[Day #27 Pyats Series] Syslog server configuration validation using pyATS for Cisco [Python for Network Engineer]
Table of Contents
Introduction on the Key Points
Welcome to Day #27 of the “101 Days of pyATS (Vendor-Agnostic)” series! Today, we tackle a crucial and often overlooked part of network observability—Syslog server configuration validation.
When managing modern enterprise networks, ensuring that devices are correctly logging events to a centralized syslog server is critical. Missing even a single log from a router or switch could mean the difference between identifying an attack in time—or missing it altogether.
In this article, you’ll learn how to:
- Verify syslog server configurations across Cisco IOS, IOS-XE, NX-OS, and even Arista or FortiGate
- Use pyATS + Genie parsers to extract structured data
- Automatically detect missing or misconfigured syslog servers
- Perform these checks across 10s or 100s of devices
This is a practical use case of Python for Network Engineer roles, where we combine automation with compliance and security audit requirements.
Topology Overview
Below is a sample topology used for this validation:
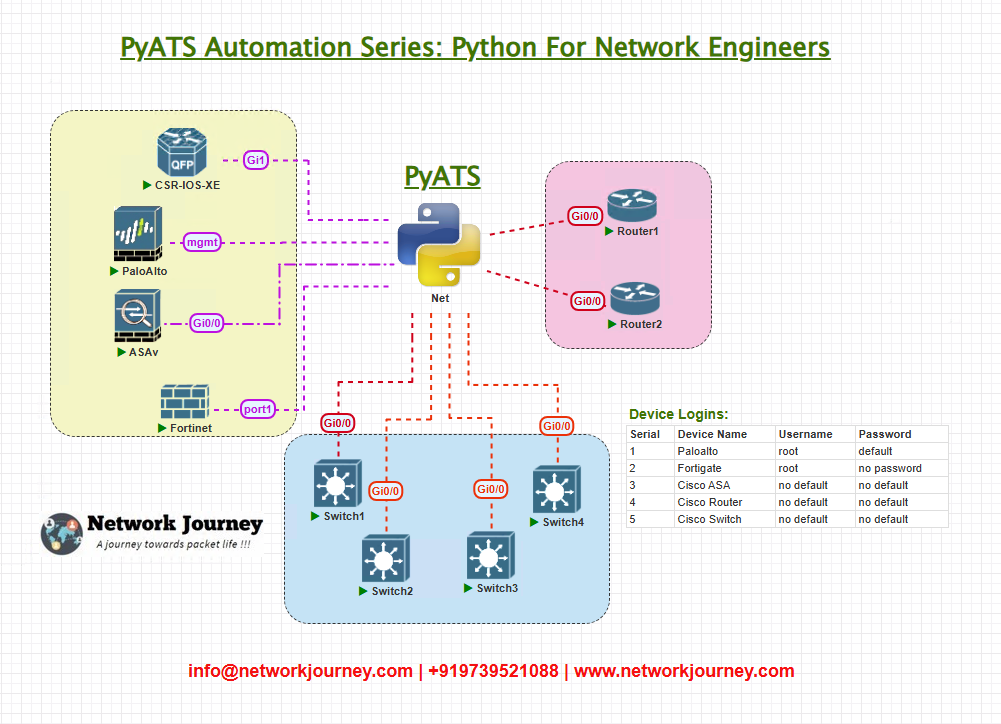
All devices are expected to send logs to the Syslog server at 192.168.100.10, and your job as a network automation engineer is to ensure that this configuration is present and correct.
Topology & Communications
Let’s define our goals:
- Devices are reachable via SSH
- Devices must be configured to send logs to a specific syslog server
- Validate the following:
- Syslog server IP exists in the configuration
- Logging is enabled
- Logging level (optional check)
- Transport protocol (UDP/TCP)
- Hostname logging is enabled (optional)
We’ll use pyATS to:
- Connect to each device
- Parse the relevant command (like
show running-config | include loggingorshow logging) - Normalize and validate
Workflow Script
Here’s a complete, reusable pyATS script that checks for the configured syslog server across devices.
#!/usr/bin/env python3
from genie.testbed import load
from rich import print
from datetime import datetime
EXPECTED_SYSLOG_SERVER = "192.168.100.10"
def check_syslog_config(device):
print(f"[bold cyan] Checking Syslog config on {device.name}[/bold cyan]")
try:
device.connect(log_stdout=False)
output = device.execute("show running-config | include logging")
if EXPECTED_SYSLOG_SERVER in output:
print(f"
[green] {device.name} has correct syslog server configured[/green]
") return { "device": device.name, "syslog_configured": True, "output": output } else: print(f"
[red] {device.name} does NOT have syslog server configured[/red]
") return { "device": device.name, "syslog_configured": False, "output": output } except Exception as e: print(f"
[yellow] Error checking syslog on {device.name}: {e}[/yellow]
") return { "device": device.name, "syslog_configured": "Error", "output": str(e) } def main(): testbed = load("testbed.yml") results = [] for dev_name in testbed.devices: device = testbed.devices[dev_name] result = check_syslog_config(device) results.append(result) print("\n[bold underline] Final Syslog Validation Report:[/bold underline]") for res in results: print(res) if __name__ == "__main__": print(f"[bold blue] pyATS Syslog Validator - {datetime.now()}[/bold blue]") main()
Explanation by Line
| Code Snippet | Description |
|---|---|
EXPECTED_SYSLOG_SERVER = "192.168.100.10" | Define the IP of the syslog server to check |
| `device.execute(“show running-config | include logging”)` |
if EXPECTED_SYSLOG_SERVER in output | Core logic to verify configuration |
device.connect() | Establish SSH session for config collection |
results.append(result) | Store device-wise result for reporting |
You can extend this script to include logging severity levels or check for additional syslog servers if needed.
testbed.yml Example
devices:
R1:
os: iosxe
type: router
connections:
cli:
protocol: ssh
ip: 192.168.1.1
SW1:
os: nxos
type: switch
connections:
cli:
protocol: ssh
ip: 192.168.1.2
AR1:
os: eos
type: switch
connections:
cli:
protocol: ssh
ip: 192.168.1.3
Make sure that the os field is correctly defined so that pyATS can load the correct behavior for Genie parsing or command execution.
Post-validation CLI Screenshots (Real Expected Output)
Cisco IOS – show run | i logging:
logging 192.168.100.10 logging trap informational
NX-OS – show running-config | include logging:
logging server 192.168.100.10 6 use-vrf management
Arista EOS – show running-config | section logging:
logging host 192.168.100.10 logging trap debugging
Your script will search these lines for the expected syslog IP and optionally validate logging level.
FAQs
1: What is a Syslog server, and why is it important in network infrastructure?
A Syslog server is a centralized logging server that receives, stores, and analyzes log messages from network devices. Its importance lies in
- Centralized monitoring of device events and issues.
- Security auditing by recording unauthorized access attempts.
- Troubleshooting network outages or misconfigurations.
- Compliance with industry regulations like PCI-DSS, HIPAA, etc.
Validating that all devices are correctly configured to send logs to the syslog server is crucial for operational and security visibility.
2: How can we validate syslog server configuration using pyATS?
pyATS enables automated validation by
- Connecting to each device in the inventory.
- Parsing device-specific commands like
show logging(Cisco) orshow syslog(Arista). - Checking if the configured syslog server IP, severity level, transport (UDP/TCP), and port are correct.
- Verifying if logging is enabled and active.
- Reporting misconfigurations or missing entries.
You can also automate this as part of your daily CI/CD validation pipeline.
3: What CLI commands are used to check syslog configuration on different vendors?
| Vendor | Command(s) |
|---|---|
| Cisco IOS/XE | `show running-config |
| Cisco NX-OS | show logging server |
| Arista EOS | show logging |
| Palo Alto | show logging-statusshow log system |
| Fortinet | `show full-configuration |
These commands can be parsed using genie parsers, custom regex, or native CLI outputs in pyATS.
4: What are common misconfigurations found in syslog settings?
Some commonly observed misconfigurations include
- Incorrect or unreachable syslog server IP.
- Wrong severity level (e.g., too high, missing critical logs).
- Misconfigured transport protocol (UDP/TCP).
- Logging disabled on interfaces.
- ACL blocking syslog traffic.
- No timestamp or hostname in syslog messages.
These can silently break logging unless validated proactively.
5: Can pyATS detect if the syslog server is not receiving logs even if it is configured correctly on the device?
Not directly. pyATS validates the device configuration, but not actual log delivery to the server. However, you can:
- Use ping tests or TCP port checks to verify syslog server reachability.
- Cross-reference device clock and last log timestamp.
- Combine pyATS with external tools (like
rsyslog, ELK, or a syslog collector) to validate end-to-end log delivery. - Add SNMP traps or script-based probes for deeper testing.
6: How can we ensure all devices in a multi-vendor network are sending logs to the same centralized syslog server?
With pyATS, you can:
- Loop through devices in the testbed file.
- Parse config/logging output from each.
- Normalize and extract configured syslog server IPs.
- Compare against the expected IP.
- Flag devices not pointing to the central logging server.
You can also verify if logging host <ip> or similar lines are missing or pointing to wrong IPs.
7: What severity levels should be configured for syslog on network devices?
Syslog messages are classified from severity 0 (emergencies) to 7 (debug):
| Level | Severity | Use Case |
|---|---|---|
| 0 | Emergency | System is unusable |
| 1 | Alert | Immediate action required |
| 2 | Critical | Critical condition |
| 3 | Error | Error condition |
| 4 | Warning | Warning condition |
| 5 | Notice | Normal but significant condition |
| 6 | Informational | Informational messages |
| 7 | Debug | Debug-level messages |
Typically, severity level 6 or lower is used in production. You can use pyATS to ensure proper severity thresholds are configured.
8: How often should syslog configuration validation be performed using automation like pyATS?
- Weekly or Bi-weekly checks are ideal for stable networks.
- Run pyATS validation after every major change or rollout.
- Integrate into CI/CD pipelines for new devices or config pushes.
- Combine with daily drift-check scripts to detect unauthorized changes.
This ensures ongoing syslog reliability and helps in compliance and audit-readiness.
YouTube Link
Watch the Complete Python for Network Engineer: Syslog server configuration validation using pyATS for Cisco [Python for Network Engineer] Lab Demo & Explanation on our channel:
Join Our Training
Are you ready to scale your career as a Python for Network Engineer?
Trainer Sagar Dhawan, a Cisco-certified expert with 14+ years of hands-on industry experience, is now leading a 3-month instructor-led training that transforms CLI engineers into full-fledged automation engineers.
Course Highlights:
- Python for Network Engineers
- Ansible Playbooks
- pyATS + Genie Automation
- Cisco DevNet APIs
- Real-world projects on EVE-NG
- Multi-vendor use cases (Cisco, Arista, FortiGate)
Learn More and Enroll Here:
https://course.networkjourney.com/python-ansible-api-cisco-devnet-for-network-engineers/
Whether you’re just starting with automation or already working in DevNet, this program will equip you with end-to-end skills for real-world production networks.
Don’t miss the next batch and join the elite group of automation-first network engineers who are fluent in Python for Network Engineer jobs!
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day #27 Pyats Series] Syslog server configuration validation using pyATS for Cisco [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/08/Syslog-server-configuration-validation-using-pyATS-for-Cisco.png)
![Don’t Let Your Router Crash! Master Control Plane Policing (CoPP) with Labs & CLI [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-CoPP.jpg)
![Security Zones Explained: From Flat Networks to Fortresses [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-security-zone.jpg)
![Ansible Playbook for VLAN Configuration – Automate Smarter, Not Harder! [CCNP ENTERPRISE]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/07/Ansible-Playbook-for-VLAN-Configuration-–-Automate-Smarter-Not-Harder-1.png)