[Day 33] Cisco ISE Mastery Training: Posture Policy Basics
Table of Contents
Introduction
Cisco ISE Posture Policy is like the network’s “bouncer” — it doesn’t just check who you are, it checks how healthy your device is before granting full access. In wired/wireless NAC environments, posture ensures that endpoints comply with corporate security standards — antivirus running, firewall enabled, OS patched — before they can access sensitive resources.
Without posture, a compromised laptop with valid credentials could still walk right into your core network. With posture, that same device is quarantined, remediated, and only then allowed in.
In this session, we’ll go deep into configuring a Posture Policy from scratch in Cisco ISE, testing it in a lab, validating results from both the ISE GUI and CLI, and ensuring you understand every moving part.
Problem Statement
Many organizations rely solely on authentication and authorization for network access, ignoring the actual security state of endpoints. This creates risks:
- Unpatched OS vulnerabilities
- Disabled antivirus or outdated signatures
- Misconfigured firewalls
- Malware-infected machines gaining access
The real challenge: How do we automatically assess and enforce endpoint compliance before granting network access?
Solution Overview
Cisco ISE’s Posture Service + AnyConnect ISE Posture Module:
- Endpoint connects (wired/wireless/VPN).
- ISE checks identity via 802.1X/MAB.
- Posture Module scans device against configured compliance rules.
- If compliant → Full access VLAN/ACL.
- If non-compliant → Remediation VLAN/ACL with limited access.
- Once fixed → ISE issues CoA (Change of Authorization) to grant full access.
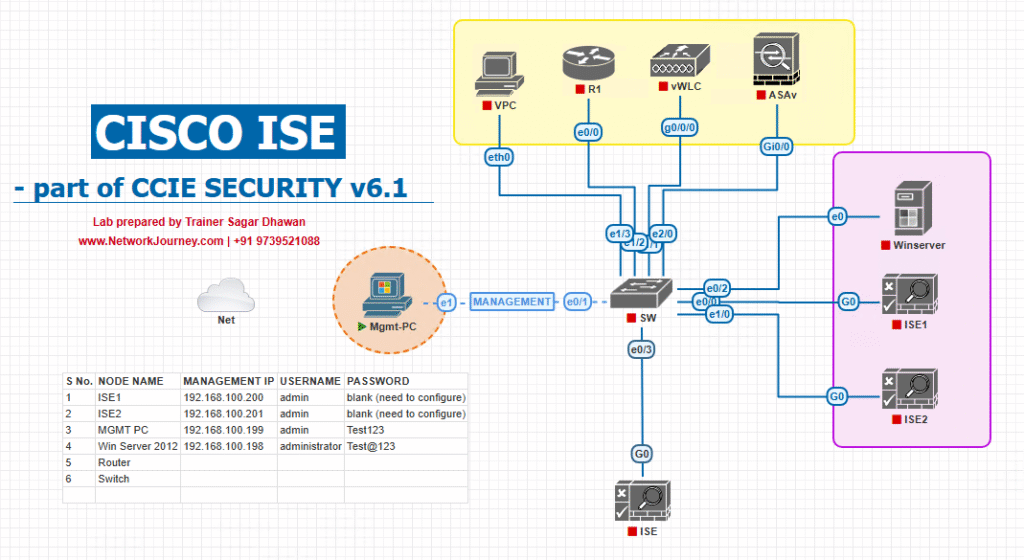
Sample Lab Topology
Lab Environment:
- Platform: VMware Workstation or EVE-NG
- ISE Server: Cisco ISE 3.x (2 CPUs, 16 GB RAM)
- Switch: Catalyst 9300 in EVE-NG or physical lab
- Endpoint: Windows 10 with AnyConnect + ISE Posture Module installed
- Optional: WLC + AP for wireless posture testing
Topology Diagram:
Step-by-Step GUI Configuration Guide
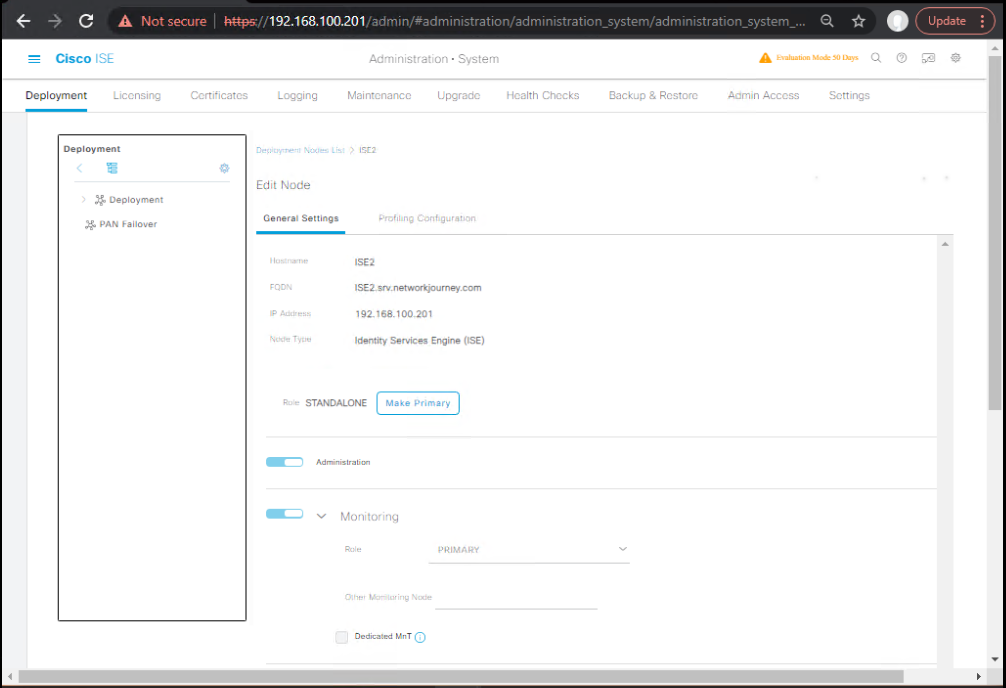
Step 1 – Enable Posture Service in ISE
- Go to Administration → System → Deployment.
- Select your ISE node.
- Enable Policy Service and Posture Service roles.
- Save & Restart node services. [Screenshot: ISE Deployment Node Roles Screen]
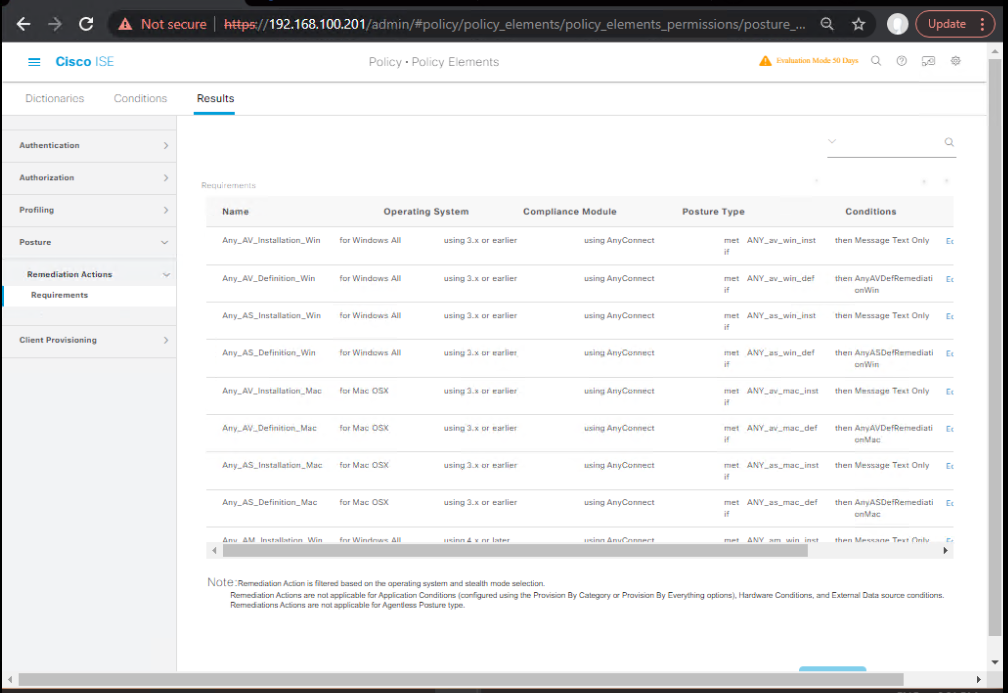
Step 2 – Create Posture Requirements
- Navigate to Policy → Policy Elements → Results → Posture → Requirements.
- Click Add → Choose OS type (Windows/Mac).
- Example: “Antivirus Enabled & Updated” requirement.
- Select conditions like Process Running or Definition Update Age. [Screenshot: Posture Requirement Configuration]
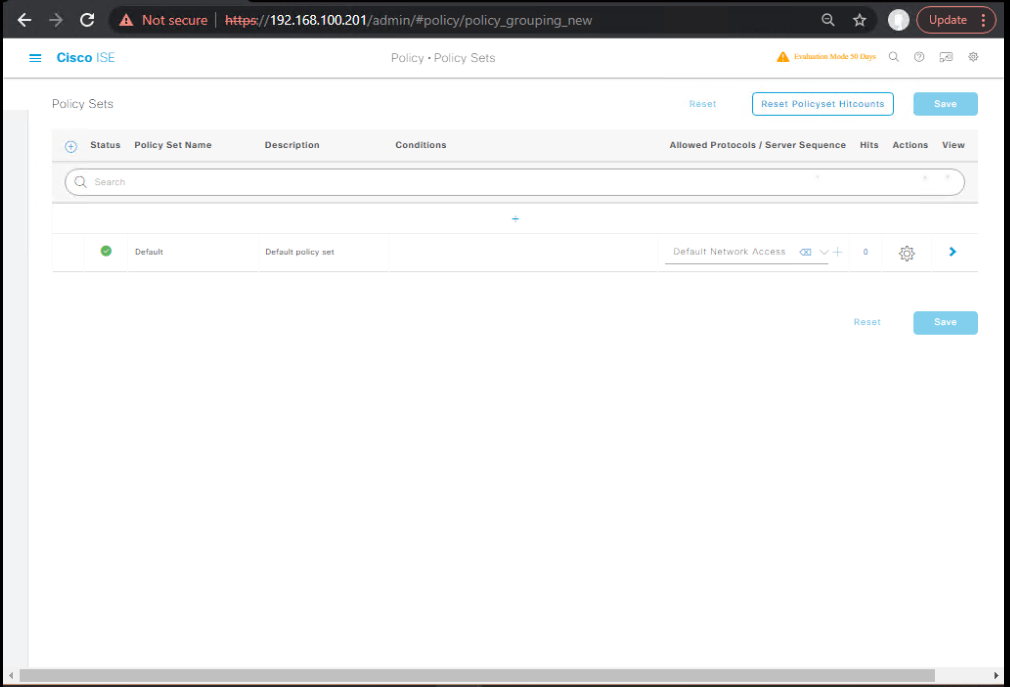
Step 3 – Create Posture Policies
- Go to Policy → Policy Sets.
- Under your Wired/Wireless Policy Set → Add Posture condition.
- Assign compliant endpoints to Full Access authorization profile.
- Assign non-compliant endpoints to Remediation VLAN/ACL.
[Screenshot: ISE Policy Set with Posture Conditions]
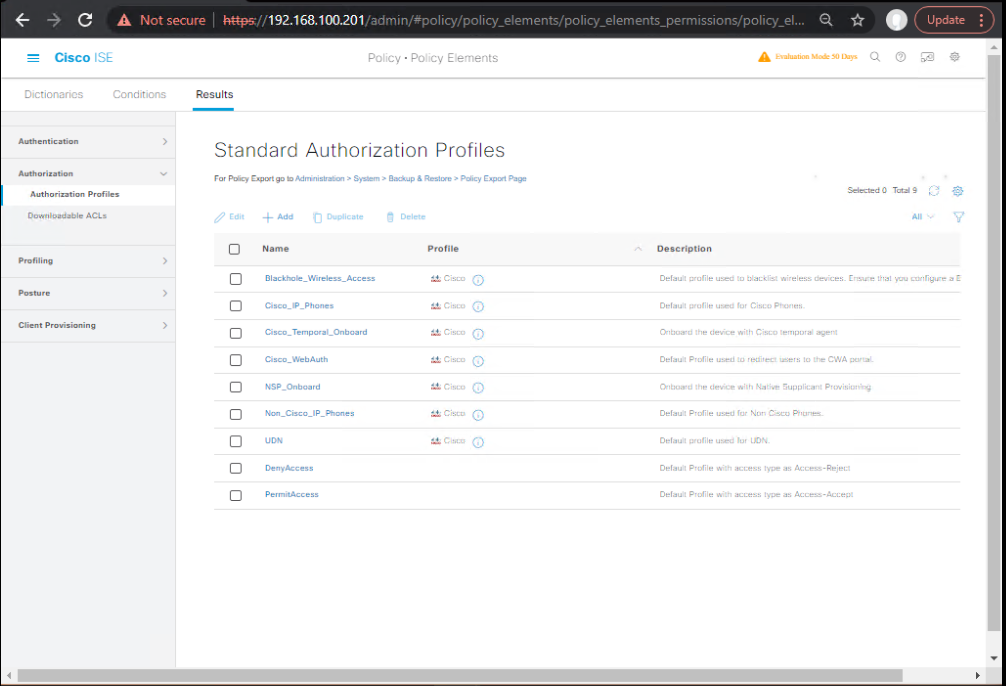
Step 4 – Configure Authorization Profiles
- Full Access VLAN: Internal VLAN with all resources.
- Remediation VLAN: Limited access (only patch servers, AV updates).
- Go to Policy → Policy Elements → Results → Authorization → Authorization Profiles. [Screenshot: Authorization Profile Screen]
Step 5 – Prepare Endpoint with AnyConnect Posture Module
Install Steps (Windows CLI):
msiexec /i anyconnect-win-predeploy-k9.msi /quiet msiexec /i anyconnect-posture-predeploy-k9.msi /quiet
- Verify installation in Control Panel → Programs or via:
Get-Service | findstr "cisco"
Step 6 – Test and Validate
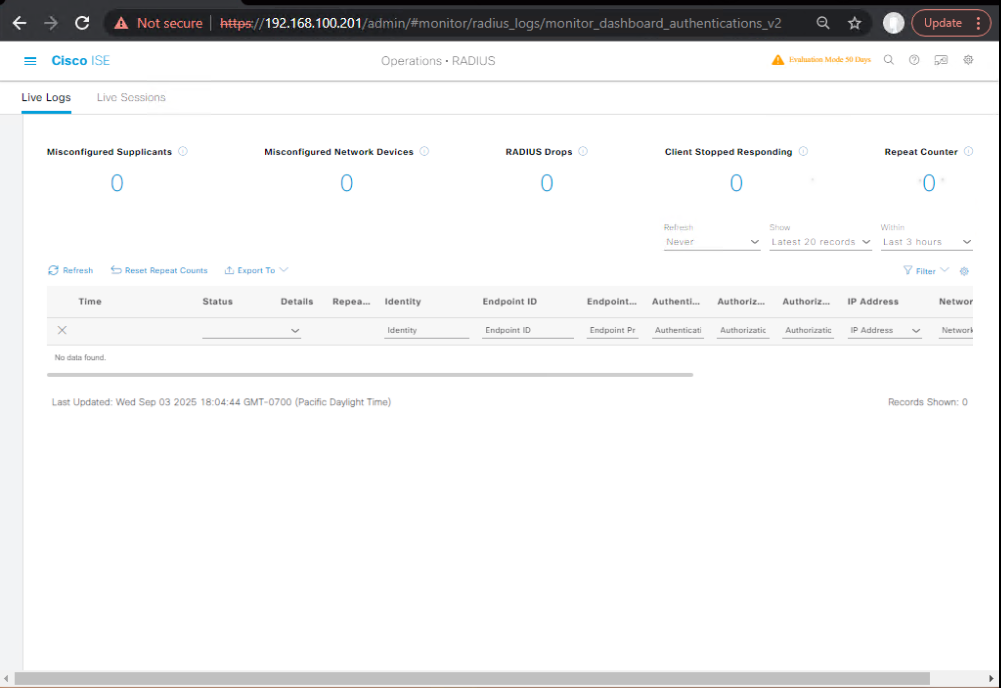
- GUI Validation (ISE):
- Go to Operations → RADIUS → Live Logs.
- Look for
PostureStatus=CompliantorNonCompliant.
[Screenshot: ISE Live Logs Posture Status]
- CLI Validation (Switch):
show authentication sessions interface Gi1/0/10 details
Look for:
Posture status: Compliant Session timeout: 1800 sec Common Session ID: C0A8...
FAQs – Cisco ISE Posture Policy Basics
1. What is the difference between Posture, Profiling, and Authorization in Cisco ISE?
- Posture checks the security health of a device (AV, firewall, patches).
- Profiling identifies what type of device it is (printer, IP phone, Windows PC).
- Authorization decides what access to give based on identity, group, posture status, etc.
ISE can combine all three to enforce very granular NAC policies.
2. Is the Cisco NAC Agent still used for posture?
No. The Cisco NAC Agent is end-of-life. Modern deployments use the AnyConnect ISE Posture Module for endpoint assessment. It’s more secure, integrates better with ISE, and supports more posture conditions.
3. How does ISE detect if an endpoint is compliant or not?
- The AnyConnect Posture Module runs checks based on posture requirements in ISE.
- It looks for OS version, AV status, firewall status, registry keys, file presence, process running, and more.
- The result is sent back to ISE over RADIUS, which updates the posture status in the Live Logs.
4. Can posture work without 802.1X authentication?
Yes, it can work with MAB (MAC Authentication Bypass), but:
- MAB does not verify user identity — only device MAC.
- It’s less secure and easier to spoof.
For best results, use 802.1X + Posture.
5. What happens when a device is non-compliant?
ISE assigns it a restricted Authorization Profile (e.g., Remediation VLAN/ACL).
- The endpoint can only reach update servers (AV definitions, patch servers, WSUS).
- Once fixed, ISE triggers CoA (Change of Authorization) and moves it to a Full Access VLAN.
6. How does CoA (Change of Authorization) work in posture?
- After remediation, the Posture Module sends a “compliant” update to ISE.
- ISE sends a RADIUS CoA packet to the switch/WLC, forcing re-authorization.
- The new policy (full access) is applied without disconnecting the user completely.
7. How can I test posture in a lab without internet?
- Use internal WSUS or AV definition servers in your remediation VLAN.
- Simulate non-compliance by disabling the AV or turning off firewall.
- Manually trigger posture reassessment by disconnect/reconnect or CoA.
8. Where can I see posture results in ISE?
- Operations → RADIUS → Live Logs → Look at
PostureStatus. - Operations → Reports → Posture → Posture Assessment by Condition for detailed history.
- CLI on switch:
show authentication sessions int Gi1/0/10 details
Look for Posture status: Compliant/NonCompliant.
9. Does posture affect performance or user experience?
- Initial scans can delay network access by a few seconds to a minute, depending on complexity.
- Avoid adding too many posture checks unless required.
- Educate users so they know why they are being quarantined.
10. Can I have different posture rules for different user groups or devices?
Yes. You can:
- Create separate Posture Policies in ISE.
- Match based on AD group, device type (profiling), OS type, or network location.
- Example: IT staff get stricter posture rules than guest users.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Posture isn’t just an add-on — it’s your frontline defense against unhealthy endpoints accessing critical resources. By combining identity, authorization, and device compliance, Cisco ISE ensures only trusted, healthy devices enter your network.
Upgrade Your Skills – Start Today
Master Cisco ISE from Zero to Expert in 4 Months.
If you enjoyed this deep-dive, you’ll love the Cisco ISE & CCIE Security Mastery Program,
A 4-month live instructor-led training covering real-world enterprise deployments, CCIE Security lab preparation, and hands-on labs using VMware/EVE-NG.
- Learn with live troubleshooting
- Get lifetime lab access
- Follow step-by-step enterprise use cases
- Prepare for CCNP/CCIE Security exams with confidence
Next batch starting soon — seats are limited!
Check the full course outline & register here → https://course.networkjourney.com/ccie-security/
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 33] Cisco ISE Mastery Training: Posture Policy Basics](https://networkjourney.com/wp-content/uploads/2025/08/Day-33-–-Cisco-ISE-Mastery-Training-Posture-Policy-Basics.png)


