the same authorization profile. The VLAN will segment the client into a specific network, and the DACL will further restrict what traffic it can send/receive.
8. How do I verify if a DACL is applied successfully?
- On the NAD CLI:
show ip access-lists show authentication sessions interface Gi1/0/10 detailsLook for the ACL name and applied rules. - On ISE GUI: Check Live Logs → Authorization Details → DACL download status.
9. How are DACL changes applied to active sessions?
If you modify a DACL in ISE, the change will not take effect automatically for existing sessions. You must trigger a CoA (Change of Authorization) to re-download the updated ACL.
10. Are there limitations or best practices for DACL usage?
- Avoid overly large DACLs — they increase download and processing time.
- Test syntax carefully; an unsupported ACE will cause the NAD to reject the entire DACL.
- Use descriptive DACL names (e.g.,
DACL-Wired-Printer) for clarity. - Always validate both from ISE Live Logs and NAD CLI to ensure successful deployment.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Mastering Downloadable ACLs means mastering dynamic, identity-based access control. With ISE, you can move away from static, hard-to-maintain ACLs and embrace a scalable, centralized policy model.
Upgrade Your Skills – Start Today
If you want to master Cisco ISE, Firepower, ASA, VPNs, and advanced security concepts from zero to CCIE Security level, join my 4-month Instructor-Led Training Program conducted by Sagar Dhawan — the trainer behind Network Journey.
- Duration: 4 Months – Live Online Classes
- Course Outline: https://course.networkjourney.com/ccie-security/
- Who Should Join: Network Engineers, Security Professionals, CCNP/CCIE aspirants, SOC/NOC engineers
Why Join:
- Learn with real-world labs in VMware/EVE-NG
- Hands-on configuration + troubleshooting skills
- Direct mentorship & career guidance from a CCIE Security expert
Spots are limited — Secure your seat today and take your NAC & network security skills to the next level.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088


![[Day 40] Cisco ISE Mastery Training: End-to-End Wired Authentication Lab Validation](https://networkjourney.com/wp-content/uploads/2025/08/Day-40-Cisco-ISE-Mastery-Training-End-to-End-Wired-Authentication-Lab-Validation.png)
![[Day 43] Cisco ISE Mastery Training: Wireless MAB Authentication](https://networkjourney.com/wp-content/uploads/2025/08/Day-43-Cisco-ISE-Mastery-Training-Wireless-MAB-Authentication.png)