[Day #40 PyATS Series] Identify Duplicate IPs in ARP Table Across Vendors Using pyATS for Cisco [Python for Network Engineer]
Table of Contents
Introduction on the Key Points
Duplicate IP addresses are one of the most common yet frustrating issues network engineers face in multi-vendor environments. They cause intermittent connectivity issues, ARP flapping, MAC address instability, and even network outages if not detected early.
As a Python for Network Engineer practitioner, you can save hours of manual troubleshooting by automating ARP table scans for duplicate IPs using pyATS. Unlike manual show arp commands on each device, this approach runs a single test script across Cisco, Arista, Palo Alto, and Fortinet devices to:
- Collect ARP entries from all devices in your network
- Identify duplicate IP addresses mapped to different MAC addresses
- Provide a vendor-agnostic, structured report for immediate action
This tutorial walks you through building a fully automated duplicate IP detection tool using pyATS, making your network health checks proactive and scalable.
Topology Overview
For this lab, we’ll consider a simplified multi-vendor network:
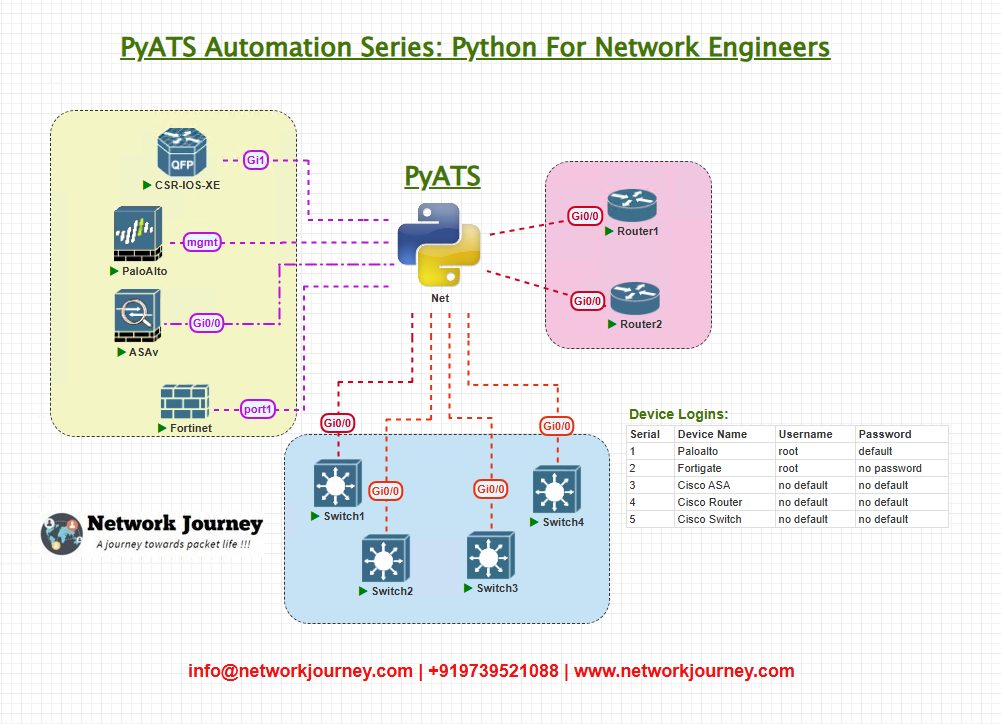
- R1: Cisco IOS-XE router (core)
- R2: Arista switch (distribution)
- FW1: Palo Alto firewall (security segment)
- FW2: Fortinet firewall (edge)
Duplicate IPs may appear if:
- Rogue DHCP servers assign overlapping addresses
- Manual static IP configurations clash
- Virtual machines or container workloads reuse IPs across VLANs
Our automation ensures we detect these anomalies before they cause downtime.
Topology & Communications
- Protocols: ARP is a Layer 2 protocol used to resolve IP-to-MAC mappings.
- Communication: pyATS connects via SSH to each device.
- Data Gathering:
show arp(Cisco, Arista) or equivalent CLI commands (Palo Alto, Fortinet) are parsed using Genie or custom parsers. - Cross-checking: We check for multiple MACs mapped to the same IP within and across devices.
Workflow Script
from genie.testbed import load
import json
from collections import defaultdict
def collect_arp_entries(device):
device.connect(log_stdout=False)
output = device.parse('show arp')
device.disconnect()
arp_data = []
for entry in output.get('interfaces', {}).values():
for arp in entry.get('arp_table', {}).values():
arp_data.append({
'ip': arp.get('ip'),
'mac': arp.get('mac'),
'interface': arp.get('interface'),
'device': device.name
})
return arp_data
def find_duplicates(arp_entries):
ip_to_macs = defaultdict(set)
duplicates = {}
for entry in arp_entries:
ip_to_macs[entry['ip']].add(entry['mac'])
for ip, macs in ip_to_macs.items():
if len(macs) > 1:
duplicates[ip] = list(macs)
return duplicates
if __name__ == "__main__":
testbed = load('testbed.yml')
all_entries = []
for name, device in testbed.devices.items():
print(f"Collecting ARP entries from {name}...")
all_entries.extend(collect_arp_entries(device))
duplicates = find_duplicates(all_entries)
with open('duplicate_ips.json', 'w') as f:
json.dump(duplicates, f, indent=4)
if duplicates:
print("Duplicate IPs found:")
print(json.dumps(duplicates, indent=4))
else:
print("No duplicate IPs detected.")
Explanation by Line
- collect_arp_entries: Connects to each device, parses ARP entries, and extracts IP, MAC, and interface details.
- find_duplicates: Maps IP addresses to MAC addresses and flags those with more than one MAC.
- Main Execution: Iterates over all devices in the testbed, aggregates ARP data, and outputs any detected duplicates to a JSON report.
- Vendor Agnostic: With Genie parsers or custom parsers for Palo Alto and Fortinet, the same logic applies seamlessly.
testbed.yml Example
testbed:
name: arp_duplicate_test
devices:
R1:
os: iosxe
type: router
connections:
cli:
protocol: ssh
ip: 192.168.10.1
credentials:
default:
username: admin
password: cisco123
R2:
os: eos
type: switch
connections:
cli:
protocol: ssh
ip: 192.168.10.2
credentials:
default:
username: admin
password: arista123
FW1:
os: panos
type: firewall
connections:
cli:
protocol: ssh
ip: 192.168.10.3
credentials:
default:
username: admin
password: palo123
FW2:
os: fortinet
type: firewall
connections:
cli:
protocol: ssh
ip: 192.168.10.4
credentials:
default:
username: admin
password: forti123
Post-validation CLI Screenshots (Expected Output)
Cisco R1:
R1# show arp Protocol Address Age MAC Address Interface Internet 192.168.10.50 0 aabb.cc00.1111 Gi0/0 Internet 192.168.10.50 0 aabb.cc00.2222 Gi0/1
(Duplicate IP with different MACs detected)
Script Output:
{
"192.168.10.50": [
"aabb.cc00.1111",
"aabb.cc00.2222"
]
}
FAQs
1. How does the pyATS script detect duplicate IP addresses?
The script collects ARP table entries from multiple devices and checks for IP addresses that map to more than one unique MAC address. If a single IP appears with different MACs, it’s flagged as a duplicate.
2. Can this script work across Cisco, Arista, Palo Alto, and Fortinet devices?
Yes. pyATS uses Genie parsers for Cisco and Arista, while Palo Alto and Fortinet can be supported with custom parsers or CLI commands, making the solution fully multi-vendor.
3. Will this script disrupt production traffic?
No. It only runs read-only show arp or equivalent commands via SSH, so it’s completely safe for live production environments.
4. Can it also detect duplicates for IPv6 addresses?
Yes. With slight modifications to use show ipv6 neighbors, the script can detect duplicate IPv6 addresses alongside IPv4 duplicates.
5. How scalable is this solution for large enterprise networks?
It’s highly scalable. pyATS can handle hundreds of devices in a single test run, and you can use multiprocessing or distributed execution for faster collection.
6. Can the report be automatically sent to teams or monitoring systems?
Yes. The output can be formatted as JSON, CSV, or HTML and sent via email, Slack, or integrated with NMS/monitoring dashboards for proactive alerting.
7. How frequently should we run this duplicate IP detection?
It depends on your network’s dynamics. For DHCP-heavy environments or high churn networks, you can run it every few hours; otherwise, daily or weekly scans work well.
8. Does this method detect duplicates across VLANs or VRFs?
Yes. The script collects ARP entries per interface, VLAN, or VRF. You can enhance it to group results by VLAN/VRF for better visibility of duplicates in segmented networks.
YouTube Link
Watch the Complete Python for Network Engineer: Identify duplicate IPs in ARP table across vendors using pyATS for Cisco [Python for Network Engineer] Lab Demo & Explanation on our channel:
Join Our Training
Detecting duplicate IPs manually wastes time and leaves networks vulnerable to outages. By mastering pyATS and Python automation, you can proactively prevent such issues across Cisco and multi-vendor networks.
Trainer Sagar Dhawan offers a 3-month, instructor-led program teaching Python, Ansible, APIs, and Cisco DevNet for Network Engineers. You’ll build hands-on projects like this one, boosting your automation expertise and career opportunities.
Join Our Training and transform your networking career with Python for Network Engineer skills.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day #40 PyATS Series] Identify Duplicate IPs in ARP Table Across Vendors Using pyATS for Cisco [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/08/Day-40-PyATS-Series-Identify-Duplicate-IPs-in-ARP-Table-Across-Vendors-Using-pyATS-for-Cisco-Python-for-Network-Engineer.png)
![[Day #76 PyATS Series] Automate Zero-Touch Provisioning Validation Using pyATS for Cisco [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/09/Day-76-PyATS-Series-Automate-Zero-Touch-Provisioning-Validation-Using-pyATS-for-Cisco-Python-for-Network-Engineer-470x274.png)
![[Day #97 PyATS Series] Vendor-Agnostic Auto-Documentation Generator (Markdown/PDF) Using pyATS for Cisco [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/09/Day-97-PyATS-Series-Vendor-Agnostic-Auto-Documentation-Generator-Markdown_PDF-Using-pyATS-for-Cisco-Python-for-Network-Engineer-470x274.png)
![[Day #86 PyATS Series] Automated RMA Device Onboarding (Multi-Vendor) Using pyATS for Cisco [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/09/Day-86-PyATS-Series-Automated-RMA-Device-Onboarding-Multi-Vendor-Using-pyATS-for-Cisco-Python-for-Network-Engineer-470x274.png)