[Day 41] Cisco ISE Mastery Training: Wireless 802.1X Authentication Overview
Table of Contents
Introduction
Wireless networks today are the primary access method for employees, guests, and IoT devices — but without proper control, they’re a security nightmare. Users can connect from anywhere, rogue devices can piggyback on open Wi-Fi, and sensitive resources can be exposed in minutes.
Wireless 802.1X Authentication with Cisco ISE and a Wireless LAN Controller (WLC) enforces identity-based access control, ensuring only authenticated and authorized users or devices get network access. It’s the gold standard for enterprise Wi-Fi security, replacing weak pre-shared keys (PSKs) with dynamic per-user credentials, certificates, and policies.
This module focuses on the end-to-end flow between wireless clients, WLC, ISE, and RADIUS — plus the exact validation steps you need to prove it’s working.
Problem Statement
Without 802.1X:
- Every device uses the same PSK → if leaked, security is broken for all users.
- No per-user policy enforcement (VLAN, ACL, posture checks).
- No central logging for who accessed what and when.
- No CoA (Change of Authorization) to dynamically change access.
This means IT has no granular control, and compliance audits fail due to lack of accountability.
Solution Overview
Cisco ISE acts as the RADIUS server, validating wireless users via:
- PEAP-MSCHAPv2 for username/password
- EAP-TLS for certificate-based auth
- EAP-TTLS or other enterprise protocols
The WLC is the RADIUS client, bridging the wireless client’s EAP messages to ISE. Once authenticated, ISE sends RADIUS Access-Accept with enforcement: VLAN, DACL, SGT, or redirect ACL.
Validation is done on both sides — WLC CLI/GUI and ISE Live Logs.
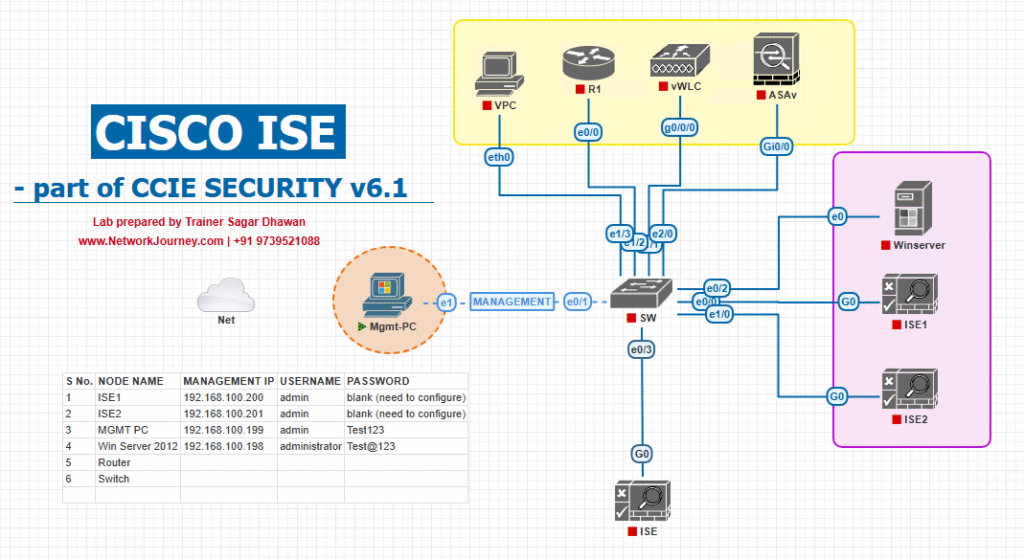
Sample Lab Topology
Environment:
- ISE: v3.x on VMware
- WLC: 9800-CL in EVE-NG or hardware 3504/5520
- Access Point: Lightweight mode (CAPWAP)
- Switch: Catalyst in lab to connect AP
- Wireless Clients: Windows 10, macOS, Linux, iOS, Android
- AD: Windows Server 2019 for identity store
Topology Diagram:
Step-by-Step GUI & CLI Configuration Guide
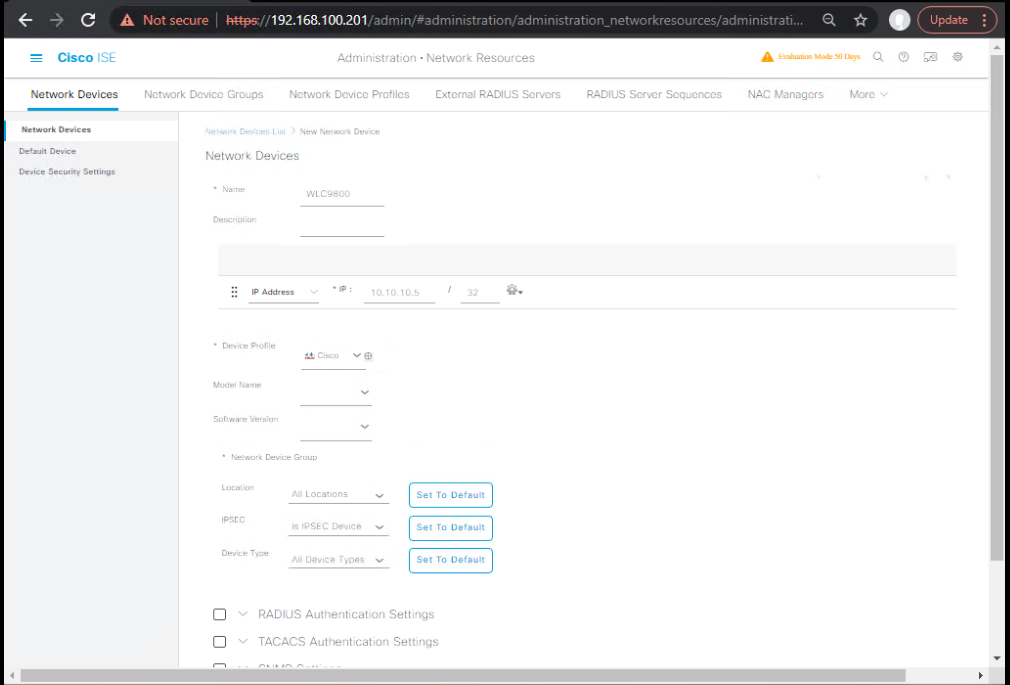
A. On ISE
- Add WLC as a Network Device
- Navigate: Administration → Network Resources → Network Devices → Add
- Name:
WLC9800 - IP:
10.10.10.5 - Shared Secret:
ISEradius123 - [Screenshot: ISE Add Network Device Screen]
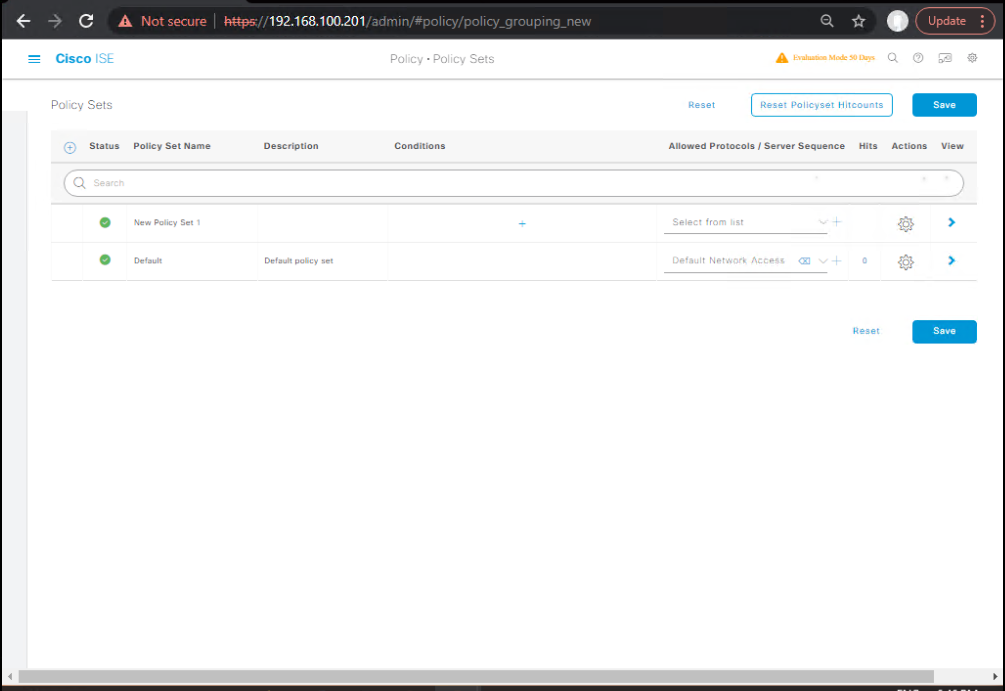
- Create Authentication & Authorization Policy
- Policy Sets → Add → Name: Wireless_8021X
- Auth Policy:
- Condition:
Wireless_MABfor MAB fallback - Condition:
Wireless_8021Xfor EAP methods
- Condition:
- AuthZ Policy:
- Rule 1:
AD_UserGroup = Domain Users→ VLAN 20, Full Access DACL - Rule 2:
Guest→ VLAN 30, Internet-Only DACL
- Rule 1:
- [Screenshot: ISE Policy Set Screen]
B. On WLC (9800 CLI)
# Enable AAA conf t aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius # Add RADIUS server radius server ISE address ipv4 10.10.10.20 auth-port 1812 acct-port 1813 key ISEradius123 # Create WLAN with 802.1X wlan CorpWiFi 1 CorpWiFi client vlan 20 security wpa wpa2 enable security dot1x authentication-list default no shutdown
[CLI Screenshot Placeholder]
C. On Client (Windows Example)
- Open Network & Sharing Center → Manage Wireless Networks.
- Add
CorpWiFiSSID. - Security Type: WPA2-Enterprise.
- Choose PEAP → Validate server certificate → Select ISE cert.
- Enter AD credentials.
D. Validation Steps
On WLC CLI:
show wlan summary show client summary show client detail <MAC>
Look for:
- Policy Manager State = RUN
- PMK derived from EAP exchange
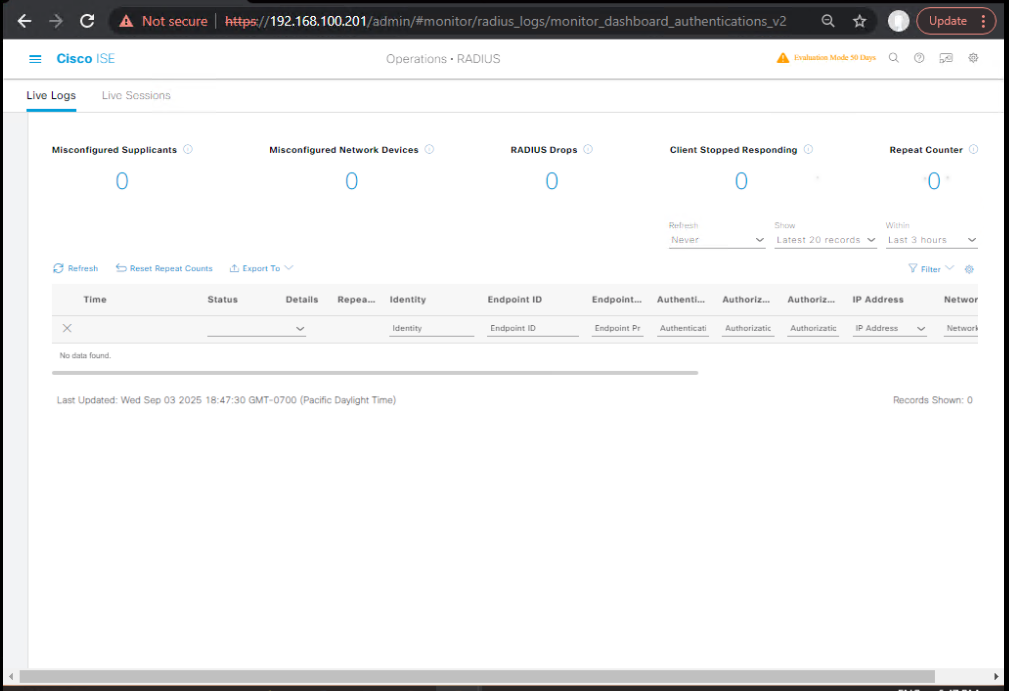
On ISE:
- Go to Operations → RADIUS Live Logs
- Filter by MAC/username → Verify AuthN = Pass, AuthZ = Pass
- [Screenshot: ISE Live Log Detail Screen]
FAQs
1. Why does my wireless 802.1X authentication fail even though my username/password is correct?
Possible Causes:
- Wrong EAP method configured on client vs. ISE policy (e.g., client using PEAP but ISE expecting EAP-TLS).
- Time mismatch between WLC, ISE, and AD server (Kerberos ticket failure).
- ISE certificate not trusted by client.
Fix: Verify NTP sync, trust chain, and EAP configuration alignment.
2. Should I use PEAP-MSCHAPv2 or EAP-TLS for corporate Wi-Fi?
- PEAP-MSCHAPv2: Easier to deploy, credentials-based, but less secure.
- EAP-TLS: Strongest security with client certificates, but requires PKI deployment.
Recommendation: Use EAP-TLS for corporate users and PEAP for BYOD/guest onboarding.
3. How can I check if the WLC is successfully communicating with ISE?
- WLC CLI:
show radius summaryLook for ISE server status = Alive. - ISE Live Logs: See if authentication requests are arriving from WLC’s IP.
4. Why do I get an “EAP Timeout” error on clients?
- Weak Wi-Fi signal during authentication.
- AP/WLC not reachable to ISE on RADIUS ports 1812/1813.
- Supplicant misconfiguration.
Tip: Temporarily set EAP timeout on WLC to 10–20 seconds and retest.
5. Can I assign different VLANs to users connecting to the same SSID?
Yes — use Dynamic VLAN Assignment via ISE Authorization Profiles.
Example:
- IT Staff → VLAN 20
- Guests → VLAN 30
- IoT Devices → VLAN 40
6. How do I push downloadable ACLs (dACL) to wireless users?
- Create dACL in ISE (Policy → Policy Elements → Results → Authorization → Downloadable ACLs).
- Assign in Authorization Profile.
- Verify on WLC CLI:
show ip access-lists
7. Why do some clients keep disconnecting after successful authentication?
- Fast roaming disabled → PMK not cached.
- Incorrect session timeout or reauthentication settings in ISE/WLC.
- Wireless interference causing 4-way handshake failure.
Fix: Enable 802.11r fast roaming for 802.1X SSIDs.
8. Can I use the same ISE policy set for both wired and wireless 802.1X?
Yes, but it’s better to separate them for easier troubleshooting and policy control by using conditions like Device Type = Wireless Controller.
9. How can I test 802.1X authentication without a real wireless client?
- Use
eapol_testfrom Linux. - Use a wireless USB adapter in monitor mode + EAP test tool.
- Some WLCs allow you to simulate authentication via CLI.
10. What’s the best way to troubleshoot 802.1X failures end-to-end?
- Client: Check supplicant logs (Windows Event Viewer → WLAN AutoConfig).
- WLC:
debug client <MAC> debug aaa all enable - ISE: Check RADIUS Live Logs → Click the session → Read failure reason.
- AD: Check Security log for failed logon attempts.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Wireless 802.1X with Cisco ISE transforms Wi-Fi from “shared password” chaos into secure, policy-driven access. Every authentication is logged, every device is validated, and policies can adapt dynamically — critical for compliance and Zero Trust models.
Upgrade Your Skills – Start Today
Ready to Master Cisco ISE & Enterprise Security?
Join the exclusive 4-month Instructor-Led CCIE Security Mastery Program, designed to take you from fundamentals to complex real-world deployments — with 100% lab-focused sessions, step-by-step config guides, and exam preparation.
- Seats are limited — Secure your spot here: https://course.networkjourney.com/ccie-security/
- Also, subscribe to the Network Journey YouTube Channel for free weekly deep-dive lessons, lab demos, and troubleshooting walkthroughs.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 41] Cisco ISE Mastery Training: Wireless 802.1X Authentication Overview](https://networkjourney.com/wp-content/uploads/2025/08/Day-41-Cisco-ISE-Mastery-Training-Wireless-802.1X-Authentication-Overview.png)


![[Day#3 PyATS Series] Installing pyATS & Genie (core, NX-OS, IOS-XR plugins) using pyATS for Cisco](https://networkjourney.com/wp-content/uploads/2025/07/Day3-PyATS-Series-Installing-pyATS-Genie-core-NX-OS-IOS-XR-plugins-using-pyATS-for-Cisco_networkjouney.png)