[Day 34] Cisco ISE Mastery Training: Wired Endpoint Posture Compliance Lab
Table of Contents
Introduction
Wired Endpoint Posture Compliance in Cisco Identity Services Engine (ISE) is where network access control meets endpoint security hygiene. It’s not enough to just identify and authenticate a device — in modern enterprise networks, you must ensure it’s secure before allowing access to sensitive resources.
This lab focuses on configuring Cisco ISE to enforce security health checks for wired endpoints using the AnyConnect ISE Posture Module. We will integrate switch-based 802.1X, endpoint posture policies, and real-time remediation, validating everything through both GUI and CLI.
By the end of this lab, you’ll know how to:
- Build posture compliance rules in ISE.
- Trigger remediation VLANs/ACLs for non-compliant endpoints.
- Validate compliance through RADIUS live logs, switch CLI, and ISE reports.
Problem Statement
In real-world enterprise networks:
- Laptops can connect to wired ports directly, bypassing wireless security controls.
- Even if authenticated via 802.1X, they could still be running outdated antivirus, missing patches, or having the firewall turned off.
- Malware infections and unpatched systems can spread laterally once inside.
Without posture compliance, the network has no visibility into device health, making it vulnerable to insider threats, ransomware, and compliance violations.
Solution Overview
Cisco ISE enforces wired posture compliance by:
- Using AnyConnect ISE Posture Module to scan endpoints.
- Checking against Posture Policies (e.g., AV must be installed and updated).
- Assigning restricted access to non-compliant devices via VLANs/ACLs.
- Automatically granting full network access once the endpoint is compliant.
- Performing dynamic CoA (Change of Authorization) to switch the endpoint’s access without manual intervention.
Sample Lab Topology
Text Description:
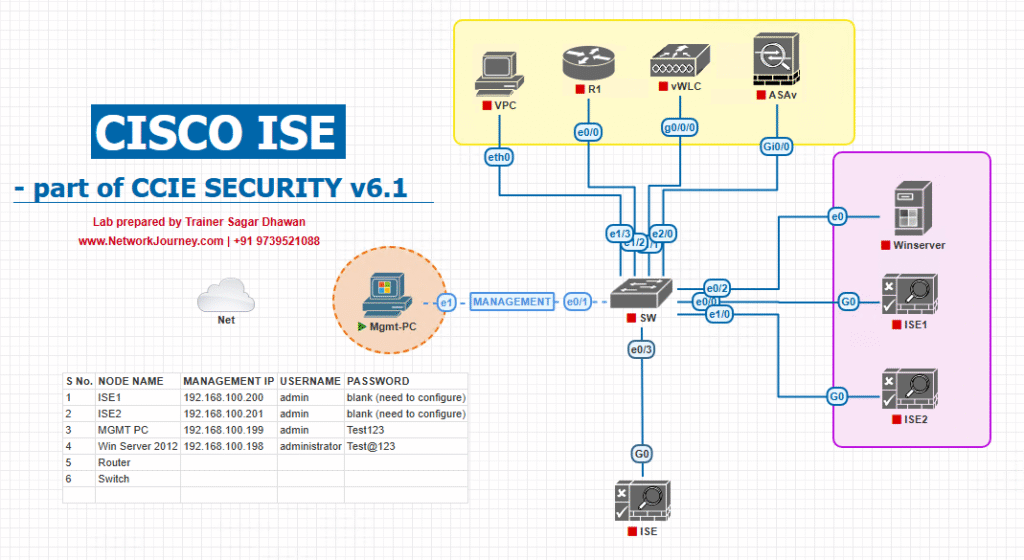
- VMware ESXi/EVE-NG for hosting ISE and Windows endpoints.
- Cisco Catalyst switch acting as the 802.1X authenticator.
- Windows 10 laptop with AnyConnect + ISE Posture Module.
- ISE 3.x deployed with full licensing.
- AD server for user identity management.
- Remediation VLAN connected to WSUS/AV update server.
Diagram placeholder:
[Screenshot: Lab Topology Diagram – Wired Posture Compliance Setup]
Step-by-Step GUI Configuration Guide
A. Configure Switch for Wired 802.1X + Posture
conf t aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius aaa accounting update periodic 1 radius-server host 10.10.10.10 key Cisco123 ip device tracking ! interface Gig1/0/10 switchport mode access authentication port-control auto mab dot1x pae authenticator spanning-tree portfast
Validation:
show authentication sessions int gi1/0/10 details
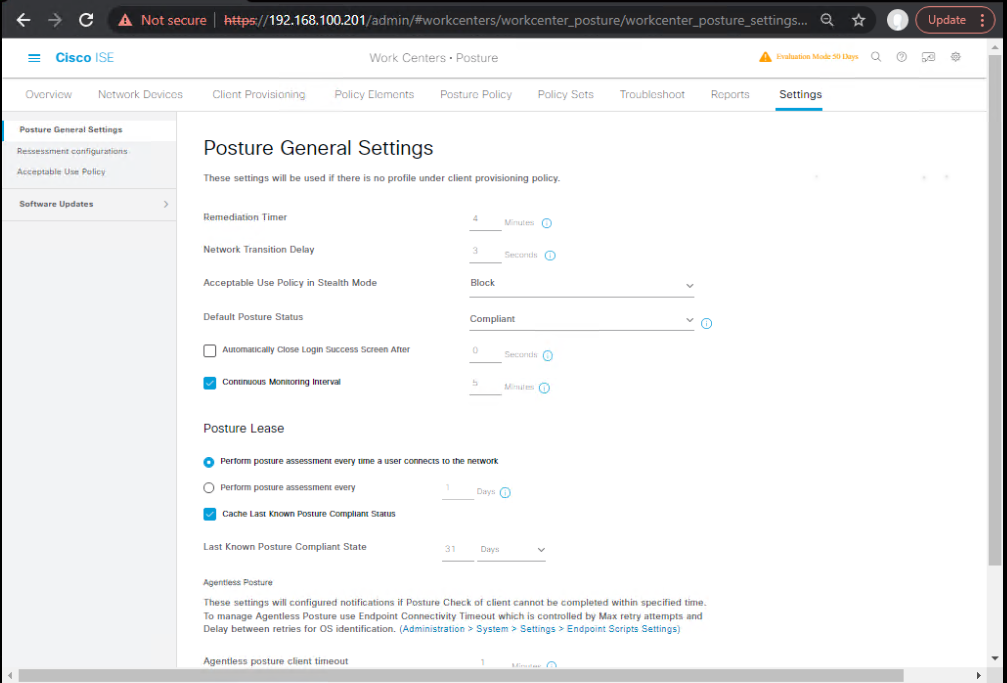
B. Enable Posture in ISE
- Go to Work Centers → Posture → Settings.
- Enable posture service globally.
- Add AnyConnect ISE Posture as the agent type.
- [Screenshot: ISE Posture Global Settings Screen]
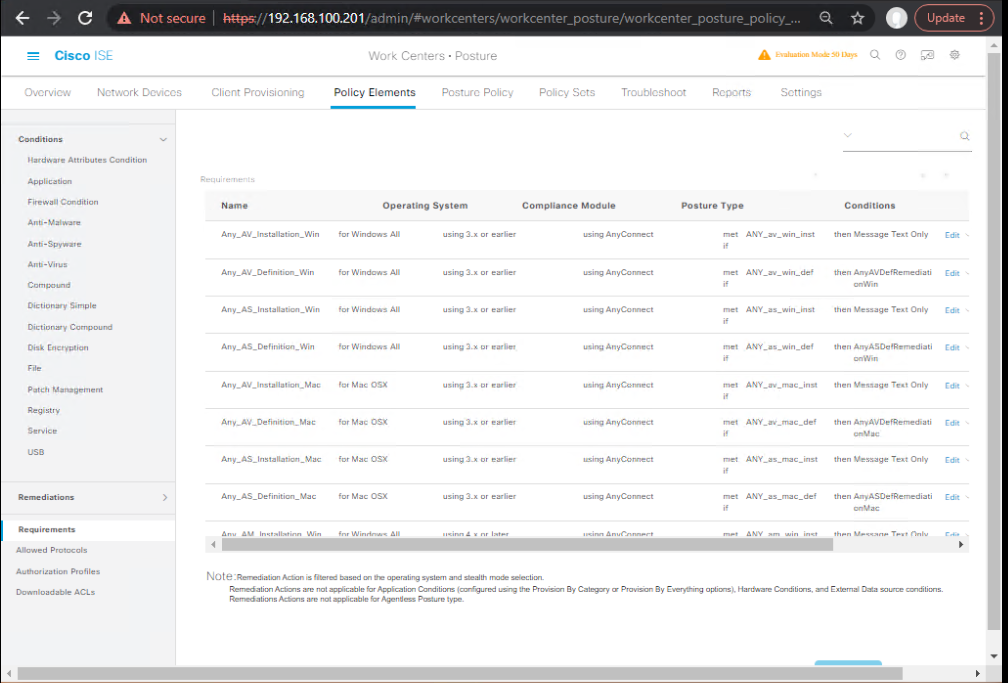
C. Create Posture Requirements
- Navigate to Work Centers → Posture → Policy Elements → Requirements.
- Example:
- Requirement: “Windows Firewall must be enabled”
- Condition: OS = Windows, Firewall Status = Enabled
- Save and publish.
- [Screenshot: ISE Posture Requirement Screen]
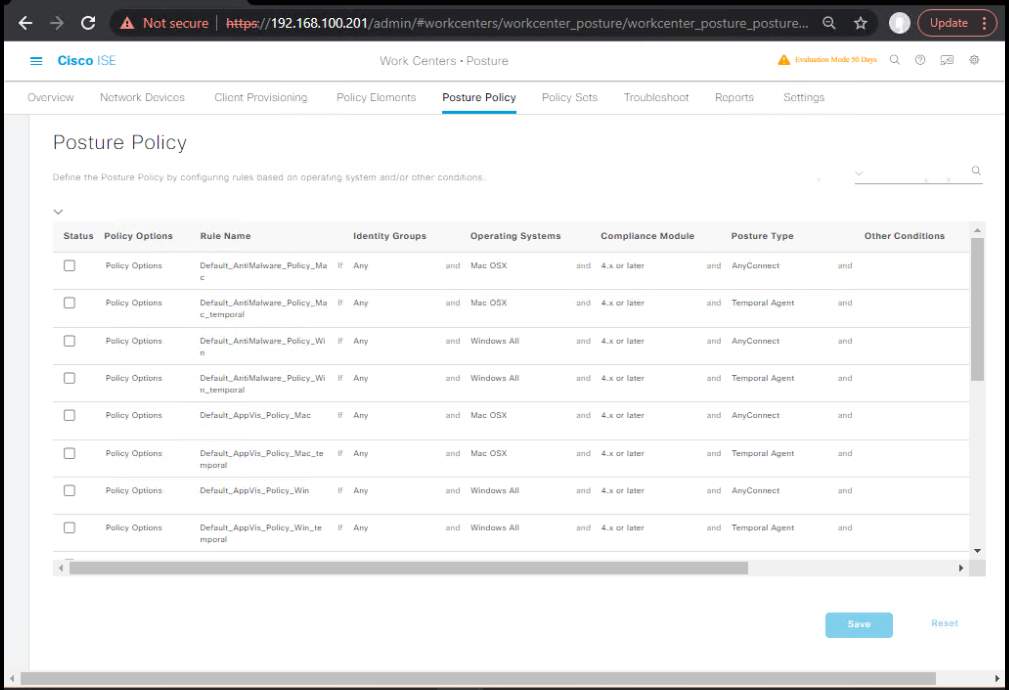
D. Create Posture Policy
- Go to Work Centers → Posture → Policy.
- Add new policy:
- Condition:
Endpoint:WindowsANDAV Installed - Result: Compliant = PermitAccess, NonCompliant = RemediationAccess.
- Condition:
- [Screenshot: ISE Posture Policy Screen]
E. Authorization Profiles
- Create Remediation VLAN profile:
- VLAN = 30
- ACL = Permit updates to AV/WSUS only.
- Create Full Access profile:
- VLAN = 10.
- [Screenshot: ISE Authorization Profile Screen]
F. Policy Sets
- Go to Policy → Policy Sets.
- Create Wired Policy Set:
- Condition:
Wired MABorWired Dot1X. - Authentication: Use AD for user auth.
- Authorization:
- If Compliant → Full Access Profile.
- If NonCompliant → Remediation VLAN Profile.
- Condition:
- [Screenshot: ISE Policy Set Screen]
G. Endpoint Validation (Posture Process)
- Connect endpoint to switch port.
- AnyConnect Posture Module launches → Scans → Sends results to ISE.
- NonCompliant → placed in Remediation VLAN.
- After fixing → CoA triggers → Moved to Full Access VLAN.
GUI Validation:
- ISE Operations → Live Logs → Check PostureStatus = Compliant/NonCompliant.
CLI Validation:
show authentication sessions int gi1/0/10 details
FAQs – Wired Endpoint Posture Compliance
1. How does ISE know whether an endpoint is compliant or not?
ISE relies on the AnyConnect ISE Posture Module installed on the endpoint. When the device connects to the network, the posture module scans for defined requirements (e.g., antivirus installed, OS patch level, firewall status) and sends the results back to ISE. ISE then applies the matching authorization rule (Full Access or Remediation).
2. Can posture compliance be enforced without 802.1X authentication?
Yes — posture can be enforced with MAB (MAC Authentication Bypass), but it’s less secure because identity is tied only to the MAC address, which can be spoofed. In production, posture is typically paired with 802.1X for stronger security.
3. What happens if the posture agent is not installed on the endpoint?
If the endpoint does not have the AnyConnect ISE Posture Module, it will fail posture by default and be placed in the remediation VLAN/ACL. From there, the user can be directed to a download portal to install the agent.
4. Can posture policies be different for different user groups or VLANs?
Yes. You can create multiple posture policies and map them to specific user roles, VLANs, or authentication conditions. For example, corporate laptops might have stricter posture requirements than guest endpoints.
5. How often does posture re-evaluation happen?
By default, posture is checked at login/connection time. You can configure periodic posture checks or trigger re-assessment via Change of Authorization (CoA) when conditions change (e.g., firewall turned off mid-session).
6. How can I verify posture results in the GUI and CLI?
- GUI: ISE → Operations → Live Logs → Look for the
PostureStatusattribute in the RADIUS request. - CLI: On the switch →
show authentication sessions interface Gi1/0/x details→ Look forStatus: Authz Successand the VLAN/ACL assigned.
7. What’s the difference between “Unknown,” “NonCompliant,” and “Compliant” in posture results?
- Unknown: No posture check performed yet or agent hasn’t reported status.
- NonCompliant: Posture agent ran but endpoint failed one or more requirements.
- Compliant: All posture requirements passed.
8. Does posture checking slow down endpoint network access?
Initial posture assessment can take a few seconds to a minute depending on the number of checks and system performance. Once compliant, normal access is restored immediately. To optimize, avoid excessive scan items (like large directory scans).
9. Can I enforce software version checks, like ensuring a specific antivirus version is installed?
Yes. In the Posture Requirements, you can define conditions for specific software names and versions. For example: “AV = Cisco Secure Endpoint, Version ≥ 7.5.1.”
10. What’s the process if a device fails posture and needs remediation?
- Endpoint connects and fails posture.
- ISE applies Remediation VLAN or ACL that only allows access to update servers (AV, WSUS, patch server).
- User fixes the issue (e.g., updates AV, enables firewall).
- AnyConnect posture agent re-scans.
- ISE receives compliant status and triggers a CoA to grant full access.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Posture compliance transforms your wired NAC deployment from identity-aware to security-health-aware. This lab showed how to build a hands-on, real-world posture enforcement workflow using ISE and AnyConnect, validated with both GUI and CLI.
Upgrade Your Skills – Start Today
Level Up Your Cisco Security Skills with Sagar Dhawan
If this lab excited you, imagine mastering the entire Cisco ISE, ASA, Firepower, VPN, and advanced CCIE Security stack over 4 months of intensive, instructor-led training.
You’ll work on real enterprise-grade labs, get lifetime access to recordings, and learn battle-tested troubleshooting skills that top security engineers use daily.
- Seats are limited — secure your spot now:
- View the Full CCIE Security Training Outline
The fastest way to go from lab enthusiast to job-ready security expert is here.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![Ticket#23: SSL VPN Users Cannot Reach Internal Resources – Split Tunnel ACL Error Fixed [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/Ticket23-SSL-VPN-Users-Cannot-Reach-Internal-Resources-–-Split-Tunnel-ACL-Error-Fixed_networkjourney.png)
![[Day 7] Cisco ISE Mastery Training: Configuring Certificates (Self-Signed & CA-Signed)](https://networkjourney.com/wp-content/uploads/2025/08/Day-7-Cisco-ISE-Mastery-Training-Configuring-Certificates-Self-Signed-CA-Signed.png)
![Ticket#4 - BGP Route Not Installing in RIB – Path Attributes and Fix [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-Ticket-4.jpg)