[Day 35] Cisco ISE Mastery Training: BYOD Wired Onboarding
Table of Contents
Introduction
In today’s hybrid workspace, BYOD (Bring Your Own Device) is no longer optional — employees, contractors, and guests all bring their own laptops to connect to corporate resources. Over wired connections, onboarding BYOD devices is trickier than wireless because physical switch ports require 802.1X/MAB authentication, provisioning portals, and secure certificate handling — all without preconfiguring the device.
Cisco ISE provides a fully automated BYOD wired onboarding workflow where endpoints:
- Self-register
- Get onboarded with an endpoint identity certificate
- Are assigned the correct network profile without manual IT intervention
This process ensures security compliance while keeping the user experience frictionless.
Problem Statement
Traditional wired onboarding involves:
- Manual IT setup
- MAC whitelisting or pre-registered device entries
- Weak guest access controls
- No endpoint compliance tracking
These methods cause:
- Security gaps (rogue devices gain access)
- Operational delays
- Frustration for end users
We need a solution that authenticates unknown devices, registers them in ISE, provisions them with certificates, and dynamically authorizes them — all without IT desk visits.
Solution Overview
Cisco ISE’s BYOD wired onboarding uses:
- 802.1X + MAB fallback
- ISE Guest/BYOD portals for self-service onboarding
- Certificate provisioning via ISE SCEP or internal CA
- Authorization policy rules that change based on onboarding stage
Flow:
- Endpoint connects to wired port
- ISE classifies device as unknown → redirects to BYOD portal
- User logs in with corporate credentials
- Certificate provisioned to endpoint
- Device reauthenticates with EAP-TLS using new certificate
- Full access granted based on compliance profile
Sample Lab Topology
Lab Tools: VMware/EVE-NG, Cisco ISE, Catalyst Switch (L2/L3), BYOD laptop endpoints
Components:
- ISE Node (2.7 or higher) on VMware
- Catalyst 9300 in EVE-NG or physical
- Windows/Mac endpoint (BYOD device)
- AD/DNS server (optional for identity store)
Diagram:
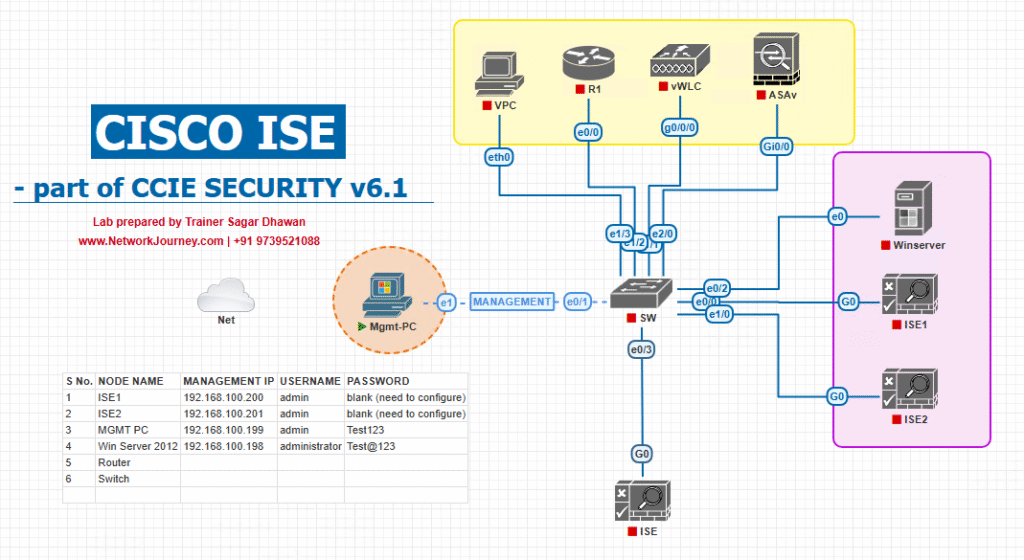
Port Gi1/0/10 configured for 802.1X + MAB with VLAN assignment via ISE.
Step-by-Step GUI + CLI Configuration Guide
A. Switch CLI Configuration
conf t aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius aaa accounting update periodic 5 radius server ISE1 address ipv4 10.10.10.5 auth-port 1812 acct-port 1813 key cisco123 ip device tracking interface Gi1/0/10 switchport mode access authentication order mab dot1x authentication priority dot1x mab authentication port-control auto mab dot1x pae authenticator spanning-tree portfast
Validation:
show authentication sessions interface Gi1/0/10 details
B. ISE GUI Configuration
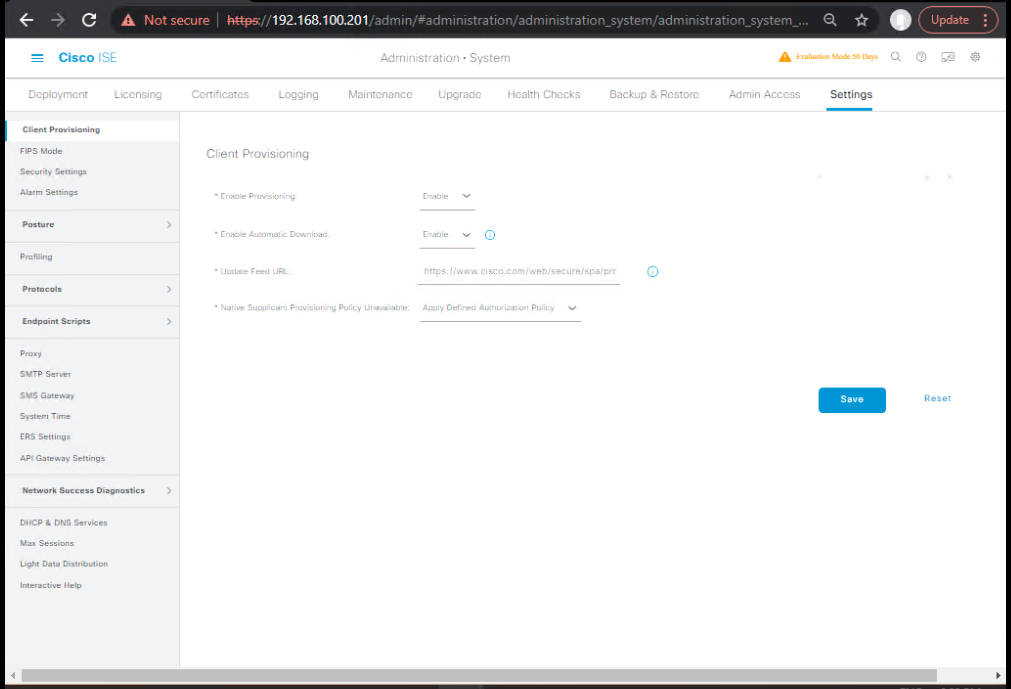
Step 1 – Enable BYOD Services
- Navigate: Administration → Settings → Client Provisioning
- Enable BYOD Device Registration and Certificate Provisioning
- [Screenshot: ISE BYOD Service Enable Screen]
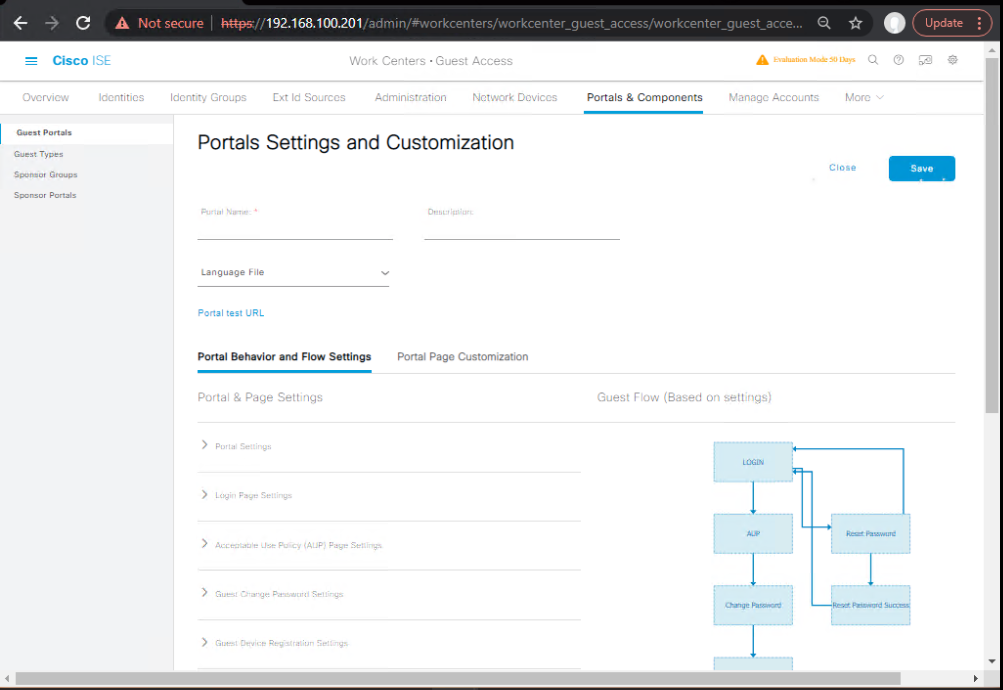
Step 2 – Create BYOD Portal
- Go to Work Centers → Guest Access → Portals & Components → BYOD Portals
- Create New BYOD Portal
- Set authentication method = AD or Internal Users
- [Screenshot: BYOD Portal Configuration]
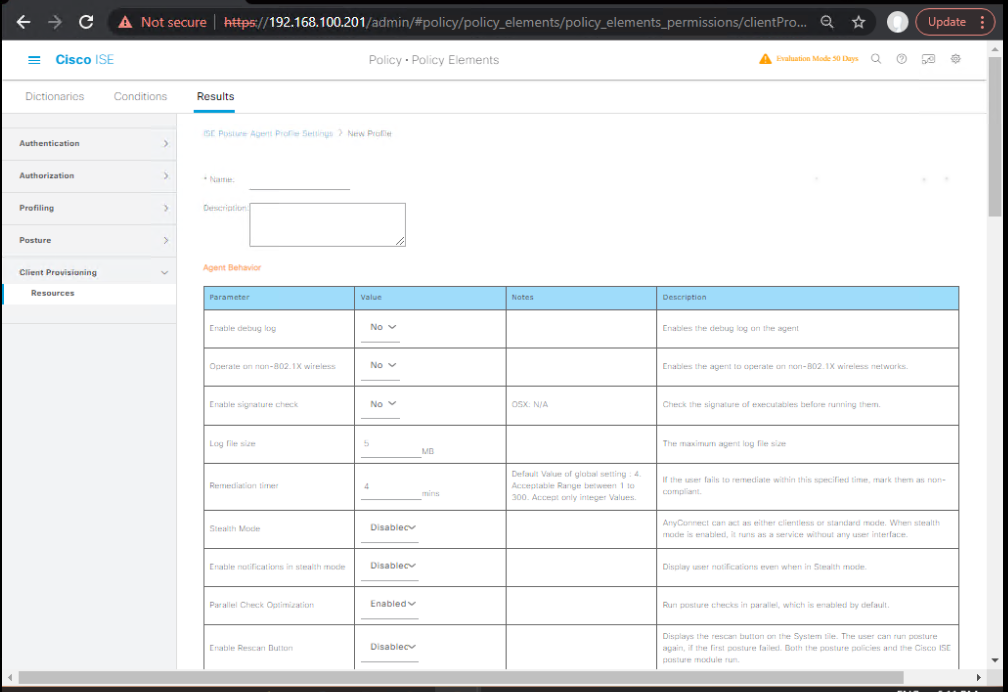
Step 3 – Client Provisioning Policy
- Go to Policy → Policy Elements → Results → Client Provisioning → Resources
- Add AnyConnect Compliance Module and Certificate provisioning script
- [Screenshot: Client Provisioning Policy]
Step 4 – Authorization Policy
Example rules:
- Condition: Wired_MAB and
Endpoint:IdentityGroup = Unknown
→ Result: Redirect to BYOD Portal ACL - Condition:
Wired_802.1XandCertificateIssuedBy ISE
→ Result: Full Access VLAN/ACL
- [Screenshot: ISE Authorization Policy Rules]
Step 5 – Download & Install AnyConnect NAM/Posture Module (if required)
- Redirect ACL allows ISE, DNS, CRL, SCEP, and update servers
- User downloads from portal → installs
CLI Validation after Onboarding:
show authentication sessions interface Gi1/0/10 details # Look for: Status: Authz Success Method: dot1x Domain: DATA
FAQs – BYOD Wired Onboarding
1. How is BYOD wired onboarding different from wireless onboarding in Cisco ISE?
- Wired onboarding requires configuring 802.1X/MAB on switch ports, handling VLAN assignments, and managing limited portal redirection through ACLs on the access switch.
- Wireless onboarding typically uses a WLC to redirect traffic to the BYOD portal without manual ACL configuration.
- In wired setups, switch hardware, IOS version, and RADIUS timeout tuning are more critical.
2. Do I need a separate VLAN for BYOD onboarding?
- Recommended but not mandatory.
- A dedicated VLAN for onboarding (with limited internet/ISE access) improves security and simplifies troubleshooting.
- VLAN assignment can be done dynamically via ISE Authorization Profiles during onboarding.
3. What’s the role of the BYOD portal ACL in wired onboarding?
- It ensures that before onboarding is complete, the endpoint can only reach:
- ISE nodes (HTTPS)
- SCEP server
- DNS server
- CRL distribution points
- Without the ACL, endpoints might either get full access prematurely or be unable to reach the onboarding resources.
4. Can a non-domain-joined device complete BYOD wired onboarding?
- Yes — domain membership is not required.
- Users authenticate with AD or internal ISE credentials, and the endpoint is provisioned with an ISE-issued certificate.
5. How do we handle endpoints that don’t support 802.1X for wired BYOD?
- Use MAB to trigger web-based onboarding.
- This is less secure and may require stricter ACLs to reduce risk.
- Some legacy devices may need manual MAC registration in ISE.
6. What happens if an onboarded device’s certificate expires?
- The device will fail 802.1X EAP-TLS authentication.
- ISE can redirect it to the BYOD portal for re-provisioning.
- Best practice: configure certificate lifetimes and renewal reminders in ISE.
7. Can posture checks be integrated into BYOD wired onboarding?
- Yes, via Cisco AnyConnect Posture Module.
- You can require compliance (e.g., AV running, OS patch level) before granting full VLAN/ACL access after onboarding.
8. How does ISE differentiate between corporate BYOD and guest devices?
- Endpoint identity groups and authorization rules separate BYOD from guests.
- Guests use guest portals; BYOD devices are recognized by certificates issued during onboarding.
9. What’s the most common failure point in BYOD wired onboarding?
- Misconfigured switch redirection ACLs or missing DNS reachability.
- Endpoints can’t load the BYOD portal if they can’t resolve ISE’s hostname or reach its HTTPS service.
10. How do I verify BYOD wired onboarding success from CLI and GUI?
- CLI (Switch):
show authentication sessions interface Gi1/0/10 details # Look for Method: dot1x, Status: Authz Success - ISE GUI:
- Go to Operations → RADIUS → Live Logs
- Look for final authentication using EAP-TLS and the endpoint identity group updated to RegisteredDevices.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
BYOD wired onboarding with Cisco ISE ensures security, automation, and compliance without slowing down productivity. With proper portal design, certificate provisioning, and authorization rules, users can self-onboard their devices in minutes — while IT retains full control.
Upgrade Your Skills – Start Today
Take Your Cisco ISE Skills from Lab to CCIE Level in 4 Months!
I run a focused an Instructor-Led CCIE Security Mastery Program — a hands-on, project-driven course where you’ll design, configure, and troubleshoot ISE deployments for real-world enterprise environments.
This isn’t just theory — you’ll build full-scale labs, get 1-on-1 mentoring, and prepare for CCIE Security certification.
Seats are limited and enrollment closes soon.
- Check the full course outline here: https://course.networkjourney.com/ccie-security/
- Secure your spot today and start your journey from network engineer to CCIE-level expert.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088


![[Day 121] Cisco ISE Mastery Training: Automated Guest User Creation via API](https://networkjourney.com/wp-content/uploads/2025/08/Day-121-Cisco-ISE-Mastery-Training-Automated-Guest-User-Creation-via-API.png)
