[Day 43] Cisco ISE Mastery Training: Wireless MAB Authentication
Table of Contents
Introduction
Wireless MAC Authentication Bypass (MAB) is one of the foundational network access control mechanisms in Cisco Identity Services Engine (ISE) — particularly critical in environments where certain wireless devices cannot perform 802.1X authentication (e.g., IoT sensors, IP phones, barcode scanners, printers).
Unlike 802.1X, which requires supplicant software and credentials, Wireless MAB uses the device’s MAC address as its identity. While not as secure as certificate-based EAP-TLS, MAB still plays an important role in segregating, profiling, and applying policy controls to non-supplicant devices on the WLAN.
In Cisco ISE, MAB authentication allows:
- Profiling unmanaged or legacy devices.
- Applying specific VLANs and ACLs dynamically.
- Controlling network access even without supplicant support.
- Enforcing compliance policies for devices that would otherwise bypass NAC.
ISE integrates with the Cisco Wireless LAN Controller (WLC) to receive MAC authentication requests, evaluate them against internal/external identity stores, and return authorization decisions — completing the NAC loop even in non-802.1X scenarios.
Problem Statement
In enterprise wireless environments, you often have:
- IoT devices that don’t support WPA2-Enterprise (802.1X).
- Legacy barcode scanners, VoIP handsets, wireless printers without supplicant capability.
- Guest devices that need temporary access without user intervention.
If such devices are connected without proper NAC enforcement, they create a massive security gap:
- No authentication means anyone with physical presence can connect.
- No role-based policy enforcement leads to flat network access.
- No device visibility prevents effective security monitoring.
Without MAB, the only fallback is open SSID or WPA2-PSK, which lacks per-device control and is highly insecure.
Solution Overview
Cisco ISE’s Wireless MAB works in tandem with a Cisco WLC as follows:
- A device connects to a MAB-enabled WLAN SSID.
- The WLC sends a RADIUS request to ISE, using the device’s MAC address as both username and password.
- ISE checks the MAC address against its configured endpoints database or an external source (like Active Directory, SQL, or an external MAC list).
- If matched, ISE applies the corresponding authorization profile (e.g., VLAN assignment, ACL, QoS policy).
- If not matched, ISE can place the device into a restricted VLAN or deny access entirely.
ISE can also profile unknown devices and dynamically add them to the endpoint database for future automated authentication.
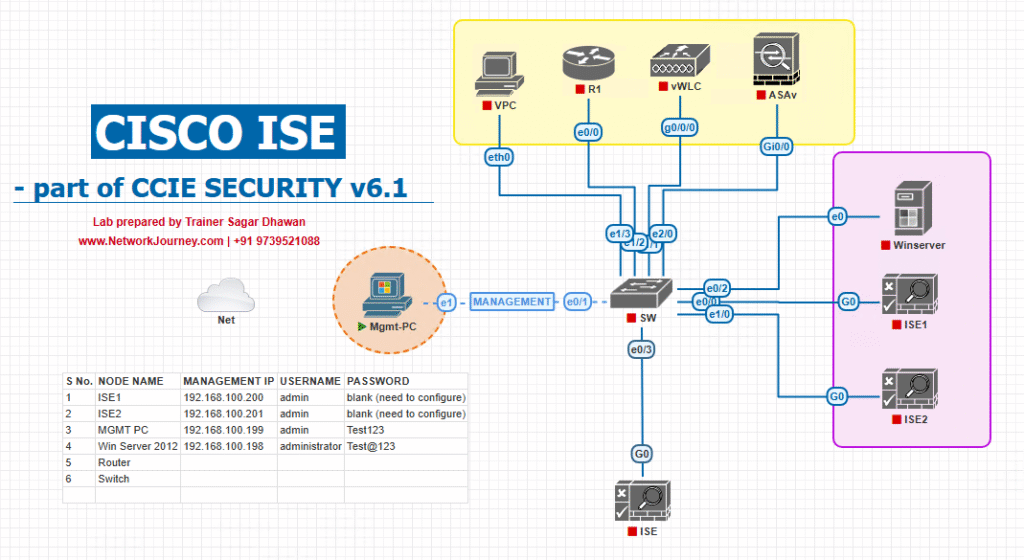
Sample Lab Topology
Lab Environment:
- Virtualization: VMware Workstation or EVE-NG for simulation.
- Cisco ISE: Version 3.x (running in VMware/EVE-NG).
- Cisco WLC: 9800-CL (virtual) or AireOS WLC (8.10+).
- Switch: Catalyst 9300 or virtual switch in EVE-NG for wired uplink to WLC.
- Endpoints:
- Wireless printer (simulated MAC in test script).
- IoT sensor (simulated MAC).
- Windows laptop for admin access.
Diagram :
Step-by-Step GUI Configuration Guide
Part A – WLC Configuration
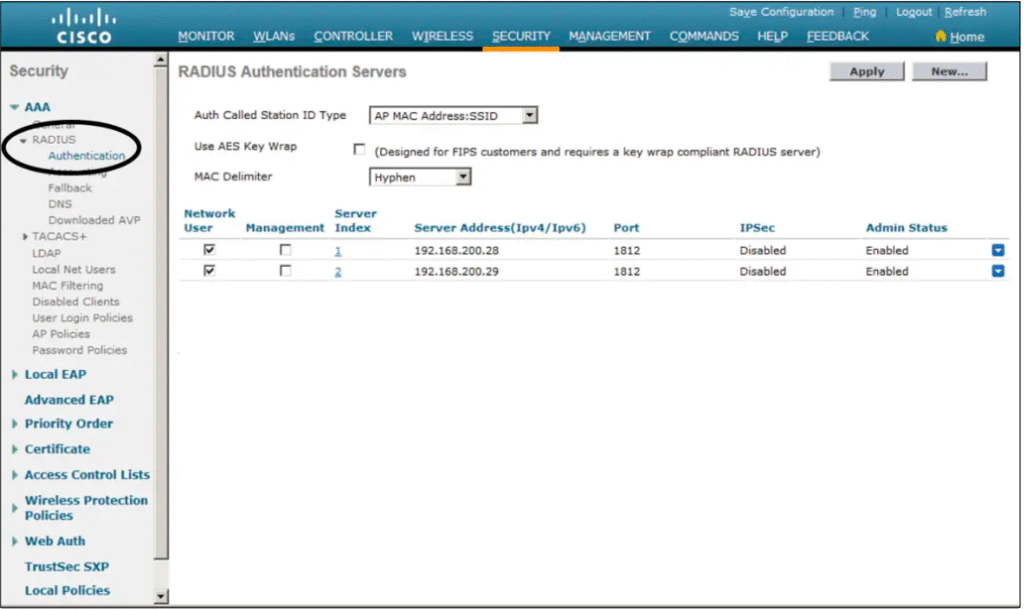
- Enable AAA Server on WLC
- Navigate: Security > AAA > RADIUS > Authentication
- Add ISE IP address.
- Set Shared Secret (must match ISE).
- [Screenshot: WLC AAA Server Config]
- Create WLAN for MAB
- Go to WLANs > Create New
- SSID:
MAB-Wireless - WLAN ID:
2(example) - [Screenshot: WLAN Creation]
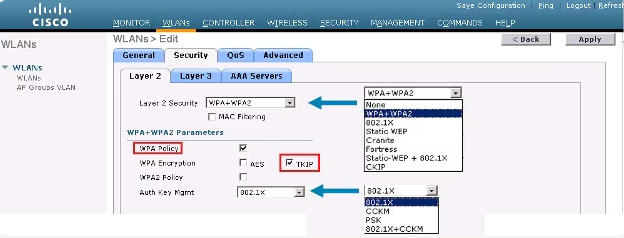
- Configure WLAN Security to MAC Filtering
- Layer 2 Security: None
- MAC Filtering: Enabled
- [Screenshot: MAC Filtering Enable]
- Bind WLAN to AAA Server
- WLAN > Security > AAA Servers
- Authentication Server: ISE RADIUS server.
- [Screenshot: WLAN AAA Binding]
Part B – Cisco ISE Configuration
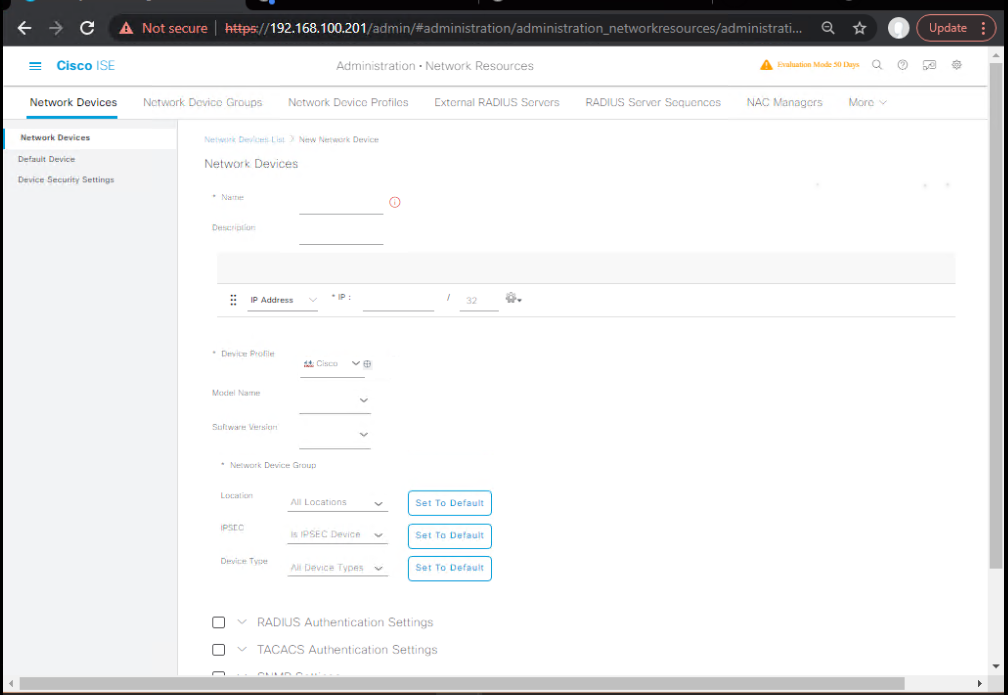
- Add WLC as Network Device
- Navigate: Administration > Network Resources > Network Devices
- Add:
WLC-9800CL - IP:
192.168.x.x - Shared Secret: Same as in WLC.
- [Screenshot: Add Network Device]
- Add Endpoint MAC in ISE
- Work Centers > Administration > Identity Management > Endpoints
- Add new endpoint, enter MAC in
xx:xx:xx:xx:xx:xxformat. - Assign Endpoint Group (e.g., Printers, IoT).
- [Screenshot: Endpoint Entry]
- Create Authorization Profile
- Navigate: Policy > Policy Elements > Results > Authorization > Authorization Profiles
- Profile Name:
IoT-Access - VLAN: 30
- ACL: IoT-Restricted
- [Screenshot: Authorization Profile Config]
- Configure Policy Set for MAB
- Navigate: Policy > Policy Sets
- Create new Policy Set:
Wireless MAB Policy - Condition:
Device Type = WirelessANDAuthMethod = MAB - Authentication Policy: Internal Endpoints
- Authorization Policy: Assign
IoT-Accessif MAC is known, elseDenyAccess - [Screenshot: Policy Set Screen]
Part C – CLI Validation (WLC & ISE)
- On WLC:
show client detail <MAC> show radius auth statistics debug client <MAC> - On ISE:
- Operations > RADIUS > Live Logs → Filter by MAC
- Check authentication method: MAB
- Verify Authorization Profile returned.
FAQs for Wireless MAB Authentication
1. How does Wireless MAB actually work on a Cisco WLC?
When a client connects to a WLAN with MAC Filtering enabled, the WLC immediately sends a RADIUS Access-Request to ISE, using the MAC address as both the username and password. ISE checks the MAC against its endpoint database or identity store and returns an Accept or Reject, along with optional VLAN, ACL, or QoS attributes.
2. Is MAB secure enough for production environments?
Not by itself — MAC addresses can be easily spoofed. In production, you combine MAB with profiling, posture assessment, dACLs, and network segmentation to limit exposure. Always place MAB devices in restricted VLANs or behind firewalls.
3. Can ISE automatically learn MAC addresses of new devices?
Yes. Unknown MACs can be allowed temporary access and auto-added to ISE’s Endpoint Identity Group through profiling or a “Permit and Learn” policy. You can then approve them manually or via workflow.
4. Does MAB work alongside 802.1X?
Yes. In fact, many deployments use MAB as a fallback method in the policy set. If 802.1X fails or the device lacks a supplicant, ISE tries MAB next.
5. What’s the difference between Wired MAB and Wireless MAB in ISE?
The principle is the same, but:
- Wired MAB: Switchport triggers authentication.
- Wireless MAB: WLC triggers authentication using MAC Filtering.
The configuration steps differ slightly on the network access device.
6. How can I profile devices during MAB?
Enable RADIUS accounting and profiling probes (e.g., DHCP, HTTP, RADIUS). ISE will fingerprint the device type and OS based on observed traffic, allowing you to build dynamic policies.
7. What happens if two devices have the same MAC address?
ISE sees them as the same endpoint — which can cause policy misapplication. MAC address spoofing can also occur. Mitigation involves physical security, NAC monitoring, and anomaly detection.
8. Can I send different VLANs for different MAB devices?
Yes. The Authorization Profile in ISE can return a unique VLAN ID per device or group. This is common for segmenting IoT, printers, and corporate assets.
9. How do I troubleshoot MAB authentication failures?
- On WLC:
debug client <MAC> show client detail <MAC> show radius auth statistics - On ISE:
Go to Operations > RADIUS > Live Logs, filter by MAC, check if the authentication method is MAB, and see the authorization result.
10. What’s the maximum number of MAB endpoints ISE can store?
It depends on your ISE licensing tier. Large deployments can handle millions of MAC addresses, but performance planning and distributed deployment design are critical at that scale.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Wireless MAB is not a replacement for secure 802.1X, but it’s a crucial part of a layered NAC strategy to handle legacy and IoT devices. In Cisco ISE, it integrates seamlessly with profiling, dynamic VLANs, and policy-based control to close wireless security gaps.
Upgrade Your Skills – Start Today
If you found this step-by-step training valuable, imagine what you could achieve in 4 months of live, instructor-led, hands-on CCIE Security training.
- Course: Cisco CCIE Security (Full Stack NAC, Firewalls, VPNs, Advanced Threat Control)
- Duration: 4 Months – Live + Lab Access
- Includes: Real-world labs, EVE-NG topologies, lifetime access to recordings, career mentorship.
- Next Step: Visit https://course.networkjourney.com/ccie-security/, reserve your seat, and transform into a job-ready security engineer.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 43] Cisco ISE Mastery Training: Wireless MAB Authentication](https://networkjourney.com/wp-content/uploads/2025/08/Day-43-Cisco-ISE-Mastery-Training-Wireless-MAB-Authentication.png)
![Introduction to JSON & YANG – The Foundation of Network Automation [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/Introduction-to-JSON_YANG–The-Foundation-of-Network-Automation_networkjourney.png)
![PBR Configuration with Match Statements [ CCNP ENTERPRISE ]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/06/PBR-Configuration-with-Match-Statements-CCNP-ENTERPRISE-.png)
![[Day 32] Cisco ISE Mastery Training: Configuring Cisco AnyConnect NAM for Wired Auth](https://networkjourney.com/wp-content/uploads/2025/08/Day-32-–-Cisco-ISE-Mastery-Training-Configuring-Cisco-AnyConnect-NAM-for-Wired-Auth.png)