[Day 31] Cisco ISE Mastery Training: Wired Posture Assessment Overview
Table of Contents
Introduction
Wired networks have historically been perceived as more secure than wireless due to their physical nature — you have to “plug in” to access them. However, this illusion of safety has been shattered by insider threats, rogue devices, and BYOD culture. Cisco Identity Services Engine (ISE) Posture Assessment bridges this security gap by continuously validating that any device connecting to your wired LAN meets your compliance and security policy standards before granting or maintaining network access.
In this deep-dive, we’ll walk through how Wired Posture Assessment works in ISE, the end-to-end lab setup, step-by-step GUI & CLI configuration, and verification techniques to ensure your setup is bulletproof. This isn’t just about turning on a feature — it’s about integrating security, usability, and visibility in your wired network with zero guesswork.
Problem Statement
Without posture assessment, a wired network port can’t distinguish between:
- A corporate-owned laptop with updated antivirus & encryption enabled.
- An infected machine with disabled firewall.
- A rogue laptop without any corporate controls.
Traditional 802.1X authentication only checks who is connecting, not what state the device is in. This gap allows vulnerable endpoints to become a threat vector — even if they pass basic authentication.
The problem: How do we ensure devices meet compliance before granting network access in a wired LAN environment?
Solution Overview
Cisco ISE’s Posture Assessment uses the Cisco AnyConnect Secure Mobility Client (with Posture module) to evaluate endpoint compliance dynamically. It checks for:
- Antivirus installed & running
- Windows/Mac security patches
- Disk encryption status
- Firewall status
- Custom corporate security rules
If an endpoint fails, ISE can quarantine it to a remediation VLAN or redirect to a captive portal until it passes.
With continuous posture, the device is re-checked periodically — meaning security is maintained beyond initial login.
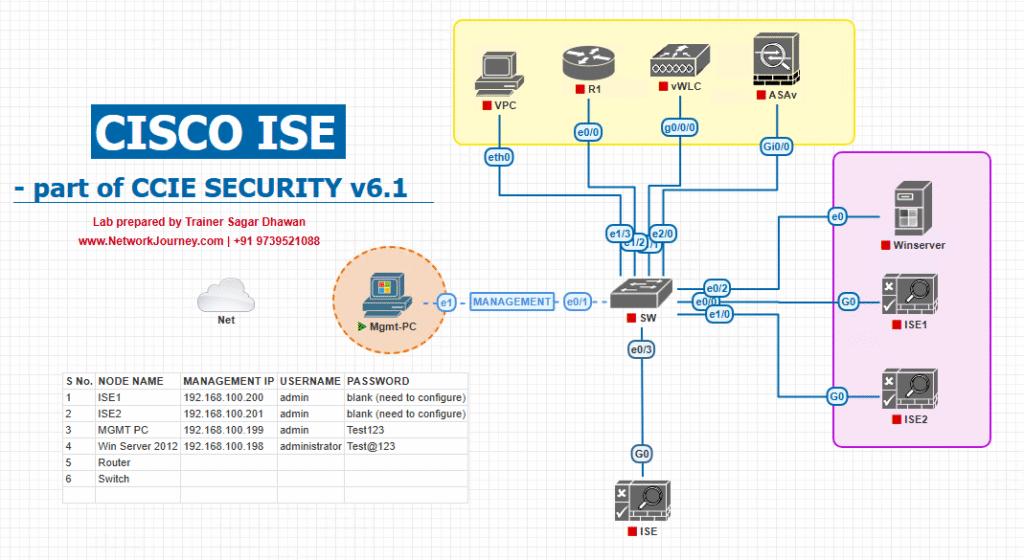
Sample Lab Topology
Lab Components:
- Cisco ISE: v3.x running on VMware Workstation / EVE-NG.
- Cisco Catalyst Switch: 9300 (real or emulated in EVE-NG) acting as access switch.
- Windows 10 Endpoint: With Cisco AnyConnect + Posture module installed.
- AD Server: For user authentication.
- Remediation Server: Optional, hosting compliance files.
Flow:
- User connects laptop to switch access port.
- Switch sends authentication request to ISE via 802.1X/MAB.
- ISE triggers posture check via AnyConnect.
- Compliant → Production VLAN. Non-compliant → Remediation VLAN.
Topology Diagram :
Step-by-Step GUI & CLI Configuration Guide
Step 1 – Install AnyConnect Posture Module
- On the endpoint, install Cisco AnyConnect Secure Mobility Client with Posture enabled.
- Verify installation under Control Panel → Programs and Features.
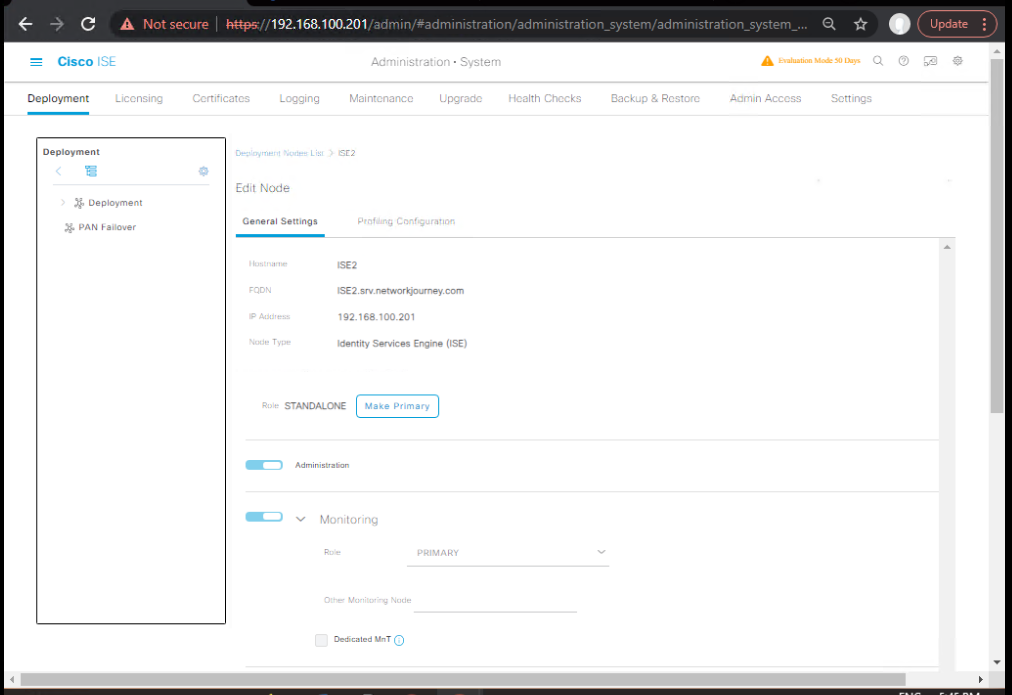
Step 2 – Enable Posture Service in ISE
GUI:
- Navigate to Administration → System → Deployment.
- Edit the ISE Policy Service Node (PSN).
- Under Services, enable Posture.
- Save & restart application services.
- [Screenshot: ISE Deployment Services Screen]
CLI Validation:
ise/admin# show application status ise # Ensure "Posture" service is running
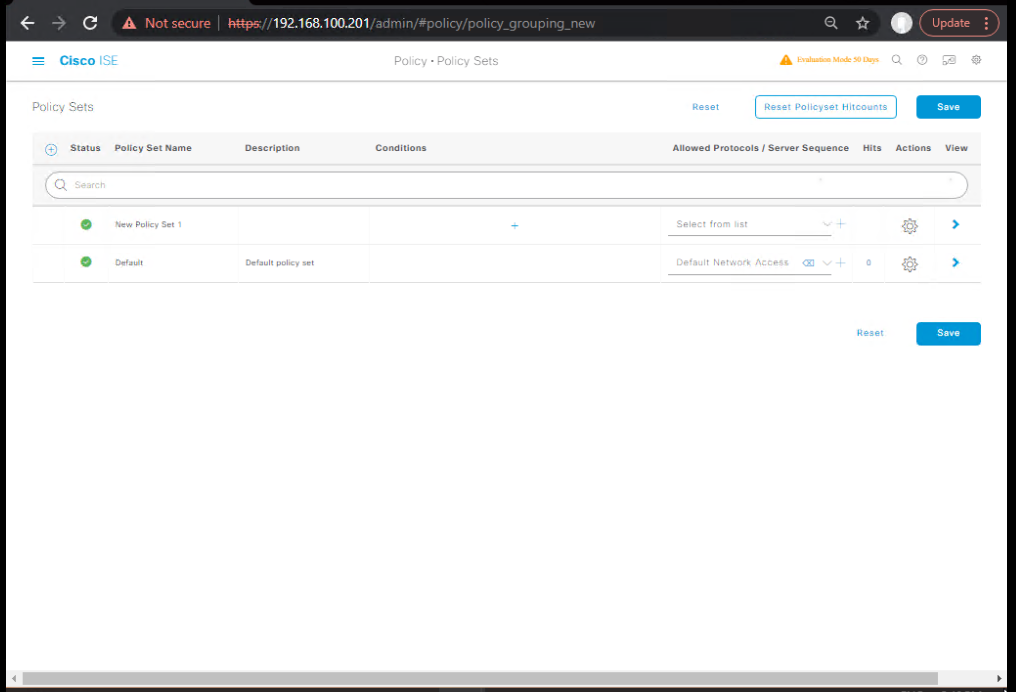
Step 3 – Create Posture Policy
GUI:
- Go to Policy → Policy Sets → [Your Policy Set].
- Add Posture conditions in Authorization Policy:
- IF User Authenticated & Posture = Compliant → VLAN 10 (Production)
- IF Posture = Non-Compliant → VLAN 20 (Remediation)
- Save.
- [Screenshot: Authorization Policy Screen]
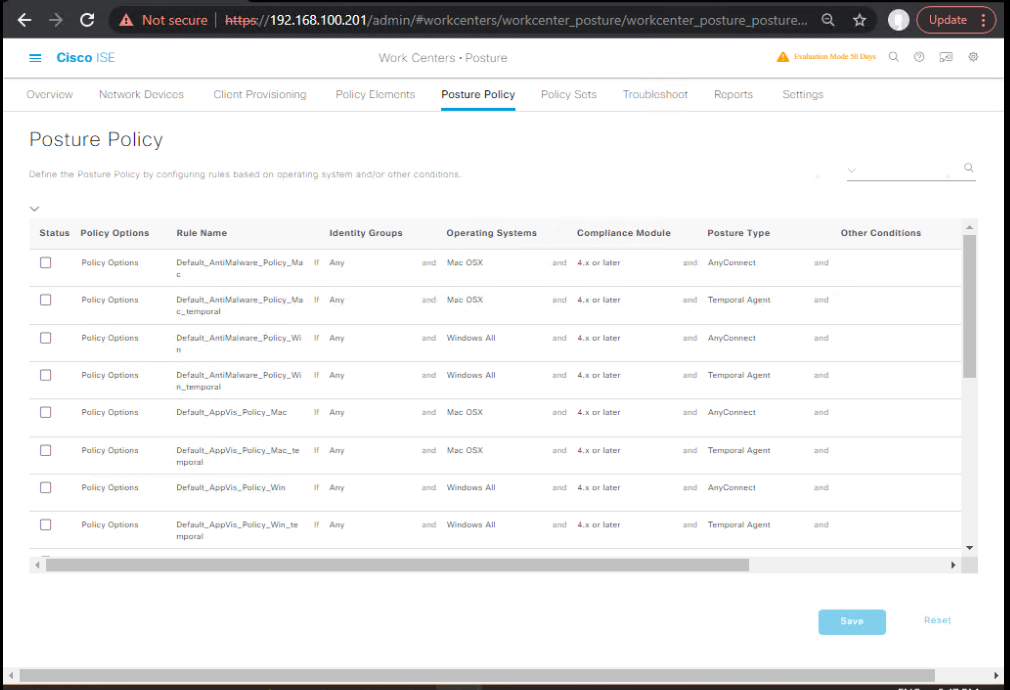
Step 4 – Configure Posture Requirements
GUI:
- Work Centers → Posture → Posture Policy.
- Add conditions:
- AV must be installed and up to date.
- Firewall must be enabled.
- OS must have latest patches.
- Assign these to your Posture Policy.
- [Screenshot: Posture Conditions Screen]
Step 5 – Configure Switch for Posture
CLI:
conf t interface Gi1/0/10 switchport mode access authentication order dot1x mab authentication priority dot1x mab authentication port-control auto mab dot1x pae authenticator spanning-tree portfast
Verify CoA (Change of Authorization) is enabled:
aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius radius-server host <ISE_IP> auth-port 1812 acct-port 1813 key <KEY>
Step 6 – Test & Validate
GUI Validation:
- In ISE: Operations → Live Logs → check endpoint posture state.
- Status should show Compliant or Non-Compliant.
CLI Validation on Switch:
show authentication sessions interface Gi1/0/10 details # Look for "Posture status: Compliant"
FAQs
1. Do I need 802.1X for Wired Posture Assessment, or can it work with MAB?
Answer:
Posture can work with both 802.1X and MAB. However:
- 802.1X provides the highest security by authenticating the user/machine before network access.
- MAB (MAC Authentication Bypass) is useful for endpoints that can’t run 802.1X but are posture-capable (e.g., some corporate PCs without certs).
If you choose MAB, you lose the per-user authentication granularity.
2. Why is Cisco AnyConnect Posture Module mandatory for wired posture?
Answer:
The posture process relies on the Cisco AnyConnect Posture Agent to collect endpoint health data (AV status, patches, firewall, etc.) and report back to ISE. Without it, ISE cannot evaluate compliance. Installing only the core AnyConnect VPN client will not work — you must include the Posture module during installation.
3. How does posture assessment actually work in the background?
Answer:
- User connects to wired port.
- Switch authenticates the user with ISE (802.1X/MAB).
- ISE sends posture requirements to AnyConnect agent.
- Agent scans the endpoint’s security posture.
- Results sent back to ISE.
- If compliant → Production VLAN; if non-compliant → Remediation VLAN or portal.
With continuous posture, this cycle repeats periodically while the session is active.
4. How does ISE enforce remediation if a device fails posture?
Answer:
ISE triggers a Change of Authorization (CoA) to the switch, forcing it to reassign the endpoint to a remediation VLAN or redirect it to a web portal. In remediation mode, the device only has access to patch servers, AV update servers, or IT tools until it meets compliance.
5. What are the common posture conditions engineers configure?
Answer:
- Antivirus installed, running, and up-to-date
- Host-based firewall enabled
- OS patches within a defined age limit
- Disk encryption (BitLocker/FileVault) enabled
- No prohibited processes or applications running
- Registry key or file existence for custom compliance checks
6. How do I verify posture status from the ISE GUI?
Answer:
Go to Operations → RADIUS → Live Logs and locate the session. The Posture Status column will show:
Compliant– passes all checks.Non-Compliant– fails at least one condition.Unknown– posture check not started or failed to run.
7. How do I check posture status from the switch CLI?
Answer:
Use:
show authentication sessions interface Gi1/0/x details
Look for:
- Posture status: Compliant / Non-Compliant / Unknown
- VLAN assignment: Correct VLAN after CoA
- Agent state: Reporting or not reporting
8. Can posture be used for Linux or non-PC devices?
Answer:
Linux support is extremely limited — Cisco Posture is primarily designed for Windows and macOS. Printers, IP phones, and IoT devices generally cannot run AnyConnect Posture, so they must be exempted or handled via profiling policies instead of posture.
9. What are common troubleshooting steps when posture fails?
Answer:
- On the endpoint: Check AnyConnect logs (Posture module tab).
- On ISE: Check Live Logs for posture results.
- On switch:
debug radiusandshow authentication sessions. - Verify CoA is functioning (
debug radius coa). - Ensure the endpoint can reach ISE over TCP 8905 (Posture communication).
10. What is the difference between initial posture check and continuous posture?
Answer:
- Initial posture: Runs only at the start of the session. Once compliant, no further checks unless re-authentication happens.
- Continuous posture: Reassesses device compliance periodically or on trigger events (e.g., AV status change). This is essential for long-lived wired connections in offices where devices may drift out of compliance over time.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
7. Closing Notes
Key Takeaways:
- Wired networks are not inherently safe — posture is essential for compliance enforcement.
- Cisco ISE posture works seamlessly with 802.1X and MAB.
- GUI + CLI validation ensures troubleshooting is straightforward.
Fast-Track to Cisco ISE Mastery Pro
If you want to master Cisco ISE from beginner to CCIE-level expert, offers an intensive 4-month instructor-led Cisco Security program — including live labs, real-world case studies, and exam-oriented practice.
Seats fill quickly — check the full course outline here: course.networkjourney.com/ccie-security and secure your slot today.
Don’t just learn ISE — master it and build job-ready skills that pay off in interviews and production networks.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 31] Cisco ISE Mastery Training: Wired Posture Assessment Overview](https://networkjourney.com/wp-content/uploads/2025/08/Day-31-–-Cisco-ISE-Mastery-Training-Wired-Posture-Assessment-Overview-1.png)
![[Day 8] Cisco ISE Mastery Training: Integrating ISE with Active Directory](https://networkjourney.com/wp-content/uploads/2025/08/Day-8-Cisco-ISE-Mastery-Training-Integrating-ISE-with-Active-Directory.png)

